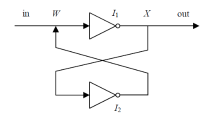
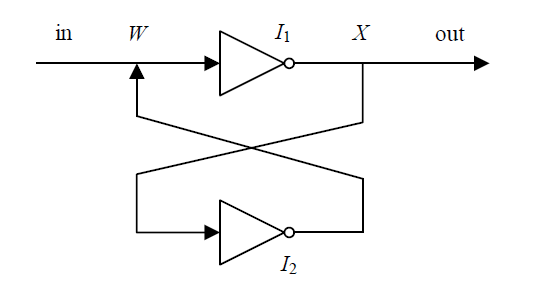
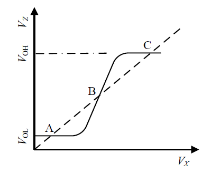
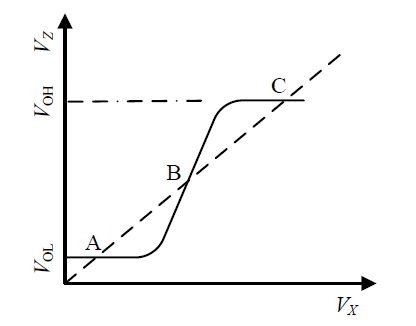
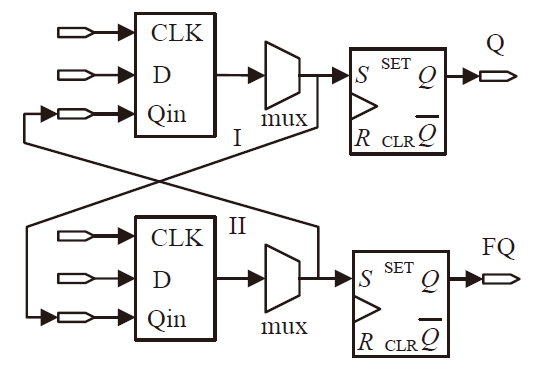
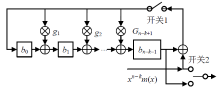
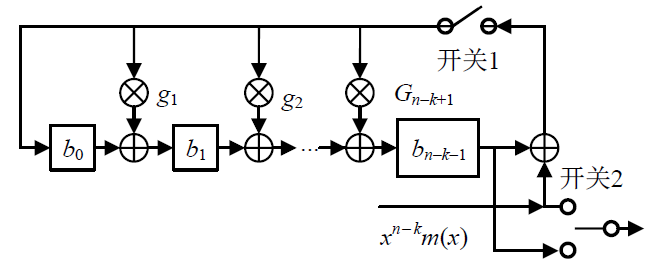
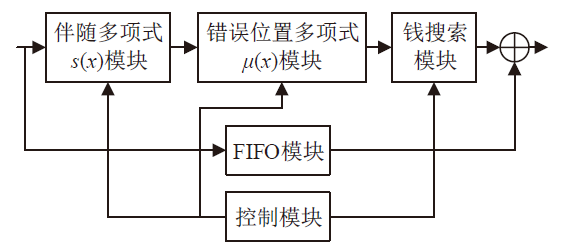
信息网络安全 ›› 2022, Vol. 22 ›› Issue (3): 53-61.doi: 10.3969/j.issn.1671-1122.2022.03.006
基于交叉耦合电路的物理不可克隆函数FPGA实现
- 北京电子科技学院,北京 100070
-
收稿日期:2021-08-12出版日期:2022-03-10发布日期:2022-03-28 -
通讯作者:李泽群 E-mail:lizer1996@163.com -
