信息网络安全 ›› 2015, Vol. 15 ›› Issue (2): 7-8.doi: 10.3969/j.issn.1671-1122.2015.02.002
信息安全风险评估关键技术研究与实现
- 1.北京大学软件与微电子学院,北京 102600
2. 洛阳电子装备试验中心,河南洛阳 471003
-
收稿日期:2014-12-17出版日期:2015-02-10发布日期:2015-07-05 -
作者简介:作者简介: 文伟平(1976-),男,湖南,副教授,博士,主要研究方向:网络攻击与防范、恶意代码研究、信息系统逆向工程和可信计算技术等;郭荣华(1972-),男,湖北,副研究员,博士,主要研究方向:信息安全;孟正(1990-),男,河北,硕士研究生,主要研究方向:系统与网络安全、漏洞分析;柏皛(1987-),女,四川,硕士研究生,主要研究方向:信息安全风险评估、系统与网络安全。
-
基金资助:国家自然科学基金[61170282]
Research and Implementation on Information Security Risk Assessment Key Technology
WEN Wei-ping1( ), GUO Rong-hua2, MENG Zheng1, BAI Xiao1
), GUO Rong-hua2, MENG Zheng1, BAI Xiao1
- 1. School of Software & Microelectronics, Peking University, Beijing 102600, China
2. LEETC, Luoyang Henan 471003, China
-
Received:2014-12-17Online:2015-02-10Published:2015-07-05
摘要:
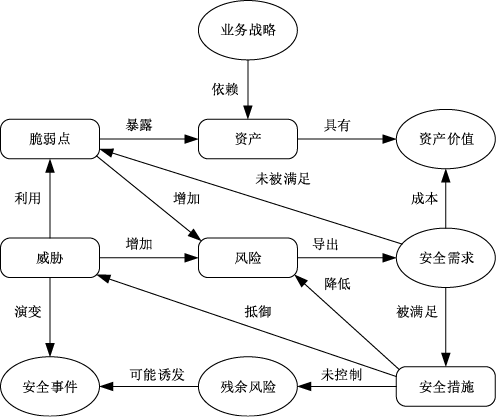
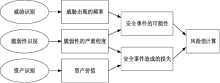
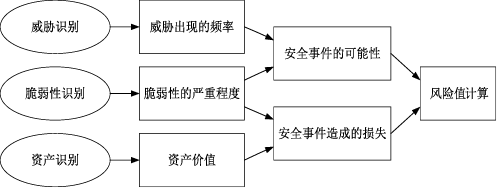
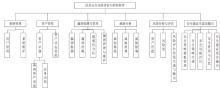
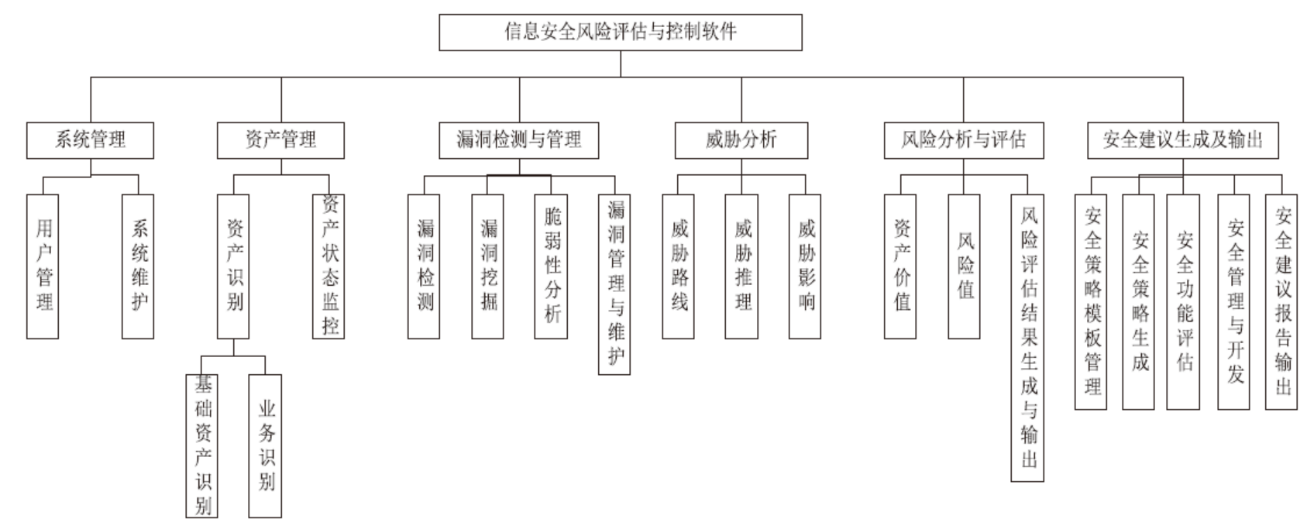
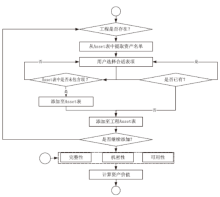
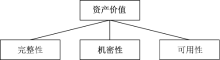
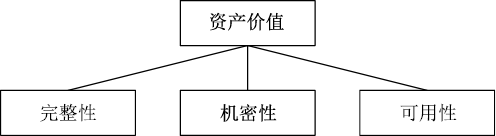
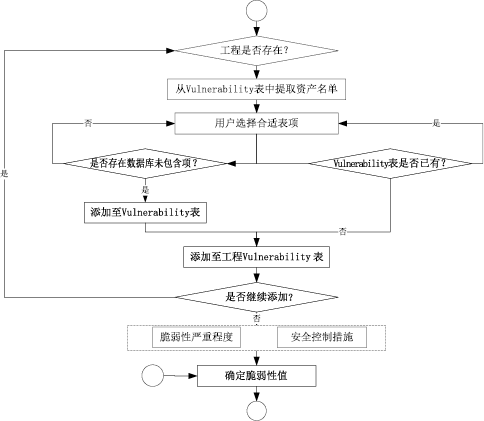
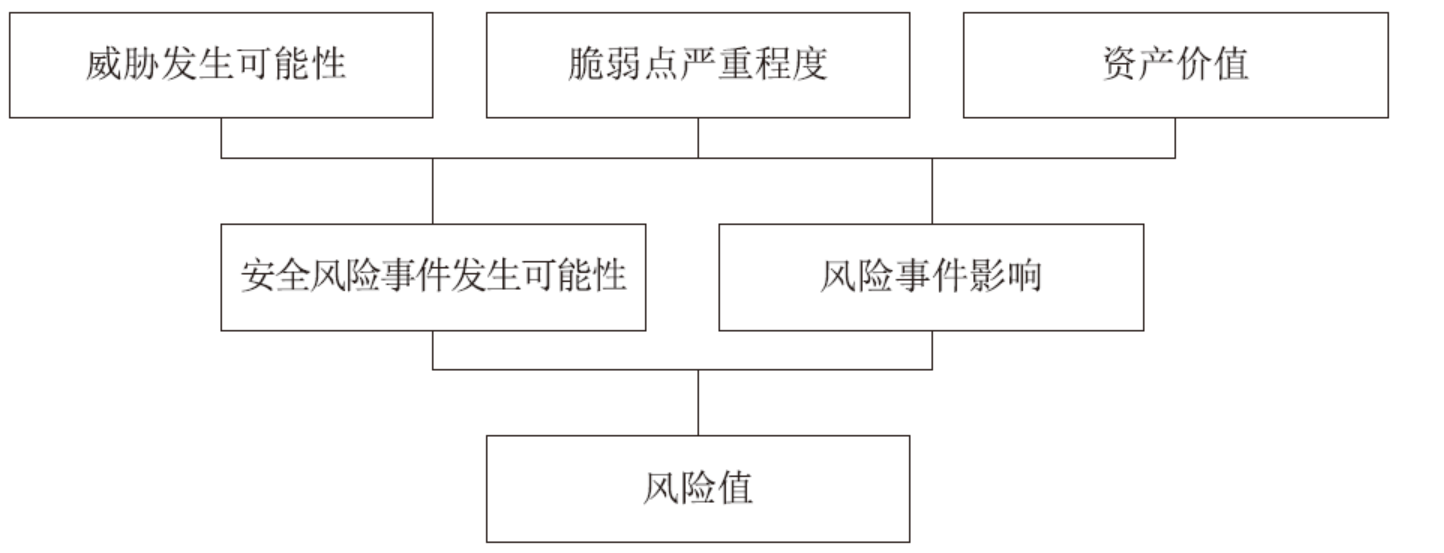
