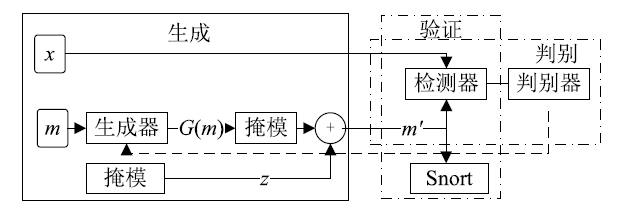
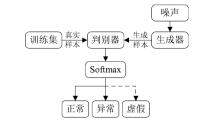
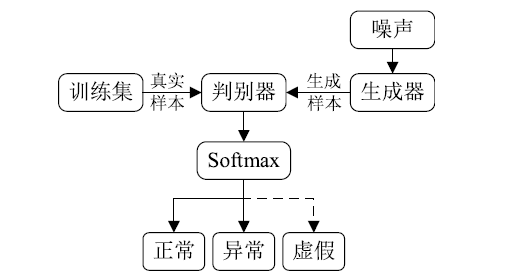
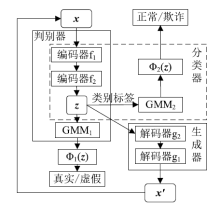
信息网络安全 ›› 2019, Vol. 19 ›› Issue (2): 1-9.doi: 10.3969/j.issn.1671-1122.2019.02.001
• 等级保护 • 下一篇
基于GAN的网络攻击检测研究综述
- 1.武汉大学国家网络安全学院,湖北武汉 430072
2.武汉大学空天信息安全与可信计算教育部重点实验室,湖北武汉 430072
-
收稿日期:2018-09-28出版日期:2019-02-10发布日期:2020-05-11 -
作者简介:作者简介:傅建明(1969—),男,湖南,教授,博士,主要研究方向为系统安全、移动安全;黎琳(1996—),女,贵州,硕士研究生,主要研究方向为网络安全;郑锐(1992—),男,河南,博士研究生,主要研究方向为网络安全;苏日古嘎(1993—),女,内蒙古,硕士研究生,主要研究方向为网络安全。
-
基金资助:国家自然科学基金[61373168];国家自然科学基金联合基金[U1636107]
Survey of Network Attack Detection Based on GAN
Jianming FU1,2( ), Lin LI1, Rui ZHENG1, Suriguga1
), Lin LI1, Rui ZHENG1, Suriguga1
- 1. School of Cyber Science and Engineering, Wuhan University, Wuhan Hubei 430072, China
2. Key Laboratory of Aerospace Information Security and Trusted Computing, Ministry of Education,Wuhan University, Wuhan Hubei 430072, China
-
Received:2018-09-28Online:2019-02-10Published:2020-05-11
摘要:
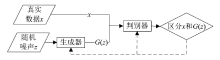
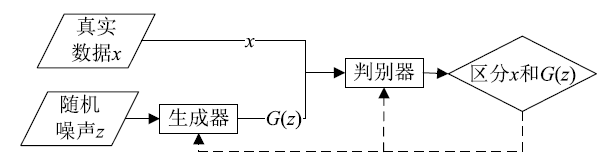
生成式对抗网络(Generative Adversarial Network,GAN)是近年来深度学习领域的一个重大突破,是一个由生成器和判别器共同构成的动态博弈模型。其“生成”和“对抗”的思想获得了广大科研工作者的青睐,满足了多个研究领域的应用需求。受该思想的启发,研究者们将GAN应用到网络安全领域,用于检测网络攻击,帮助构建智能有效的网络安全防护机制。文章介绍了GAN的基本原理、基础结构、理论发展和应用现状,着重从网络攻击样本生成、网络攻击行为检测两大方面研究了其在网络攻击检测领域的应用现状。
中图分类号:
引用本文
傅建明, 黎琳, 郑锐, 苏日古嘎. 基于GAN的网络攻击检测研究综述[J]. 信息网络安全, 2019, 19(2): 1-9.
