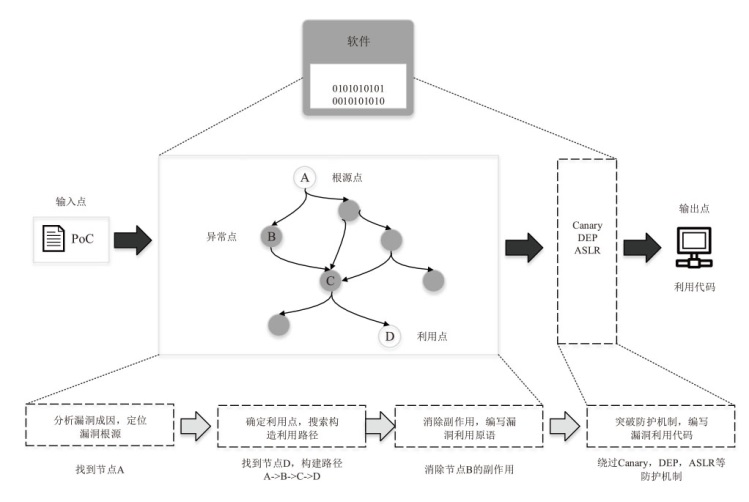
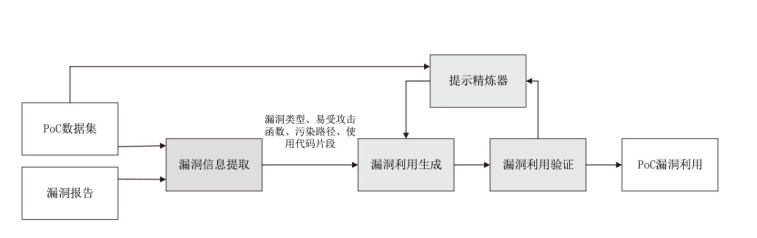
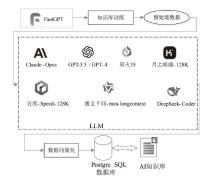
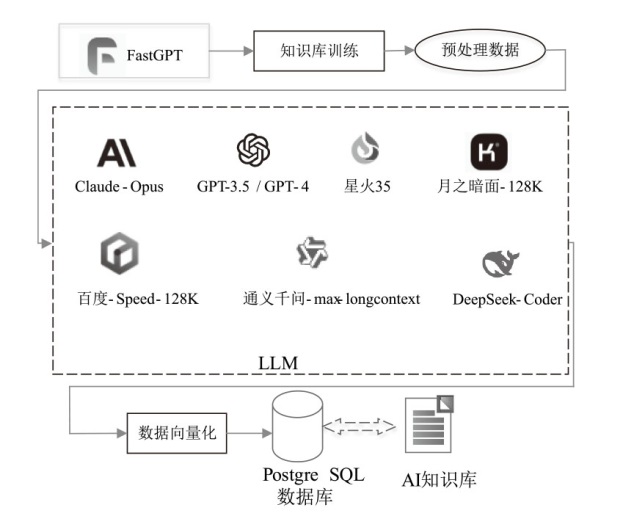
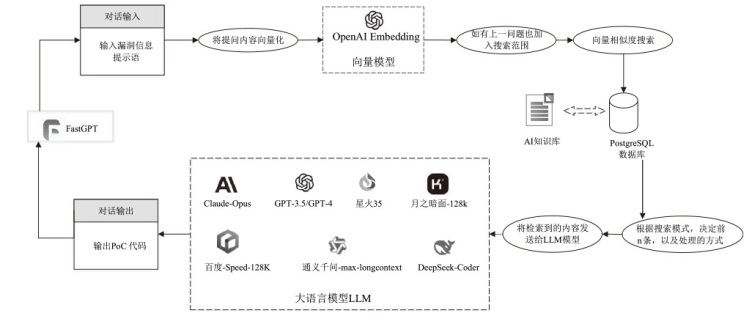
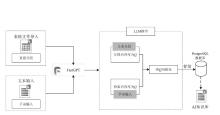
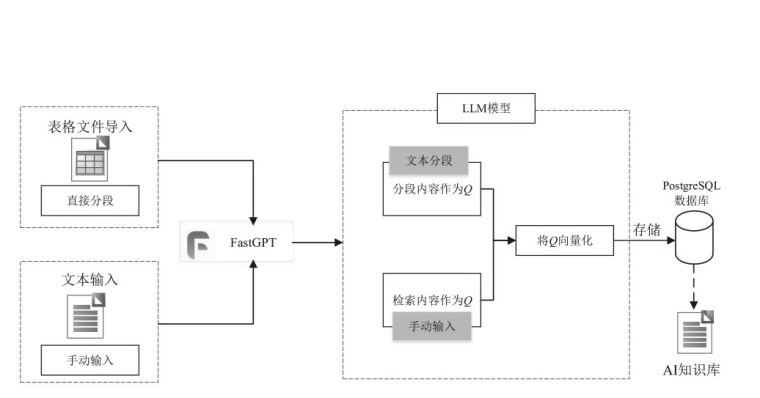
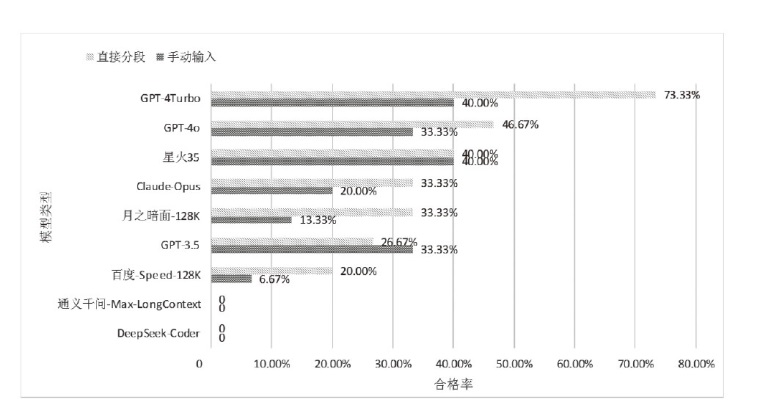
| [1] |
KULSUM U, ZHU Haotian, XU Bowen, et al. A Case Study of LLM for Automated Vulnerability Repair: Assessing Impact of Reasoning and Patch Validation Feedback[EB/OL]. (2024-05-24)[2025-05-25]. https://arxiv.org/abs/2405.15690.
