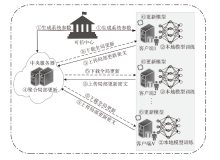
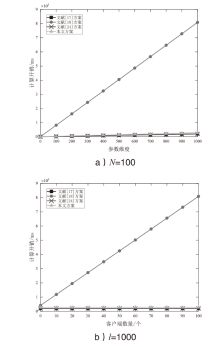
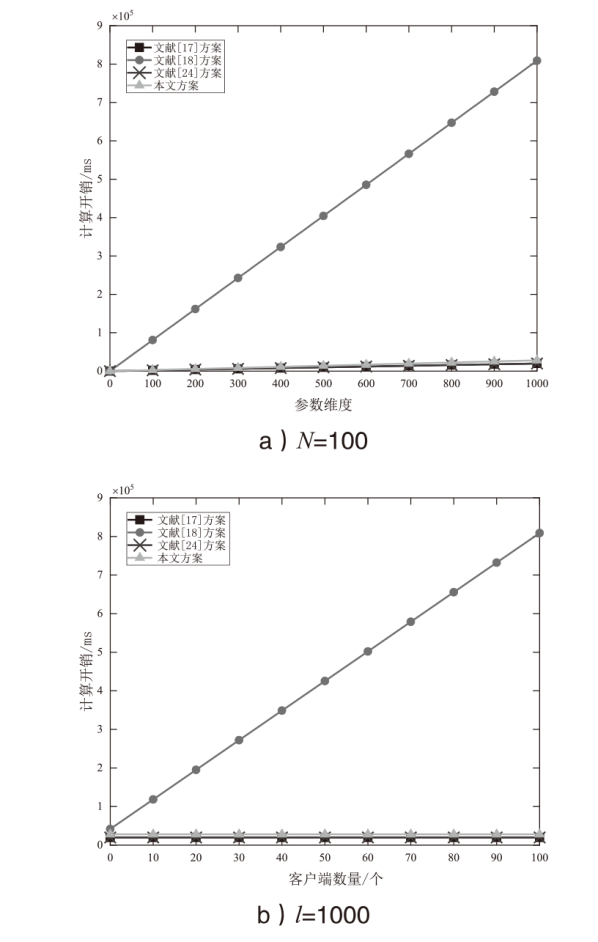
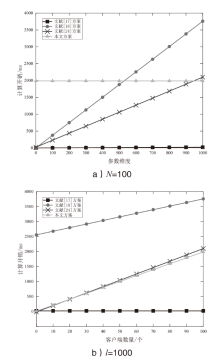
信息网络安全 ›› 2024, Vol. 24 ›› Issue (1): 93-105.doi: 10.3969/j.issn.1671-1122.2024.01.009
基于同态加密的隐私保护与可验证联邦学习方案
- 西安邮电大学网络空间安全学院,西安 710121
-
收稿日期:2023-07-16出版日期:2024-01-10发布日期:2024-01-24 -
通讯作者:赖成喆 E-mail:lcz_xupt@163.com -
作者简介:赖成喆(1985—),男,陕西,教授,博士,CCF会员,主要研究方向为无线网络安全、应用密码学|赵益宁(1998—),女,陕西,硕士研究生,主要研究方向为隐私计算、信息安全|郑东(1964—),男,山西,教授,博士,主要研究方向为编码密码学和网络安全 -
