信息网络安全 ›› 2021, Vol. 21 ›› Issue (11): 17-27.doi: 10.3969/j.issn.1671-1122.2021.11.003
基于攻击识别的网络安全度量方法研究
- 北京理工大学计算机学院,北京 100081
-
收稿日期:2021-07-08出版日期:2021-11-10发布日期:2021-11-24 -
通讯作者:赵小林 E-mail:zhaoxl@bit.edu.cn -
作者简介:赵小林(1971—),男,山西,副教授,博士,主要研究方向为网络空间安全、软件安全理论|赵斌(1997—),男,内蒙古,硕士研究生,主要研究方向为网络空间安全、软件安全理论|赵晶晶(1996—),女,山西,硕士研究生,主要研究方向为网络空间安全、软件安全理论|薛静锋(1975—),男,陕西,教授,博士,主要研究方向为网络安全、数据安全、软件安全、软件测试 -
基金资助:国家重点研发计划项目(2020YFB1712104);山东省重大科技创新工程项目(2020CXGC010116)
Research on Network Security Measurement Method Based on Attack Identification
ZHAO Xiaolin( ), ZHAO Bin, ZHAO Jingjing, XUE Jingfeng
), ZHAO Bin, ZHAO Jingjing, XUE Jingfeng
- School of Computer Science and Technology, Beijing Institute of Technology, Beijing 100081
-
Received:2021-07-08Online:2021-11-10Published:2021-11-24 -
Contact:ZHAO Xiaolin E-mail:zhaoxl@bit.edu.cn
摘要:
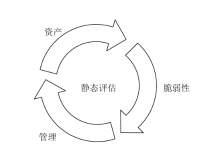
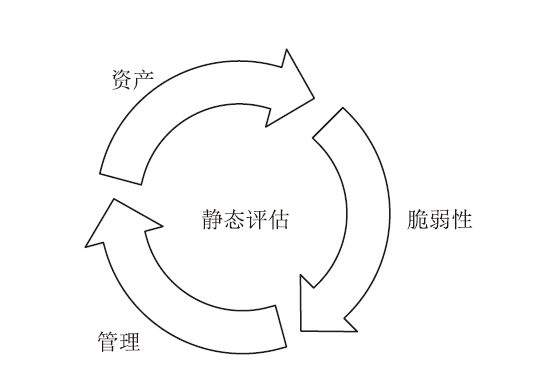
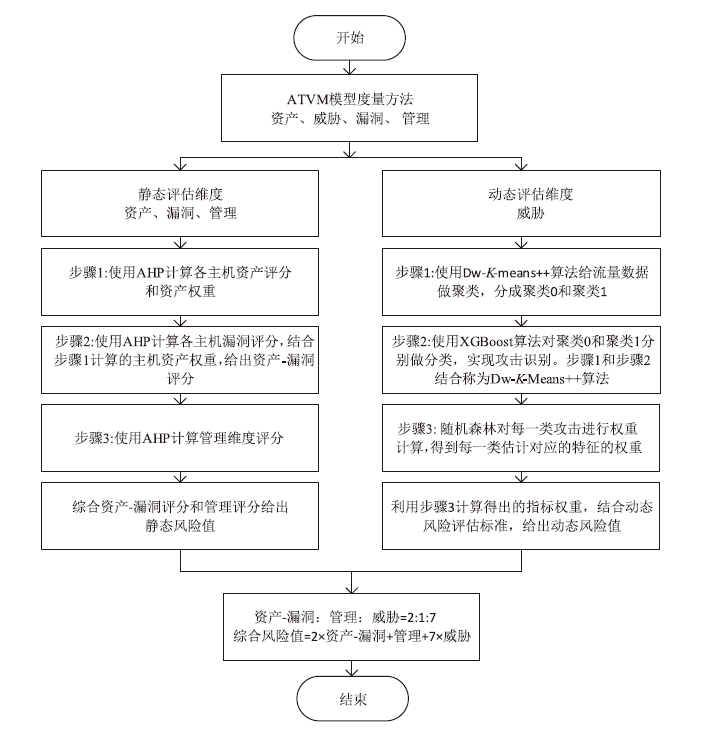
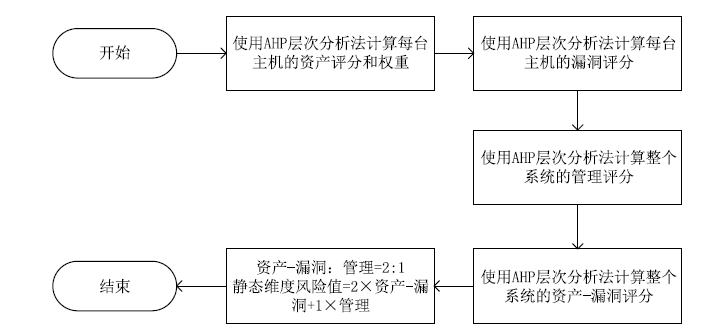
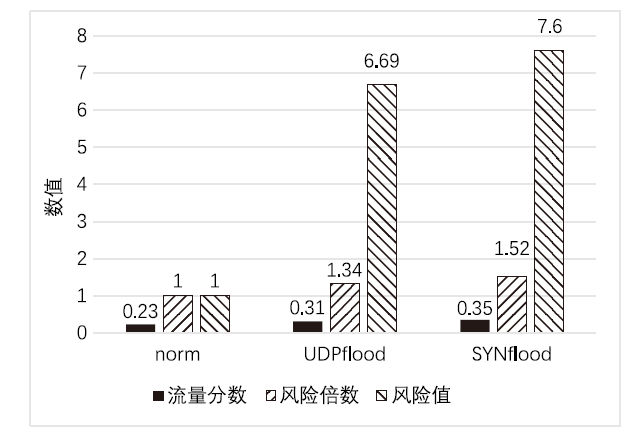
目前,传统系统安全状态评估准则多为定性评估,其不足之处是不能量化风险,而定量评估方法大多存在评估不全面、识别攻击的精确率较低等问题。攻击识别技术对网络安全度量具有重要作用,文章采用静态评估与动态评估相结合的资产威胁脆弱性管理网络安全度量模型。静态评估使用AHP层次分析法,结合通用漏洞评分系统给出资产漏洞评分和管理评分。动态评估使用Dw-K-means++算法和XGBoost方法相结合,优化攻击识别的效果。综合静态评估与动态评估,给出网络系统总体的评估结果。文章使用公开数据集CICIDS2017证明了Dw-K-means++算法在大型数据集上的聚类优势,同时使用基于仿真实验的数据验证了网络安全度量模型的有效性。
中图分类号:
引用本文
赵小林, 赵斌, 赵晶晶, 薛静锋. 基于攻击识别的网络安全度量方法研究[J]. 信息网络安全, 2021, 21(11): 17-27.
ZHAO Xiaolin, ZHAO Bin, ZHAO Jingjing, XUE Jingfeng. Research on Network Security Measurement Method Based on Attack Identification[J]. Netinfo Security, 2021, 21(11): 17-27.
表1
节点资产得分
| 主机 | 权重向量 | 属性分值 向量 | 主机资产 评分 | 主机资产 权重 |
|---|---|---|---|---|
| Host0 | [0.169,0.371,0.259,0.201] | [1,3,3,3] | 2.137 | 0.073 |
| Host1 | [0.48, 0.24, 0.16, 0.12] | [3,2,3,3] | 2.76 | 0.117 |
| Host2 | [0.523,0.211,0.146,0.12] | [1,2,1,3] | 1.135 | 0.039 |
| Host3 | [0.202,0.157,0.358,0.283] | [1,1,1,3] | 0.824 | 0.028 |
| Host4 | [0.315,0.469,0.137,0.079] | [5,5,1,5] | 4.452 | 0.153 |
| Host5 | [0.274,0.538,0.114,0.074] | [5,7,3,5] | 5.848 | 0.201 |
| Host6 | [0.226,0.092,0.092,0.59] | [1,1,5,5] | 3.728 | 0.128 |
| Host7 | [0.486,0.08,0.207,0.227] | [4,1,3,5] | 3.780 | 0.13 |
| Host8 | [0.4975,0.7753,0.2372, 0.3084] | [1,2,1,5] | 3.827 | 0.131 |
表3
