信息网络安全 ›› 2025, Vol. 25 ›› Issue (1): 13-26.doi: 10.3969/j.issn.1671-1122.2025.01.002
基于PUF的电力物联网智能终端认证协议
- 1.北京电子科技学院密码科学与技术系,北京 100070
2.中国星网网络系统研究院有限公司,北京 100029
3.国网信息通信产业集团有限公司,北京 100031
-
收稿日期:2024-07-11出版日期:2025-01-10发布日期:2025-02-14 -
通讯作者:袁征 E-mail:sxzyyz5318@163.com -
作者简介:袁征(1968—),女,山西,教授,博士,主要研究方向为密码设计、密码分析、区块链、隐私保护和密码设备应用|张跃飞 (2000—),男,河北,硕士研究生,主要研究方向为密码学、信息安全|冯笑(1989—),女,山西,高级工程师,博士,主要研究方向为信息安全|乔雅馨(2000—),女,河北,硕士研究生,主要研究方向为密码学、信息安全 -
基金资助:国家密码发展基金(MMJJ20180217);国家电网有限公司总部科技项目(5700-202341290A-1-1-ZN)
PUF-Based Smart Terminal Authentication Protocol for Power Internet of Things
YUAN Zheng1,2( ), ZHANG Yuefei1, FENG Xiao3, QIAO Yaxin1
), ZHANG Yuefei1, FENG Xiao3, QIAO Yaxin1
- 1. Department of Cryptography Science and Technology, Beijing Institute of Electronic Science and Technology, Beijing 100070, China
2. China StarNet Network System Research Institute Co., Ltd., Beijing 100029, China
3. State Grid Information & Telecommunication Industry Co., Ltd., Beijing 100031, China
-
Received:2024-07-11Online:2025-01-10Published:2025-02-14 -
Contact:YUAN Zheng E-mail:sxzyyz5318@163.com
摘要:
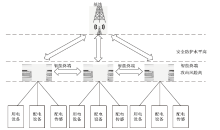
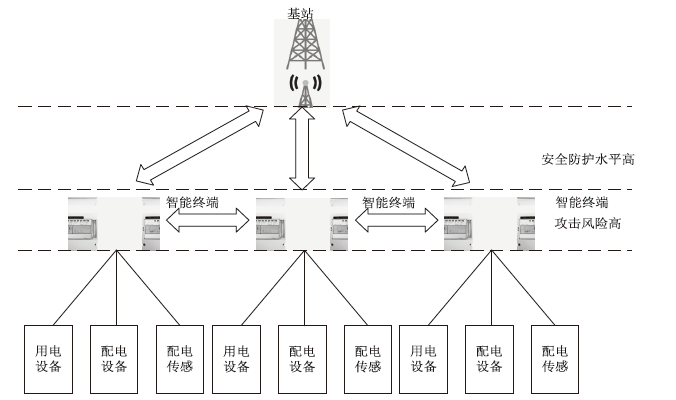
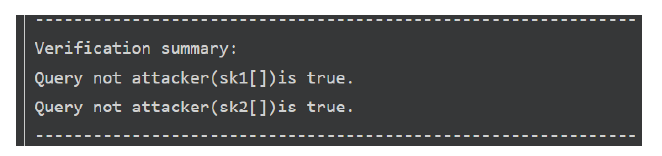
电力系统逐步向智能化和数字化转型,越来越多的终端设备通过物联网技术实现互联和数据共享,但由于设备多样性、资源受限、通信环境复杂、物理分布广泛等特点以及高实时性需求,电力物联网智能终端安全验证在密码破解、仿冒攻击和复杂性等方面面临严峻的挑战。为应对电力物联网智能终端在通信中的认证安全性挑战,引入PUF技术并设计扩展CRP结构,提出一种基于物理不可克隆函数(PUF)的电力物联网智能终端认证协议。使用ProVerif工具和Tamarin工具进行模拟实验,证明该协议能够有效抵御常见攻击,如中间人攻击和仿冒攻击等,对轻量级和双向认证等协议特征进行理论分析,并与相似方案进行比较,结果显示该方案在多方面具有显著优势。该研究为电力物联网智能终端的安全认证提供了一种高效的解决方案,不仅弥补了传统认证方案的不足,还为未来的电力物联网系统提供更为安全可靠的技术基础,有助于提升电力系统的整体安全水平和运行效率。
中图分类号:
引用本文
袁征, 张跃飞, 冯笑, 乔雅馨. 基于PUF的电力物联网智能终端认证协议[J]. 信息网络安全, 2025, 25(1): 13-26.