基金资助:国家自然科学基金(62072371);陕西省重点研发计划(2021ZDLGY06-02)
A Privacy Preserving and Verifiable Federated Learning Scheme Based on Homomorphic Encryption
LAI Chengzhe( ), ZHAO Yining, ZHENG Dong
), ZHAO Yining, ZHENG Dong
- School of Cyberspace Security, Xi’an University of Posts and Telecommunications, Xi’an 710121, China
-
Received:2023-07-16Online:2024-01-10Published:2024-01-24 -
Contact:LAI Chengzhe E-mail:lcz_xupt@163.com
摘要:
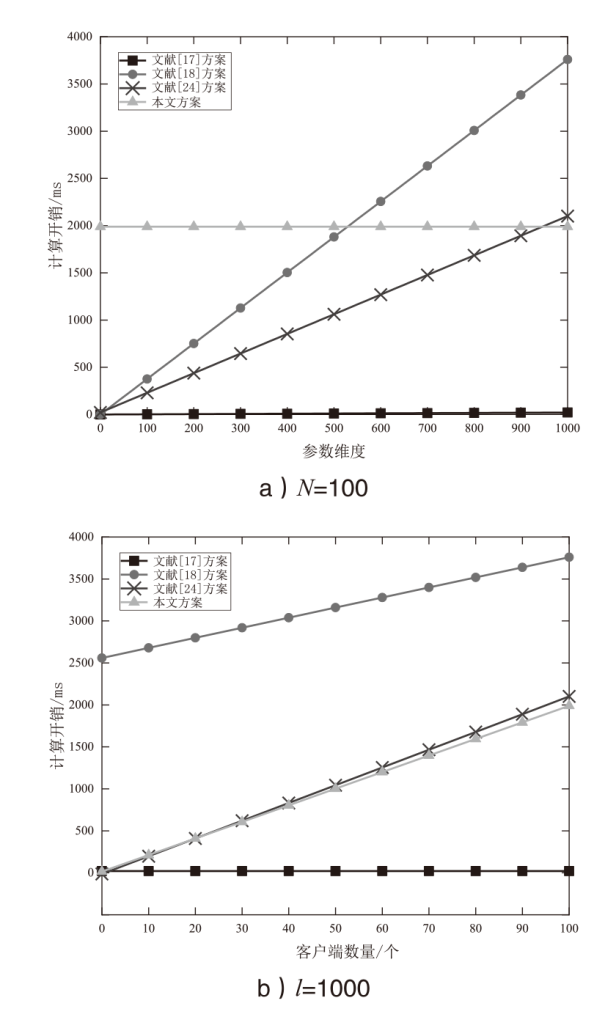
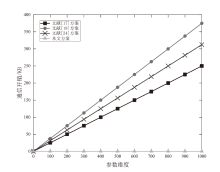
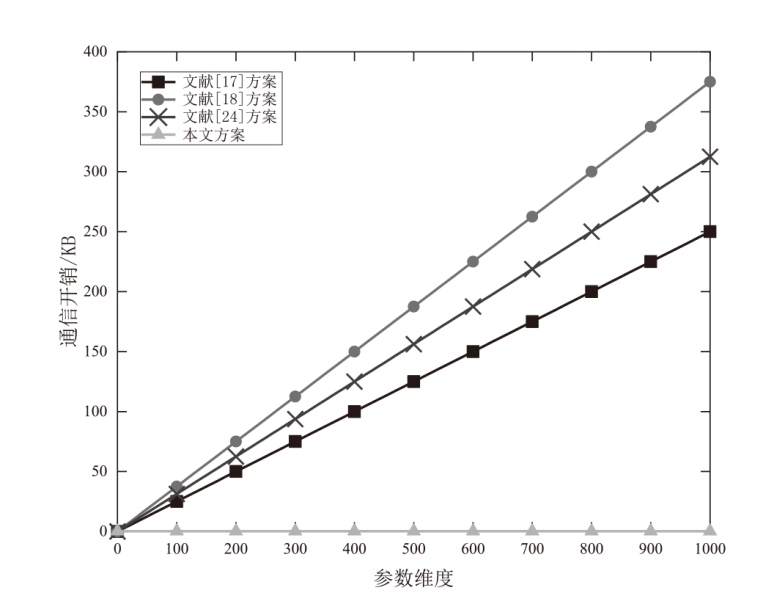
