信息网络安全 ›› 2023, Vol. 23 ›› Issue (8): 109-120.doi: 10.3969/j.issn.1671-1122.2023.08.010
面向跨链的改进加权拜占庭容错算法
- 南京航空航天大学计算机科学与技术学院,南京 211106
-
收稿日期:2023-04-23出版日期:2023-08-10发布日期:2023-08-08 -
通讯作者:蒋佳佳 E-mail:jiangjiajia@nuaa.edu.cn -
作者简介:邵震哲(2002—),男,浙江,硕士研究生,主要研究方向为区块链|蒋佳佳(1997—),女,山东,博士研究生,主要研究方向为区块链与密码学|赵佳豪(1998—),男,安徽,硕士研究生,主要研究方向为区块链与密码学|张玉书(1987—),男,江苏,教授,博士,CCF会员,主要研究方向为多媒体安全、人工智能、区块链、物联网安全、云计算、大数据安全 -
基金资助:国家重点研发计划(2020YFB1005500)
An Improved Weighted Byzantine Fault Tolerance Algorithm for Cross-Chain System
SHAO Zhenzhe, JIANG Jiajia( ), ZHAO Jiahao, ZHANG Yushu
), ZHAO Jiahao, ZHANG Yushu
- College of Computer Science and Technology, Nanjing University of Aeronautics and Astronautics,Nanjing 211106, China
-
Received:2023-04-23Online:2023-08-10Published:2023-08-08 -
Contact:JIANG Jiajia E-mail:jiangjiajia@nuaa.edu.cn
摘要:
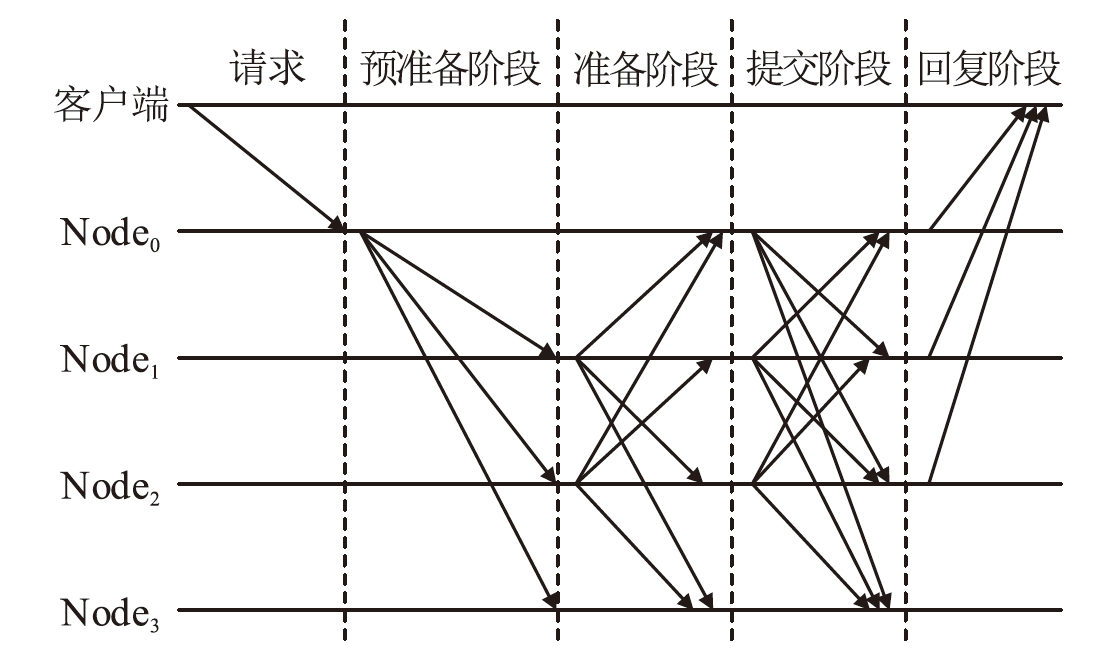
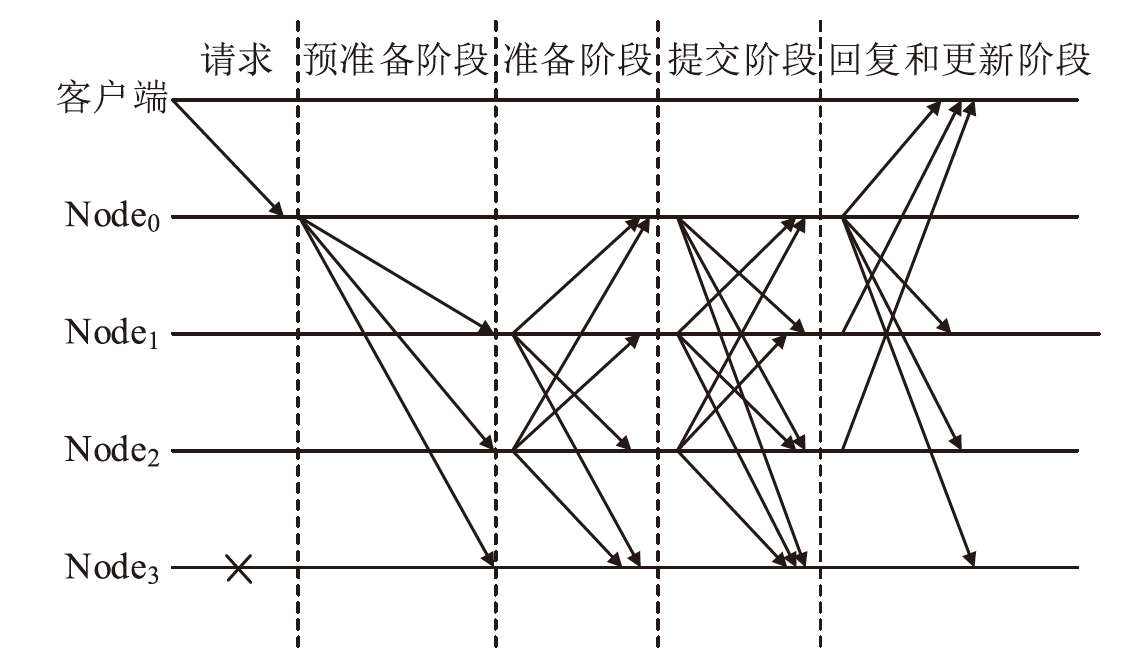
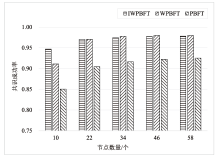
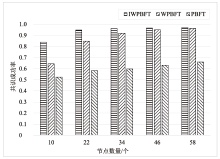
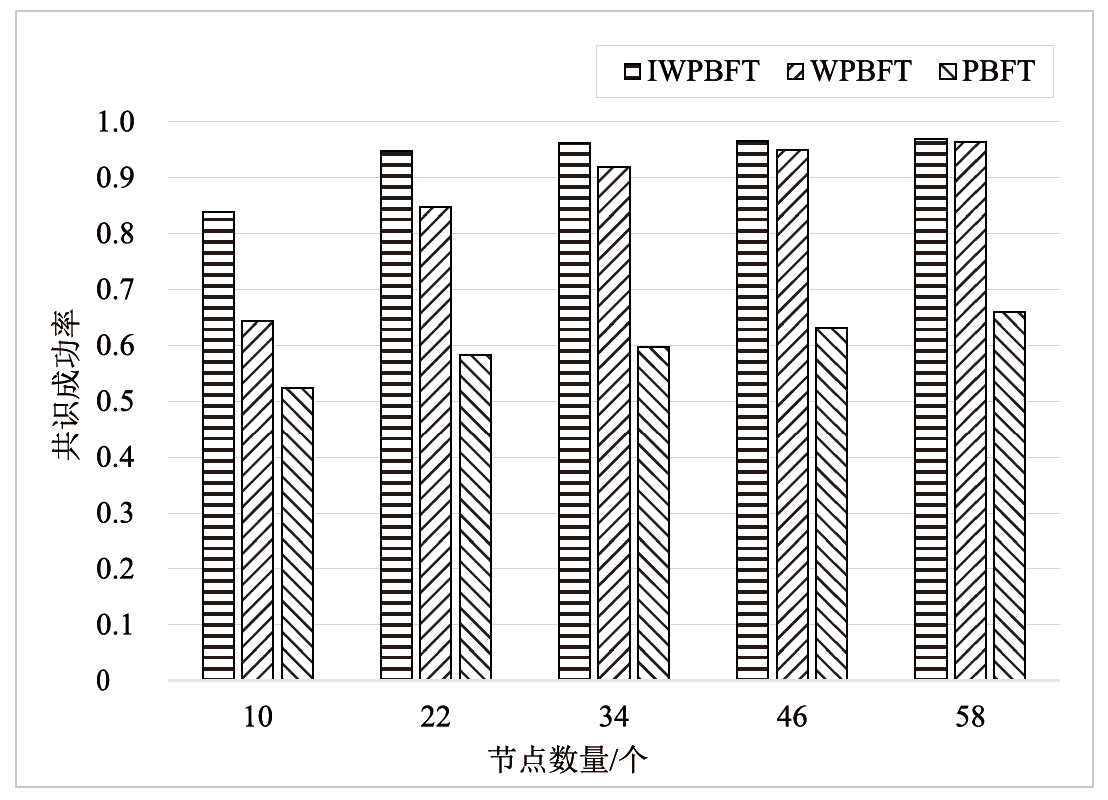
