信息网络安全 ›› 2021, Vol. 21 ›› Issue (9): 74-79.doi: 10.3969/j.issn.1671-1122.2021.09.011
基于图卷积网络的比特币非法交易识别方法
- 1.海南师范大学信息科学技术学院,海口 571158
2.数据科学与智慧教育教育部重点实验室,海口 571158
-
收稿日期:2021-06-14出版日期:2021-09-10发布日期:2021-09-22 -
通讯作者:文斌 E-mail:binwen@hainnu.edu.cn -
作者简介:郑海潇(1998—),男,河南,硕士研究生,主要研究方向为网络空间安全|文斌(1970—),男,四川,博士,教授,主要研究方向为网络空间安全、区块链服务、大数据共享与交易。 -
基金资助:国家自然科学基金(61562024);海南省自然科学基金(620RC605)
Bitcoin Illegal Transaction Identification Method Based on Graph Convolutional Network
ZHENG Haixiao1,2, WEN Bin1,2( )
)
- 1. School of Information Science and Technology, Hainan Normal University, Haikou 571158, China
2. Key Laboratory of Data Science and Smart Education of Ministry of Education, Haikou 571158, China
-
Received:2021-06-14Online:2021-09-10Published:2021-09-22 -
Contact:WEN Bin E-mail:binwen@hainnu.edu.cn
摘要:
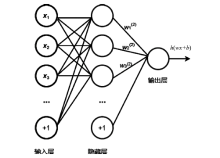
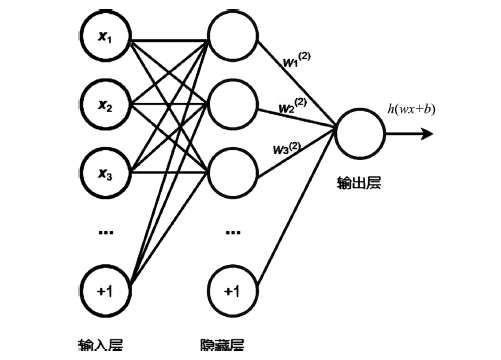
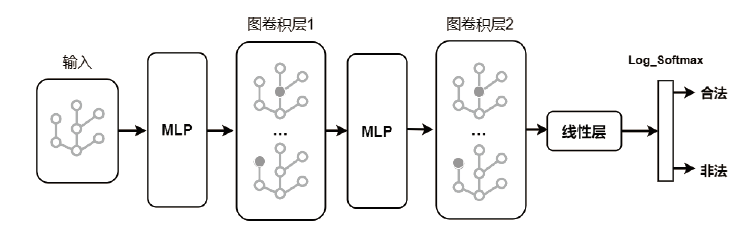
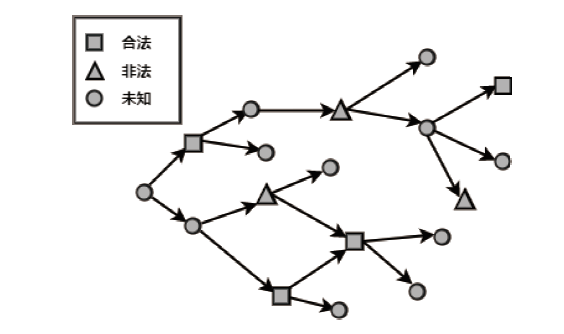
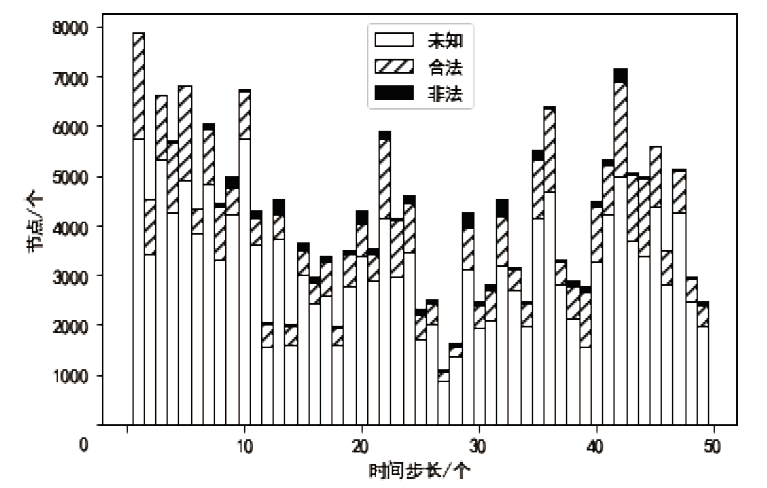
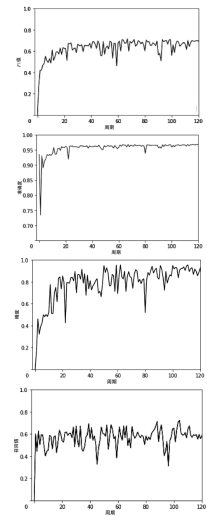
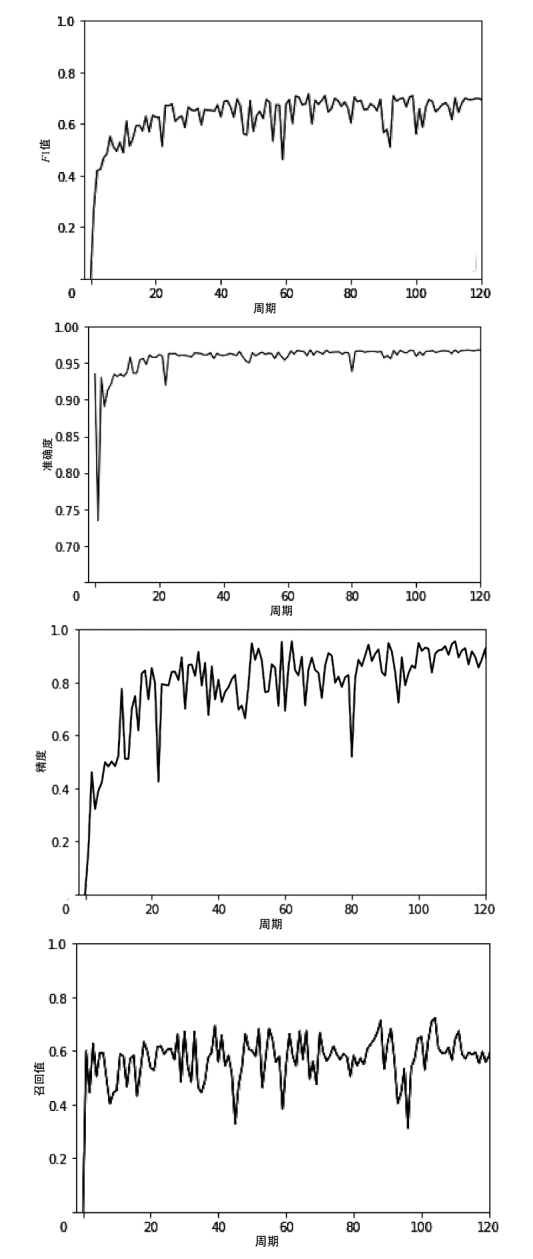
比特币作为匿名的加密数字资产逐渐成为部分非法地下交易的选择。为了净化金融市场、打击非法交易,需要对比特币网络中的非法交易活动进行识别。在相关工作的基础上,文章提出一种基于多层感知器与图卷积网络结合的检测比特币网络中非法交易的方法(Multi-layer Perceptrons + Graph Convolutional Network,MP-GCN)。MP-GCN使用多层感知器与图卷积网络组合,构建识别非法交易的模型。具体来说,在图卷积层之前和两层图卷积层中间用多层感知器进行辅助的特征提取,最后用线性层对非法交易进行划分。实验结果证明,MP-GCN达到的检测效果优于相同数据集的传统图卷积网络的检测效果。
中图分类号:
引用本文
郑海潇, 文斌. 基于图卷积网络的比特币非法交易识别方法[J]. 信息网络安全, 2021, 21(9): 74-79.