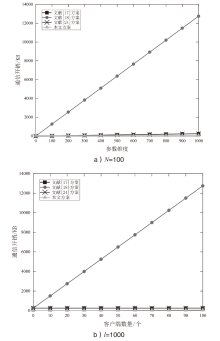
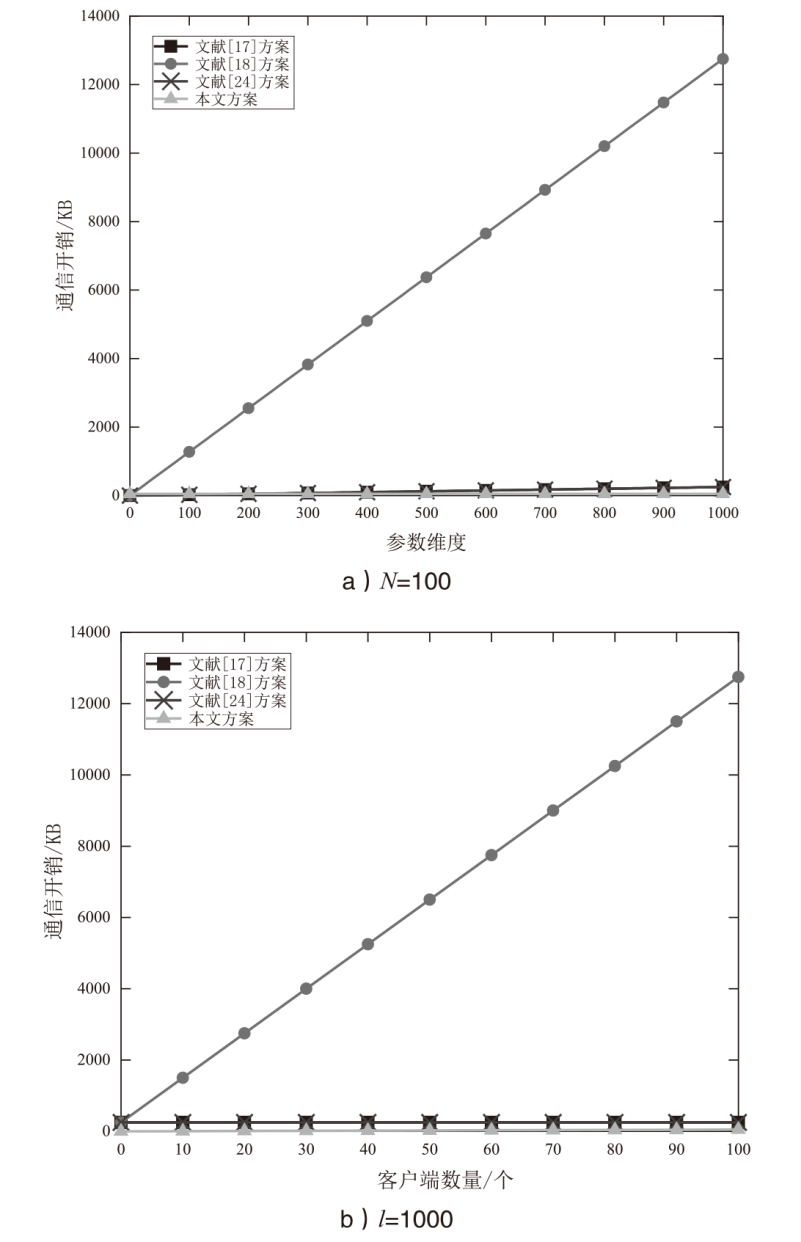
Cross-silo联邦学习使客户端可以在不共享原始数据的情况下通过聚合本地模型更新来协作训练一个机器学习模型。然而研究表明,训练过程中传输的中间参数也会泄露原始数据隐私,且好奇的中央服务器可能为了自身利益伪造或篡改聚合结果。针对上述问题,文章提出一种抗合谋的隐私保护与可验证cross-silo联邦学习方案。具体地,对每个客户端中间参数进行加密以保护数据隐私,同时为增强系统安全性,结合秘密共享方案实现密钥管理和协同解密。此外,通过聚合签名进一步实现数据完整性和认证,并利用多项式承诺实现中央服务器聚合梯度的可验证性。安全性分析表明,该方案不仅能保护中间参数的隐私及验证数据完整性,而且能够确保聚合梯度的正确性。同时,性能分析表明,相比于现有同类方案,文章所提方案的通信开销显著降低。
中图分类号:
引用本文
赖成喆, 赵益宁, 郑东. 基于同态加密的隐私保护与可验证联邦学习方案[J]. 信息网络安全, 2024, 24(1): 93-105.
