信息网络安全 ›› 2025, Vol. 25 ›› Issue (10): 1537-1545.doi: 10.3969/j.issn.1671-1122.2025.10.005
面向云边协同场景中固件的模糊测试方法
- 复旦大学大数据研究院,上海 200433
-
收稿日期:2025-06-25出版日期:2025-10-10发布日期:2025-11-07 -
通讯作者:陈平 E-mail:pchen@fudan.edu.cn -
作者简介:陶慈(2003—),女,安徽,博士研究生,主要研究方向为系统安全|王逸(1981—),男,江苏,研究员,博士,主要研究方向为软件安全、系统安全、人工智能安全|张蕾(1982—),女,江苏,助理研究员,硕士,主要研究方向为网络安全、密码学|陈平(1985—),男,江苏,研究员,博士,主要研究方向为软件和系统安全、内生安全、智能车安全 -
基金资助:国家重点研发计划(2022YFB3104300)
Fuzz Testing Method for Firmware in Cloud-Edge Collaborative Scenarios
TAO Ci, WANG Yi, ZHANG Lei, CHEN Ping( )
)
- Institute of Big Data, Fudan University, Shanghai 200433, China
-
Received:2025-06-25Online:2025-10-10Published:2025-11-07 -
Contact:CHEN Ping E-mail:pchen@fudan.edu.cn
摘要:
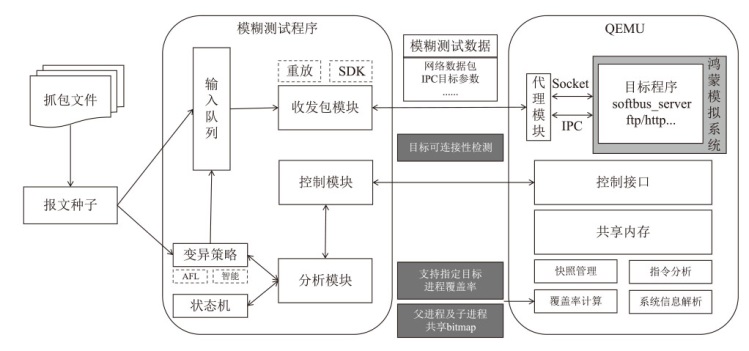
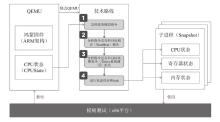