ZHENG Haixiao, WEN Bin. Bitcoin Illegal Transaction Identification Method Based on Graph Convolutional Network[J]. Netinfo Security, 2021, 21(9): 74-79.
| [1] | NAKAMOTO S. Bitcoin: A Peer-to-peer Electronic Cash System[EB/OL]. https://nakamotoinstitute.org/bitcoin/, 2008-10-31. |
| [2] | BISTARELLI S, SANTINI F. Go with the-bitcoin-flow, with Visual Analytics [C]//ACM. Proceedings of the 12th International Conference on Availability, Reliability and Security, August 29-September 1, 2017, Calabria, ITALY. New York: ACM, 2017: 1-6. |
| [3] | DECKER C, WATTENHOFER R. Information Propagation in the Bitcoin Network [C]// IEEE. IEEE P2P 2013 Proceedings, September 9-11, 2013, Trento, Italy. Piscataway: IEEE, 2013: 1-10. |
| [4] | HARLEV M A, SUN Yinhaohua, LANGENHELDT K C, et al. Breaking Bad: De-anonymising Entity Types on the Bitcoin Blockchain Using Supervised Machine Learning [C]//IEEE. Proceedings of the 51st Hawaii International Conference on System Sciences, January 2-6, 2018, Koloa, Hawaii. Piscataway: IEEE, 2018: 3497-3506. |
| [5] | MONAMO P, MARIVATE V, TWALA B. Unsupervised Learning for Robust Bitcoin Fraud Detection [C]//IEEE. 2016 Information Security for South Africa (ISSA), August 17-18, 2016, Johannesburg, SOUTH AFRICA. New York: IEEE, 2016: 129-134. |
| [6] | WEBER M, DOMENICONI G, CHEN Jie, et al. Anti-money Laundering in Bitcoin: Experimenting with Graph Convolutional Networks for Financial Forensics[EB/OL]. https://arxiv.org/abs/1908.02591, 2019-07-31. |
| [7] | ALARAB I, PRAKOONWIT S, NACER M I. Comparative Analysis Using Supervised Learning Methods for Anti-money Laundering in Bitcoin [C]//ACM. Proceedings of the 2020 5th International Conference on Machine Learning Technologies, June 19-21, 2020, Beijing, China. New York: ACM, 2020: 11-17. |
| [8] | PHAM T, LEE S. Anomaly Detection in Bitcoin Network Using Unsupervised Learning Methods[EB/OL]. https://arxiv.org/abs/1611.03941, 2016-11-12. |
| [9] | LORENZ J, SILVA M I, APARICIO D, et al. Machine Learning Methods to Detect Money Laundering in The Bitcoin Blockchain in The Presence of Label Scarcity[EB/OL]. https://arxiv.org/abs/2005.14635, 2020-05-29. |
| [10] | LI Yang, CAI Yue, TIAN Hao, et al. Identifying Illicit Addresses in Bitcoin Network [C]//Springer. International Conference on Blockchain and Trustworthy Systems, August 6-7, 2020, Dali, China. Singapore: Springer, 2020: 99-111. |