LAI Chengzhe, ZHAO Yining, ZHENG Dong. A Privacy Preserving and Verifiable Federated Learning Scheme Based on Homomorphic Encryption[J]. Netinfo Security, 2024, 24(1): 93-105.
| [1] | LIU Yixuan, CHEN Hong, LIU Yuhan, et al. Privacy-Preserving Techniques in Federated Learning. Journal of Software, 2022, 33(3): 1057-1092. |
| 刘艺璇, 陈红, 刘宇涵, 等. 联邦学习中的隐私保护技术[J]. 软件学报, 2022, 33(3):1057-1092. | |
| [2] |
GODDARD M. The Eu General Data Protection Regulation (Gdpr): European Regulation That Has a Global Impact[J]. International Journal of Market Research, 2017, 59 (6): 703-705.
doi: 10.2501/IJMR-2017-050 URL |
| [3] | ZHOU Chuanxin, SUN Yi, WANG Degang, et al. Survey of Federated Learning Research[J]. Chinese Journal of Network and Information Security, 2021, 7 (5): 77-92. |
| 周传鑫, 孙奕, 汪德刚, 等. 联邦学习研究综述[J]. 网络与信息安全学报, 2021, 7(5):77-92. | |
| [4] | MCMAHAN H B, MOORE E, RAMAGE D, et al. Communication-Efficient Learning of Deep Networks from Decentralized Data[EB/OL]. (2017-02-28) [2023-06-27]. https://arxiv.org/abs/1602.05629v3. |
| [5] |
KAIROUZ P, MCMAHAN H B, AVENT B, et al. Advances and Open Problems in Federated Learning[J]. Foundations and Trends® in Machine Learning, 2021, 14 (1-2): 1-210.
doi: 10.1561/2200000083 URL |
| [6] | ZHOU Wei, WANG Chao, XU Jian, et al. Privacy-Preserving and Decentralized Federated Learning Model Based on the Blockchain[J]. Journal of Computer Research and Development, 2022, 59(11): 2423-2436. |
| 周炜, 王超, 徐剑, 等. 基于区块链的隐私保护去中心化联邦学习模型[J]. 计算机研究与发展, 2022, 59(11):2423-2436. | |
| [7] | TRUONG N, SUN Kai, WANG Siyao, et al. Privacy Preservation in Federated Learning: An Insightful Survey from the Gdpr Perspective[J]. Computers & Security, 2021, 110 (4): 402-411. |
| [8] | HITAJ B, ATENIESE G, PEREZ-CRUZ F. Deep Models under the Gan: Information Leakage from Collaborative Deep Learning[C]// ACM. 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 603-618. |
| [9] | FU Chong, ZHANG Xuhong, JI Shouling, et al. Label Inference Attacks against Vertical Federated Learning[C]// USENIX. 31st USENIX Security Symposium, Security 2022. Berkeley: USENIX, 2022: 1397-1414. |
| [10] | ZHANG Yanci, YU Han. Towards Verifiable Federated Learning[EB/OL]. (2022-02-15) [2023-06-27]. https://arxiv.org/abs/2202.08310. |
| [11] | ZHANG Chengliang, LI Suyi, XIA Junzhe, et al. Batchcrypt: Efficient Homomorphic Encryption for Cross-Silo Federated Learning[C]// USENIX. 2020 USENIX Annual Technical Conference. Berkeley: USENIX, 2020: 493-506. |
| [12] | WANG Ning, XIAO Xiaokui, YANG Yin, et al. Collecting and Analyzing Multidimensional Data with Local Differential Privacy[C]// IEEE. 2019 IEEE 35th International Conference on Data Engineering. New York: IEEE, 2019: 638-649. |
| [13] | ZHOU Chuanxin, SUN Yi, WANG Degang. Federated Learning with Gaussian Differential Privacy[C]// ACM. 2020 2nd International Conference on Robotics, Intelligent Control and Artificial Intelligence. New York: ACM, 2020: 296-301. |
| [14] | BONAWITZ K, IVANOV V, KREUTER B, et al. Practical Secure Aggregation for Privacy-Preserving Machine Learning[C]// ACM. 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 1175-1191. |
| [15] | MOHASSEL P, ZHANG Yupeng. Secureml: A System for Scalable Privacy-Preserving Machine Learning[C]// IEEE. 2017 IEEE Symposium on Security and Privacy. New York: IEEE, 2017: 19-38. |
| [16] |
LI Ping, LI Jin, HUANG Zhengan, et al. Multi-Key Privacy-Preserving Deep Learning in Cloud Computing[J]. Future Generation Computer Systems, 2017, 74: 76-85.
