信息网络安全 ›› 2024, Vol. 24 ›› Issue (7): 1038-1049.doi: 10.3969/j.issn.1671-1122.2024.07.006
一种基于函数依赖的跨合约模糊测试方案
- 1.武汉大学国家网络安全学院,武汉 430072
2.武汉大学空天信息安全与可信计算教育部重点实验室,武汉 430072
-
收稿日期:2023-03-09出版日期:2024-07-10发布日期:2024-08-02 -
通讯作者:严飞yanfei@whu.edu.cn -
作者简介:张立强(1979—),男,黑龙江,副教授,博士,CCF会员,主要研究方向为系统安全和安全测评|路梦君(1998—),女,山东,硕士研究生,主要研究方向为系统安全、区块链和智能合约|严飞(1980—),男,湖北,副教授,博士,CCF会员,主要研究方向为系统安全和可信计算。 -
基金资助:湖北省重点研发计划(2021BAA027)
A Cross-Contract Fuzzing Scheme Based on Function Dependencies
ZHANG Liqiang1,2, LU Mengjun1,2, YAN Fei1,2( )
)
- 1. School of Cyber Science and Engineering, Wuhan University, Wuhan 430072, China
2. Key Laboratory of Aerospace Information Security and Trusted Computing of Ministry of Education, Wuhan University, Wuhan 430072, China
-
Received:2023-03-09Online:2024-07-10Published:2024-08-02
摘要:
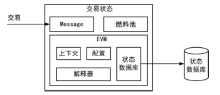
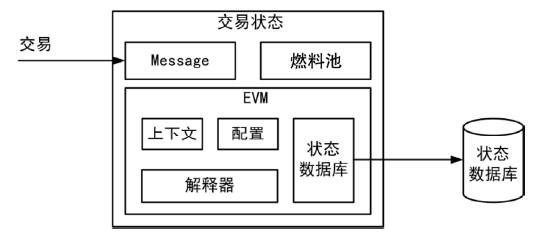
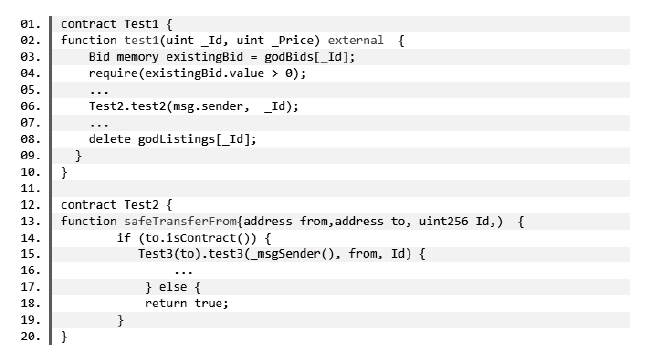
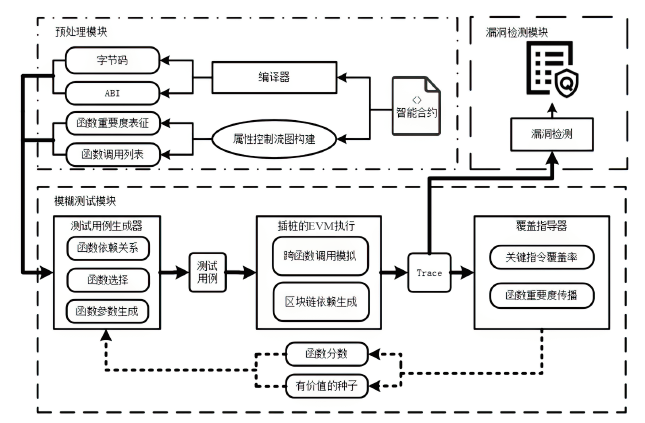
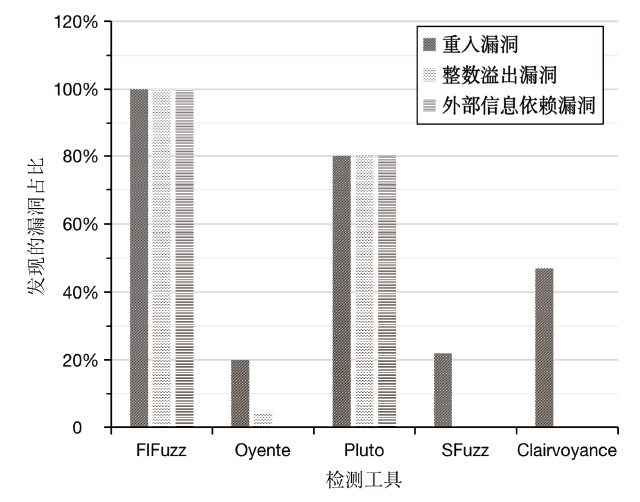
随着区块链应用的快速发展和智能合约的广泛使用,由智能合约引发的安全事件急剧增多,导致基于区块链的数字资产产生了巨大损失。目前,虽然部分工具可以检测智能合约安全漏洞,但是它们主要针对单个智能合约进行检测,未考虑跨合约之间的交互依赖关系,因此会产生较多的误报。针对上述智能合约漏洞检测工具在跨合约场景下误报率较高和性能消耗过大的问题,文章提出一种基于函数依赖的跨合约模糊测试方案FIFuzz。该方案提出ContractRank算法进行合约间依赖关系建模,采用函数重要度来表征函数在合约间交互过程中的重要程度,并在后续模糊测试模块中加以利用。模糊测试通过基于函数重要度的交易序列生成策略和基于合约地址映射关系的地址类型数据生成策略来提高检测效率,缩减跨合约漏洞检测的搜索空间。另外,通过合约调用模拟来降低漏洞检测的假阳性率。与相关工具的对比实验表明,FIFuzz的漏洞检测时间相对其他工具缩短了80%,检测到的漏洞数量是其他工具的两倍,检测跨合约漏洞的准确率也明显高于其他工具。实验结果表明,FIFuzz能够有效提升跨合约漏洞的检测准确率,降低误报率,并减小时间开销。
中图分类号:
引用本文
张立强, 路梦君, 严飞. 一种基于函数依赖的跨合约模糊测试方案[J]. 信息网络安全, 2024, 24(7): 1038-1049.
ZHANG Liqiang, LU Mengjun, YAN Fei. A Cross-Contract Fuzzing Scheme Based on Function Dependencies[J]. Netinfo Security, 2024, 24(7): 1038-1049.
| [1] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. (2008-10-31)[2023-03-07]. https://www.researchgate.net/publication/228640975_Bitcoin_A_Peer-to-Peer_Electronic_Cash_System. |
| [2] | UNDERWOOD S. Blockchain beyond Bitcoin[J]. Communications of the ACM, 2016, 59(11): 15-17. |
| [3] | LI Dongcheng, WONG W E, PAN S, et al. Design Principles and Best Practices of Central Bank Digital Currency[J]. International Journal of Performability Engineering, 2021, 17(5): 411-421. |
| [4] |
TIAN Zhihong, LI Mohan, QIU Meikang, et al. Block-DEF: A Secure Digital Evidence Framework Using Blockchain[J]. Information Sciences, 2019, 491: 151-165.
doi: 10.1016/j.ins.2019.04.011 |
