信息网络安全 ›› 2018, Vol. 18 ›› Issue (4): 15-22.doi: 10.3969/j.issn.1671-1122.2018.04.003
动态虚拟MSISDN的拟态自动机模型与安全性验证方法
- 郑州大学信息工程学院,河南郑州 450001
-
收稿日期:2018-01-30出版日期:2018-04-15发布日期:2020-05-11 -
作者简介:作者简介:朱维军(1976—),男,河南,副教授,博士,主要研究方向为信息安全、形式化方法;樊永文(1993—),男,河南,硕士研究生,主要研究方向为形式化方法;班绍桓(1996—),男,河南,硕士研究生,主要研究方向为形式化方法。
-
基金资助:国家自然科学基金联合基金[U1204608];国家重点研发计划[2016YFB0800100]
A Mimic-automaton-based Model for the MSISDN Virtualization and Its Method for Verifying the Security
Weijun ZHU( ), Yongwen FAN, Shaohuan BAN
), Yongwen FAN, Shaohuan BAN
- School of Information Engineering, Zhengzhou University, Zhengzhou Henan 450001, China
-
Received:2018-01-30Online:2018-04-15Published:2020-05-11
摘要:
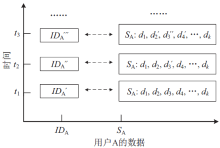
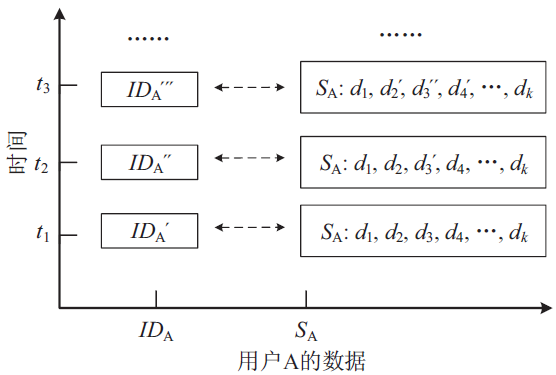
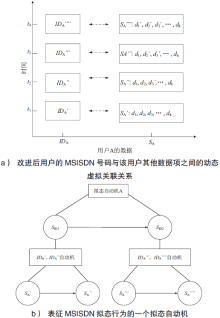
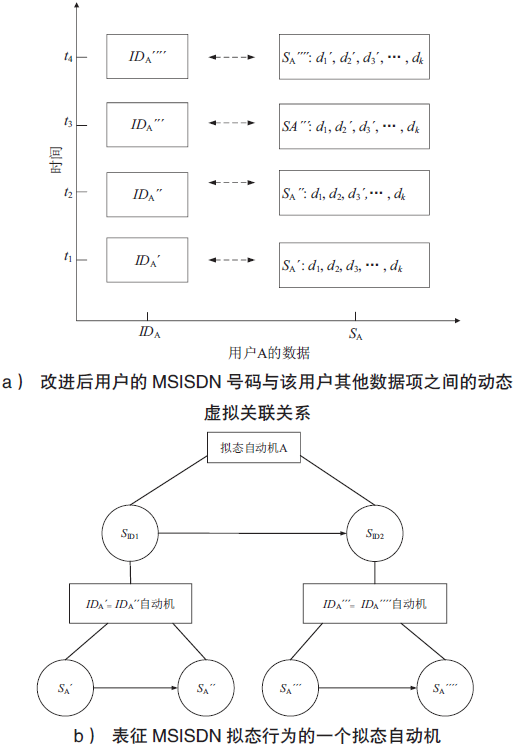
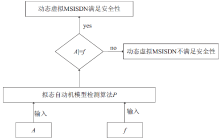
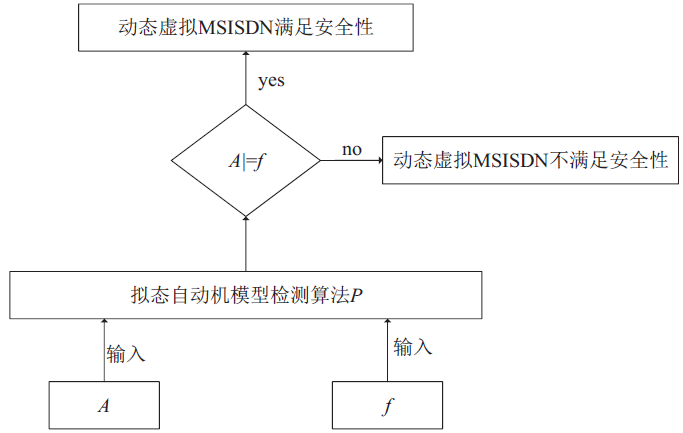
移动通信MSISDN号码对外公开,导致用户数据信息泄露或被恶意窃取。动态虚拟MSISDN号码通过引入拟态防御机制,可实现用户信息防泄露和防窃取。然而,对于该技术在全状态空间的安全性,目前尚缺乏有效的分析方法。文章首先使用有穷状态自动机描述动态虚拟MSISDN的状态迁移;使用细胞自动机描述动态虚拟MSISDN的变化结构;使用层次自动机描述动态虚拟MSISDN的不同计算粒度。其次,将各种自动机按照一定的逻辑关系组织起来,即可获得描述动态虚拟MSISDN内在行为的拟态自动机模型。然后,使用特定的线性时序逻辑公式描述动态虚拟MSISDN安全性。最后,将动态虚拟MSISDN安全性问题按如下方式规约为拟态自动机模型检测问题:若模型检测结果指出拟态自动机满足给定的线性时序逻辑公式,则动态虚拟MSISDN满足安全性;若模型检测结果指出拟态自动机不满足给定的线性时序逻辑公式,则动态虚拟MSISDN不满足安全性。由此便可在全状态空间上自动验证动态虚拟MSISDN的安全性。仿真实验证实了文中方法的高效性。
中图分类号:
引用本文
朱维军, 樊永文, 班绍桓. 动态虚拟MSISDN的拟态自动机模型与安全性验证方法[J]. 信息网络安全, 2018, 18(4): 15-22.