|
| [2] |
WU Zehui, WEI Qiang, WANG Xinlei, et al. Survey of Automatic Software Vulnerability Exploitation[J]. Journal of Computer Research and Development, 2024, 61(9): 2261-2274.
|
|
武泽慧, 魏强, 王新蕾, 等. 软件漏洞自动化利用综述[J]. 计算机研究与发展, 2024, 61(9): 2261-2274.
|
| [3] |
HOUSEHOLDER A D, CHRABASZCZ J, NOVELLY T, et al. Historical Analysis of Exploit Availability Timelines[EB/OL]. (2020-03-25)[2025-05-25]. https://resources.sei.cmu.edu/library/asset-view.cfmassetid=646561.
|
| [4] |
STEENHOEK B, RAHMAN M M, ROY M K, et al. A Comprehensive Study of the Capabilities of Large Language Models for Vulnerability Detection[EB/OL]. (2024-03-26)[2025-05-25]. https://arxiv.org/abs/2403.17218.
|
| [5] |
YANG Yanjing, ZHOU Xin, MAO Runfeng, et al. DLAP: A Deep Learning Augmented Large Language Model Prompting Framework for Software Vulnerability Detection[EB/OL]. (2024-05-02)[2025-05-25]. https://arxiv.org/abs/2405.01202.
|
| [6] |
MATHEWS N S, BRUS Y, AAFER Y, et al. LLbezpeky: Leveraging Large Language Models for Vulnerability Detection[EB/OL]. (2024-01-02)[2025-05-25]. https://arxiv.org/abs/2401.01269.
|
| [7] |
YADMANI S E, THE R, GADYATSKAYA O. Beyond the Surface: Investigating Malicious CVE Proof of Concept Exploits on GitHub[EB/OL]. (2022-10-15)[2025-05-25]. https://arxiv.org/abs/2210.08374.
|
| [8] |
FANG Ruoyu, BINDU R, GUPTA A, et al. Teams of LLM Agents Can Exploit Zero-Day Vulnerabilities[EB/OL]. (2024-06-03)[2025-06-15]. https://arxiv.org/abs/2406.01637.
|
| [9] |
DAO T. FlashAttention-2:Faster Attention with Better Parallelism and Work Partitioning[EB/OL]. (2023-07-17)[2025-05-25]. https://arxiv.org/abs/2307.08691.
|
| [10] |
ZHOU Xingchen, ZHANG Ting, LO D. Large Language Model for Vulnerability Detection: Emerging Results and Future Directions[C]// ACM. The 2024 ACM/IEEE 44th International Conference on Software Engineering:New Ideas and Emerging Results. New York: ACM, 2024: 47-51.
|
| [11] |
FANG Ruoyu, BINDU R, GUPTA A, et al. LLM Agents Can Autonomously Exploit One-Day Vulnerabilities[EB/OL]. (2024-04-11)[2025-05-25]. https://arxiv.org/abs/2404.08144.
|
| [12] |
LI Ziyang, DUTTA S, NAIK M. LLM-Assisted Static Analysis for Detecting Security Vulnerabilities[EB/OL]. (2024-05-27)[2025-05-25]. https://arxiv.org/abs/2405.17238.
|
| [13] |
GONG Bingjiang, TANG Yujing. Research on Software Security Vulnerability Mining Methods on Android Platform[D]. Beijing: Beijing University of Posts and Telecommunications, 2014.
|
|
龚炳江, 唐宇敬. Android平台下软件安全漏洞挖掘方法研究[D]. 北京: 北京邮电大学, 2014.
|
| [14] |
ZHOU Xingchen, CAO Shen, SUN Xiang, et al. Large Language Model for Vulnerability Detection and Repair: Literature Review and Roadmap[EB/OL]. (2024-04-03)[2025-05-25]. https://arxiv.org/abs/2404.02525.
|
| [15] |
LIU Bo, WEN Weiping, SUN Huiping, et al. ClearBug: An Improved Tool for Automatic Vulnerability Analysis[J]. Netinfo Security, 2009, 9(5): 28-31.
|
|
刘波, 文伟平, 孙惠平, 等. ClearBug 一种改进的自动化漏洞分析工具[J]. 信息网络安全, 2009, 9(5): 28-31.
|
| [16] |
LIU Fanwen, HU Cheng. Exploring Vulnerabilities and Protections in Large Language Models: A Survey[EB/OL]. (2024-05-31)[2025-05-25]. https://arxiv.org/abs/2406.00240.
|
 ), GAO Haotian, ZHANG Jie, YU Hang, YANG Bin, FAN Xuejian
), GAO Haotian, ZHANG Jie, YU Hang, YANG Bin, FAN Xuejian