作者简介:李莉(1974—),女,山东,副教授,博士,主要研究方向为网络与系统安全、嵌入式系统安全应用|李泽群(1996—),男,吉林,硕士研究生,主要研究方向为密码与系统安全|李雪梅(1975—),女,辽宁,副教授,博士,主要研究方向为电子设计自动化、信号处理|史国振(1974—),男,河南,教授,博士,主要研究方向为网络与系统安全、嵌入式安全 -
基金资助:国家重点研发计划[2017YFB0801803];北京高校“高精尖”学科建设项目[2017YFB0801803]
FPGA Realization of Physical Unclonable Function Based on Cross-coupling Circuit
LI Li, LI Zequn( ), LI Xuemei, SHI Guozhen
), LI Xuemei, SHI Guozhen
- Beijing Electronic Science and Technology Institute, Beijing 100070, China
-
Received:2021-08-12Online:2022-03-10Published:2022-03-28 -
Contact:LI Zequn E-mail:lizer1996@163.com
摘要:
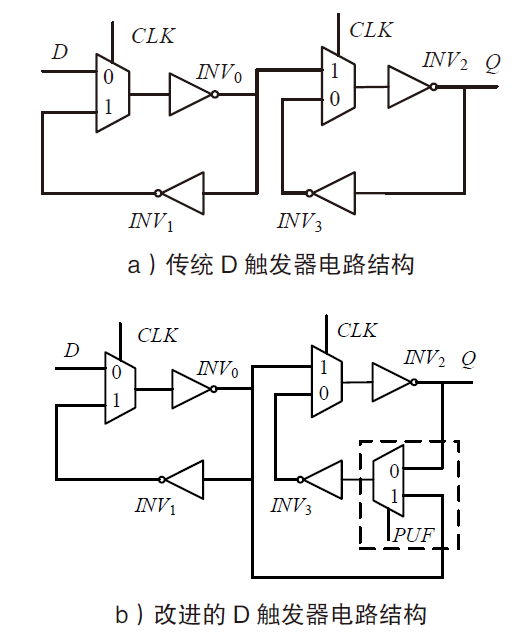
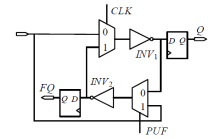
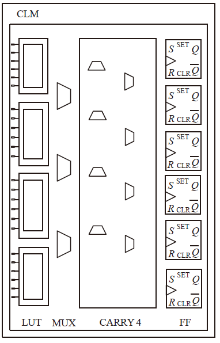