Weijun ZHU, Yongwen FAN, Shaohuan BAN. A Mimic-automaton-based Model for the MSISDN Virtualization and Its Method for Verifying the Security[J]. Netinfo Security, 2018, 18(4): 15-22.
| [1] | LIU Caixia, JI Xinsheng, WU Jiangxing.A Mimic Defense Mechanism for Mobile Communication User Data Basedon MSISDN Virtualization[J]. Chinese Journal of Computers, 2017, 41(2): 275-287. |
| 刘彩霞,季新生,邬江兴. 一种基于MSISDN虚拟化的移动通信用户数据拟态防御机制[J]. 计算机学报,2017,41(2):275-287. | |
| [2] | WU Jiangxing.Meaning and Vision of Mimic Computing and Mimic Security Defense[J]. Telecommunications Science, 2014, 30(7): 1-7. |
| 邬江兴. 拟态计算与拟态安全防御的原意和愿景[J]. 电信科学,2014,30(7):1-7. | |
| [3] | WU Jiangxing. Mimic Computing and Mimic Security[EB/OL]. , 2018-1-11. |
| 邬江兴. 拟态计算与拟态安全[EB/OL]. , 2018-1-11. | |
| [4] | ScienceNet. The Top 10 Scientific and Technological Progress of China and the World in 2013 is Announced[EB/OL] . , 2018-1-11. |
| 科学网. 2013中国、世界十大科技进展新闻揭晓[EB/OL]. , 2018-1-11. | |
| [5] | LI Yun, YANG Sen. A Game Changer of Cyberspace: Behind the Scenes of the Mimic Defense Theory[EB/OL]. , 2018-1-11. |
| 黎云,杨森. 做网络空间游戏规则的改变者—拟态防御理论问世的台前幕后[EB/OL]. , 2018-1-11. | |
| [6] | SI Xueming. Study on Theory of Mimic Security[EB/OL]. , 2018-1-11. |
| 斯雪明. 拟态安全理论研究[EB/OL]. , 2018-1-11. | |
| [7] | HU Hongchao, CHEN Fucai, WANG Zhenpeng.Performance Evaluations on DHR for Cyberspace Mimic Defense[J]. Journal of Cyber Security, 2016, 1(4): 40-51. |
| 扈红超,陈福才,王禛鹏. 拟态防御DHR模型若干问题探讨和性能评估[J]. 信息安全学报,2016,1(4):40-51. | |
| [8] | WU Jiangxing.Research on Cyber Mimic Defense[J]. Journal of Cyber Security, 2016, 1(4): 1-10. |
| 邬江兴. 网络空间拟态防御研究[J]. 信息安全学报,2016,1(4):1-10. | |
| [9] | WU Jiangxing.Introduction to Cyberspace Mimic Defense[M]. Beijing: Science Press, 2017. |
| 邬江兴. 网络空间拟态防御导论[M]. 北京:科学出版社,2017. | |
| [10] | MA Hailong, YI Peng, JIANG Yiming, et al.Dynamic Heterogeneous Redundancy Based Router Architecture with Mimic Defenses[J]. Journal of Cyber Security, 2017, 2(1): 29-42. |
| 马海龙,伊鹏,江逸茗,等,基于动态异构冗余机制的路由器拟态防御体系结构[J]. 信息安全学报,2017,2(1):29-42. | |
| [11] | TONG Qing, ZHANG Zheng, ZHANG Weihua, et al.Design and Implementation of Mimic Defense Web Server[J]. Journal of Software, 2017, 28(4): 883-897. |
| 仝青,张铮,张为华,等. 拟态防御Web服务器设计与实现[J]. 软件学报,2017,28(4):883-897. | |
| [12] | YANG Tao, XIAO Ttianyuan, ZHANG Linxuan.Behavior Modeling for Application Software Using Hierarchical Automata[J]. Journal of System Simulation, 2005, 17(4): 778-781. |
| 杨涛,肖田元,张林鍹. 基于层次自动机的应用软件行为建模[J]. 系统仿真学报,2005,17(4):778-781. | |
| [13] | WOLFRAM S.Computation Theory of Cellular Automata[J]. Communications in Mathematical Physics, 1984, 96(1): 15-57. |
| [14] | ZHU Weijun, FAN Yongwen, BAN Shaohuan.A Novel Type of Automata for Mimic Computing[C]//IEEE. 2007 IEEE International Conference on Software Engineering and Service Science, November 11-24, 2017, Beijing, China. New Jersey: IEEE, 2017: 859-862. |
