信息网络安全 ›› 2019, Vol. 19 ›› Issue (8): 22-28.doi: 10.3969/j.issn.1671-1122.2019.08.004
网络攻击检测中流量数据抽样技术研究
- 1.武汉理工大学计算机科学与技术学院,湖北武汉 430063
2.中国科学院信息工程研究所,北京 100049
3.中国劳动关系学院应用技术学院,北京 100048
4.中国科学院大学网络空间安全学院,北京 100049
-
收稿日期:2019-04-15出版日期:2019-08-10发布日期:2020-05-11 -
作者简介:作者简介:陈良臣(1982—),男,湖北,讲师,博士研究生,主要研究方向为大数据、网络攻防技术和安全态势感知;刘宝旭(1972—),男,山东,研究员,博士,主要研究方向为网络攻防技术、安全态势感知;高曙(1967—),女,安徽,教授,博士,主要研究方向为大数据处理、可视化分析。
-
基金资助:国家自然科学基金[61802404,61602470];北京市科委重点研究项目[D181100000618003];中国劳动关系学院院级重点科研项目[17YZ004];中国劳动关系学院中央高校基本科研业务费专项基金[19ZYJS007];中国劳动关系学院教学与改革项目[JG1739]
Research on Traffic Data Sampling Technology in Network Attack Detection
Liangchen CHEN1,2,3, Baoxu LIU2,4( ), Shu GAO1
), Shu GAO1
- 1. School of Computer Science and Technology, Wuhan University of Technology, Wuhan Hubei 430063, China
2. Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100049, China
3. School of Applied Technology, China University of Labor Relations, Beijing 100048, China
4. School of Cyber Security, University of Chinese Academy of Sciences, Beijing 100049, China
-
Received:2019-04-15Online:2019-08-10Published:2020-05-11
摘要:
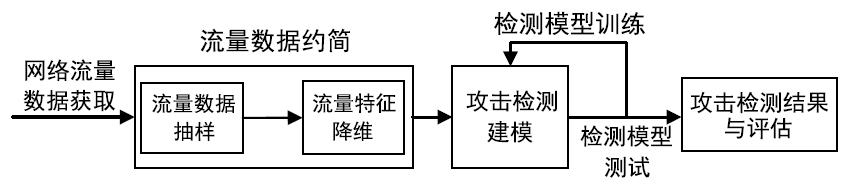
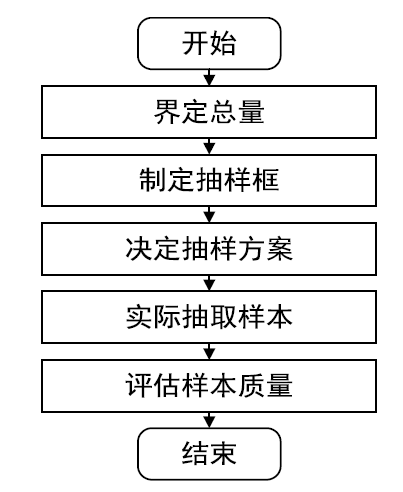
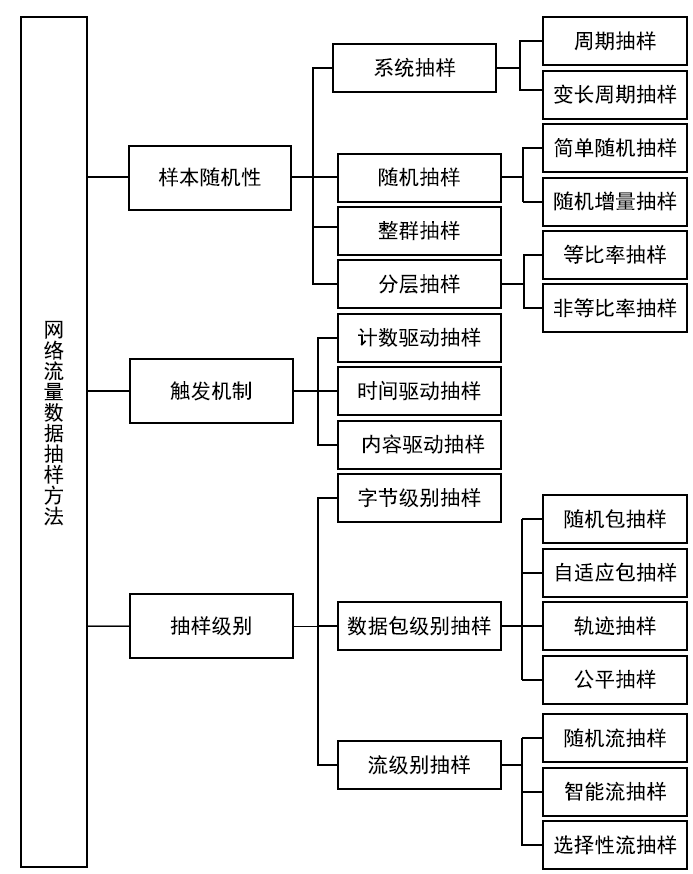
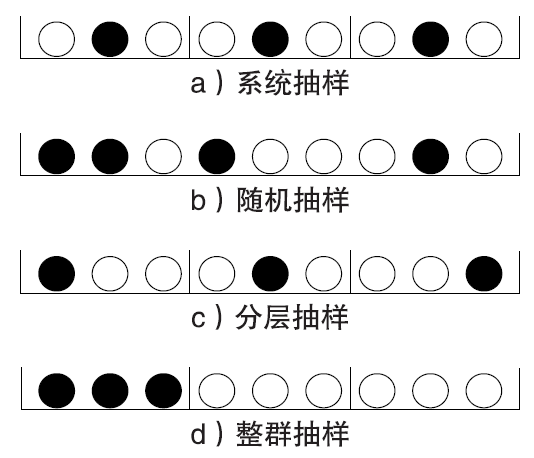
网络攻击检测的关键是通过对网络流量的分析快速识别网络中的未知攻击行为。大数据环境下,如何在不影响异常检测效果的前提下通过数据抽样技术粗粒度减少需要处理的网络流量数据,筛选出需要进行细粒度异常检测的子集,为网络攻击发现提供可靠数据支撑,是网络入侵检测系统研究的重要问题,也是目前网络行为分析、网络测量分析、网络异常检测、网络流量模型研究的重点。文章对网络攻击检测中流量数据抽样技术的基本概念、研究进展和存在问题进行阐述,对网络流量数据抽样技术面临的挑战和发展趋势进行总结和展望。文章可为进一步探索网络攻击检测领域的新方法和新技术提供借鉴和参考。
中图分类号:
引用本文
陈良臣, 刘宝旭, 高曙. 网络攻击检测中流量数据抽样技术研究[J]. 信息网络安全, 2019, 19(8): 22-28.
Liangchen CHEN, Baoxu LIU, Shu GAO. Research on Traffic Data Sampling Technology in Network Attack Detection[J]. Netinfo Security, 2019, 19(8): 22-28.
| [1] | USSATH M, JAEGER D, CHENG Feng, et al.Advanced Persistent Threats: Behind the Scenes[C]//IEEE. Annual Conference on Information Science and Systems, March 16-18, 2016, Princeton, NJ, USA. NJ: IEEE, 2016: 181-186. |
| [2] | GUAN Lei, HU Guangjun, WANG Zhuan.Research on Network Security Situational Awareness Technology Based on Big Data[J]. Netinfo Security, 2016, 16(9): 45-50. |
| 管磊,胡光俊,王专.基于大数据的网络安全态势感知技术研究[J].信息网络安全,2016,16(9):45-50. | |
| [3] | NIU Weina.Research on Exfiltration Complex Network Attack Modeling and Identification Method[D]. Chengdu: University of Electronic Science and Technology in China, 2018. |