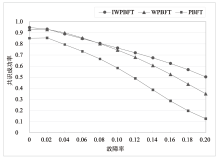
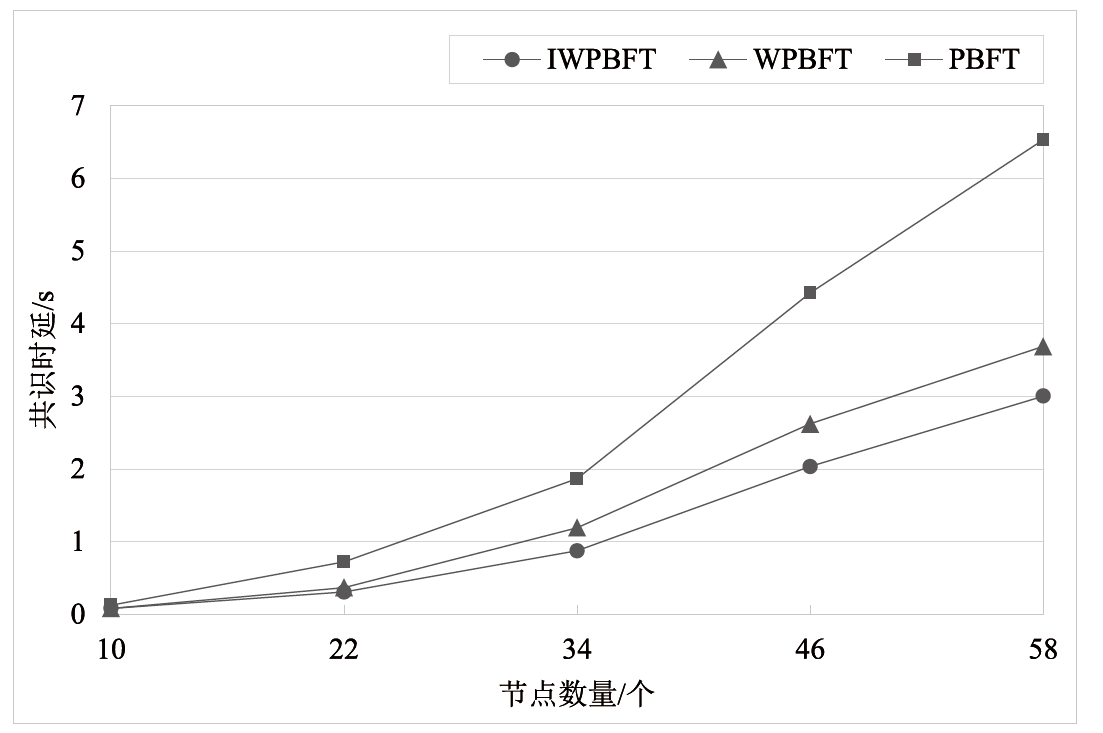
中继链是被广泛认可的跨链技术之一,当前跨链多采用实用拜占庭容错及其改进算法,如加权拜占庭容错(Weighted Practical Byzantine Fault Tolerance,WPBFT)算法。WPBFT算法为节点附加权重,降低恶意节点的影响,但其权重更新机制简单,作恶成本较低,严重威胁了系统的安全。为此,针对中继链安全和效率需求,文章提出一种应用于中继链的改进加权拜占庭容错(Improved Weighted Practical Byzantine Fault Tolerance,IWPBFT)算法。该算法对WPBFT算法的共识过程和权重变更机制进行改进,设计了新的权重更新和节点奖惩机制。实验表明,IWPBFT算法主节点出错概率较低,共识成功率较高,可有效提高中继链的安全性、可靠性和容错性,降低共识时延,提升中继链的跨链效率。
中图分类号:
引用本文
邵震哲, 蒋佳佳, 赵佳豪, 张玉书. 面向跨链的改进加权拜占庭容错算法[J]. 信息网络安全, 2023, 23(8): 109-120.
