信息网络安全 ›› 2021, Vol. 21 ›› Issue (9): 80-89.doi: 10.3969/j.issn.1671-1122.2021.09.012
一种基于安全区域的WSN流量分析聚合方法
- 1.广东东软学院计算机学院,佛山 528225
2.南昌工程学院协同感知与先进计算技术研究所,南昌 330003
-
收稿日期:2021-06-20出版日期:2021-09-10发布日期:2021-09-22 -
通讯作者:张永棠 E-mail:gov211@163.com -
作者简介:张永棠(1981—),男,江西,教授,博士,主要研究方向为通信及网络空间安全技术、网络安全感知。 -
基金资助:国家自然科学基金(61663029);广东省高校重点平台与特色创新项目(2020KTSCX771)
A Secure Area Based Clustering Approach for Traffic Analysis in WSN
- 1. School of Computer, Guangdong Neusoft Institute, Foshan 528225, China
2. Institute of Cooperative Sensing and Advanced Computing Technology, Nanchang Technology Institute, Nanchang 330003, China
-
Received:2021-06-20Online:2021-09-10Published:2021-09-22 -
Contact:ZHANG Yongtang E-mail:gov211@163.com
摘要:
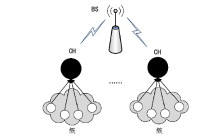
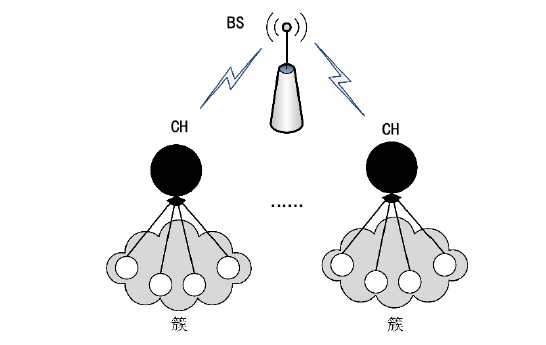
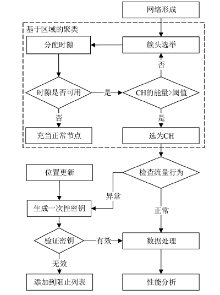