| [15] | ZHU Weijun. A Novel Type of Automata for Dynamic, Heterogeneous and Random Architectures[EB/OL]. , 2018-1-12. |
| [16] | CLARKE E M.Model Checking[M]. Cambridge: MIT Press, 1999. |
| [17] | CHENG Pingguang.Mimic Community Clustering of Society Networks[J]. Computer Science, 2015, 42(8): 136-138. |
| 成平广. 基于拟态计算的社会网络划分算法[J]. 计算机科学,2015,42(8):136-138. | |
| [18] | WEI Shuai, YU Hong, GU Zeyu, et al.Architecture of Mimic Security Processor for Industry Control System[J]. Journal of Cyber Security, 2017, 2(1): 54-73. |
| 魏帅,于洪,顾泽宇,等. 面向工控领域的拟态安全处理机架构[J]. 信息安全学报,2017,2(1):54-73. | |
| [19] | WANG Zhenpeng,HU Hongchao,CHENG Guozhen.A DNS Architecture Based on Mimic Security Defense[J]. Acta Electronica Sinica, 2017(11): 2705-2714. |
| 王禛鹏,扈红超,程国振. 一种基于拟态安全防御DNS框架设计[J]. 电子学报,2017(11):2705-2714. | |
| [20] | WANG Zhenpeng, HU Hongchao, CHENG Guozhen, et al.Implementation Architecture of Mimic Security Defense Based on SDN[J]. Chinese Journal of Network and Information Security, 2017(10): 52-61. |
| 王禛鹏,扈红超,程国振,等. 软件定义网络下的拟态防御实现架构[J]. 网络与信息安全学报,2017(10):52-61. | |
| [21] | PANG Jianmin, ZHANG Yujia, ZHANG Zheng, et al.Applying a Combination of Mimic Defense and Software Diversity in the Software Security Industry[J]. Engineering Sciences, 2016,18(6): 74-78. |
| 庞建民,张宇嘉,张铮,等. 拟态防御技术结合软件多样化在软件安全产业中的应用[J]. 中国工程科学,2016,18(6):74-78. | |
| [22] | SU Li, Shao Jing, DU Haitao.Risk Analysis of Mutual 0peration of 2G/3G/4G Mobile Communication Network and Protection Scheme[J]. Netinfo Security, 2017(9): 69-72. |
| 粟栗,邵京,杜海涛. 移动通信网2G/3G/4G互操作风险分析与防护方案[J]. 信息网络安全,2017(9):69-72. | |
| [23] | WANG Pan, LIANG Yiwen.Distributed Immune Modal for Mobile Phone Malware Detection[J]. Computer Engineering and Applications, 2016, 52(16): 30-35. |
| 王盼,梁意文. 手机恶意软件检测的分布式免疫模型[J]. 计算机工程与应用,2016,52(16):30-35. | |
| [24] | CHEN Chen, WANG Yijun, HU Guangjun, et al.Research on APT Attack Technology of Smartphones[J]. Netinfo Security, 2015(3): 33-37. |
| 陈晨,王奕钧,胡光俊,等. 针对手机的APT攻击方式的研究[J]. 信息网络安全,2015(3):33-37. | |
| [25] | FU Yu,LI Hongcheng, WU Xiaoping, et al.Detecting APT Attacks: A Survey from the Perspective of Big Data Analysis[J]. Journal on Communications, 2015, 36(11): 1-14. |
| 付钰,李洪成,吴晓平,等. 基于大数据分析的APT攻击检测研究综述[J]. 通信学报,2015,36(11):1-14. | |
| [26] | ZHANG Fan, ZHONG Zhangdui.Detection and Prevention of Mobile Malware Based on the Analysis of Permissions[J]. Netinfo Security, 2015(10): 66-73. |
| 张帆,钟章队. 基于权限分析的手机恶意软件检测与防范[J]. 信息网络安全,2015(10):66-73. |
| [1] | 易辉凡, 万良, 黄娜娜, 王鹍鹏. 基于SPIN的安全协议的攻击者建模方法研究[J]. 信息网络安全, 2018, 18(2): 61-70. |
| [2] | 蔡林, 陈铁明. Android移动恶意代码检测的研究概述与展望[J]. 信息网络安全, 2016, 16(9): 218-222. |
| [3] | . 基于AVISPA的快速切换认证协议FHAM的安全建模与检测[J]. , 2014, 14(5): 21-. |
| [4] | 徐有福;文伟平;万正苏. 基于漏洞模型检测的安全漏洞挖掘方法研究[J]. , 2011, 11(8): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||