YUAN Zheng, ZHANG Yuefei, FENG Xiao, QIAO Yaxin. PUF-Based Smart Terminal Authentication Protocol for Power Internet of Things[J]. Netinfo Security, 2025, 25(1): 13-26.
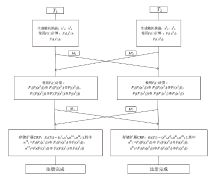
表1
符号及其含义
| 符号 | 描述 |
|---|---|
| Ti | 智能终端i |
| idi | 智能终端i身份标识号 |
| xis | 智能终端i生成的第s个挑战x |
| αijs | 智能终端i用于验证智能终端j的真实性的第s个模糊响应α |
| βijs | 智能终端j用来向智能终端i证明其真实性的第s个模糊响应β |
| Fi(·) | 智能终端i的PUF函数 |
| Fi(xis) | 智能终端i的PUF函数对智能终端i生成的第s个挑战x的响应 |
| H(·) | 一个公共散列函数 |
| H(*) | 用于保护消息M完整性的散列 |
| ⊕ | 异或运算符 |
| Ei(Tj) | 智能终端i用于挑战和验证智能终端j的真实性的扩展CRP |
| Ni | 智能终端i生成的随机数 |
| Nij | Ni和Nj的异或,即Ni⊕Nj |
| i|j | i或者j,两者其中的一个 |
| K | 加解密密钥 |
| [1] | LIANG Xiaolin, SUN Donglei, LI Wensheng. Composition Form and Function Configuration of Intelligent Terminal Based on Edge Computing for Power Internet of Things[C]// The Organizing Committee of the International Conference on Renewable Energy and Environmental Protection. 2020 5th International Conference on Renewable Energy and Environmental Protection (ICREEP2020). Bristol: IOP, 2021: 1-7. |
| [2] | ZOU Zhenwan, LI Feng, HOU Yingsa, et al. Research on Security Protection Technology of Intelligent Terminal of Electricity Internet of Things[C]// IEEE. 2021 IEEE 5th Information Technology, Networking, Electronic and Automation Control Conference (ITNEC). New York: IEEE, 2021: 1467-1470. |
| [3] | GAO Yansong, Al-SARAWI S F, ABBOTT D. Physical Unclonable Functions[J]. Nature Electronics, 2020, 3(2): 81-91. |
| [4] |
PAPPU R, RECHT B, TAYLOR J, et al. Physical One-Way Functions[J]. Science, 2002, 297(5589): 2026-2030.
pmid: 12242435 |
| [5] | LIU Dan, GUO Limin, YU Jun, et al. A Safe Two-Way Certification Agreement Based on SRAM PUF[J]. Code Journal, 2017, 4(4): 360-371. |
|
刘丹, 郭丽敏, 俞军, 等. 一种基于SRAM PUF的安全双向认证协议[J]. 密码学报, 2017, 4(4):360-371.