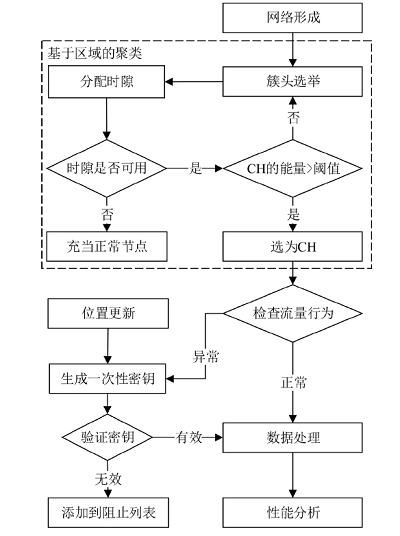
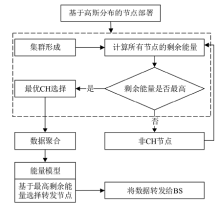
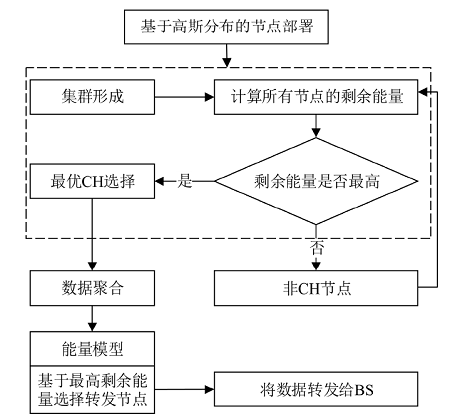
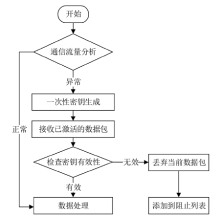
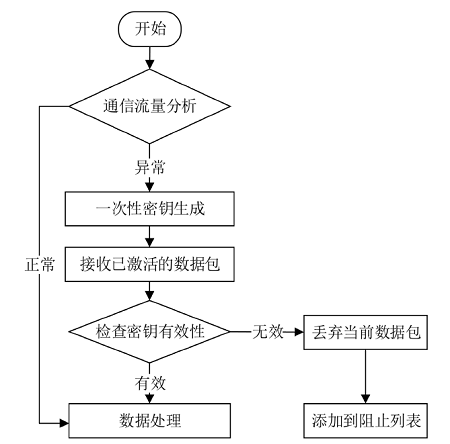
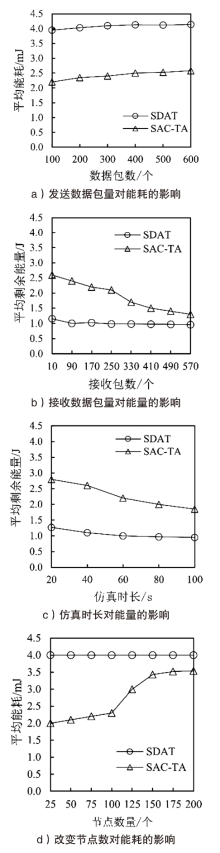
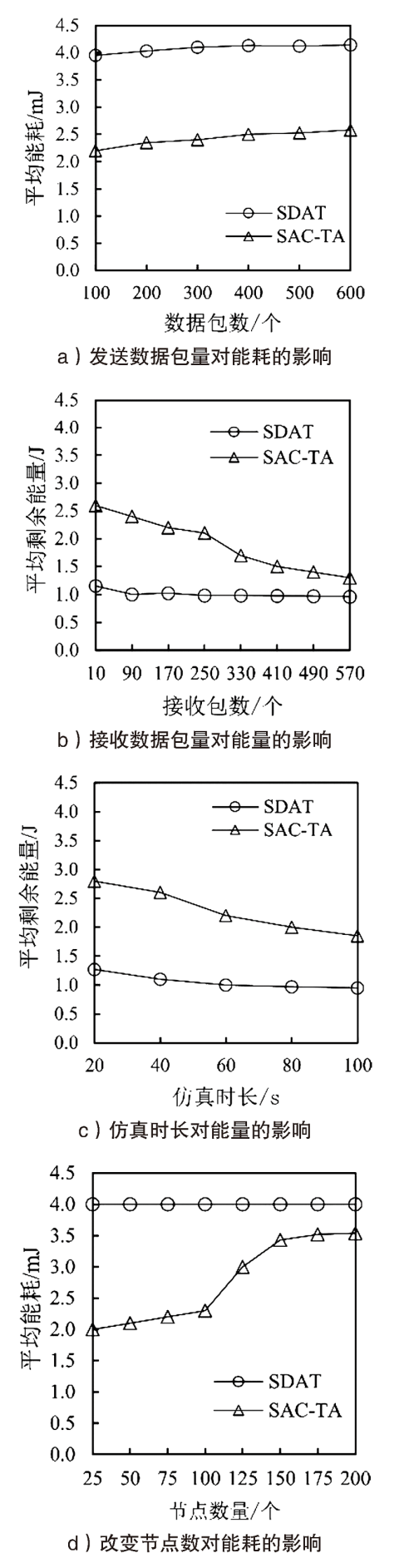
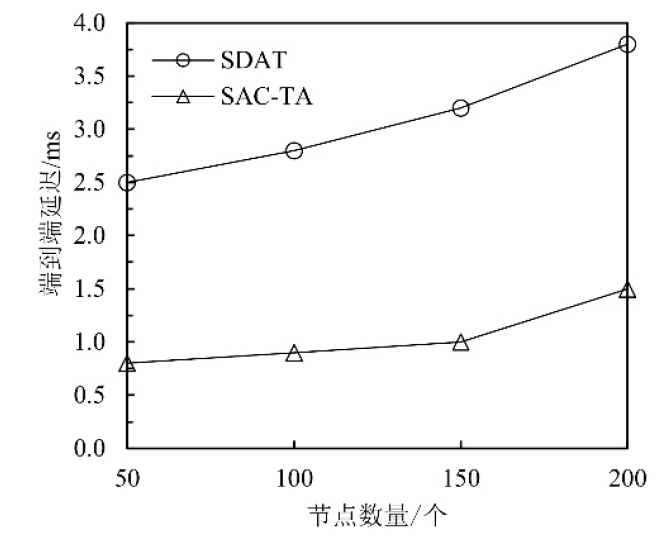
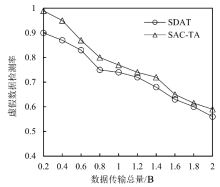
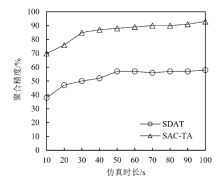
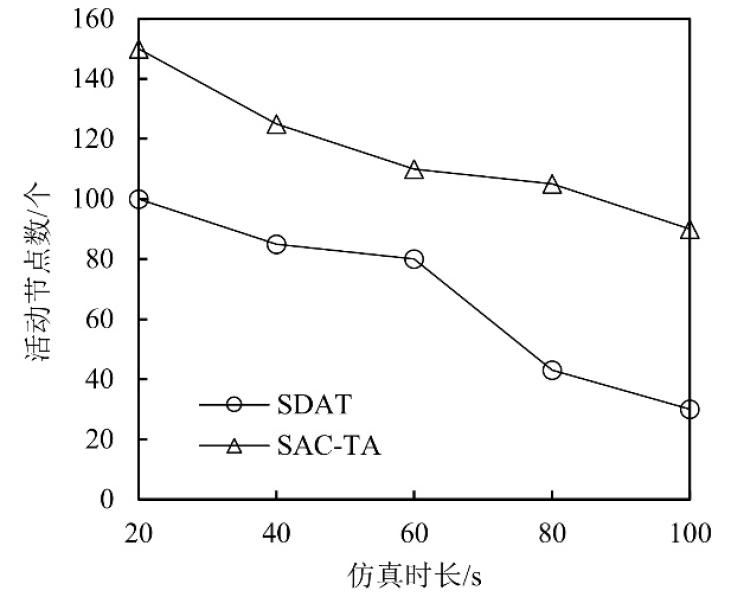
聚类是无线传感器网络中最重要的任务,其特点是通过簇头(Cluster Head,CH)进行数据聚合,降低了通信成本。由于无线传感器网络部署在远程和敌对环境中进行敏感信息的传输,使得传感器节点更容易受到虚假的数据注入攻击。为克服这些问题,提高网络的安全性,文章提出一种基于安全区域的无线传感器网络流量分析聚类方法。将传感器网络聚类成小簇,每个簇都有一个CH来管理和收集来自正常传感器节点的信息。根据预定义的时隙、簇中心和最高剩余能量来选择CH。基于流量分析和一次性密钥生成过程对收集到的数据进行验证,以识别路由上的恶意节点,提供一个安全的数据收集过程,提高能源效率。仿真结果表明,与现有的安全数据聚合技术相比,文章所提基于安全区域的流量分析聚类方法具有更低的平均能耗、更低的端到端延迟、更高的平均剩余能量、更高的数据聚合精度和错误数据检测率。
中图分类号:
引用本文