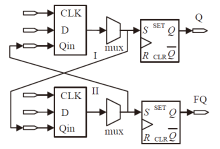
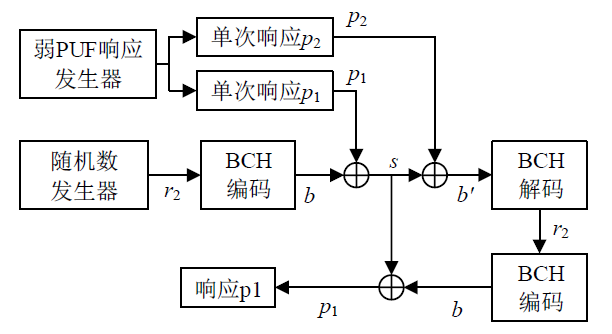
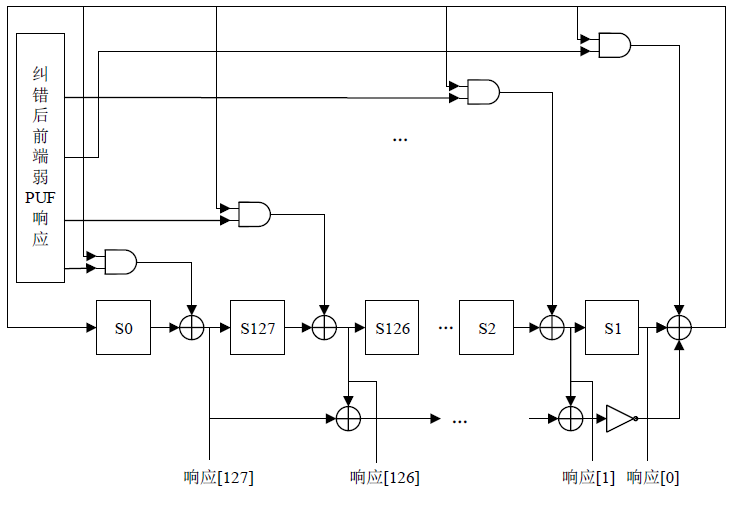
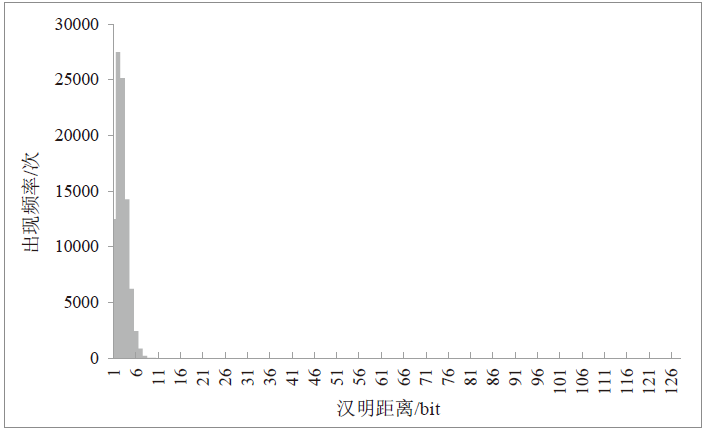
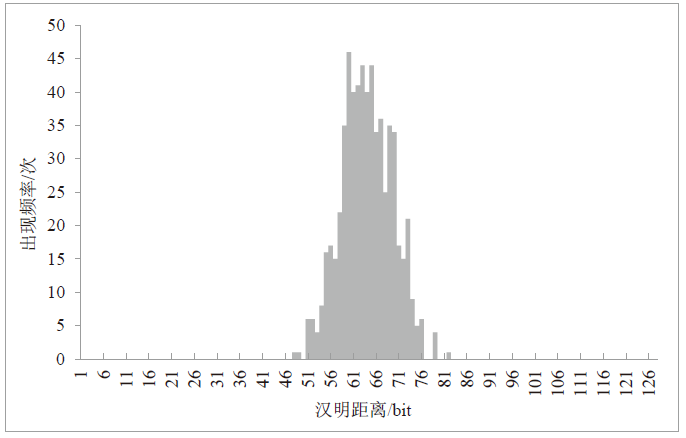
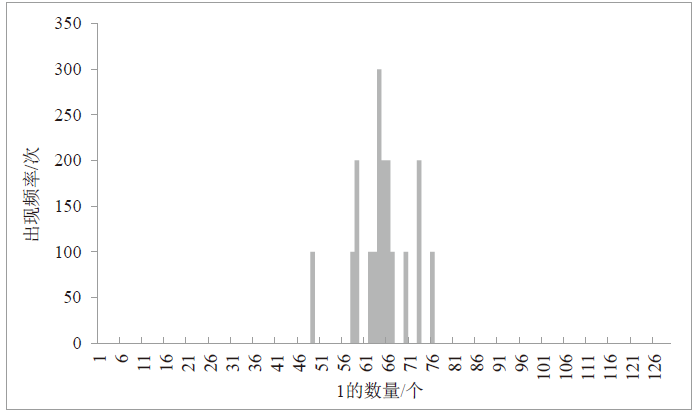
随着IoT设备数量的迅速增加和应用范围的不断扩展,IoT设备信息安全问题越发受到重视,PUF为解决IoT设备运行中的数据安全问题提供了新思路。针对C-PUF存在的激励-响应对数量不足和R-PUF占用资源过多的问题,文章将C-PUF、BCH码和LFSR相结合,提出一种由C-PUF构成R-PUF的方案,该方案具有高可靠性、高唯一性和占用资源较少的优点。文章在40 nm Alinx FPGA上实现了具有128 bit响应的R-PUF。在采用128 bit BCH码的结构下,R-PUF输出响应的可靠性达到100%,唯一性达到49.83%。与L-PUF相比,该PUF可靠性提升了3.7%,唯一性提高了0.08%。
中图分类号:
引用本文
李莉, 李泽群, 李雪梅, 史国振. 基于交叉耦合电路的物理不可克隆函数FPGA实现[J]. 信息网络安全, 2022, 22(3): 53-61.