信息安全问题是全球信息化发展最关注的问题,随着各机构逐渐进入信息化办公时代,机构的信息资产几乎全部保存在信息系统中,一旦面临威胁和遭遇攻击,造成的危害和损失将难以想象。信息安全风险评估理论最早由国外提出,目前广泛应用于信息安全领域。文章首先研究风险评估的基础理论和流程,对风险评估的定义、风险评估要素之间的关联关系、安全风险模型和常见的风险评估方法进行介绍。然后对风险评估与控制软件进行架构设计和功能模块设计,该软件涉及资产识别、威胁分析、脆弱性分析、现有安全策略的确认与评估、综合风险评估、评估报告输出等多个环节。接下来结合SQL Server数据库和Tomcat中间件技术完成系统的实现,并在测试平台上对其进行测试。文章在评估软件的设计过程中加入了漏洞检测功能,为评估工作的准确性提供了进一步的保障。系统模块结构简洁清晰,评估功能完善强大,效果突出。
中图分类号:
引用本文
文伟平, 郭荣华, 孟正, 柏皛. 信息安全风险评估关键技术研究与实现[J]. 信息网络安全, 2015, 15(2): 7-8.
WEN Wei-ping, GUO Rong-hua, MENG Zheng, BAI Xiao. Research and Implementation on Information Security Risk Assessment Key Technology[J]. Netinfo Security, 2015, 15(2): 7-8.
| [1] | 杨继华. 信息安全风险评估模型及方法研究[D].西安:西安电子科技大学,2007. |
| [2] | 刘莹,顾卫东.信息安全风险评估研究综述[J].青岛大学学报. 2008,23(2):37-43. |
| [3] | Common Criteria for Information Technology Security Evaluation[S]. ISO/IEC 15408: 1999. |
| [4] | 范红,冯登国,吴亚非.信息安全风险评估方法与应用[M]. 北京:清华大学出版社,2006. |
| [5] | GB/T20984-2007.信息安全风险管理规范[S]. |
| [6] | GB/Z 24364-2009.信息安全风险管理指南[S]. |
| [7] | 岳芳. 网络安全的标准与组织[J].网络安全技术与应用,2004,(5):74-75. |
| [8] | 聂晓伟,张玉清,杨鼎才,等.一个基于BS7799标准的风险分析方法[C]//中国计算机安全学会2004年会论文集,2004:67-69. |
| [9] | 李杨,聂晓伟,杨鼎才. 基于BS7799标准风险评估实施性研究[J].计算机应用研究,2005,22(7):42-44, 62. |
| [10] | 陈光,匡兴华.信息系统安全风险评估研究[J].网络安全技术与应用,2004,(7):62-64. |
| [11] | 高建新,舒首衡,伭剑辉,等.大型活动信息系统网络安全监控研究[J].信息网络安全. 2010.(1):41-43. |
| [12] | 范并思. 20世纪西方与中国的图书馆学——基于德尔斐法测评的理论史纲[M].北京:北京图书馆出版社,2004. |