SHAO Zhenzhe, JIANG Jiajia, ZHAO Jiahao, ZHANG Yushu. An Improved Weighted Byzantine Fault Tolerance Algorithm for Cross-Chain System[J]. Netinfo Security, 2023, 23(8): 109-120.
| [1] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. (2008-10-31)[2022-11-28]. https://bitcoin.org/bitcoin.pdf. |
| [2] | BUTERIN V. A Next-Generation Smart Contract and Decentralized Application Platform[EB/OL]. (2022-05-26)[2023-02-01]. https://github.com/ethereum/wiki/wiki/White-Paper. |
| [3] | CACHIN C. Architecture of the Hyperledger Blockchain Fabric[C]//IBM. The Workshop on Distributed Cryptocurrencies and Consensus Ledgers. Chicago: IBM, 2016: 310-313. |
| [4] | BROWN R G, CARLYLE J, GRIGG I, et al. Corda: An Introduction[EB/OL]. (2021-08-16)[2022-12-10]. https://docs.corda.net/static/corda-introductory-whitepaper.pdf. |
| [5] | JPMORGAN Chase & Co.. Quorum Whitepaper[EB/OL]. (2018-08-24)[2023-01-20]. https://github.com/ConsenSys/quorum/blob/master/docs/Quorum%20Whitepaper%20v0.2.pdf. |
| [6] | ZHANG Yushu, JIANG Jiajia, DONG Xuewen, et al. BeDCV: Blockchain-Enabled Decentralized Consistency Verification for Cross-Chain Calculation[EB/OL]. (2022-08-08)[2023-02-01]. https://ieeexplore.ieee.org/document/9851945. |
| [7] | ADRIAN H-B, STEFEN T. Interledger:Creating a Standard for Payments[C]//ACM. The 25th International Conference Companion on World Wide Web. New York: ACM, 2016: 281-282. |
| [8] | BACK A, CORALLO M, DASHIR L, et al. Enabling Blockchain Innovations with Pegged Sidechains[EB/OL]. (2014-10-22)[2023-02-20]. https://www.blockstream.com/sidechains.pdf. |
| [9] | ETHEREUM. Welcome to BTC Relay’s Documentation[EB/OL]. (2021-1-29)[2023-01-10]. https://btc-relay.readthedocs.io/en/latest/. |
| [10] | POON J, DRYJA T. The Bitcoin Lightning Network: Scalable off-Chain Instant Payments[EB/OL]. (2016-01-14)[2022-11-14]. https://www.bitcoinlightning.com/wp-content/uploads/2018/03/lightning-network-paper.pdf. |
| [11] | BUTERIN V. Chain Interoperability[EB/OL]. (2016-09-01)[2023-01-20]. https://r3.com/reports/chain-interoperability. |
| [12] | KWON J, BUCHMAN E. Cosmos Whitepaper[EB/OL]. (2019-01-30)[2023-01-08]. https://github.com/cosmos/cosmos/blob/master/WHITEPAPER.md. |
| [13] | NOLAN T. Alt Chains and Atomic Transfers[EB/OL]. (2015-05-10)[2023-01-06]. https://bitcointalk.org/index.php?topic=193281.0. |