LI Li, LI Zequn, LI Xuemei, SHI Guozhen. FPGA Realization of Physical Unclonable Function Based on Cross-coupling Circuit[J]. Netinfo Security, 2022, 22(3): 53-61.
| [1] | SADEGHI A R, WACHSMANN C, WAIDNER M. Security and Privacy Challenges in Industrial Internet of Things [C]//ACM. 52nd Annual Design Automation Conference, June 7-11 2015, San Francisco, California, USA. New York: ACM, 2015: 1-6. |
| [2] | ZHONG Jie, LEI Yanming, ZHENG Li, et al. Usability Availability Evaluation of Chip PUF[J]. Telecommunication Engineering, 2021, 61(4):391-395. |
| 钟杰, 雷颜铭, 郑力, 等. 芯片物理指纹的可用性评估[J]. 电讯技术, 2021, 61(4):391-395. | |
| [3] | DEVADAS S, SUH E, PARAL S, et al. Design and Implementation of PUF-based “Unclonable” RFID ICs for Anti-counterfeiting and Security Applications [C]//IEEE. 2008 IEEE International Conference on RFID, April 16-17, 2008, Las Vegas, NV, USA. New Jersey: IEEE, 2008: 58-64. |
| [4] |
LI Sensen, HUANG Yicai, YU Bin, et al. A PUF-based Low Cost Secure Communication Scheme for IoT[J]. Acta Electronica Sinica, 2019, 47(4):812-817.
doi: 10.3969/j.issn.0372-2112.2019.04.007 |
|
李森森, 黄一才, 郁滨, 等. 基于PUF的低开销物联网安全通信方案[J]. 电子学报, 2019, 47(4):812-817.
doi: 10.3969/j.issn.0372-2112.2019.04.007 |
|
| [5] |
MA Chaofang, YE Jing, LI Xiaowei, et al. Adjustable and Configurable Ring Oscillator Physical Unclonable Function[J]. Journal of Computer-aided Design and Computer Graphics, 2021, 33(3):340-345.
doi: 10.3724/SP.J.1089.2021.18561 URL |
| 麻超方, 叶靖, 李晓维, 等. 可调可重构的环形振荡器物理不可克隆函数[J]. 计算机辅助设计与图形学学报, 2021, 33(3):340-345. | |
| [6] |
CHEN Bin, WILLEMS J. Secret Key Generation over Biased Physical Unclonable Functions with Polar Codes[J]. IEEE Internet of Things Journal, 2019, 6(1):435-445.
doi: 10.1109/JIOT.2018.2864594 URL |
| [7] |
TEHRANIPOOR F, KARIMIAN N, YAN Wei, et al. DRAM-based Intrinsic Physically Unclonable Functions for System-level Security and Authentication[J]. IEEE Transactions on Very Large Scale Integration Systems, 2017, 25(3):1085-1097.
doi: 10.1109/TVLSI.2016.2606658 URL |
| [8] |
AMAN M, TANEJA S, SIKDAR B, et al. Token-based Security for the Internet of Things with Dynamic Energy-quality Tradeoff[J]. IEEE Internet of Things Journal, 2019, 6(2):2843-2859.
doi: 10.1109/JIoT.6488907 URL |
| [9] |
PAPPU R, RECHT B, TAYLOR J, et al. Physical One-way Functions[J]. Science, 2002, 297(5589):2026-2030.
doi: 10.1126/science.1074376 URL |
| [10] | LOFSTROM K, DAASCH W R, TAYLOR D. IC Identification Circuit Using Device Mismatch[EB/OL]. https://ieeexplore.ieee.org/document/839821, 2002-08-06. |
| [11] | GAO Yansong, RANASINGHE D C, AL-SARAWI S F, et al. Emerging Physical Unclonable Functions with Nanotechnology[EB/OL]. https://ieeexplore.ieee.org/document/7420781, 2021-04-11. |
| [12] |
GAO Yansong, AL-SARAWI S F, ABBOTT D. Physical Unclonable Functions[J]. Nature Electronics, 2020, 3(2):81-91.