各节点漏洞得分向量
| 主机 | 可用性权重 | 影响性权重 | 主机脆弱性 评分 | 资产—漏洞 评分 |
|---|---|---|---|---|
| Host0 | [0.169,0.168,0.164] | [0.106,0.166,0.228] | 3.123 | 0.228 |
| Host1 | [0.229,0.271] | [0.153,0.347] | 3.9989 | 0.468 |
| Host2 | 0.5 | 0.5 | 3.8 | 0.148 |
| Host3 | 0 | 0 | 0 | 0 |
| Host4 | [0.167,0.167,0.167] | [0.207,0.086,0.207] | 3.123 | 0.228 |
| Host5 | [0.169,0.168,0.164] | [0.106,0.166,0.228] | 4.522 | 0.692 |
| Host6 | 0 | 0 | 0 | 0 |
| Host7 | [0.193,0.181,0.149] | [0.135,0.135,0.230] | 4.0378 | 0.525 |
| Host8 | 0 | 0 | 0 | 0 |
| [1] | SHI Leyi, LIU Jia, LIU Weihao, et al. Survey of Research on Network Security Situation Awareness[J]. Computer Engineering and Applications, 2019, 55(24):1-9. |
| 石乐义, 刘佳, 刘伟豪, 等. 网络安全态势感知研究综述[J]. 计算机工程与应用, 2019, 55(24):1-9. | |
| [2] | DU Jiawei, ZHOU Ying, GUO Ronghua, et al. Network Security Situational Awareness[M]. Beijing: China Machine Press, 2018. |
| 杜嘉薇, 周颖, 郭荣华, 等. 网络安全态势感知[M]. 北京: 机械工业出版社, 2018. | |
| [3] | LI Xuebin, FAN Jiulun, LIU Yixian. On Information System Vulnerabilities Assess Based on Analytic Hierarchy Process and Common Vulnerability Score System[J]. Journal of Xi’an University of Post and Telecommunications, 2016, 21(1):42-46. |
| 黎学斌, 范九伦, 刘意先. 基于AHP和CVSS的信息系统漏洞评估[J]. 西安邮电大学学报, 2016, 21(1):42-46. | |
| [4] | LIU Zhiming, LI Sheng, HE Jin, et al. Complex Network Security Analysis Based on Attack Graph Model[C]// IEEE. 2012 Second International Conference on Instrumentation, Measurement, Computer, Communication and Control, December 8-10, 2012, Harbin, China. Piscataway: IEEE, 2012: 183-186. |
| [5] | FENG Yi, HUANG Yicai, FU Zhengxin. A Logic-based Attack Graph for Analyzing Network Security Risk Against Potential Attack[C]// IEEE. 2018 IEEE International Conference on Networking, Architecture and Storage(NAS), October 11-14, 2018, Chongqing, China. Piscataway: IEEE, 2018: 1-4. |
| [6] | SANTOSH K, ANURADHA N, KESHAV P, et al. Evaluation of Network Risk Using Attack Graph Based Security Metrics[C]// IEEE. 2016 IEEE 14th International Conference on Dependable, Autonomic and Secure Computing, August 8-12, 2016, Auckland, NewZealand. Piscataway: IEEE, 2016: 91-93. |