| [14] | SHAO Qifeng, JIN Cheqing, ZHANG Zhao, et al. Blockchain: Architecture and Research Progress[J]. Chinese Journal of Computers, 2018, 41(5): 969-988. |
| 邵奇峰, 金澈清, 张召, 等. 区块链技术:架构及进展[J]. 计算机学报, 2018, 41(5):969-988. | |
| [15] | QASSE I A, ABU T M, NASIR Q. Inter Blockchain Communication:A Survey[C]//ACM. The ArabWIC 6th Annual International Conference Research Track. New York: ACM, 2019: 1-6. |
| [16] | HU Zhiyan. Research on Improvement of Cross-Chain Consensus Algorithm Based on Node Similarity in Trading Network[D]. Wuhan: Zhongnan University of Economics and Law, 2020. |
| 胡治衍. 基于交易网络节点相似度的跨链共识算法改进研究[D]. 武汉: 中南财经政法大学, 2020. | |
| [17] | CHENG Yuntao. A New Block Chain Consensus Algorithm Based on Weighted Byzantine Fault Tolerance[D]. Lanzhou: Northwest Normal University, 2021. |
| 成云涛. 基于加权拜占庭容错机制的区块链共识算法研究与应用[D]. 兰州: 西北师范大学, 2021. | |
| [18] | GOES C. The Interblockchain Communication Protocol: An Overview[EB/OL]. (2020-06-29)[2023-01-10]. https://arxiv.org/pdf/2006.15918.pdf. |
| [19] |
ALANGOT B, REIJSBERGEN D, VENUGOPALAN S, et al. Decentralized and Lightweight Approach to Detect Eclipse Attacks on Proof of Work Blockchains[J]. IEEE Transactions on Network and Service Management, 2021, 18(2): 1659-1672.
doi: 10.1109/TNSM.2021.3069502 URL |
| [20] |
MALAKHOV I, MARIN A, ROSSI S, et al. On the Use of Proof-of-Work in Permissioned Blockchains: Security and Fairness[J]. IEEE Access, 2022, 10: 1305-1316.
doi: 10.1109/ACCESS.2021.3138528 URL |
| [21] |
ROSU I, SALEH F. Evolution of Shares in a Proof-of-Stake Cryptocurrency[J]. Management Science, 2021, 67(2): 661-672.
doi: 10.1287/mnsc.2020.3791 URL |
| [22] |
YANG Jiawei, PAUDEL A, GOOI H B. Compensation for Power Loss by a Proof-of-Stake Consortium Blockchain Microgrid[J]. IEEE Transactions on Industrial Informatics, 2021, 17(5): 3253-3262.
doi: 10.1109/TII.9424 URL |
| [23] | CASTRO M, LISKOV B. Practicality of Practical Byzantine Fault Tolerance[J]. Operating Systems Review, 2002, 20(4): 398-461. |
| [24] | HAN Xuan, LIU Yamin. Research on the Consensus Mechanisms of Blockchain Technology[J]. Netinfo Security, 2017, 17(9): 147-152. |
| 韩璇, 刘亚敏. 区块链技术中的共识机制研究[J]. 信息网络安全, 2017, 17(9):147-152. | |
| [25] |
CASTRO M, LISKOV B. Practical Byzantine Fault Tolerance and Proactive Recovery[J]. ACM Transactions on Computer Systems, 2002, 20(4): 398-461.
