信息网络安全 ›› 2023, Vol. 23 ›› Issue (8): 99-108.doi: 10.3969/j.issn.1671-1122.2023.08.009
基于动态时间切片和高效变异的定向模糊测试
- 四川大学网络空间安全学院,成都 610065
-
收稿日期:2023-02-06出版日期:2023-08-10发布日期:2023-08-08 -
通讯作者:贾鹏 E-mail:pengjia@scu.edu.cn -
作者简介:钟远鑫(1998—),男,四川,硕士研究生,主要研究方向为模糊测试|刘嘉勇(1962—),男,四川,教授,博士,主要研究方向为网络应用安全、信息内容安全|贾鹏(1988—),男,河南,副教授,博士,主要研究方向为漏洞挖掘、软件动静态分析 -
基金资助:国家自然科学基金(61902265)
Directed Fuzzing Based on Dynamic Time Slicing and Efficient Mutation
ZHONG Yuanxin, LIU Jiayong, JIA Peng( )
)
- School of Cyber Science and Engineering, Sichuan University, Chengdu 610065, China
-
Received:2023-02-06Online:2023-08-10Published:2023-08-08 -
Contact:JIA Peng E-mail:pengjia@scu.edu.cn
摘要:
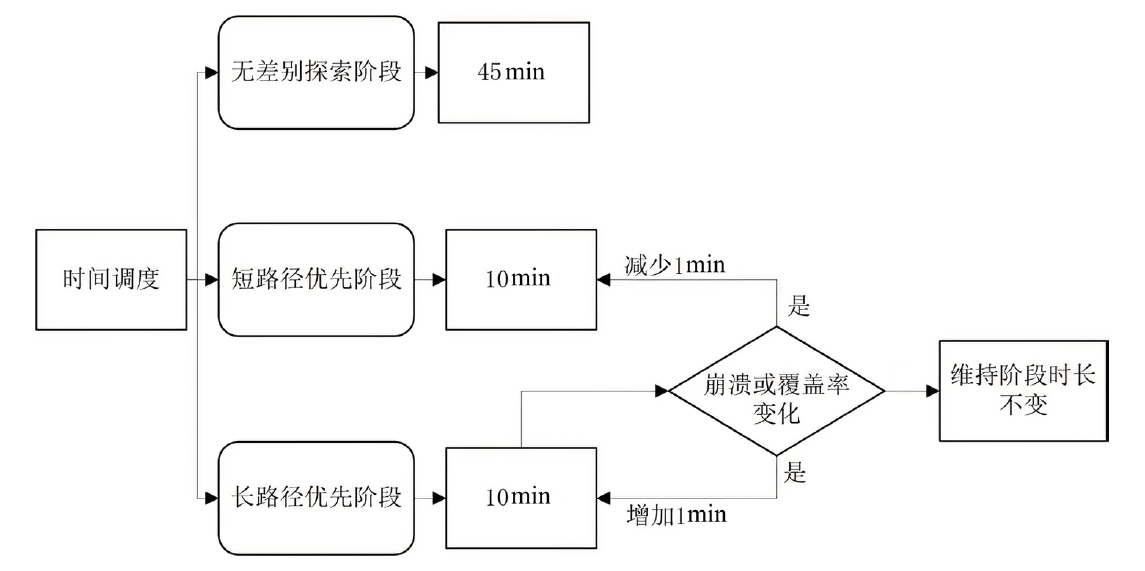
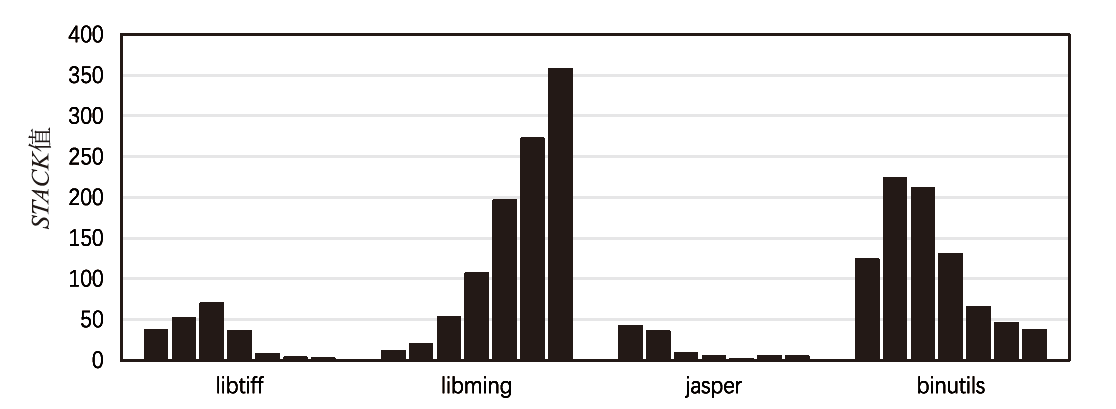
定向灰盒模糊测试(Directed Grey Box Fuzzing,DGF)是一种漏洞挖掘领域的新技术,它的最大优势是高效性。DGF已被广泛应用于补丁测试、信息流检测和崩溃复现等领域。然而,现有的DGF技术存在两个问题,第一,传统的DGF没有考虑到长路径种子也能触发漏洞,并且没有考虑种子的优先级;第二,强随机性的变异会浪费大量资源,从而降低定向模糊测试的效率。文章提出了一种基于动态时间切片和高效变异的定向灰盒模糊测试方法。文章提出了动态时间切片策略,将时间分为3个阶段,包括无差别探索阶段、短路径优先阶段和长路径优先阶段,同时应用了基于种子路径执行频率的模拟退火算法用于能量分配。同时,还使用了ε-贪婪算法来引导变异过程的havoc阶段,以提升变异效率。文章基于这3种策略实现了一个名为DyFuzz的系统并且在8个真实的数据集上与AFLGo进行比较。实验表明,该方法能够有效提高触发漏洞的概率和速度,覆盖更多的边缘和触发更多的崩溃。
中图分类号:
引用本文
钟远鑫, 刘嘉勇, 贾鹏. 基于动态时间切片和高效变异的定向模糊测试[J]. 信息网络安全, 2023, 23(8): 99-108.
ZHONG Yuanxin, LIU Jiayong, JIA Peng. Directed Fuzzing Based on Dynamic Time Slicing and Efficient Mutation[J]. Netinfo Security, 2023, 23(8): 99-108.