doi: 10.1038/s41928-020-0372-5 URL |
| [13] | KHAN S, SHAH A P, CHOUHAN S S, et al. A Symmetric D Flip-flop Based PUF with Improved Uniqueness[EB/OL]. https://www.sciencedirect.com/science/article/abs/pii/S0026271419308005, 2021-04-22. |
| [14] | YUAN Xiaodong. D Flip-flop Based Physical Unclonable Functions[D]. Hangzhou: Zhejiang University, 2018. |
| 袁晓东. 基于D触发器的物理不可克隆函数[D]. 杭州:浙江大学, 2018. | |
| [15] | GUAJARDO J, KUMAR S S, SCHRIJEN G J, et al. FPGA Intrinsic PUFs and Their Use for IP Protection[EB/OL]. https://dl.acm.org/doi/10.1007/978-3-540-74735-2_5, 2007-10-10. |
| [16] | OROSA L, WANG Yaohua, PUDDU I, et al. Dataplant: Enhancing System Security with Low-cost In-DRAM Value Generation Primitives[EB/OL]. https://arxiv.org/abs/1902.07344v2, 2019-11-05. |
| [17] | KUMAR S S, GUAJARDO J, MAES R, et al. Extended Abstract: the Butterfly PUF Protecting IP on Every FPGA [C]//IEEE. 2008 IEEE International Workshop on Hardware-oriented Security and Trust, June 9, 2008, Anaheim, CA, USA. New Jersey: IEEE, 2008: 67-70. |
| [18] | ZHANG Peiyong, YUAN Xiaodong, WANG Xuejie, et al. D Flip-flop Based Physical Unclonable Functions[J]. Journal of ZheJiang University(Science Edition), 2019, 46(1):32-38. |
| 张培勇, 袁晓东, 王雪洁, 等. 基于D触发器的物理不可克隆函数[J]. 浙江大学学报(理学版), 2019, 46(1):32-38. | |
| [19] | KHAN S, SHAH A P, GUPTA N, et al. An Ultra-low Power, Reconfigurable, Aging Resilient RO PUF for IoT Applications[EB/OL]. https://www.sciencedirect.com/science/article/abs/pii/S0026269219303593, 2019-10-22. |
| [20] |
LIM D, LEE J W, GASSEND B, et al. Extracting Secret Keys from Integrated Circuits[J]. IEEE Transactions on Very Large Scale Integration Systems, 2005, 13(10):1200-1205.
doi: 10.1109/TVLSI.2005.859470 URL |
| [21] | NGUYEN P H, SAHOO D P, JIN Chenglu, et al. The Interpose PUF: Secure PUF Design against State-of-the-art Machine Learning Attacks[EB/OL]. https://www.researchgate.net/publication/346705656, 2019-08-10. |
| [22] | LU Lu, KIM T H. A Sequence-dependent Configurable PUF Based on 6T SRAM for Enhanced Challenge Response Space [C]//IEEE. 2019 IEEE International Symposium on Circuits and Systems(ISCAS), May 26-29, Sapporo, Japan. New Jersey: IEEE, 2019: 1-5. |
| [23] | YANG Xuan, YE Wenqiang, CUI Xiaole. Design of PUF Based on RRAM Delay Unit[J]. Acta Electronica Sinica, 2020, 48(8):1565-1571. |
| 杨轩, 叶文强, 崔小乐. 基于RRAM延时单元的PUF设计[J]. 电子学报, 2020, 48(8):1565-1571. | |
| [24] | HOU Shen, LI Jinglong, LIU Hailong, et al. Design of Lightweight Configurable Strong Physical non Clonable Function[J]. Journal of Computer-aided Design & Computer Graphics, 2021, 33(10):1627-1634. |