doi: 10.1145/571637.571640 URL |
| [26] | GARG V K, BRIDGMAN J. The Weighted Byzantine Agreement Problem[C]//IEEE. IEEE International Parallel & Distributed Processing Symposium. New York: IEEE, 2011: 524-531. |
| [27] | SAINI P, SINGH A K. Hash Based Byzantine Fault Tolerant Agreement with Enhanced View Consistency[C]// IEEE. 12th International Conference on Parallel and Distributed Computing,Applications and Technologies. New York: IEEE, 2011: 368-374. |
| [28] | BIRYUKOV A, FEHER D, KHOVRATOVICH D. Guru: Universal Reputation Module for Distributed Consensus Protocols[EB/OL]. (2017-06-07)[2023-02-20]. https://eprint.iacr.org/2017/671.pdf. |
| [29] | XU Hao, LONG Yu, LIU Zhiqiang, et al. Dynamic Practical Byzantine Fault Tolerance[C]//IEEE. IEEE Conference on Communications and Network Security. New York: IEEE, 2018: 1-8. |
| [30] | CRAIN T, GRAMOLI V, LARREA M, et al. DBFT:Efficient Leaderless Byzantine Consensus and Its Application to Blockchains[C]//IEEE. IEEE 17th International Symposium on Network Computing and Applications. New York: IEEE, 2018: 1-8. |
| [31] | LEI Kai, ZHANG Qichao, XU Limei, et al. Reputation-Based Byzantine Fault-Tolerance for Consortium Blockchain[C]//IEEE. IEEE 24th International Conference on Parallel and Distributed Systems. New York: IEEE, 2018: 604-611. |
| [32] | RIAHI K, BRAHMIA M-A, ABOUAISSA A, et al. APBFT:An Adaptive PBFT Consensus for Private Blockchains[C]//IEEE. GLOBECOM 2022-2022 IEEE Global Communications Conference. New York: IEEE, 2022: 1788-1793. |
| [33] | KOTLA R, ALVISI L, DAHLIN M, et al. Zyzzyva: Speculative Byzantine Fault Tolerance[J]. ACM Transactions on Computer Systems, 2009, 27(4): 1-39. |
| [34] | LI Yuhua, YI Xin, SUN Xiaolin. Application of a Link Discovery Algorithm Based on Graph Entropy in the Money-Laundering Field[J]. Computer Engineering & Science, 2007, 29(11): 50-52. |
| 李玉华, 易鑫, 孙小林. 基于图熵的链接发现算法在反洗钱领域的应用[J]. 计算机工程与科学, 2007, 29(11):50-52. |
| [1] | 公鹏飞, 谢四江, 程安东. 基于HotStuff改进的多主节点共识算法[J]. 信息网络安全, 2023, 23(9): 108-117. |
| [2] | 周权, 陈民辉, 卫凯俊, 郑玉龙. 基于SM9的属性加密的区块链访问控制方案[J]. 信息网络安全, 2023, 23(9): 37-46. |
| [3] | 赵佳豪, 蒋佳佳, 张玉书. 基于动态默克尔哈希树的跨链数据一致性验证模型[J]. 信息网络安全, 2023, 23(9): 95-107. |
| [4] | 覃思航, 代炜琦, 曾海燕, 顾显俊. 基于区块链的电力应用数据安全共享研究[J]. 信息网络安全, 2023, 23(8): 52-65. |
| [5] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [6] | 李春晓, 王耀飞, 徐恩亮, 赵钰. 基于双线性映射的区块链安全范围搜索技术研究[J]. 信息网络安全, 2023, 23(3): 22-34. |
| [7] | 王晶宇, 马兆丰, 徐单恒, 段鹏飞. 支持国密算法的区块链交易数据隐私保护方案[J]. 信息网络安全, 2023, 23(3): 84-95. |
| [8] | 冯怡婷, 马兆丰, 徐单恒, 段鹏飞. 跨链接入的区块链安全强度评估方法[J]. 信息网络安全, 2023, 23(1): 84-92. |
| [9] | 张光华, 刘永升, 王鹤, 于乃文. 基于BiLSTM和注意力机制的智能合约漏洞检测方案[J]. 信息网络安全, 2022, 22(9): 46-54. |
| [10] | 胡艺, 佘堃. 基于区块链和智能合约的双链车联网系统[J]. 信息网络安全, 2022, 22(8): 26-35. |
| [11] | 黄保华, 赵伟宏, 彭丽, 谢统义. 基于MPT索引的高效链上PKI模型[J]. 信息网络安全, 2022, 22(8): 72-80. |
| [12] | KELEKET GOMA Christy Junior Yannick, 易文哲, 王鹃. 一种基于SGX的轻量Fabric链码可信执行环境构建方法[J]. 信息网络安全, 2022, 22(7): 73-83. |
| [13] | 王姝爽, 马兆丰, 刘嘉微, 罗守山. 区块链跨链安全接入与身份认证方案研究与实现[J]. 信息网络安全, 2022, 22(6): 61-72. |
| [14] | 于克辰, 郭莉, 阴宏伟, 燕雪松. 面向数据中心场景的基于区块链与博弈论的高价值数据共享模型[J]. 信息网络安全, 2022, 22(6): 73-85. |
| [15] | 冯景瑜, 张琪, 黄文华, 韩刚. 基于跨链交互的网络安全威胁情报共享方案[J]. 信息网络安全, 2022, 22(5): 21-29. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||