| 牛伟纳. 窃密型复杂网络攻击建模与识别方法研究[D].成都:电子科技大学,2018. | |
| [4] | NING Zhuo, GONG Jian, GU Wenjie.Sampling Method for IDS in High Bandwidth Network[J]. Journal on Communications, 2009, 30(11): 27-36. |
| 宁卓,龚俭,顾文杰. 高速网络中入侵检测的抽样方法[J]. 通信学报,2009,30(11):27-36. | |
| [5] | ZHAI Jinfeng, SUN Libo, LU Kai, et al.Research on Flow Sampling Algorithm Based on Counting Bloom Filter[J]. Computer Engineering, 2018, 44(8): 279-284. |
| 翟金凤,孙立博,鲁凯,等. 基于Counting Bloom Filter的流抽样算法研究[J]. 计算机工程,2018,44(8):279-284. | |
| [6] | LUO Ling.Anomaly Detection of Backbone Network Based on Dimensionality Reduction[D]. Hefei: University of Science and Technology of China, 2015. |
| 罗玲. 基于降维的骨干网流量异常检测研究[D].合肥:中国科学技术大学,2015. | |
| [7] | LIU Wei, LIU Shang, BAI Runcai, et al.Reducing Training Times in Neural Network Classifiers by Using Dynamic Data Reduction[J]. CAAI Transactions on Intelligent Systems, 2017, 12( 2): 258-265. |
| 刘威,刘尚,白润才,等. 动态数据约简的神经网络分类器训练方法研究[J]. 智能系统学报,2017,12(2):258-265. | |
| [8] | SU Liya, YAO Yepeng, LI Ning, et al.Hierarchical Clustering Based Network Traffic Data Reduction for Improving Suspicious Flow Detection[C]//IEEE. 2018 17th IEEE International Conference On Trust, Security And Privacy In Computing And Communications/12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE), August 1-3, 2018, New York, NY, USA. NJ: IEEE, 2018: 744-753. |
| [9] | MA Xuejun.Research on the Method of Traffic Anomaly Detection for Large-scale Network[D]. Changchun: Jilin University. 2018 |
| 马雪君. 大规模网络流量异常检测方法研究[D].长春:吉林大学. 2018. | |
| [10] | AHN S H, KIM N U, CHUNG T M.Big Data Analysis System Concept for Detecting Unknown Attacks[C]//IEEE. The 16th International Conference on Advanced Communication Technology, February 16-19, 2014, Pyeongchang, South Korea. NJ: IEEE, 2014: 269-272. |
| [11] | GUO Chun.Research on Key Technologies of Network Intrusion Detection Based on Data Mining[D]. Beijing: Beijing University of Posts and Telecommunications, 2014. |
| 郭春. 基于数据挖掘的网络入侵检测关键技术研究[D].北京:北京邮电大学,2014 | |
| [12] | WANG Sunan, LI Yinhai, LUO Xingguo.Anomalous Attack Traffic Detection Based on Stratified Sampling Algorithm[J]. Computer Engineering, 2012, 38(12): 105-109. |
| 王苏南,李印海,罗兴国. 基于分层抽样算法的异常攻击流量检测[J]. 计算机工程,2012,38(12):105-109. | |
