信息网络安全 ›› 2019, Vol. 19 ›› Issue (1): 8-8.doi: 10.3969/j.issn.1671-1122.2019.01.002
基于改进DGHV算法的云存储密文全文检索研究
- 1.东南大学网络空间安全学院,江苏南京 210096
2.东南大学信息科学与工程学院,江苏南京 210096
-
收稿日期:2018-09-11出版日期:2019-01-20发布日期:2020-05-11 -
作者简介:作者简介:秦中元(1974—),男,河南,副教授,博士,主要研究方向为网络安全;韩尹(1993—),女,江苏,硕士研究生,主要研究方向为网络安全;朱雪金(1992—),男,安徽,硕士研究生,主要研究方向为网络安全。
-
基金资助:江苏省自然科学基金[bk20161099]
Research on Ciphertext Full-text Retrieval of Cloud Storage Based on Improved DGHV Algorithm
Zhongyuan QIN1( ), Yin HAN2, Xuejin ZHU2
), Yin HAN2, Xuejin ZHU2
- 1. School of Cyberspace Security, Southeast University, Nanjing Jiangsu 210096, China
2. School of Information Engineering, Southeast University, Nanjing Jiangsu 210096, China
-
Received:2018-09-11Online:2019-01-20Published:2020-05-11
摘要:
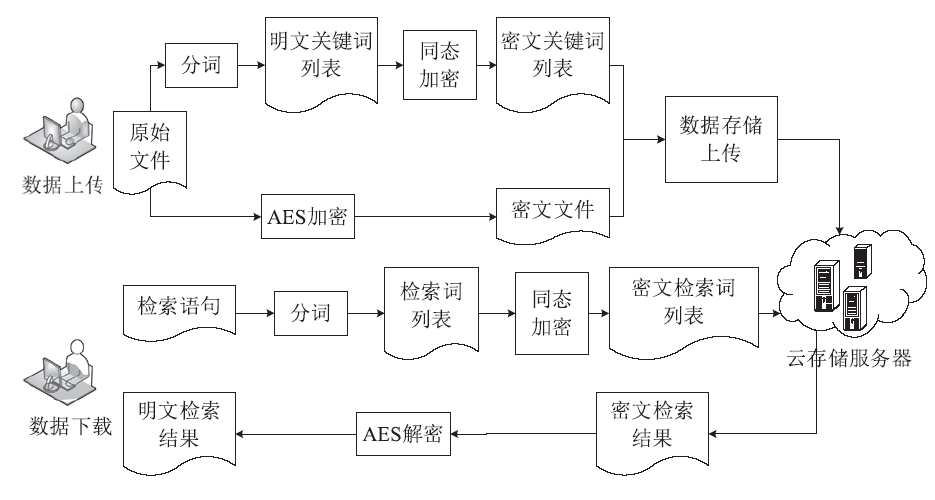
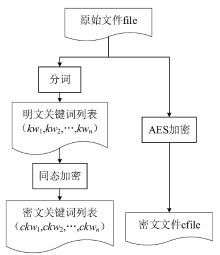
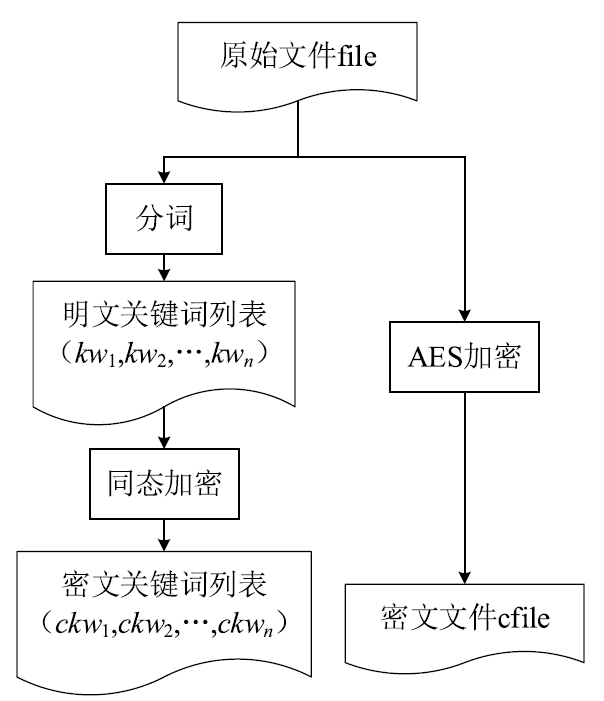
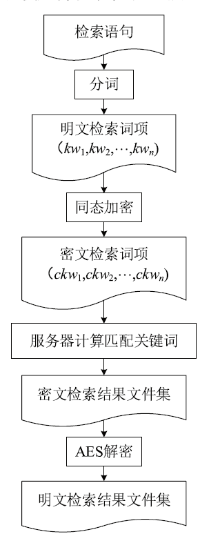
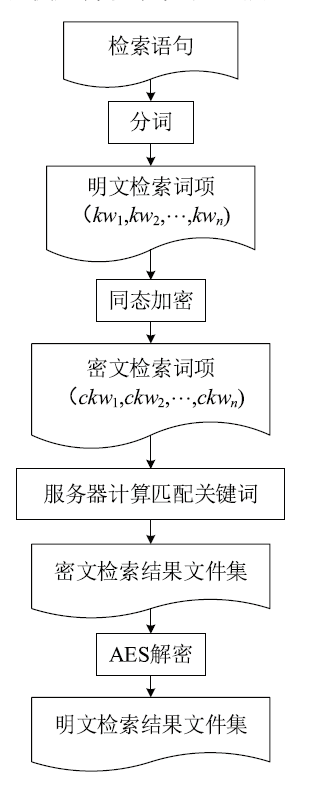
为了有效解决云存储中用户数据的机密性问题,文章提出一种基于同态加密的云存储密文全文检索方法。文章首先介绍了同态加密,并研究了基于DGHV算法的密文检索方案。接着提出一种基于改进DGHV算法的方案用于云存储密文全文检索。该方案采用两个密钥对明文关键词进行同态加密,一个为只有用户知道的用户密钥,另一个为用户与云服务器共享的检索密钥。用户检索文件时,云服务器只需利用检索密钥就能对文件进行全文检索,而用户密钥始终仅保留在用户手中,云服务器无法获取,也就无法解密出用户的明文数据。该方案可以在第三方服务器不可信的云存储场景下实现高效的检索,保证了用户数据的机密性。
中图分类号:
引用本文
秦中元, 韩尹, 朱雪金. 基于改进DGHV算法的云存储密文全文检索研究[J]. 信息网络安全, 2019, 19(1): 8-8.
Zhongyuan QIN, Yin HAN, Xuejin ZHU. Research on Ciphertext Full-text Retrieval of Cloud Storage Based on Improved DGHV Algorithm[J]. Netinfo Security, 2019, 19(1): 8-8.
| [1] | FENG Dengguo, ZHANG Min, ZHANG Yan, et al.Study on Cloud Computing Security[J]. Journal of Software, 2011, 22(1): 71-83. |
| 冯登国,张敏,张妍,等. 云计算安全研究[J]. 软件学报,2011,22(1):71-83. | |
| [2] | FENG Chaosheng, QIN Zhiguang, YUAN Ding.Techniques of Secure Storage for Cloud Data[J]. Chinese Journal of Computers, 2015, 38(1): 150-163. |
| 冯朝胜,秦志光,袁丁. 云数据安全存储技术[J]. 计算机学报,2015,38(1):150-163. | |