Jianming FU, Lin LI, Rui ZHENG, Suriguga. Survey of Network Attack Detection Based on GAN[J]. Netinfo Security, 2019, 19(2): 1-9.
| [1] | GOODFELLOW I. NIPS2016 Tutorial: Generative Adversarial Networks[EB/OL]. |
| [2] | ARJOVSKY M, BOTTOU L. Towards Principled Methods for Training Generative Adversarial Networks[EB/OL]. ,2017-1-17. |
| [3] | AGHAKHANI H, MACHIRY A, NILIZADEH S, et al. Detecting Deceptive Reviews Using Generative Adversarial Networks[EB/OL].,2018-5-25. |
| [4] | GOODFELLOW I, POUGET-ABADIE J, MIRZA M, et al.Generative Adversarial Nets[C]//NIPS. The 2014 Conference on Advances in Neural Information Processing Systems 27, December 8-13, 2014, Montreal, Canada. NY:Curran Associates, 2014. 2672-2680. |
| [5] | SALIMANS T, GOODFELLOW I, ZAREMBA W, et al. Improved Techniques for Training Gans[EB/OL]. ,2016-6-10. |
| [6] | ZHAO Junbo, MATHIEU M, LECUN Y. Energy-based Generative Adversarial Network[EB/OL]. ,2017-3-6. |
| [7] | ARJOVSKY M, CHINTALA S, BOTTOU L. Wasserstein Gan[EB/OL]. ,2017-12-6. |
| [8] | GULRAJANI I, AHMED F, ARJOVSKY M, et al. Improved Training of Wasserstein Gans[EB/OL].,2017-12-25. |
| [9] | LEDIG C, THEIS L, HUSZÁR F, et al. Photo-realistic Single Image Super-resolution Using a Generative Adversarial Network[EB/OL]. ,2017-5-25. |
| [10] | WU Huikai, ZHENG Shuai, ZHANG Junge, et al. GP-GAN: Towards Realistic High-Resolution Image Blending[EB/OL]. ,2017-3-25 . |
| [11] | PATHAK D, KRAHENBUHL P, DONAHUE J, et al.Context Encoders: Feature Learning by Inpainting[C]//IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, June 27-30,2016, Las Vegas,USA.NJ:IEEE,2016: 2536-2544. |
| [12] | MOGREN O. C-RNN-GAN: Continuous Recurrent Neural Networks with Adversarial Training[EB/OL]. ,2016-11-29. |
| [13] | YU Lantao, ZHANG Weinan, WANG Jun, et al.SeqGAN: Sequence Generative Adversarial Nets with Policy Gradient[C]//AAAI. The Thirty-first AAAI Conference on Artificial Intelligence and the Twenty-ninth Innovative Applications of Artificial Intelligence Conference, February 4-9,2017,San Francisco,California,USA. CA:AAAI, 2017: 2852-2858. |
| [14] | LI Jiwei, MONROE W, SHI Tianlin, et al. Adversarial Learning for Neural Dialogue Generation[EB/OL]. ,2017-9-24. |
| [15] | ZHANG Yizhe, GAN Zhe, CARIN L. Generating Text via Adversarial Training[EB/OL]. ,2018-6-11. |
| [16] | MIYATO T, DAI A M, GOODFELLOW I. Adversarial Training Methods for Semi-Supervised Text Classification[EB/OL].,2017-5-6. |