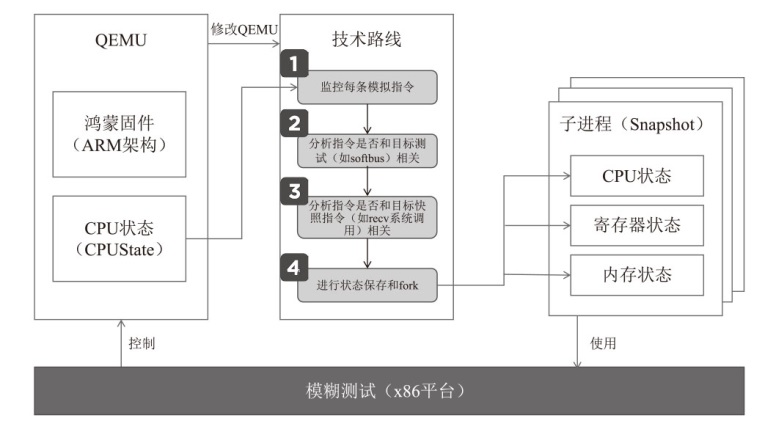
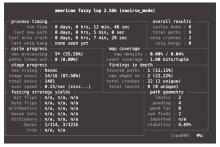
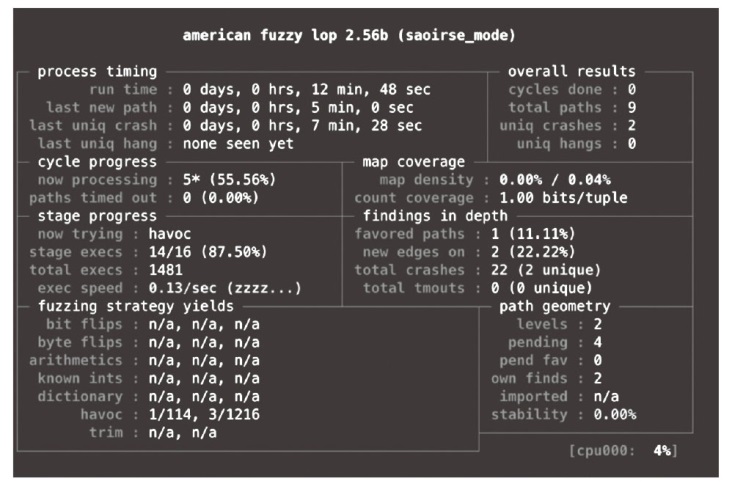
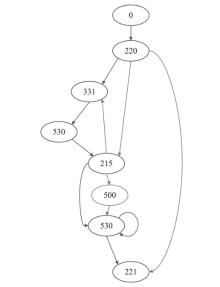
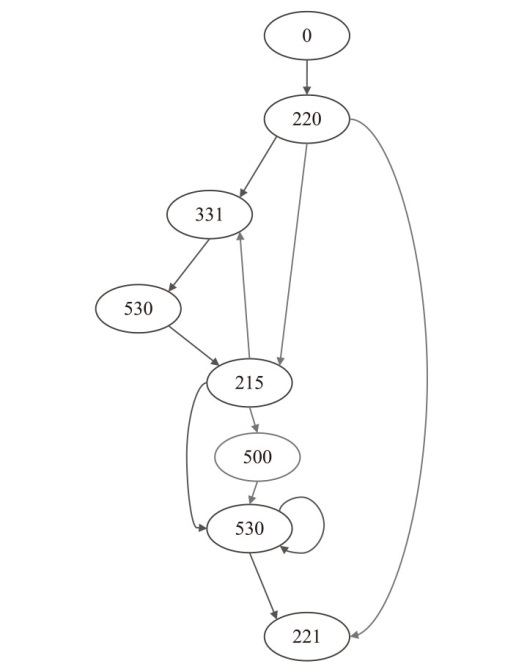
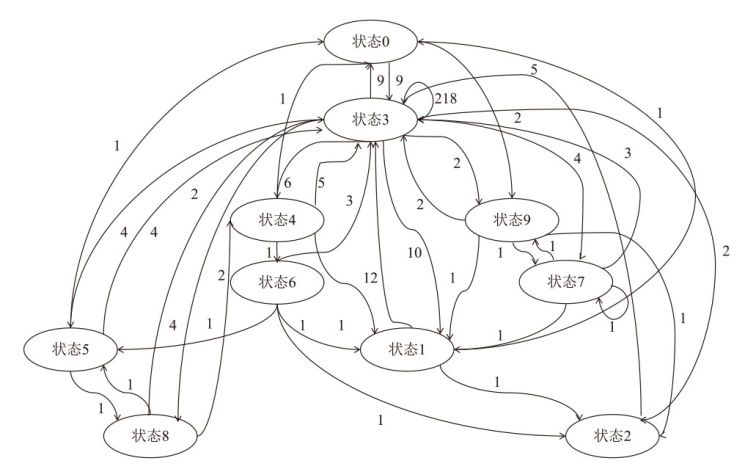
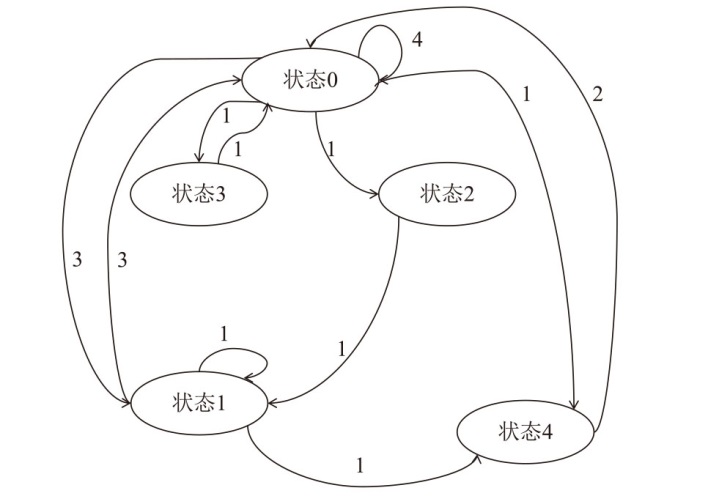
在云边协同场景中,保障海量边缘设备固件安全面临状态感知困难和执行效率低下的双重挑战。由于固件通常以二进制形式发布,依赖源码插桩的状态感知方法不再适用。同时,在x86平台上对ARM等异构架构固件进行高效全系统仿真成为现有技术的瓶颈,严重限制了模糊测试的吞吐量。针对这些问题,文章提出一种面向ARM架构固件的高效模糊测试框架。为突破跨架构仿真的性能瓶颈,文章将fork机制应用于QEMU内部,设计并实现了一种不依赖特定硬件(如Intel VT-x)的轻量级、跨架构全系统虚拟机快照技术。为实现无源码下的状态感知,文章实现了基于网络数据包、内存数据聚类和调用堆栈分析的多种状态识别方法。此外,统一的代理模块还支持对网络服务等复杂目标的透明测试。实验结果表明,该框架在测试效率上取得近19%的提升,成功复现了CVE-2019-15232等已知漏洞,并验证了其在无源码条件下对程序进行状态建模的能力,为云边协同安全测试提供了有效的解决方案。
中图分类号:
引用本文
陶慈, 王逸, 张蕾, 陈平. 面向云边协同场景中固件的模糊测试方法[J]. 信息网络安全, 2025, 25(10): 1537-1545.