表3
在binutils上的性能对比
| CVE | Tool | R/次 | TTE/s | Factor |
|---|---|---|---|---|
| 2016-4487 | DyFuzz | 8 | 192 | — |
| AFLGo | 8 | 341 | 1.78 | |
| 2016-4488 | DyFuzz | 8 | 102 | — |
| AFLGo | 8 | 132 | 1.29 | |
| 2016-4490 | DyFuzz | 8 | 91 | — |
| AFLGo | 8 | 143 | 1.57 | |
| 2016-4491 | DyFuzz | 1 | 16413 | — |
| AFLGo | 0 | — | — | |
| 2016-4492 | DyFuzz | 8 | 863 | — |
| AFLGo | 8 | 1432 | 1.66 | |
| 2016-4493 | DyFuzz | 3 | 23112 | — |
| AFLGo | 2 | 20123 | 0.87 |
表4
在7个程序上的性能对比
| Program | Tool | R/次 | TTE/s | Factor |
|---|---|---|---|---|
| cb-multios | DyFuzz | 8 | 27 | — |
| AFLGo | 8 | 31 | 1.15 | |
| MJS | DyFuzz | 6 | 13564 | — |
| AFLGo | 5 | 15021 | 1.11 | |
| yasm | DyFuzz | 6 | 14576 | — |
| AFLGo | 6 | 22053 | 1.51 | |
| libming | DyFuzz | 7 | 6841 | — |
| AFLGo | 6 | 7935 | 1.16 | |
| libtiff | DyFuzz | 8 | 1475 | — |
| AFLGo | 8 | 3458 | 2.34 | |
| jasper | DyFuzz | 8 | 87 | — |
| AFLGo | 8 | 115 | 1.32 | |
| libxml2 | DyFuzz | 6 | 14520 | — |
| AFLGo | 4 | 24579 | 1.69 |
表5
路径和崩溃数量
| Program | Tool | Path | Crash |
|---|---|---|---|
| MJS | DyFuzz | 1703 | 51 |
| AFLGo | 1457 | 26 | |
| cb-multios | DyFuzz | 76 | 163 |
| AFLGo | 55 | 51 | |
| yasm | DyFuzz | 6632 | 8 |
| AFLGo | 5665 | 3 | |
| libtiff | DyFuzz | 1893 | 2 |
| AFLGo | 1545 | 1 | |