| [17] | SUTSKEVER I, VINYALS O, LE Q V.Sequence to Sequence Learning with Neural Networks[C]//NIPS. Advances in Neural Information Processing Systems, December 8-13,2014,Montreal,Quebec,Canada.NY:Curran Associates,2016: 3104-3112. |
| [18] | MIKOLOV T, SUTSKEVER I, CHEN K, et al.Distributed Representations of Words and Phrases and Their Compositionality[C]//NIPS.Advances in Neural Information Processing Systems,December 5-10,2013,Lake Tahoe,Nevada,USA.NY:Curran Associates,2013: 3111-3119. |
| [19] | HARER J, OZDEMIR O, LAZOVICH T, et al. Learning to Repair Software Vulnerabilities with Generative Adversarial Networks[EB/OL].,2018-5-28. |
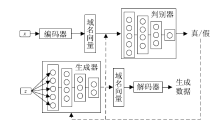
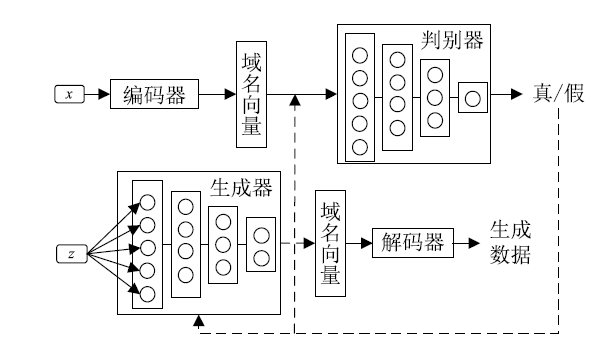
| [20] | YUAN Chen, QIAN Liping, ZHANG Hui, et al. Generation of Malicious Domain Training Data Based on Generative Adversarial Network[EB/OL].. |
| 袁辰, 钱丽萍, 张慧, 等. 基于生成对抗网络的恶意域名训练数据生成[EB/OL].. | |
| [21] | PAN Yiming, LIN Jiajun.Generation and Verification of Malicious Network Flow Based on Generative Adversarial Networks[EB/OL]. |
| 潘一鸣,林家骏.基于生成对抗网络的恶意网络流生成及验证[EB/OL]. | |
| [22] | HU Weiwei, TAN Ying. Generating Adversarial Malware Examples for Black-Box Attacks Based on GAN[EB/OL]. ,2017-2-20. |
| [23] | ZHENG Shengjun, GUO Longhua, CHEN Jian, et al.An Online Detection System for Advanced Malware Based on Virtual Execution Technology[J]. Netinfo Security, 2016,16(1) : 29-33. |
| 郑生军,郭龙华,陈建,等. 基于虚拟执行技术的高级恶意软件攻击在线检测系统[J]. 信息网络安全,2016,16(1) : 29-33. | |
| [24] | KIM J Y, BU S J, CHO S B.Malware Detection Using Deep Transferred Generative Adversarial Networks[C]//ICONIP. the 24th International Conference on Neural Information Processing, November 14-18,2017,Guangzhou,China.HK:Springer,2017: 556-564. |
| [25] | ARNOLD A, NALLAPATI R, COHEN W W.A Comparative Study of Methods for Transductive Transfer Learning[C]//IEEE.ICDM Workshops 2007,October 28,2007,Omaha,USA.NJ:IEEE, 2007: 77-82. |
| [26] | MICROSOFT. Microsoft Malware Classification Challenge (BIG 2015)[EB/OL]. |
| [27] | KIM J Y, BU S J, CHO S B.Zero-day Malware Detection Using Transferred Generative Adversarial Networks Based on Deep Autoencoders[J]. Information Sciences, 2018, 460(9): 83-102. |
| [28] | HEN Hongsong, WANG Gang, SONG Jianlin.Research on Anomaly Behavior Classification Algorithm of Internal Network User Based on Cloud Computing Intrusion Detection Data Set[J]. Netinfo Security, 2018 ,18(3) : 1-7. |