doi: 10.13868/j.cnki.jcr.000188 |
|
| [6] | SHAMSOSHOARA A, KORENDA A, AFGHAH F, et al. A Survey on Physical Unclonable Function (PUF)-Based Security Solutions for Internet of Things[EB/OL]. (2020-12-24)[2024-05-08]. https://www.sciencedirect.com/science/article/pii/S1389128620312275. |
| [7] | YOON S, KIM B, KANG Y, et al. Puf-Based Authentication Scheme for Iot Devices[C]// IEEE. 2020 International Conference on Information and Communication Technology Convergence (ICTC). New York: IEEE, 2020: 1792-1794. |
| [8] | GHAFI B K, MAYBODI B M N. A Distributed PUF-Based Mutual Authentication System with Self-Correction[C]// IEEE. 2020 28th Iranian Conference on Electrical Engineering (ICEE). New York: IEEE, 2020: 1-5. |
| [9] | QURESHI M A, MUNIR A. PUF-RAKE: A PUF-Based Robust and Lightweight Authentication and Key Establishment Protocol[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 19(4): 2457-2475. |
| [10] | ZHENG Yue, CHANG C H. Secure Mutual Authentication and Key-Exchange Protocol Between PUF-Embedded IoT Endpoints[C]// IEEE. 2021 IEEE International Symposium on Circuits and Systems (ISCAS). New York: IEEE, 2021: 1-5. |
| [11] | GUO Xuan. The Company Has Issued the Opinion on Comprehen Sively Deepening Reform and Striving for Breakthroughs[N]. State Grid Corporation of China, 2020-01-14( 2). |
| 郭萱. 公司印发《关于全面深化改革奋力攻坚突破的意见》[N]. 国家电网报, 2020-01-14(2). | |
| [12] | HE Fenglu, CHEN Jiaqi, LI Qinhao, et al. The Internet of Things Technology in the Smart Grid[J]. Power System Protection and Control, 2020, 48(3): 58-69. |
| 何奉禄, 陈佳琦, 李钦豪, 等. 智能电网中的物联网技术应用与发展[J]. 电力系统保护与控制, 2020, 48(3):58-69. | |
| [13] |
DONGSHENG Y, DAOHAO W, BOWEN Z, et al. Key Technologies and Application Prospects of Ubiquitous Power Internet of Things[J]. Power Generation Technology, 2019, 40(2): 107-114.
doi: 10.12096/j.2096-4528.pgt.19061 |
| [14] | National Energy Administration. Notice from the National Energy Administration on Issuing the “Action Plan for Electricity Safety Production (2018-2020)”: National Energy Development Safety[2018] No. 55[EB/OL]. (2018-06-27)[2024-05-09]. https://zfxxgk.nea.gov.cn/auto93/201807/t20180705_3206.htm. |
| 国家能源局. 国家能源局关于印发《电力安全生产行动计划(2018-2020年)》的通知:国能发安全[2018]55号[EB/OL]. (2018-06-27)[2024-05-09]. https://zfxxgk.nea.gov.cn/auto93/201807/t20180705_3206.htm. | |
| [15] | TAN Weijie, YANG Yuting, NIU Kun, et al. MI-PUF-Based V2X Vehicle Networking Communication Security Certification Agreement[J]. Information Network Security, 2023, 23(12): 38-48. |
| 谭伟杰, 杨雨婷, 牛坤, 等. 基于MI-PUF的V2X车联网通信安全认证协议[J]. 信息网络安全, 2023, 23(12):38-48. | |
| [16] | SHAMIR A. How to Share A Secret[J]. Communications of the ACM, 1979, 22(11): 612-613. |
| [17] | YANAMBAKA V P, MOHANTY S P, KOUGIANOS E, et al. PMsec: Physical Unclonable Function-Based Robust and Lightweight Authentication in the Internet of Medical Things[J]. IEEE Transactions on Consumer Electronics, 2019, 65(3): 388-397. |