张永棠. 一种基于安全区域的WSN流量分析聚合方法[J]. 信息网络安全, 2021, 21(9): 80-89.
ZHANG Yongtang. A Secure Area Based Clustering Approach for Traffic Analysis in WSN[J]. Netinfo Security, 2021, 21(9): 80-89.
| [1] |
GOPIKRISHNAN S, PRIAKANTH P. HSDA: Hybrid Communication for Secure Data Aggregation in Wireless Sensor Network[J]. Wireless Networks, 2017, 22(3): 1-18.
doi: 10.1007/s11276-015-0946-8 URL |
| [2] | YU Xiuwu, XIE Xiaoyong, LIANG Beikong, et al. A Deep Mine WSN Localization Algorithm Based on Both Particle Swarm Optimization and Tunnel Partition[J]. China Safety Science Journal, 2019, 29(2): 170-175. |
| 余修武, 谢晓永, 梁北孔, 等. 基于粒子群优化和巷道分区的深井WSN定位算法[J]. 中国安全科学学报, 2019, 29(2): 170-175. | |
| [3] |
XIAN Guangli, WEI Dengjia, YU Benzhi, et al. Aggregation Tree Statistical Computing Based on Functional Encryption[J]. Wuhan University Journal of Natural Sciences, 2019, 24(2): 116-124.