doi: 10.1016/j.future.2017.02.006 URL |
| [17] |
PHONG L T, AONO Y, HAYASHI T, et al. Privacy-Preserving Deep Learning via Additively Homomorphic Encryption[J]. IEEE Transactions on Information Forensics and Security, 2018, 13 (5): 1333-1345.
doi: 10.1109/TIFS.2017.2787987 URL |
| [18] |
MA Xu, ZHANG Fangguo, CHEN Xiaofeng, et al. Privacy Preserving Multi-Party Computation Delegation for Deep Learning in Cloud Computing[J]. Information Sciences, 2018, 459: 103-116.
doi: 10.1016/j.ins.2018.05.005 URL |
| [19] |
XU Guowen, LI Hongwei, LIU Sen, et al. Verifynet: Secure and Verifiable Federated Learning[J]. IEEE Transactions on Information Forensics and Security, 2020, 15: 911-926.
doi: 10.1109/TIFS.10206 URL |
| [20] | HAN Gang, ZHANG Tiantian, ZHANG Yinghui, et al. Verifiable and Privacy Preserving Federated Learning without Fully Trusted Centers[J]. Journal of Ambient Intelligence Humanized Computing, 2021(2): 1-11. |
| [21] |
GUO Xiaojie, LIU Zheli, LI Jin, et al. Verifl: Communication-Efficient and Fast Verifiable Aggregation for Federated Learning[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 1736-1751.
doi: 10.1109/TIFS.10206 URL |
| [22] |
FU Anmin, ZHANG Xianglong, XIONG Naixue, et al. Vfl: A Verifiable Federated Learning with Privacy-Preserving for Big Data in Industrial IoT[J]. IEEE Transactions on Industrial Informatics, 2022, 18 (5): 3316-3326.
doi: 10.1109/TII.2020.3036166 URL |
| [23] |
JIANG Changsong, XU Chunxiang, ZHANG Yuan. Pflm: Privacy-Preserving Federated Learning with Membership Proof[J]. Information Sciences, 2021, 576: 288-311.
doi: 10.1016/j.ins.2021.05.077 URL |
| [24] | ZHANG Xianglong, FU Anmin, WANG Huaqun, et al. A Privacy-Preserving and Verifiable Federated Learning Scheme[C]// IEEE. ICC 2020-2020 IEEE International Conference on Communications. New York: IEEE, 2020: 1-6. |
| [25] | MADI A, STAN O, MAYOUE A, et al. A Secure Federated Learning Framework Using Homomorphic Encryption and Verifiable Computing[C]// IEEE. 2021 Reconciling Data Analytics, Automation, Privacy, and Security:A Big Data Challenge. New York: IEEE, 2021: 1-8. |
| [26] |
YANG Zhen, ZHOU Ming, YU Haiyang, et al. Efficient and Secure Federated Learning with Verifiable Weighted Average Aggregation[J]. IEEE Transactions on Network Science and Engineering, 2023, 10 (1): 205-222.
doi: 10.1109/TNSE.2022.3206243 URL |
| [27] | YANG Qiang, LIU Yang, CHEN Tianjian, et al. Federated Machine Learning: Concept and Applications[J]. ACM Transactions on Intelligent Systems and Technology, 2019, 10: 1-19. |
| [28] |
SHAMIR A. How to Share a Secret[J]. Communications of the ACM, 1979, 22 (11): 612-613.
doi: 10.1145/359168.359176 URL |
| [29] |
KOBLITZ N. Elliptic Curve Cryptosystems[J]. Mathematics of Computation, 1987, 48 (177): 203-209.
doi: 10.1090/mcom/1987-48-177 URL |
| [30] | MILLER V S. Use of Elliptic Curves in Cryptography[C]// Springer. Conference on the Theory and Aapplication of Cryptographic Techniques. Heidelberg: Springer, 1985: 417-426. |
| [31] |
ELGAMAL T. A Public Key Cryptosystem and a Signature Scheme Based on Discrete Logarithms[J]. IEEE Transactions on Information Theory, 1985, 31 (4): 469-472.