| [5] | WOOD G. Ethereum: A Secure Decentralised Generalised Transaction Ledger[J]. Ethereum Project Yellow Paper, 2014, 151: 1-32. |
| [6] | NICK S. The Idea of Smart Contracts[EB/OL]. (1997-10-31)[2023-03-07]. http://www.fon.hum.uva.nl/rob/Courses/InformationInSpeech/CDROM/Literature/LOTwinterschool2006/szabo.best.vwh.net/idea.html. |
| [7] | Bitinfocharts. Ethereum Daily Transaction Chart[EB/OL]. (2023-02-16)[2023-03-07]. https://etherscan.io/chart/tx. |
| [8] | Secbit. A Disastrous Vulnerability Found in Smart Contracts of Beautychain(BEC)[ EB/OL]. (2022-08-11)[2023-03-07]. https://medium.com/secbit-media/a-disastrous-vulnerability-found-in-smart-contracts-of-beautychain-bec-dbf24ddbc30e. |
| [9] | YU Xiaoliang, AL-BATAINEH O, LO D, et al. Smart Contract Repair[J]. ACM Transactions on Software Engineering and Methodology (TOSEM), 2020, 29(4): 1-32. |
| [10] | LEE S. Blockchain Smart Contracts: More Trouble than They are Worth?[EB/OL]. (2018-07-10)[2023-03-07]. https://www.forbes.com/sites/shermanlee/2018/07/10/blockchain-smart-contracts-more-trouble-than-they-are-worth/493735e623a6. |
| [11] | CHANG S. Ethereum Smart Contracts Vulnerable to Hacks: $4 Million in Ether at Risk[EB/OL]. (2019-06-25)[2023-03-07]. https://www.investopedia.com/news/ethereum-smart-contracts-vulnerable-hacks\-4-million-ether-risk/. |
| [12] | LUU L, CHU D H, OLICKEL H, et al. Making Smart Contracts Smarter[C]// ACM. The 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 254-269. |
| [13] | RAZA A. The Binance KYC Data Breach: The Hacker Confirms the Attack[EB/OL]. (2019-03-29)[2023-03-07]. https://cryptopotato.com/the-binance-kyc-data-breach-the-hacker-confirms-the-attack/. |
| [14] | ZHENG G, GAO Longxiang, HUANG Liqun, et al. Upgradable Contract[M]. Heidelberg: Springer, 2021. |
| [15] | LI Wenkai, BU Jiuyang, LI Xiaoqi, et al. A Survey of DeFi Security: Challenges and Opportunities[J]. Journal of King Saud University-Computer and Information Sciences, 2022, 34(10): 10378-10404. |
| [16] | MCKAY J. DeFi-ing Cyber Attacks[EB/OL]. (2022-04-27)[2023-03-07]. https://tellingstorieswithdata.com/inputs/pdfs/final_paper-2022-jack_mckay. pdf. |
| [17] | NIKOLIĆ I, KOLLURI A, SERGEY I, et al. Finding the Greedy, Prodigal, and Suicidal Contracts at Scale[C]// ACM. The 34th Annual Computer Security Applications Conference. New York: ACM, 2018: 653-663. |