| [3] | GONG Changqing, XIAO Yun, LI Mengfei, et al.Summary of Cloud Computing Security Research[J]. Journal of Shenyang Aerospace Ace University, 2017, 34(4): 1-17. |
| 拱长青,肖芸,李梦飞,等. 云计算安全研究综述[J]. 沈阳航空航天大学学报,2017,34(4):1-17. | |
| [4] | BOKHARI M U, MAKKI Q, TAMANDANI Y K.A Survey on Cloud Computing[J]. International Journal on Computer Science & Engineering, 2018, 5(6): 302-311. |
| [5] | CACHIN C, KEIDAR I, SHRAER A.Trusting the Cloud[J]. Acm Sigact News, 2009, 40(2): 81-86. |
| [6] | TAKABI H, JOSHI J B D, AHN G J. Security and Privacy Challenges in Cloud Computing Environments[J]. IEEE Security & Privacy, 2010, 8(6): 24-31. |
| [7] | SINGH A, CHATTERJEE K. Cloud Security Issues and Challenges: A Survey[EB/OL]. , 2018-2-11. |
| [8] | WANG Wenxu, ZHANG Jian, CHANG Qing, et al.Research on the Security Problem of Cloud Computing Virtualization Platform[J]. Netinfo Security, 2016, 16(9): 163-168. |
| 王文旭,张健,常青,等. 云计算虚拟化平台安全问题研究[J]. 信息网络安全,2016,16(9):163-168. | |
| [9] | XIA Zhihua, CHEN Li, SUN Xingming, et al.A Multi-keyword Ranked Search over Encrypted Cloud Data Supporting Semantic Extension[J]. International Journal of Multimedia & Ubiquitous Engineering, 2016, 11(8): 107-120. |
| [10] | NA Haiyang, YANG Geng, SHU Xiaowei.Multi-keyword Ranked Search Scheme over Encrypted Cloud Data[J]. Computer Science, 2017, 44(1): 149-154. |
| 那海洋,杨庚,束晓伟. 基于B+树的多关键字密文排序检索方法[J]. 计算机科学,2017,44(1):149-154. | |
| [11] | YAN Xiaolong, PANG Xiaoqiong, REN Mengqi.Multi-keyword Ranked Search Method Supporting Dynamic Update[J]. Computer Engineering and Design, 2018, 39(4): 901-906. |
| 严小龙,庞晓琼,任孟琦. 支持动态更新的多关键词密文排序检索[J]. 计算机工程与设计,2018,39(4):901-906. | |
| [12] | DING Wei, LIU Yongji, ZHANG Jianfeng.Chinese-keyword Fuzzy Search and Extraction over Encrypted Patent Documents[C]//IEEE. 7th International Joint Conference on Knowledge Discovery, Knowledge Engineering and Knowledge Management, November 12-14, 2015, Lisbon, Portugal. New Jersey: IEEE, 2015: 168-176. |