| libming | DyFuzz | 3621 | 487 |
| AFLGo | 3396 | 372 | |
| libxml2 | DyFuzz | 2998 | 162 |
| AFLGo | 2735 | 128 | |
| jasper | DyFuzz | 191 | 26 |
| AFLGo | 153 | 23 | |
| binutils | DyFuzz | 3325 | 165 |
| AFLGo | 2999 | 116 |
表7
引入新的能量分配算法后的实验结果
| CVE | Tool | R/次 | TTE/s | Factor |
|---|---|---|---|---|
| 2016-4487 | DyFuzz | 8 | 309 | — |
| AFLGo | 8 | 341 | 1.10 | |
| 2016-4488 | DyFuzz | 8 | 167 | — |
| AFLGo | 8 | 132 | 0.79 | |
| 2016-4490 | DyFuzz | 8 | 257 | — |
| AFLGo | 8 | 143 | 0.96 | |
| 2016-4491 | DyFuzz | 2 | 18766 | — |
| AFLGo | 0 | — | — | |
| 2016-4492 | DyFuzz | 8 | 1365 | — |
| AFLGo | 8 | 1432 | 1.06 | |
| 2016-4493 | DyFuzz | 3 | 19564 | — |
| AFLGo | 2 | 20123 | 1.03 |
表8
基于ε-贪婪算法的havoc变异实验结果
| CVE | Tool | R/次 | TTE/s | Factor |
|---|---|---|---|---|
| 2016-4487 | DyFuzz | 8 | 185 | — |
| AFLGo | 8 | 341 | 1.84 | |
| 2016-4488 | DyFuzz | 8 | 143 | — |
| AFLGo | 8 | 132 | 0.92 | |
| 2016-4490 | DyFuzz | 8 | 112 | — |
| AFLGo | 8 | 143 | 1.28 | |
| 2016-4491 | DyFuzz | 1 | 10273 | — |
| AFLGo | 0 | — | — | |
| 2016-4492 | DyFuzz | 8 | 1642 | — |
| AFLGo | 8 | 1432 | 0.87 | |
| 2016-4493 | DyFuzz | 4 | 18656 | — |
| AFLGo | 2 | 20123 | 1.08 |
| [1] |
MILLER B P, FREDRIKSEN L, SO B. An Empirical Study of the Reliability of UNIX Utilities[J]. Communications of the ACM, 1990, 33(12): 32-44.