TAO Ci, WANG Yi, ZHANG Lei, CHEN Ping. Fuzz Testing Method for Firmware in Cloud-Edge Collaborative Scenarios[J]. Netinfo Security, 2025, 25(10): 1537-1545.
| [1] | RAHMANOVIĆ A, HAKIĆ E, SARAČEVIĆ M, et al. Application and Development of Embedded Systems with IoT Components: Aspect of Safety and Reliability[EB/OL]. (2023-12-25)[2025-06-10]. https://doi.org/10.18421/SAR64-03. |
| [2] | Palo Alto Networks. 2020 Unit 42 Iot Threat Report[EB/OL]. (2020-03-10)[2025-06-10]. https://unit42.paloaltonetworks.com/iot-threat-Rep.-2020/. |
| [3] | NETGEAR Security Team. The 2024 Iot Security Landscape Report[EB/OL]. [2025-06-10]. https://www.netgear.com/hub/network/2024-iot-threat-report/. |
| [4] |
MILLER B P, FREDRIKSEN L, SO B. An Empirical Study of the Reliability of Unix Utilities[J]. Communications of the ACM, 1990, 33(12): 32-44.
doi: 10.1145/96267.96279 URL |
| [5] | PHAM V T, BÖHME M, ROYCHOUDHURY A. AFLNet: A Greybox Fuzzer for Network Protocols[C]// IEEE. 2020 IEEE 13th International Conference on Software Testing, Validation and Verification (ICST). New York: IEEE, 2020: 460-465. |
| [6] | NATELLA R. StateAFL: Greybox Fuzzing for Stateful Network Servers[EB/OL]. (2022-10-04)[2025-06-10]. https://doi.org/10.1007/s10664-022-10233-3. |
| [7] |
GAO Jian, XU Yiwen, JIANG Yu, et al. EM-Fuzz: Augmented Firmware Fuzzing via Memory Checking[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2020, 39(11): 3420-3432.
doi: 10.1109/TCAD.43 URL |
| [8] | ZHANG Chi, WANG Yu, WANG Linzhang, Firmware Fuzzing: The State of the Art[C]// ACM. The 12th Asia-Pacific Symposium on Internetware. New York: ACM, 2020: 110-115. |
| [9] | ZHENG Yaowen, DAVANIAN A, YIN Heng, et al. FIRM-AFL: High-Throughput Greybox Fuzzing of IoT Firmware via Augmented Process Emulation[C]// USENIX. 28th USENIX Security Symposium (USENIX Security’19). Berkely: USENIX, 2019: 1099-1114. |
| [10] | SHAN Haoqi, NISSANKARARAO S, LIU Yujia, et al. LightEMU: Hardware Assisted Fuzzing of Trusted Applications[C]// IEEE. 2024 IEEE International Symposium on Hardware Oriented Security and Trust (HOST). New York: IEEE, 2024: 1-11. |
| [11] | SCHUMILO S, ASCHERMANN C, ABBASI A, et al. Nyx: Greybox Hypervisor Fuzzing Using Fast Snapshots and Affine Types[C]// USENIX. 30th USENIX Security Symposium (USENIX Security’21). Berkely: USENIX, 2021: 2597-2614. |
| [12] | BASICEVIC I, POPOVIC M, VELIKIC I. Use of Finite State Machine Based Framework in Implementation of Communication Protocols-A Case Study[C]// IEEE. 2010 Sixth Advanced International Conference on Telecommunications. New York: IEEE, 2010: 161-166. |
| [13] | DRUMEA A, POPESCU C. Finite State Machines and Their Applications in Software for Industrial Control[C]// IEEE. 27th International Spring Seminar on Electronics Technology:Meeting the Challenges of Electronics Technology Progress. New York: IEEE, 2004: 25-29. |
| [14] | CHEN Yurong, LAN Tian, VENKATARAMANI G. Exploring Effective Fuzzing Strategies to Analyze Communication Protocols[C]// ACM. The 3rd ACM Workshop on Forming an Ecosystem Around Software Transformation. New York: ACM, 2019: 17-23. |
| [15] | QIN Shisong, HU Fan, MA Zheyu, et al. NSFuzz: Towards Efficient and State-Aware Network Service Fuzzing[J]. ACM Transactions on Software Engineering and Methodology, 2023, 32(6): 1-26. |
| [16] | BELLARD F. QEMU, A Fast and Portable Dynamic Translator[C]// USENIX. USENIX Annual Technical Conference. Berkely: USENIX, 2005: 41-46. |
| [17] | LI Wenqiang, SHI Jiameng, LI Fengjun, et al. μAFL: Non-Intrusive Feedback-Driven Fuzzing for Microcontroller Firmware[C]// ACM. The 44th International Conference on Software Engineering. New York: ACM, 2022: 1-12. |
| [18] | SCHUMILO S, ASCHERMANN C, GAWLIK R, et al. kAFL: Hardware-Assisted Feedback Fuzzing for OS Kernels[C]// USENIX. 26th USENIX Security Symposium (USENIX Security’17). Berkely: USENIX, 2017: 167-182. |
| [19] | SONG D, HETZELT F, KIM J, et al. Agamotto: Accelerating Kernel Driver Fuzzing with Lightweight Virtual Machine Checkpoints[C]// USENIX. 29th USENIX Security Symposium (USENIX Security’20). Berkely: USENIX, 2020: 2541-2557. |
| [20] |
DENNING D E. A Lattice Model of Secure Information Flow[J]. Communications of the ACM, 1976, 19(5): 236-243.