| [13] | WANG Yilei, BAO Wenyi, ZHAO Yang, et al.An ElGamal Encryption with Fuzzy Keyword Search on Cloud Environment[J]. International Journal of Network Security, 2016, 19(3): 481-486. |
| [14] | LV Qi.Research on Fuzzy Search and Access Control over Encrypted Data in Cloud Storage[D]. Nanning: Guangxi University, 2018. |
| 吕琦. 云存储中密文的模糊搜索与访问控制研究[D].南宁:广西大学,2018. | |
| [15] | DIJK M V, GENTRY C, HALEVI S, et al.Fully Homomorphic Encryption over the Integers[C]//Springer. 2010 Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 30-June 3, 2010, Monaco and Nice, France. Heidelberg: Springer, 2010: 24-43. |
| [16] | RIVEST R L, ADLEMAN L, DERTOUZOS M L. On Data Banks and Privacy Homomorphisms[EB/OL]. ,2018-2-15. |
| [17] | GENTRY C.Fully Homomorphic Encryption Using Ideal Lattices[J]. Stoc, 2009, 9(4): 169-178. |
| [18] | GENTRY C. A Fully Homomorphic Encryption Scheme[EB/OL]. , 2018-2-18. |
| [19] | BLACK N.Homomorphic Encryption and the Approximate GCD Problem[D]. Clemson: Clemson University, 2014. |
| [20] | MARINELLI F, ARAGONA R, MARCOLLA C, et al.Some Security Bounds for the Key Sizes of DGHV Scheme[J]. Applicable Algebra in Engineering Communication & Computing, 2014, 25(5): 383-392. |
| [21] | CORON J S, NACCACHE D, TIBOUCHI M.Public Key Compression and Modulus Switching for Fully Homomorphic Encryption over the Integers[C]//Springer. 31st Annual International Conference on Theory and Applications of Cryptographic Techniques, April 15-19, 2012, Cambridge, United Kingdom. Heidelberg: Springer, 2012: 446-464. |
| [22] | LI Zichen, ZHANG Fengjuan, WANG Peidong.Highly Efficient Fully Homomorphic Encryption Scheme with Shorter Public Keys[J]. Application Research of Computers, 2017, 34(2): 487-489. |
| 李子臣,张峰娟,王培东. 一种短密钥高效全同态加密方案[J]. 计算机应用研究,2017,34(2):487-489. | |
| [23] | CHEON J H, CORON J S, KIM J, et al.Batch Fully Homomorphic Encryption over the Integers[C]//Spring. 2013 Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 26-30, 2013, Athens, Greece. Heidelberg: Springer, 2013: 315-335. |