| [13] | CLAFFY K C, POLYZOS G C, BRAUN H W.Application of Sampling Methodologies to Network Traffic Characterization[J]. ACM SIGCOMM Computer Communication Review, 1993, 23(4): 194-203. |
| [14] | ZHU Yu, WANG Tian.Construction and Application of Dynamic Sampling Frame in Network Data Environment[J]. Statistics & Decision, 2019(2): 5-8. |
| 朱钰,王恬. 网络数据环境下动态抽样框的构建及其应用[J]. 统计与决策,2019(2):5-8. | |
| [15] | ZHANG Zhonglin.Research The Detection Applications of Network Quality[D]. Beijing: Beijing University of Posts and Telecommunications, 2015. |
| 张忠琳. 网络质量探测应用的研究[D]. 北京:北京邮电大学,2015. | |
| [16] | ZHANG Linlin.Research on Sampling Algorithms in Network Traffic Measuremen[D]. Qufu: Qufu Normal University, 2015. |
| 张淋淋. 网络流量测量中的抽样算法研究[D].曲阜:曲阜师范大学,2015. | |
| [17] | WANG Chunlong.Research on Network Heavy Flow Measurement[D]. Wuxi: Jiangnan University, 2014. |
| 王春龙. 网络大流测量技术研究[D].无锡:江南大学,2014. | |
| [18] | CAO Jie.Research of Feature Reduction and Traffic Classification Method based on SVM[D]. Changchun: Jilin University. 2017. |
| 曹杰. 基于SVM的网络流量特征降维与分类方法研究[D]. 长春:吉林大学,2017. | |
| [19] | CHENG Guang.Sampling Measurement and Behavior Analysis of Large-scale High-speed IP Network Traffic[D]. Nanjing: Southeast University, 2003. |
| 程光. 大规模高速IP网络流量抽样测量及行为分析研究[D].南京:东南大学,2003. | |
| [20] | TATSUYA M, MASATO U, RYOICHI K.Identifying Elephant Flows through Periodically Sampled Packets[J]. Ieice Technical Report Information Networks, 2004, 104: 115-120. |
| [21] | CHEN Song, WANG Shan, ZHOU Mingtian.Network Data Measurement and Statistics Model Based on Real-Time Analysis[J]. Acta Electronica Sinica, 2010, 38(5): 1177-1180. |
| 陈松,王珊,周明天. 基于实时分析的网络测量抽样统计模型[J]. 电子学报,2010,38(5):1177-1180. | |
| [22] | DUFFIELD N, GROSSGLAUSER M.Trajectory Sampling With Unreliable Reporting[J]. ACM Transactions on Networking, 2008, 16(1): 37-50. |
| [23] | ZHANG Jin, WU Jiangxing, NIU Xiaona.Space-Efficient Fair Packet Sampling Algorithm[J]. Journal of Software, 2010, 21(10): 2642-2655. |
| 张进,邬江兴,钮晓娜.空间高效的数据包公平抽样算法[J].软件学报,2010,21(10):2642-2655. | |
| [24] | SALAMA A, SAATCHI R, BURKE D.Adaptive Sampling Technique Using Regression Modelling and Fuzzy Inference System for Network Traffic[J]. Studies in Health Technology & Informatics, 2017, 242: 592. |
| [25] | SUN Yu.Research on Anomaly Detection Techniques of Network Traffic Based on Sampling Flow[D]. Beijing: Beijing Jiaotong University, 2018 |