doi: 10.1109/TIT.1985.1057074 URL |
| [32] | BONEH D, GENTRY C, LYNN B, et al. Aggregate and Verifiably Encrypted Signatures from Bilinear Maps[C]// Springer. Advances in Cryptology- EUROCRYPT 2003:International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2003: 416-432. |
| [33] | KATE A, ZAVERUCHA G M, GOLDBERG I. Constant-Size Commitments to Polynomials and Their Applications[C]// Springer. Advances in Cryptology-ASIACRYPT 2010: 16th International Conference on the Theory and Application of Cryptology and Information Security. Heidelberg: Springer, 2010: 177-194. |
| [34] | TSIOUNIS Y, YUNG M. On the Security of Elgamal Based Encryption[C]// Springer. Public Key Cryptography: First International Workshop on Practice and Theory in Public Key Cryptography, PKC’98. Heidelberg:Springer, 2006: 117-134. |
| [35] | CARO A D, IOVINO V. Jpbc: Java Pairing Based Cryptography[C]// IEEE. 2011 IEEE Symposium on Computers and Communications. New York: IEEE, 2011: 850-855. |
| [1] | 吴昊天, 李一凡, 崔鸿雁, 董琳. 基于零知识证明和区块链的联邦学习激励方案[J]. 信息网络安全, 2024, 24(1): 1-13. |
| [2] | 宋玉涵, 祝跃飞, 魏福山. 一种基于AdaBoost模型的区块链异常交易检测方案[J]. 信息网络安全, 2024, 24(1): 24-35. |
| [3] | 许可, 李嘉怡, 蒋兴浩, 孙锬锋. 一种基于轮廓稀疏对抗的视频步态隐私保护算法[J]. 信息网络安全, 2024, 24(1): 48-59. |
| [4] | 赵佳, 杨博凯, 饶欣宇, 郭雅婷. 基于联邦学习的Tor流量检测算法设计与实现[J]. 信息网络安全, 2024, 24(1): 60-68. |
| [5] | 徐茹枝, 戴理朋, 夏迪娅, 杨鑫. 基于联邦学习的中心化差分隐私保护算法研究[J]. 信息网络安全, 2024, 24(1): 69-79. |
| [6] | 彭翰中, 张珠君, 闫理跃, 胡成林. 联盟链下基于联邦学习聚合算法的入侵检测机制优化研究[J]. 信息网络安全, 2023, 23(8): 76-85. |
| [7] | 俞惠芳, 乔一凡, 孟茹. 面向区块链金融的抗量子属性基门限环签密方案[J]. 信息网络安全, 2023, 23(7): 44-52. |
| [8] | 陈晶, 彭长根, 谭伟杰, 许德权. 基于差分隐私和秘密共享的多服务器联邦学习方案[J]. 信息网络安全, 2023, 23(7): 98-110. |
| [9] | 唐雨, 张驰. 一种基于Intel SGX的信息中心网络隐私保护方案[J]. 信息网络安全, 2023, 23(6): 55-65. |
| [10] | 李增鹏, 王梅, 陈梦佳. 新形态伪随机函数研究[J]. 信息网络安全, 2023, 23(5): 11-21. |
| [11] | 杜卫东, 李敏, 韩益亮, 王绪安. 基于密文转换的高效通用同态加密框架[J]. 信息网络安全, 2023, 23(4): 51-60. |
| [12] | 尹曙, 陈兴蜀, 朱毅, 曾雪梅. 基于字符空间构造的域名匿名化算法[J]. 信息网络安全, 2023, 23(4): 80-89. |
| [13] | 刘长杰, 石润华. 基于安全高效联邦学习的智能电网入侵检测模型[J]. 信息网络安全, 2023, 23(4): 90-101. |
| [14] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [15] | 李晓华, 王苏杭, 李凯, 徐剑. 一种支持隐私保护的传染病人际传播分析模型[J]. 信息网络安全, 2023, 23(3): 35-44. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||