| [13] | 苏忠,林繁,陈厚金,等.网络安全态势感知系统的构建与应用[J].信息网络安全,2014,(5):73-77. |
| [14] | 孙鹏鹏, 张玉清, 韩臻. 信息安全风险评估工具的设计与实现[J] . 计算机工程与应用, 2007 , 43(9) : 95-98. |
| [15] | 卫成业. 信息安全风险评估模型[J].网络安全技术与应用,2002,(4):10-15. |
| [16] | 李平安. 信息网络安全及风险防范措施分析[J].信息网络安全,2013,(7):15-17. |
| [17] | Zhang Y Z, Fang B X, Chi Y, et al.Research on network node correlation in network risk assessment[J]. Chinese Journal of Computers, 2007, 30(2): 234-240. |
| [18] | Zhang Y Z, Fang B X, Chi Y, et al.Risk propagation model for assessing network information systems[J]. Journal of Software, 2007,18(1):137-145. |
| [19] | Mohammad Salim Ahmed, Ehab Al-Shaer, Mohamed Taibah, et al.Objective risk evaluation for automated security management[J]. Journal of Network and Systems Management, Sep. 2011, (19):343-366. |
| [20] | Lu Jiayuan.Research on network system risk assessment using risk transmission[C]// Internet Technology and Applications, 2010 International Conference on.Wuhan, 2010:1-5. |
| [21] | Chen T P, Qiao X D, Zheng L Q, et al.Application of graph theory in treat situation analysis of network security[J]. Journal of Beijing university of posts and telecommunications, 2009, 32(1):113-117. |
| [22] | Young-Gab Kim, Dongwon Jeong, Soo-Hyun Park, et al.Simulation of risk propagation model in information systems[C] // Computational Intelligence and Security,Guangzhou, 2006, (2):1555-1558. |