| [18] | JIANG Bo, LIU Ye, CHAN W K. ContractFuzzer: Fuzzing Smart Contracts for Vulnerability Detection[C]// IEEE. 2018 33rd IEEE/ACM International Conference on Automated Software Engineering (ASE). New York: IEEE, 2018: 259-269. |
| [19] | NGUYEN T D, PHAM L H, SUN Jun, et al. SFuzz: An Efficient Adaptive Fuzzer for Solidity Smart Contracts[C]// ACM. Proceedings of the ACM/IEEE 42nd International Conference on Software Engineering. New York: ACM, 2020: 778-788. |
| [20] | HE Jingxuan, BALUNOVIĆ M, AMBROLADZE N, et al. Learning to Fuzz from Symbolic Execution with Application to Smart Contracts[C]// ACM. The 2019 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2019: 531-548. |
| [21] | TSANKOV P, DAN A, DRACHSLER-COHEN D, et al. Securify: Practical Security Analysis of Smart Contracts[C]// ACM. The 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 67-82. |
| [22] | GRECH N, KONG M, JURISEVIC A, et al. MadMax: Surviving Out-of-Gas Conditions in Ethereum Smart Contracts[J]. Proceedings of the ACM on Programming Languages, 2018, 116(2): 1-27. |
| [23] | XUE Yinxing, MA Mingliang, LIN Yun, et al. Cross-Contract Static Analysis for Detecting Practical Reentrancy Vulnerabilities in Smart Contracts[C]// ACM. The 35th IEEE/ACM International Conference on Automated Software Engineering. New York: ACM, 2020: 1029-1040. |
| [24] | MA Fuchen, XU Zhenyang, REN Meng, et al. Pluto: Exposing Vulnerabilities in Inter-Contract Scenarios[J]. IEEE Transactions on Software Engineering, 2022, 48(11): 4380-4396. |
| [25] | LIAO Zeqin, ZHENG Zibin, CHEN Xiao, et al. SmartDagger: A Bytecode-Based Static Analysis Approach for Detecting Cross-Contract Vulnerability[C]// ACM. The 31st ACM SIGSOFT International Symposium on Software Testing and Analysis. New York: ACM, 2022: 752-764. |
| [26] | XIONG Wei, XIONG Li. Smart Contract Based Data Trading Mode Using Blockchain and Machine Learning[J]. IEEE Access, 2019, 7: 102331-102344. |
| [27] | XU Guangxia, HU Mengxiao, MA Chuang. Secure and Smart Autonomous Multi-Robot Systems for Opinion Spammer Detection[J]. Information Sciences, 2021, 576: 681-693. |
| [28] | PAGE L, BRIN S, MOTWANI R, et al. The PageRank Citation Ranking: Bringing Order to the Web[EB/OL]. (1999-11-11)[2023-03-07]. https://xueshu.baidu.com/usercenter/paper/show?paperid=189f33f55815fd274b89c7f425e3452e&site=xueshu_se. |
| [29] | FEIST J, GRIECO G, GROCE A. Slither: A Static Analysis Framework for Smart Contracts[C]// IEEE. 2019 IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB). New York: IEEE, 2019: 8-15. |