| 孙宇. 基于抽样流的网络流量异常检测技术研究[D].北京:北京交通大学,2018. | |
| [26] | XIE Dongqing, ZHOU Zaihong, LUO Jiawei.An Algorithm Based on LRU and SCBF for Elephant Flows Identification and Its application in DDos Defense[J]. Journal of Comuter Research and Development, 2011, 48(8): 1517-1523. |
| 谢冬青,周再红,骆嘉伟. 基于LRU和SCBF的大象流提取及其在DDoS防御中的应用[J]. 计算机研究与发展,2011,48(8):1517-1523. | |
| [27] | LI Heng, SHEN Huawei, CHENG Xueqi, et al.Review of Network High Flow Distributed Denial of Service Attack and Defense Mechanisms[J]. Netinfo Security, 2017, 17(5): 37-43. |
| 李恒,沈华伟,程学旗,等.网络高流量分布式拒绝服务攻击防御机制研究综述[J].信息网络安全,2017,17(5):37-43. | |
| [28] | MAI J, CHUAH C N, SRIDHARAN A, et al.Is Sampled Data Sufficient for Anomaly Detection?[C]//ACM. The 6th ACM SIGCOMM Conference on Internet Measurement, October 25-27, Rio de Janeriro, Brazil. New York: ACM, 2006: 165-176. |
| [29] | CHEN Liangchen, GAO Shu, LIU Baoxu, et al.Research Status and Development Trends on Network Encrypted Traffic Identification[J]. Netinfo Security, 2019, 19(3): 67-73. |
| 陈良臣,高曙,刘宝旭,等. 网络加密流量识别研究进展及发展趋势[J].信息网络安全,2019,19(3):67-73. |
| [1] | 刘建伟, 韩祎然, 刘斌, 余北缘. 5G网络切片安全模型研究[J]. 信息网络安全, 2020, 20(4): 1-11. |
| [2] | 赵志岩, 纪小默. 智能化网络安全威胁感知融合模型研究[J]. 信息网络安全, 2020, 20(4): 87-93. |
| [3] | 黎水林, 祝国邦, 范春玲, 陈广勇. 一种新的等级测评综合得分算法研究[J]. 信息网络安全, 2020, 20(2): 1-6. |
| [4] | 荆涛, 万巍. 面向属性迁移状态的P2P网络行为分析方法研究[J]. 信息网络安全, 2020, 20(1): 16-25. |
| [5] | 裘玥. 大型体育赛事网络安全风险分析与评估[J]. 信息网络安全, 2019, 19(9): 61-65. |
| [6] | 高孟茹, 谢方军, 董红琴, 林祥. 面向关键信息基础设施的网络安全评价体系研究[J]. 信息网络安全, 2019, 19(9): 111-114. |
| [7] | 尚文利, 尹隆, 刘贤达, 赵剑明. 工业控制系统安全可信环境构建技术及应用[J]. 信息网络安全, 2019, 19(6): 1-10. |
| [8] | 张可, 汪有杰, 程绍银, 王理冬. DDoS攻击中的IP源地址伪造协同处置方法[J]. 信息网络安全, 2019, 19(5): 22-29. |
| [9] | 倪一涛, 陈咏佳, 林柏钢. 基于自动解混淆的恶意网页检测方法[J]. 信息网络安全, 2019, 19(4): 37-46. |
| [10] | 陈良臣, 高曙, 刘宝旭, 卢志刚. 网络加密流量识别研究进展及发展趋势[J]. 信息网络安全, 2019, 19(3): 19-25. |
| [11] | 傅建明, 黎琳, 郑锐, 苏日古嘎. 基于GAN的网络攻击检测研究综述[J]. 信息网络安全, 2019, 19(2): 1-9. |
| [12] | 韦力, 段沁, 刘志伟. 互联网时代医院网络安全管理综述[J]. 信息网络安全, 2019, 19(12): 88-92. |
| [13] | 张振峰, 张志文, 王睿超. 网络安全等级保护2.0云计算安全合规能力模型[J]. 信息网络安全, 2019, 19(11): 1-7. |
| [14] | 张健, 陈博翰, 宫良一, 顾兆军. 基于图像分析的恶意软件检测技术研究[J]. 信息网络安全, 2019, 19(10): 24-31. |
| [15] | 訾然, 刘嘉. 基于精益信任的风险信任体系构建研究[J]. 信息网络安全, 2019, 19(10): 32-41. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||