| [11] | ALARAB I, PRAKOONWIT S, NACER M I. Competence of graph Convolutional Networks for Anti-Money Laundering in Bitcoin Blockchain [C]//ACM. Proceedings of the 2020 5th International Conference on Machine Learning Technologies, June 19-21, 2020, Beijing, China. New York: ACM, 2020: 23-27. |
| [12] | ZHANG Chi, GUO Yuan, LI Ming. Review of Development and Application of Artificial Neural Network Models[J]. Computer Engineering and Applications, 2021, 57(11): 57-69. |
| 张驰, 郭媛, 黎明. 人工神经网络模型发展及应用综述[J]. 计算机工程与应用, 2021, 57(11): 57-69. | |
| [13] | KIPF T N, WELLING M. Semi-supervised Classification with Graph Convolutional Networks[EB/OL]. http://arxiv.org/abs/1609.02907, 2016-09-09. |
| [14] | DEFFERRARD M, BRESSON X, VANDERGHEYNST P. Convolutional Neural Networks on Graphs with Fast Localized Spectral Filtering [C]//ACM. Proceedings of the 30th International Conference on Neural Information Processing Systems, December 5-10, 2016, Barcelona, Spain. Red Hook: Curran Associates, 2016: 3844-3852. |
| [15] | BUSCH J, KOCHETUROV A, TRESP V, et al. NF-GNN: Network Flow Graph Neural Networks for Malware Detection and Classification [C]//ACM. 33rd International Conference on Scientific and Statistical Database Management, July 6-7, 2021, FL, Tampa, USA. New York: ACM, 2021: 121-132. |
| [16] | FEY M, LENSSEN J E. Fast Graph Representation Learning with PyTorch Geometric[EB/OL]. https://arxiv.org/abs/1903.02428, 2019-03-06. |
| [1] | 王跃东, 熊焰, 黄文超, 武建双. 一种面向5G专网鉴权协议的形式化分析方案[J]. 信息网络安全, 2021, 21(9): 1-7. |
| [2] | 顾兆军, 姚峰, 丁磊, 隋翯. 基于半实物的机场供油自控系统网络安全测试[J]. 信息网络安全, 2021, 21(9): 16-24. |
| [3] | 马玲, 覃亮成. 基于DCT-DQFT变换和QR分解的彩色图像盲水印算法[J]. 信息网络安全, 2021, 21(9): 25-31. |
| [4] | 孙力. 区块链+在线教育资源联盟信息保护机制研究与应用[J]. 信息网络安全, 2021, 21(9): 32-39. |
| [5] | 江皓臻, 江苾菲, 贺朗月, 单亦伟. 基于THD89的智能密码钥匙设计与实现[J]. 信息网络安全, 2021, 21(9): 40-45. |
| [6] | 陶云亭, 孔凡玉, 于佳, 徐秋亮. 抗量子格密码体制的快速数论变换算法研究综述[J]. 信息网络安全, 2021, 21(9): 46-51. |
| [7] | 弋晓洋, 张健. 基于图像的网络钓鱼邮件检测方法研究[J]. 信息网络安全, 2021, 21(9): 52-58. |
| [8] | 李彦霖, 蔡满春, 芦天亮, 席荣康. 遗传算法优化CNN的网站指纹攻击方法[J]. 信息网络安全, 2021, 21(9): 59-66. |
| [9] | 陈庆港, 杜彦辉, 韩奕, 刘翔宇. 基于深度可分离卷积的物联网设备识别模型[J]. 信息网络安全, 2021, 21(9): 67-73. |
| [10] | 吴克河, 程瑞, 郑碧煌, 崔文超. 电力物联网安全通信协议研究[J]. 信息网络安全, 2021, 21(9): 8-15. |
| [11] | 张永棠. 一种基于安全区域的WSN流量分析聚合方法[J]. 信息网络安全, 2021, 21(9): 80-89. |
| [12] | 杨晓琪, 白利芳, 唐刚. 基于DSMM模型的数据安全评估模型研究与设计[J]. 信息网络安全, 2021, 21(9): 90-95. |
| [13] | 靳姝婷, 何泾沙, 朱娜斐, 潘世佳. 基于本体推理的隐私保护访问控制机制研究[J]. 信息网络安全, 2021, 21(8): 52-61. |
| [14] | 鲍亮, 俞少华, 唐晓婷. 基于马尔可夫链的Web业务安全分析预警[J]. 信息网络安全, 2021, 21(8): 91-96. |
| [15] | 李群, 董佳涵, 关志涛, 王超. 一种基于聚类分类的物联网恶意攻击检测方法[J]. 信息网络安全, 2021, 21(8): 82-90. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||