| [1] | 王君艳, 伊鹏, 贾洪勇, 张建辉. 基于改进CAE的物联网终端风险评估模型[J]. 信息网络安全, 2024, 24(1): 150-159. |
| [2] | 张光华, 刘永升, 王鹤, 于乃文. 基于BiLSTM和注意力机制的智能合约漏洞检测方案[J]. 信息网络安全, 2022, 22(9): 46-54. |
| [3] | 顾兆军, 杨睿, 隋翯. 面向网络架构的系统攻击面建模方法[J]. 信息网络安全, 2022, 22(3): 29-38. |
| [4] | 黄波, 秦玉海, 刘旸, 季铎. 基于通用攻击树的脆弱性评估与风险概率研究[J]. 信息网络安全, 2022, 22(10): 39-44. |
| [5] | 朱容辰, 李欣, 林小暖. 基于贝叶斯网络的视频专网安全风险分析方法[J]. 信息网络安全, 2021, 21(12): 91-101. |
| [6] | 赵小林, 赵斌, 赵晶晶, 薛静锋. 基于攻击识别的网络安全度量方法研究[J]. 信息网络安全, 2021, 21(11): 17-27. |
| [7] | 刘永磊, 金志刚, 郝琨, 张伟龙. 基于STRIDE和模糊综合评价法的移动支付系统风险评估[J]. 信息网络安全, 2020, 20(2): 49-56. |
| [8] | 文伟平, 李经纬, 焦英楠, 李海林. 一种基于随机探测算法和信息聚合的漏洞检测方法[J]. 信息网络安全, 2019, 19(1): 1-7. |
| [9] | 赵健, 王瑞, 李思其. 基于污点分析的智能家居漏洞挖掘技术研究[J]. 信息网络安全, 2018, 18(6): 36-44. |
| [10] | 王庆, 屠晨阳, shenjiahui@iie.ac.cn. 侧信道攻击通用框架设计及应用[J]. 信息网络安全, 2017, 17(5): 57-62. |
| [11] | 董晓宁, 赵华容, 李殿伟, 王甲生. 基于模糊证据理论的信息系统安全风险评估研究[J]. 信息网络安全, 2017, 17(5): 69-73. |
| [12] | 梁智强, 林丹生. 基于电力系统的信息安全风险评估机制研究[J]. 信息网络安全, 2017, 17(4): 86-90. |
| [13] | 李涛, 张驰. 基于信息安全等保标准的网络安全风险模型研究[J]. 信息网络安全, 2016, 16(9): 177-183. |
| [14] | 滕希龙, 曲海鹏. 基于区间值直觉模糊集相似性的信息安全风险评估方法研究[J]. 信息网络安全, 2015, 15(5): 62-68. |
| [15] | 何鹏程, 方勇. 一种基于Web日志和网站参数的入侵检测和风险评估模型的研究[J]. 信息网络安全, 2015, 15(1): 61-65. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||