doi: 10.1145/96267.96279 URL |
| [2] | CNCERT. 2020 China Internet Network Security Report[EB/OL]. (2021-07-21)[2022-10-06]. https://www.cert.org.cn/publish/man/upload/File/2020%20Annual%20Report.pdf. |
| 国家互联网应急中心. 2020年中国互联网网络安全报告[EB/OL]. (2021-07-21)[2022-10-06]. https://www.cert.org.cn/publish/man/upload/File/2020%20Annual%20Report.pdf. | |
| [3] | ZALEWSKI M. American Fuzzy Lop[EB/OL]. (2020-11-11)[2022-10-11]. https://lcamtuf.coredump.cx/afl/. |
| [4] | GODEFROID P. Random Testing for Security:Blackbox vs Whitebox Fuzzing[C]//IEEE. Proceedings of the 2nd International Workshop on Random Testing: Co-Located with the 22nd IEEE/ACM International Conference on Automated Software Engineering (ASE 2007). New York: IEEE, 2007: 1-12. |
| [5] | RAWAT S, JAIN V, KUMAR A, et al. VUzzer:Application-Aware Evolutionary Fuzzing[C]//ISOC. Network and Distributed System Security Symposium 2017. San Diego: ISOC, 2017: 1-14. |
| [6] | CHEN Peng, CHEN Hao. Angora:Efficient Fuzzing by Principled Search[C]//IEEE. 2018 IEEE Symposium on Security and Privacy. New York: IEEE, 2018: 711-725. |
| [7] | ASCHERMANN C, SCHUMILO S, BLAZYTKO T, et al. REDQUEEN:Fuzzing with Input-to-State Correspondence[C]//ISOC. Network and Distributed System Security Symposium 2019. San Diego: ISOC, 2019: 1-15. |
| [8] | GAN Shuitao, ZHANG Chao, CHEN Peng, et al. GREYONE:Data Flow Sensitive Fuzzing[C]//ACM. 29th USENIX Security Symposium. New York: ACM, 2020: 2577-2594. |
| [9] | LYU Chenyang, JI Shouling, ZHANG Chao, et al. MOPT:Optimized Mutation Scheduling for Fuzzers[C]//ACM. 28th USENIX Security Symposium. New York: ACM, 2019: 1949-1966. |
| [10] | HU Zhicheng, SHI Jianqi, HUANG Yanhong, et al. GANFuzz:A GAN-Based Industrial Network Protocol Fuzzing Framework[C]//ACM. CF '18:Computing Frontiers Conference. NewYork: ACM, 2018: 138-145. |
| [11] | CUMMINS C, PETOUMENOS P, MURRAY A, et al. Compiler Fuzzing Through Deep Learning[C]//ACM. ISSTA'18:International Symposium on Software Testing and Analysis. NewYork: ACM, 2018: 95-105. |
| [12] | SHE Dongdong, PEI Kexin, EPSTEIN D, et al. Neuzz:Efficient Fuzzing with Neural Program Smoothing[C]//IEEE. 2019 IEEE Symposium on Security and Privacy. New York: IEEE, 2019: 803-817. |
| [13] | GODEFROID P, PELEG H, SINGH R. Learn&Fuzz:Machine Learning for Input Fuzzing[C]//IEEE. 2017 32nd IEEE/ACM International Conference on Automated Software Engineering (ASE). New York: IEEE, 2017: 50-59. |
| [14] | BÖHME M, PHAM V T, NGUYEN M D, et al. Directed Greybox Fuzzing[C]//ACM. CCS'17: 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 2329-2344. |
| [15] | CHEN Hongxu, XUE Yinxing, LI Yuekang, et al. Hawkeye:Towards a Desired Directed Grey-Box Fuzzer[C]//ACM. CCS '18: 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 2095-2108. |