| [7] | WANG Jiao, FAN Kefeng, MO Wei, et al. A Method for Information Security Risk Assessment Based on the Dynamic Bayesian Network[C]// IEEE. 2016 International Conference on Networking and Network Applications (NaNA), July 23-25, 2016, Hakodate, Japan. Piscataway: IEEE, 2016: 279-283. |
| [8] | KOTENKO I, PARASHCHUK I. An Approach to Modeling the Decision Support Process of the Security Event and Incident Management Based on Markov Chains[J]. IFAC-PapersOnLine, 2019, 52(13):934-939. |
| [9] | LI Xi, LU Yu, NIE Wei. Network Security Situation Assessment Method Based on Markov Game Model[J]. KSII Transactions on Internet and Information Systems, 2018, 12(5):2414-2428. |
| [10] | HAYATLE O, OTROK H, YOUSSEF A. A Markov Decision Process Model for High Interaction Honeypots[J]. Information Security Journal, 2013, 22(4):159-170. |
| [11] | ZHAO Zhongwei, ZHOU Tingting, WANG Huan. Quantitative Evaluation Model of Network Security Situation Based on D-S Evidence Theory[C]// IEEE. 2019 6th International Conference on Dependable Systems and Their Applications (DSA), January 1-3, 2020, Harbin, China. Piscataway: IEEE, 2020: 371-376. |
| [12] | LIU Zihao, ZHANG Bin, ZHU Ning, et al. Hierarchical Network Threat Situation Assessment Method for DDoS Based on D-S Evidence Theory[C]// IEEE. 2017 IEEE International Conference on Intelligence and Security Informatics (ISI), July 22-24, 2017, Beijing, China. Piscataway: IEEE, 2017: 49-53. |
| [13] | ANAND S J V, PRANAV I, NEETISH M, et al. Network Intrusion Detection Using Improved Genetick-means Algorithm[C]// IEEE. 2018 International Conference on Advances in Computing, Communications and Informatics (ICACCI), September 19-22, 2018, Bangalore, India. Piscataway: IEEE, 2018: 2441-2446. |
| [14] | CHEN Tianqi, GUESTRIN C. XGBoost: A Scalable Tree Boosting System[C]// ACM. Proceedings of the 22nd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, August 13-17, 2016, San Francisco, CA, United States. New York: ACM, 2016: 785-794. |
| [15] | CALISIR S, ATAY R, PEHLIVANOĞLU M K, et al. Intrusion Detection Using Machine Learning and Deep Learning Techniques[C]// IEEE. 2019 4th International Conference on Computer Science and Engineering (UBMK), September 1-3, 2019, Samsun, Turkey. Piscataway: IEEE, 2019: 656-660. |
| [16] |
HU Changzhen. Calculation of the Behavior Utility of a Network System: Conception and Principle[J]. Engineering, 2018, 4(1):78-84.