| [18] | DIJK M V, RÜHRMAIR U. Protocol Attacks on Advanced PUF Protocols and Countermeasures[C]// IEEE. 2014 Design, Automation & Test in Europe Conference & Exhibition (DATE). New York: IEEE, 2014: 1-6. |
| [19] | PANDYA D, NARAYAN K R, THAKKAR S, et al. An Overview of Various Authentication Methods and Protocols[J]. International Journal of Computer Applications, 2015, 131(9): 25-27. |
| [20] | KHALAFALLA M, GEBOTYS C. PUFs Deep Attacks: Enhanced Modeling Attacks Using Deep Learning Techniques to Break the Security of Double Arbiter PUFs[C]// IEEE. 2019 Design, Automation & Test in Europe Conference & Exhibition (DATE). New York: IEEE, 2019: 204-209. |
| [21] | BOYD C, GELLERT K. A Modern View on Forward Security[J]. The Computer Journal, 2021, 64(4): 639-652. |
| [22] | YANG Ting, ZHAI Feng, ZHAO Yingjie, et al. Definition and Research Prospects of Ubiquitous Power Internet of Things[J]. Power System Automation, 2019, 43 (13): 9-20, 53. |
| 杨挺, 翟峰, 赵英杰, 等. 泛在电力物联网释义与研究展望[J]. 电力系统自动化, 2019, 43(13): 9-20,53. | |
| [23] | GOPE P. PMAKE: Privacy-Aware Multi-Factor Authenticated Key Establishment Scheme for Advancemetering Infrastructure in Smart Grid[J]. Computer Communications, 2020, 152: 338-344. |
| [24] | AYSU A, GULCAN E, MORIYAMA D, et al. End-to-End Design of a PUF-Based Privacy Preserving Authentication Protocol[C]// Springer. Cryptographic Hardware and Embedded Systems-CHES 2015: 17th International Workshop. Heidelberg: Springer, 2015: 556-576. |
| [1] | 夏喆, 夏学志, 吕文杰, 张明武. 车联网中基于证书的局部可验证聚合签名方案[J]. 信息网络安全, 2025, 25(1): 48-62. |
| [2] | 段昊哲, 李志慧, 韦性佳, 胡珂欣. d维量子系统中无需纠缠的量子身份认证协议[J]. 信息网络安全, 2024, 24(9): 1364-1374. |
| [3] | 黄旺旺, 周骅, 王代强, 赵麒. 基于国密SM9的物联网可重构密钥安全认证协议设计[J]. 信息网络安全, 2024, 24(7): 1006-1014. |
| [4] | 沈卓炜, 汪仁博, 孙贤军. 基于Merkle树和哈希链的层次化轻量认证方案[J]. 信息网络安全, 2024, 24(5): 709-718. |
| [5] | 翟鹏, 何泾沙, 张昱. 物联网环境下基于SM9算法和区块链技术的身份认证方法[J]. 信息网络安全, 2024, 24(2): 179-187. |
| [6] | 陈宝刚, 张毅, 晏松. 民航空管信息系统用户多因子持续身份可信认证方法研究[J]. 信息网络安全, 2024, 24(11): 1632-1642. |
| [7] | 谭伟杰, 杨雨婷, 牛坤, 彭长根. 基于MI-PUF的V2X车联网通信安全认证协议[J]. 信息网络安全, 2023, 23(12): 38-48. |
| [8] | 张敏, 许春香, 张建华. 无人机网络中基于多因子的认证密钥协商协议研究[J]. 信息网络安全, 2022, 22(9): 21-30. |
| [9] | 王姝爽, 马兆丰, 刘嘉微, 罗守山. 区块链跨链安全接入与身份认证方案研究与实现[J]. 信息网络安全, 2022, 22(6): 61-72. |
| [10] | 李莉, 李泽群, 李雪梅, 史国振. 基于交叉耦合电路的物理不可克隆函数FPGA实现[J]. 信息网络安全, 2022, 22(3): 53-61. |
| [11] | 吴克河, 程瑞, 姜啸晨, 张继宇. 基于SDP的电力物联网安全防护方案[J]. 信息网络安全, 2022, 22(2): 32-38. |
| [12] | 张昱, 孙光民, 翟鹏, 李煜. 一种基于切比雪夫混沌映射的可证明安全的溯源认证协议[J]. 信息网络安全, 2022, 22(12): 25-33. |
| [13] | 吴克河, 程瑞, 郑碧煌, 崔文超. 电力物联网安全通信协议研究[J]. 信息网络安全, 2021, 21(9): 8-15. |
| [14] | 沈卓炜, 高鹏, 许心宇. 基于安全协商的DDS安全通信中间件设计[J]. 信息网络安全, 2021, 21(6): 19-25. |
| [15] | 张昱, 孙光民, 李煜. 基于SM9算法的移动互联网身份认证方案研究[J]. 信息网络安全, 2021, 21(4): 1-9. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||