| 侯申, 李景龙, 刘海龙, 等. 轻量级可配置强物理不可克隆函数设计[J]. 计算机辅助设计与图形学学报, 2021, 33(10):1627-1634. | |
| [25] | SANTIAGO L, PATIL V C, PRADO C B, et al. Realizing Strong PUF from Weak PUF via Neural Computing[C]//IEEE. 2017 IEEE International Symposium on Defect and Fault Tolerance in VLSI and Nanotechnology Systems(DFT), October, 23-25, Cambridge, UK. New Jersey: IEEE, 2017: 1-6. |
| [26] | HOU Shen, GUO Yang, LI Tun, et al. A Lightweight Strong Physical Unclonable Function Design Based on LFSR[J]. Journal of Graphics, 2020, 41(1):125-131. |
| 侯申, 郭阳, 李暾, 等. 一种基于线性反馈移位寄存器的轻量级强PUF设计[J]. 图学学报, 2020, 41(1):125-131. | |
| [27] | GU Chongyan, CUI Yijun, HANLEY N, et al. Novel Lightweight FF-APUF Design for FPGA [C]//IEEE. 29th IEEE International System-on-Chip Conference(SOCC), September 6-9, 2016, Seattle, WA, USA. New Jersey: IEEE, 2016: 75-80. |
| [28] | MAITI A, GUNREDDY V, SCHAUMONT P. A Systematic Method to Evaluate and Compare the Performance of Physical Unclonable Functions[M]. Heidelberg: Springer, 2011. |
| [29] | LEE J W, LIM D, GASSEND B, et al. A Technique to Build a Secret Key in Integrated Circuits for Identification and Authentication Applications [C]//IEEE. 2004 Symposium on VLSI Circuits, June 17-19, 2004, Hawaii, USA. New Jersey: IEEE, 2004: 176-179. |
| [1] | 胡艺, 佘堃. 基于区块链和智能合约的双链车联网系统[J]. 信息网络安全, 2022, 22(8): 26-35. |
| [2] | 于克辰, 郭莉, 阴宏伟, 燕雪松. 面向数据中心场景的基于区块链与博弈论的高价值数据共享模型[J]. 信息网络安全, 2022, 22(6): 73-85. |
| [3] | 宋晶, 刁润, 周杰, 戚建淮. 工业控制系统功能安全和信息安全策略优化方法[J]. 信息网络安全, 2022, 22(11): 68-76. |
| [4] | 孟玺. 面向网络信息安全的反情报工作机制及优化策略研究[J]. 信息网络安全, 2022, 22(10): 76-81. |
| [5] | 胡博文, 周纯杰, 刘璐. 基于模糊多目标决策的智能仪表功能安全与信息安全融合方法[J]. 信息网络安全, 2021, 21(7): 10-16. |
| [6] | 于克辰, 郭莉, 姚萌萌. 基于区块链的高价值数据共享系统设计[J]. 信息网络安全, 2021, 21(11): 75-84. |
| [7] | 张敏情, 周能, 刘蒙蒙, 柯彦. 同态加密域可逆信息隐藏技术研究[J]. 信息网络安全, 2020, 20(8): 25-36. |
| [8] | 王利, 李二霞, 纪宇晨, 李小勇. 基于PUF的抗物理克隆RFID安全认证协议[J]. 信息网络安全, 2020, 20(8): 89-97. |
| [9] | 张正, 查达仁, 柳亚男, 方旭明. 基于物理不可克隆函数的Kerberos扩展协议及其形式化分析[J]. 信息网络安全, 2020, 20(12): 91-97. |
| [10] | 胡蝶, 马东堂, 龚旻, 马召. 一种基于PUF的物理层安全认证方法[J]. 信息网络安全, 2020, 20(1): 61-66. |
| [11] | 周艺华, 吕竹青, 杨宇光, 侍伟敏. 基于区块链技术的数据存证管理系统[J]. 信息网络安全, 2019, 19(8): 8-14. |
| [12] | 黎琳, 张旭霞. zk-snark的双线性对的国密化方案[J]. 信息网络安全, 2019, 19(10): 10-15. |
| [13] | 李月, 姜玮, 季佳华, 段德忠. 一种基于虚拟化平台的安全外包技术研究[J]. 信息网络安全, 2018, 18(5): 82-88. |
| [14] | 李月, 姜玮, 季佳华, 段德忠. 一种基于虚拟化平台的安全外包技术研究[J]. 信息网络安全, 2018, 18(5): 82-88. |
| [15] | 陈妍, 戈建勇, 赖静, 陆臻. 云上信息系统安全体系研究[J]. 信息网络安全, 2018, 18(4): 79-86. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||