doi: 10.1007/s11859-019-1376-8 URL |
| [4] | HU Xiangdong, XING Youquan, HE Wenxiang. An Energy-efficient Secure Clustering Algorithm Fusing Reputation Evaluation and Patrol Mechanism for WSN[J]. Telecommunication Engineering, 2019, 59(2): 125-132. |
| 胡向东, 邢有权, 何文祥. 融合信誉评估与巡查机制的WSN能量高效安全成簇算法[J]. 电讯技术, 2019, 59(2): 125-132. | |
| [5] | CHEN Xingshu, CHEN Jinghan, SHAO Guolin, et al. A Covert Communication Behavior Detection Method Based on Session Flow Aggregation[J]. Journal of University of Electronic Science and Technology of China, 2019, 48(3): 388-396. |
| 陈兴蜀, 陈敬涵, 邵国林, 等. 基于会话流聚合的隐蔽性通信行为检测方法[J]. 电子科技大学学报, 2019, 48(3): 388-396. | |
| [6] | YING Kezhen, ZHOU Xiannian, MAO Keji. Data Acquisition Algorithm in Wireless Sensor Network Based on Improved Region Growing Method[J]. Journal of Chinese Computer Systems, 2019, 40(3): 567-572. |
| 应可珍, 周贤年, 毛科技, 等. 一种改进区域生长法的WSN数据采集算法研究[J]. 小型微型计算机系统, 2019, 40(3): 567-572. | |
| [7] | MA Dongchao, SUN Xingguo, MA Li. A Regulatable Model Based on Data Aggregation in WSN[J]. Chinese Journal of Computers, 2019, 42(2): 437-452. |
| 马东超, 孙兴国, 马礼. 一种基于数据聚合的传感器网络可调模型[J]. 计算机学报, 2019, 42(2): 437-452. | |
| [8] |
WARD J R, YOUNIS M. Cross-layer Traffic Analysis Countermeasures Against Adaptive Attackers of Wireless Sensor Networks[J]. Wireless Networks, 2019, 25(5): 2869-2887.
doi: 10.1007/s11276-019-02003-9 URL |
| [9] |
ISLAM M, FAHMIN A, HOSSAIN M S, et al. Denial-of-Service Attacks on Wireless Sensor Network and Defense Techniques[J]. Wireless Personal Communications, 2021, 116(4): 1-29.
doi: 10.1007/s11277-020-07702-7 URL |
| [10] |
SONG W, BEASLEY M, PRZYSTUPA K, et al. A Software Deep Packet Inspection System for Network Traffic Analysis and Anomaly Detection[J]. Sensors, 2020, 20(6): 1637-1678.
doi: 10.3390/s20061637 URL |
| [11] |
HAJIAN R, ERFANI S H. CHESDA: Continuous Hybrid And Energy-efficient Secure Data Aggregation For WSN[J]. The Journal of Supercomputing, 2021, 77(5): 5045-5075.
doi: 10.1007/s11227-020-03455-z URL |
| [12] |
PANKHURST R J. Key Generation by Computer[J]. Nature, 2019, 227(5264): 1269-1270.
doi: 10.1038/2271269a0 URL |
| [13] | SONI A, UPADHYAY R, KUMAR A. Performance Improvement of Wireless Secret Key Generation with Colored Noise for IoT[J]. International Journal of Communication Systems, 2019, 32(8): 4124-4137. |
| [14] |
LI GANG, ZHANG ZHE, YU YANG, et al. A Hybrid Information Reconciliation Method for Physical Layer Key Generation[J]. Entropy, 2019, 21(7): 84-90.
doi: 10.3390/e21010084 URL |
| [15] |
BALDI M, CHIARALUCE F, INCIPINI L, et al. Code-based Physical Layer Secret Key Generation in Passive Optical Networks[J]. Ad Hoc Networks, 2019, 89(6): 1-8.
doi: 10.1016/j.adhoc.2019.02.003 URL |
| [16] |
JIAO LING, WANG NING, WANG Peng, et al. Physical Layer Key Generation in 5G Wireless Networks[J]. IEEE Wireless Communications, 2019, 26(5): 48-54.
doi: 10.1109/MWC.7742 URL |
| [17] |
HAZAY C, MIKKELSEN G L, RABIN T, et al. Efficient RSA Key Generation and Threshold Paillier in the Two-party Setting[J]. Journal of Cryptology, 2019, 32(2): 265-323.