| [16] | LIANG Hongliang, ZHANG Yini, YU Yue, et al. Sequence Coverage Directed Greybox Fuzzing[C]//IEEE. ICSE '19: 41st International Conference on Software Engineering. New York: IEEE, 2019: 249-259. |
| [17] | LEE G, SHIM W, LEE B. Constraint-Guided Directed Greybox Fuzzing[C]//ACM. 30th USENIX Security Symposium. New York: ACM, 2021: 3559-3576. |
| [18] | HUANG Heqing, GUO Yiyuan, SHI Qingkai, et al. BEACON:Directed Grey-Box Fuzzing with Provable Path Pruning[C]//IEEE. 2022 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2022: 36-50. |
| [19] | ÖSTERLUND S, RAZAVI K, BOS H, et al. Parmesan:Sanitizer-Guided Greybox Fuzzing[C]//ACM. SEC'20: 29th USENIX Conference on Security Symposium. New York: ACM, 2020: 2289-2306. |
| [20] | ZHANG Chenhui, ZHOU Anmin, JIA Peng. A Time Slicing-Based Directed Fuzzing[J]. Modern Computer, 2022, 28(8):63-67. |
| 张晨辉, 周安民, 贾鹏. 一种基于时间分片的定向模糊测试[J]. 现代计算机, 2022, 28(8):63-67. | |
| [21] | JASON S. GNU Binutils[EB/OL]. (2001-06-19)[2022-11-04]. https://www.gnu.org/software/binutils/. |
| [22] | DMITRY F. MJS: Restricted JavaScript Engine[EB/OL]. (2018-02-09)[2022-11-04]. https://github.com/cesanta/mjs. |
| [23] | KAREEM E. DARPA Challenge Binaries on Linux, OS X, and Windows[EB-OL]. (2021-04-14)[2022-11-04]. https://github.com/trailofbits/cb-multios. |
| [24] | SANDRO S. Libming[EB/OL]. (2021-05-11)[2022-11-04]. http://www.libming.org/. |
| [25] | ALAN Y. Jasper[EB/OL]. (2021-09-28)[2022-11-04]. https://ece.engr.uvic.ca/frodo/jasper/doc. |
| [26] | NICK W. Libxml2[EB/OL]. (2022-08-25)[2022-11-04]. https://github.com/GNOME/libxml2. |
| [27] | VADIM Z. Libtiff[EB/OL]. (2017-11-29)[2022-11-04]. https://github.com/vadz/libtiff. |
| [28] | PETER J. Yasm[EB/OL]. (2022-09-15)[2022-11-04]. https://github.com/yasm/yasm. |
| [1] | 王鹃, 张冲, 龚家新, 李俊娥. 基于机器学习的模糊测试研究综述[J]. 信息网络安全, 2023, 23(8): 1-16. |
| [2] | 吴佳明, 熊焰, 黄文超, 武建双. 一种基于距离导向的模糊测试变异方法[J]. 信息网络安全, 2021, 21(10): 63-68. |
| [3] | 杜笑宇, 叶何, 文伟平. 基于字节码搜索的Java反序列化漏洞调用链挖掘方法[J]. 信息网络安全, 2020, 20(7): 19-29. |
| [4] | 李明磊, 黄晖, 陆余良. 面向漏洞挖掘的基于符号分治区的测试用例生成技术[J]. 信息网络安全, 2020, 20(5): 39-46. |
| [5] | 段斌, 李兰, 赖俊, 詹俊. 基于动态污点分析的工控设备硬件漏洞挖掘方法研究[J]. 信息网络安全, 2019, 19(4): 47-54. |
| [6] | 胡建伟, 赵伟, 闫峥, 章芮. 基于机器学习的SQL注入漏洞挖掘技术的分析与实现[J]. 信息网络安全, 2019, 19(11): 36-42. |
| [7] | 王夏菁, 胡昌振, 马锐, 高欣竺. 二进制程序漏洞挖掘关键技术研究综述[J]. 信息网络安全, 2017, 17(8): 1-13. |
| [8] | 郭亮, 罗森林, 潘丽敏. 编码函数交叉定位网络协议测试数据生成方法研究[J]. 信息网络安全, 2016, 16(3): 8-14. |
| [9] | . 基于模糊测试的网络协议自动化漏洞挖掘工具设计与实现[J]. , 2014, 14(6): 23-. |
| [10] | 崔化良;兰芸;崔宝江. 动态污点分析技术在ActiveX控件漏洞挖掘上的应用[J]. , 2013, 13(12): 0-0. |
| [11] | 黄超;李毅;麻荣宽;马建勋. 网页漏洞挖掘系统设计[J]. , 2012, 12(9): 0-0. |
| [12] | 王学;李学新;周智鹏;袁耀文. S2E测试平台及并行性能分析[J]. , 2012, 12(7): 0-0. |
| [13] | 康凯;郭颖;崔宝江. 基于XML的面向二进制漏洞模式形式化描述研究[J]. , 2012, 12(12): 0-0. |
| [14] | 徐有福;文伟平;尹亮. 基于补丁引发新漏洞的防攻击方法研究[J]. , 2011, 11(7): 0-0. |
| [15] | 姚洪波;尹亮;文伟平. 基于FUZZING试技术的Windows内核安全漏洞挖掘方法研究及应用[J]. , 2011, 11(12): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||