| 陈红松,王钢,宋建林. 基于云计算入侵检测数据集的内网用户异常行为分类算法研究[J]. 信息网络安全,2018,18(3):1-7. | |
| [29] | YIN Chuanlong, ZHU Yuefei, LIU Shengli, et al.An Enhancing Framework for Botnet Detection Using Generative Adversarial Networks[C]//IEEE.2018 International Conference on Artificial Intelligence and Big Data (ICAIBD),May 26-28,2018,Chengdu,China.NJ:IEEE, 2018:228-234. |
| [30] | SHIRAVI A, SHIRAVI H, TAVALLAEE M, et al.Toward Developing a Systematic Approach to Generate Benchmark Datasets for Intrusion Detection[J]. Computers & Security, 2012, 31(3): 357-374. |
| [31] | FIORE U, DE S A, PERLA F, et al. Using Generative Adversarial Networks for Improving Classification Effectiveness in Credit Card Fraud Detection[EB/OL]. ,2017-12-30. |
| [32] | DAL P A, CAELEN O, JOHNSON R A, et al.Calibrating Probability with Undersampling for Unbalanced Classification[C]//IEEE. 2015 IEEE Symposium Series on Computational Intelligence, December 7-10,2015,Cape Town,South Africa.NJ:IEEE,2015: 159-166. |
| [33] | ZHENG Yujun, ZHOU Xiaohan, SHENG Weiguo, et al.Generative Adversarial Network-based Telecom Fraud Detection at the Receiving Bank[J]. Neural Networks, 2018, 102(6): 78-86. |
| [1] | 刘建伟, 韩祎然, 刘斌, 余北缘. 5G网络切片安全模型研究[J]. 信息网络安全, 2020, 20(4): 1-11. |
| [2] | 赵志岩, 纪小默. 智能化网络安全威胁感知融合模型研究[J]. 信息网络安全, 2020, 20(4): 87-93. |
| [3] | 王腾飞, 蔡满春, 芦天亮, 岳婷. 基于iTrace_v6的IPv6网络攻击溯源研究[J]. 信息网络安全, 2020, 20(3): 83-89. |
| [4] | 黎水林, 祝国邦, 范春玲, 陈广勇. 一种新的等级测评综合得分算法研究[J]. 信息网络安全, 2020, 20(2): 1-6. |
| [5] | 荆涛, 万巍. 面向属性迁移状态的P2P网络行为分析方法研究[J]. 信息网络安全, 2020, 20(1): 16-25. |
| [6] | 董威, 李永刚. 基于复杂网络的智能电网网络攻击影响分析研究[J]. 信息网络安全, 2020, 20(1): 52-60. |
| [7] | 裘玥. 大型体育赛事网络安全风险分析与评估[J]. 信息网络安全, 2019, 19(9): 61-65. |
| [8] | 高孟茹, 谢方军, 董红琴, 林祥. 面向关键信息基础设施的网络安全评价体系研究[J]. 信息网络安全, 2019, 19(9): 111-114. |
| [9] | 陈良臣, 刘宝旭, 高曙. 网络攻击检测中流量数据抽样技术研究[J]. 信息网络安全, 2019, 19(8): 22-28. |
| [10] | 尚文利, 尹隆, 刘贤达, 赵剑明. 工业控制系统安全可信环境构建技术及应用[J]. 信息网络安全, 2019, 19(6): 1-10. |
| [11] | 陈冠衡, 苏金树. 基于深度神经网络的异常流量检测算法[J]. 信息网络安全, 2019, 19(6): 68-75. |
| [12] | 张可, 汪有杰, 程绍银, 王理冬. DDoS攻击中的IP源地址伪造协同处置方法[J]. 信息网络安全, 2019, 19(5): 22-29. |
| [13] | 王耀杰, 钮可, 杨晓元. 基于生成对抗网络的图像隐藏方案[J]. 信息网络安全, 2019, 19(5): 54-60. |
| [14] | 倪一涛, 陈咏佳, 林柏钢. 基于自动解混淆的恶意网页检测方法[J]. 信息网络安全, 2019, 19(4): 37-46. |
| [15] | 陈良臣, 高曙, 刘宝旭, 卢志刚. 网络加密流量识别研究进展及发展趋势[J]. 信息网络安全, 2019, 19(3): 19-25. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||