| [30] | MICHAL Z. American Fuzzy Lop (AFL)[EB/OL]. (2018-04-17)[2023-03-07]. http://lcamtuf.coredump.cx/afl/. |
| [31] | STEPHENS N, GROSEN J, SALLS C, et al. Driller: Augmenting Fuzzing through Selective Symbolic Execution[EB/OL]. (2016-02-21)[2023-03-07]. https://www.researchgate.net/publication/316906731_Driller_Augmenting_Fuzzing_Through_Selective_Symbolic_Execution. |
| [32] | GRIECO G, SONG W, CYGAN A, et al. Echidna: Effective, Usable, and Fast Fuzzing for Smart Contracts[C]// ACM. The 29th ACM SIGSOFT International Symposium on Software Testing and Analysis. New York: ACM, 2020: 557-560. |
| [33] | MUELLER B. Mythril-Reversing and Bug Hunting Framework for the Ethereum Blockchain[EB/OL]. (2022-11-03)[2023-03-07]. https://pypi.org/project/mythril/0.8.2/. |
| [34] | TIKHOMIROV S, VOSKRESENSKAYA E, IVANITSKIY I, et al. SmartCheck: Static Analysis of Ethereum Smart Contracts[C]// IEEE. 2018 IEEE/ACM 1st International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB). New York: IEEE, 2018: 9-16. |
| [35] | XU Guangxia, WU Xinkai, LIU Jun, et al. A Community Detection Method Based on Local Optimization in Social Networks[J]. IEEE Network, 2020, 34(4): 42-48. |
| [1] | 刘峰, 江佳齐, 黄灏. 面向加密货币交易介质及过程的安全综述[J]. 信息网络安全, 2024, 24(3): 330-351. |
| [2] | 王鹃, 龚家新, 蔺子卿, 张晓娟. 多维深度导向的Java Web模糊测试方法[J]. 信息网络安全, 2024, 24(2): 282-292. |
| [3] | 洪玄泉, 贾鹏, 刘嘉勇. AFLNeTrans:状态间关系感知的网络协议模糊测试[J]. 信息网络安全, 2024, 24(1): 121-132. |
| [4] | 王鹃, 张冲, 龚家新, 李俊娥. 基于机器学习的模糊测试研究综述[J]. 信息网络安全, 2023, 23(8): 1-16. |
| [5] | 覃思航, 代炜琦, 曾海燕, 顾显俊. 基于区块链的电力应用数据安全共享研究[J]. 信息网络安全, 2023, 23(8): 52-65. |
| [6] | 钟远鑫, 刘嘉勇, 贾鹏. 基于动态时间切片和高效变异的定向模糊测试[J]. 信息网络安全, 2023, 23(8): 99-108. |
| [7] | 李春晓, 王耀飞, 徐恩亮, 赵钰. 基于双线性映射的区块链安全范围搜索技术研究[J]. 信息网络安全, 2023, 23(3): 22-34. |
| [8] | 张光华, 刘永升, 王鹤, 于乃文. 基于BiLSTM和注意力机制的智能合约漏洞检测方案[J]. 信息网络安全, 2022, 22(9): 46-54. |
| [9] | 张玉健, 刘代富, 童飞. 基于局部图匹配的智能合约重入漏洞检测方法[J]. 信息网络安全, 2022, 22(8): 1-7. |
| [10] | 胡艺, 佘堃. 基于区块链和智能合约的双链车联网系统[J]. 信息网络安全, 2022, 22(8): 26-35. |
| [11] | 王健, 黄俊. 基于智能合约的日志安全存储与公平访问方法[J]. 信息网络安全, 2022, 22(7): 27-36. |
| [12] | 于克辰, 郭莉, 阴宏伟, 燕雪松. 面向数据中心场景的基于区块链与博弈论的高价值数据共享模型[J]. 信息网络安全, 2022, 22(6): 73-85. |
| [13] | 华景煜, 黄达明. 以太坊智能合约定理证明中的形式化规约研究综述[J]. 信息网络安全, 2022, 22(5): 11-20. |
| [14] | 冯景瑜, 张琪, 黄文华, 韩刚. 基于跨链交互的网络安全威胁情报共享方案[J]. 信息网络安全, 2022, 22(5): 21-29. |
| [15] | 李鹏, 郑田甜, 徐鹤, 朱枫. 基于区块链技术的RFID安全认证协议[J]. 信息网络安全, 2021, 21(5): 1-11. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||