doi: 10.1016/j.eng.2018.02.010 URL |
| [17] |
ZHAO Xiaolin, ZHANG Yiman, SHAN Chun, et al. Research on Network Risk Evaluation Method Based on a Differential Manifold[J]. IEEE Access, 2020, 8(4):66315-66326.
doi: 10.1109/Access.6287639 URL |
| [18] |
ZHAO Xiaolin, CHEN Quanbao, XUE Jingfeng, et al. A Method for Calculating Network System Security Risk Based on a Lie Group[J]. IEEE Access, 2019, 7(5):70610-70623.
doi: 10.1109/Access.6287639 URL |
| [19] | SUN Hongyu, HE Yuan, WANG Jice, et al. Application of Artificial Intelligence Technology in the Field of Security Vulnerability[J]. Journal on Communications, 2018, 39(8):1-17. |
| 孙鸿宇, 何远, 王基策, 等. 人工智能技术在安全漏洞领域的应用[J]. 通信学报, 2018, 39(8):1-17. | |
| [20] | SHARAFALDIN I, LASHKARI A H, GHORBANI A A. Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization[EB/OL]. https://www.scitepress.org/Link.aspx?doi=10.5220/0006639801080116, 2018-01-22. |
| [1] | 顾兆军, 姚峰, 丁磊, 隋翯. 基于半实物的机场供油自控系统网络安全测试[J]. 信息网络安全, 2021, 21(9): 16-24. |
| [2] | 蔡满春, 王腾飞, 岳婷, 芦天亮. 基于ARF的Tor网站指纹识别技术[J]. 信息网络安全, 2021, 21(4): 39-48. |
| [3] | 吴佳明, 熊焰, 黄文超, 武建双. 一种基于距离导向的模糊测试变异方法[J]. 信息网络安全, 2021, 21(10): 63-68. |
| [4] | 金志刚, 王新建, 李根, 岳顺民. 融合攻击图和博弈模型的网络防御策略生成方法[J]. 信息网络安全, 2021, 21(1): 1-9. |
| [5] | 刘大恒, 李红灵. QR码网络钓鱼检测研究[J]. 信息网络安全, 2020, 20(9): 42-46. |
| [6] | 李世斌, 李婧, 唐刚, 李艺. 基于HMM的工业控制系统网络安全状态预测与风险评估方法[J]. 信息网络安全, 2020, 20(9): 57-61. |
| [7] | 毕亲波, 赵呈东. 基于STRIDE-LM的5G网络安全威胁建模研究与应用[J]. 信息网络安全, 2020, 20(9): 72-76. |
| [8] | 来疆亮, 侯一凡, 卢旭明. 基于信息度量和损耗的网络安全系统综合效能分析研究[J]. 信息网络安全, 2020, 20(8): 81-88. |
| [9] | 冉金鹏, 王翔, 赵尚弘, 高航航. 基于果蝇优化的虚拟SDN网络映射算法[J]. 信息网络安全, 2020, 20(6): 65-74. |
| [10] | 孟相如, 徐江, 康巧燕, 韩晓阳. 基于熵权VIKOR的安全虚拟网络映射算法[J]. 信息网络安全, 2020, 20(5): 21-28. |
| [11] | 刘建伟, 韩祎然, 刘斌, 余北缘. 5G网络切片安全模型研究[J]. 信息网络安全, 2020, 20(4): 1-11. |
| [12] | 赵志岩, 纪小默. 智能化网络安全威胁感知融合模型研究[J]. 信息网络安全, 2020, 20(4): 87-93. |
| [13] | 黎水林, 祝国邦, 范春玲, 陈广勇. 一种新的等级测评综合得分算法研究[J]. 信息网络安全, 2020, 20(2): 1-6. |
| [14] | 刘永磊, 金志刚, 郝琨, 张伟龙. 基于STRIDE和模糊综合评价法的移动支付系统风险评估[J]. 信息网络安全, 2020, 20(2): 49-56. |
| [15] | 郭启全, 张海霞. 关键信息基础设施安全保护技术体系[J]. 信息网络安全, 2020, 20(11): 1-9. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||