doi: 10.1007/s00145-017-9275-7 URL |
| [18] | ZHANG Yongtang. C-RAN Dynamic Resource Allocation Method for DRL. Journal of Chinese Computer Systems, 2021, 42(1): 132-136. |
| 张永棠. 一种深度强化学习的C-RAN动态资源分配方法[J]. 小型微型计算机系统, 2021, 42(1): 132-136. | |
| [19] | CHEN Liangchen, GAO Shu, LIU Baoxu, et al. Research Status and Development Trends on Network Encrypted Traffic Identification[J]. Netinfo Security, 2019, 19(3): 25-31. |
| 陈良臣, 高曙, 刘宝旭, 等. 网络加密流量识别研究进展及发展趋势[J]. 信息网络安全, 2019, 19(3): 25-31. | |
| [20] | WANG Lele, WANG Binqiang, LIU Jiangang, et al. Study on Malicious Program Detection Based on Recurrent Neural Network[J]. Computer Science, 2019, 46(7): 92-96. |
| 王乐乐, 汪斌强, 刘建港, 等. 基于递归神经网络的恶意程序检测研究[J]. 计算机科学, 2019, 46(7): 92-96. | |
| [21] | SINGH P, GUPTA A K, SINGH R. Improved Priority-based Data Aggregation Congestion Control Protocol[J]. Modern Physics Letters B, 2019, 34(2): 1-19. |
| [22] |
CHANG J, LIU F. A Byzantine Sensing Network Based on Majority-ponsensus Data Aggregation Mechanism[J]. Sensors, 2021, 21(1): 248-264.
doi: 10.3390/s21010248 URL |
| [1] | 江金芳, 韩光洁. 无线传感器网络中信任管理机制研究综述[J]. 信息网络安全, 2020, 20(4): 12-20. |
| [2] | 亢保元, 王佳强, 邵栋阳, 李春青. 一种适用于异构Ad Hoc无线传感器网络的身份认证与密钥共识协议[J]. 信息网络安全, 2018, 18(1): 23-30. |
| [3] | 章红艳, 许力, 林丽美. 无线传感器网络中基于超立方体的对密钥建立方案研究[J]. 信息网络安全, 2017, 17(12): 1-5. |
| [4] | 钟敦昊, 张冬梅, 张玉. 一种基于相似度计算的无线传感器网络入侵检测方法[J]. 信息网络安全, 2016, 16(2): 22-27. |
| [5] | 刘伟, 叶清, 王成. 基于动态密钥管理的改进LEACH路由算法[J]. 信息网络安全, 2015, 15(8): 41-46. |
| [6] | 苏彬庭, 方禾, 许力. 基于Q-Learning的无线传感器网络生命周期平衡路由[J]. 信息网络安全, 2015, 15(4): 74-77. |
| [7] | 龚婉婉, 刘士兴, 冯婷婷. 基于无线传感器网络的智能家居监控平台设计[J]. 信息网络安全, 2015, 15(3): 79-83. |
| [8] | 仇各各, 汪学明, 张言胜. 基于HECC的WSN身份认证协议研究[J]. 信息网络安全, 2015, 26(12): 54-58. |
| [9] | 石沙沙, 孙文红, 江明建, 曲海鹏. 基于分布式数据聚合的智能电网隐私保护协议研究[J]. 信息网络安全, 2015, 26(12): 59-65. |
| [10] | 杨骏玮, 方杰, 张仕斌, 陈建钧. WSNs中基于重复博弈的信任评价方法研究[J]. 信息网络安全, 2014, 14(8): 82-87. |
| [11] | 佟鑫;张利;戴明. 物联网感知层安全威胁建模研究[J]. , 2013, 13(Z): 0-0. |
| [12] | 郎为民;陈林;王昊. 无线传感器网络云连接认证研究[J]. , 2013, 13(3): 0-0. |
| [13] | 高立兵. 基于无线传感器网络的井下定位系统研究[J]. , 2013, 13(2): 0-0. |
| [14] | 卢伟龙. 基于公钥密码体制的动态无线传感器网络安全数据聚合研究[J]. , 2013, 13(12): 0-0. |
| [15] | 张婷婷;夏戈明;吴伟彬. 安全与应急响应的监测型移动传感器网络系统[J]. , 2013, 13(11): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||