| [24] | XIE Xueshuo.An Effectively Fully Homomorphic Encryption over the Integers[D]. Jinan: Shandong University, 2014. |
| 谢学说. 一类整数上有效的全同态加密方案[D]. 济南:山东大学,2014. | |
| [25] | WANG Rongbing, LI Yanan, XU Hongyan, et al.Full Homomorphic Encryption Scheme over Real Number Suitable for Cloud Service Environment[J]. Netinfo Security, 2018, 19(11): 49-56. |
| 王嵘冰,李雅囡,徐红艳,等. 适合云服务环境的实数全同态加密方案[J]. 信息网络安全,2018,19(11):49-56. | |
| [26] | WU Zuowei, LI Taoshen.An Improved Fully Homomorphic Encryption Scheme under the Cloud Environment[C]//ACM. 12th Chinese Conference on Computer Supported Cooperative Work and Social Computing, September 22-23, 2017, Chongqing, China. New York: ACM, 2017: 251-252. |
| [1] | 傅智宙, 王利明, 唐鼎, 张曙光. 基于同态加密的HBase二级密文索引方法研究[J]. 信息网络安全, 2020, 20(4): 55-64. |
| [2] | 唐春明, 林旭慧. 隐私保护集合交集计算协议[J]. 信息网络安全, 2020, 20(1): 9-15. |
| [3] | 李晓冉, 郝蓉, 于佳. 具有数据上传管控的无证书可证明数据持有方案[J]. 信息网络安全, 2020, 20(1): 83-88. |
| [4] | 刘建华, 郑晓坤, 郑东, 敖章衡. 基于属性加密且支持密文检索的安全云存储系统[J]. 信息网络安全, 2019, 19(7): 50-58. |
| [5] | 侯林, 李明洁, 徐剑, 周福才. 基于变长认证跳表的分布式动态数据持有证明模型[J]. 信息网络安全, 2019, 19(7): 67-74. |
| [6] | 秦中元, 韩尹, 张群芳, 朱雪金. 一种改进的多私钥生成中心云存储访问控制方案[J]. 信息网络安全, 2019, 19(6): 11-18. |
| [7] | 邵必林, 李肖俊, 边根庆, 赵煜. 云存储数据完整性审计技术研究综述[J]. 信息网络安全, 2019, 19(6): 28-36. |
| [8] | 刘文超, 潘峰, 杨晓元, 周潭平. 基于GPU的全同态加密软件库调试与分析[J]. 信息网络安全, 2019, 19(6): 76-83. |
| [9] | 黑一鸣, 刘建伟, 张宗洋, 喻辉. 基于区块链的可公开验证分布式云存储系统[J]. 信息网络安全, 2019, 19(3): 52-60. |
| [10] | 李帅, 刘晓洁, 徐兵. 一种基于目录哈希树的磁盘数据同步方法研究[J]. 信息网络安全, 2019, 19(2): 53-59. |
| [11] | 赵星, 王晓东, 张串绒. 一种基于数据漂移的动态云安全存储机制[J]. 信息网络安全, 2019, 19(10): 65-73. |
| [12] | 游林, 梁家豪. 基于同态加密与生物特征的安全身份认证研究[J]. 信息网络安全, 2018, 18(4): 1-8. |
| [13] | 鲁秀青, 咸鹤群. 云存储中基于用户授权的大数据完整性审计方案[J]. 信息网络安全, 2018, 18(4): 32-37. |
| [14] | 宋新霞, 马佳敏, 陈智罡, 陈克非. 基于SEAL的虹膜特征密文认证系统[J]. 信息网络安全, 2018, 18(12): 15-22. |
| [15] | 马苗立, 张洪波, 丁卫颖. 基于字节级优化更新的云存储增量式网络编码方法研究[J]. 信息网络安全, 2018, 18(11): 18-26. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||