doi: 10.1145/360051.360056 URL |
| [21] | LIANG Jie, WANG Mingzhe, ZHOU Chijin, et al. Pata: Fuzzing with Path Aware Taint Analysis[C]// IEEE. 2022 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2022: 1-17. |
| [22] | HOSSAIN M M, DIPU N F, AZAR K Z, et al. TaintFuzzer: SoC Security Verification Using Taint Inference-Enabled Fuzzing[C]// IEEE. 2023 IEEE/ACM International Conference on Computer Aided Design (ICCAD). New York: IEEE, 2023: 1-9. |
| [1] | 胡斌, 黑一鸣, 吴铁军, 郑开发, 刘文忠. 大模型安全检测评估技术综述[J]. 信息网络安全, 2025, 25(10): 1477-1492. |
| [2] | 张大龙, 丁曙光, 韩志龙, 付守利, 唐志青, 石磊. 网络韧性评估框架和方法综述[J]. 信息网络安全, 2025, 25(10): 1493-1505. |
| [3] | 兰佳晨, 陈夏润, 周杨凯, 文伟平. 多模态网络中的路由技术与协议研究综述[J]. 信息网络安全, 2025, 25(10): 1506-1522. |
| [4] | 余发江, 王朝州. TrustZone半虚拟化与容器化实现机制[J]. 信息网络安全, 2025, 25(10): 1523-1536. |
| [5] | 谢四江, 冯雁, 阎亚龙, 宁飞. 基于密钥双同步的量子密钥通用服务模式研究[J]. 信息网络安全, 2025, 25(10): 1546-1553. |
| [6] | 李古月, 张子豪, 毛承海, 吕锐. 基于累积量与深度学习融合的水下调制识别模型[J]. 信息网络安全, 2025, 25(10): 1554-1569. |
| [7] | 胡隆辉, 宋虹, 王伟平, 易佳, 张智雄. 大语言模型在安全托管服务误报处理中的应用研究[J]. 信息网络安全, 2025, 25(10): 1570-1578. |
| [8] | 王友贺, 孙奕. 基于CNN-BiLSTM-CBAM的多特征融合恶意PDF文档检测方法[J]. 信息网络安全, 2025, 25(10): 1579-1588. |
| [9] | 张璐, 贾鹏, 刘嘉勇. 基于多元语义图的二进制代码相似性检测方法[J]. 信息网络安全, 2025, 25(10): 1589-1603. |
| [10] | 梁凤梅, 潘正豪, 刘阿建. 基于共性伪造线索感知的物理和数字人脸攻击联合检测方法[J]. 信息网络安全, 2025, 25(10): 1604-1614. |
| [11] | 李涛, 程柏丰. 基于图神经网络的网络资产主动识别技术研究[J]. 信息网络安全, 2025, 25(10): 1615-1626. |
| [12] | 王彦昕, 贾鹏, 范希明, 彭熙. C/C++代码跨形态相似性检测技术研究[J]. 信息网络安全, 2025, 25(10): 1627-1638. |
| [13] | 詹东阳, 黄子龙, 谭凯, 俞兆丰, 贺铮, 张宏莉. 面向Serverless应用的跨函数行为分析与约束技术[J]. 信息网络安全, 2025, 25(9): 1329-1337. |
| [14] | 曹骏, 向尕, 任亚唯, 谭自程, 杨群生. 基于大模型的少样本APT攻击事件抽取方法[J]. 信息网络安全, 2025, 25(9): 1338-1347. |
| [15] | 胡雨翠, 高浩天, 张杰, 于航, 杨斌, 范雪俭. 车联网安全自动化漏洞利用方法研究[J]. 信息网络安全, 2025, 25(9): 1348-1356. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||