信息网络安全 ›› 2024, Vol. 24 ›› Issue (9): 1422-1431.doi: 10.3969/j.issn.1671-1122.2024.09.010
基于图像凸包特征的CBAM-CNN网络入侵检测方法
- 桂林电子科技大学计算机与信息安全学院,桂林 541004
-
收稿日期:2024-03-09出版日期:2024-09-10发布日期:2024-09-27 -
通讯作者:黎汇业948524859@qq.com -
作者简介:刘联海(1978—),男,福建,副教授,博士,主要研究方向为网络协议设计与优化、网络安全应用、大数据管理和分析|黎汇业(1998—),男,广西,硕士研究生,主要研究方向为网络安全应用、聚类算法应用|毛冬晖(2000—),男,安徽,硕士研究生,主要研究方向为网络安全应用、移动边缘计算 -
基金资助:国家自然科学基金(62167002);广西密码学与信息安全重点实验室开放课题(GCIS201822)
CBAM-CNN Network-Based Intrusion Detection Method Using Image Convex Hull Features
LIU Lianhai, LI Huiye( ), MAO Donghui
), MAO Donghui
- School of Computer Science and Information Security, Guilin University of Electronic Technology, Guilin 541004, China
-
Received:2024-03-09Online:2024-09-10Published:2024-09-27
摘要:
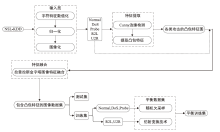
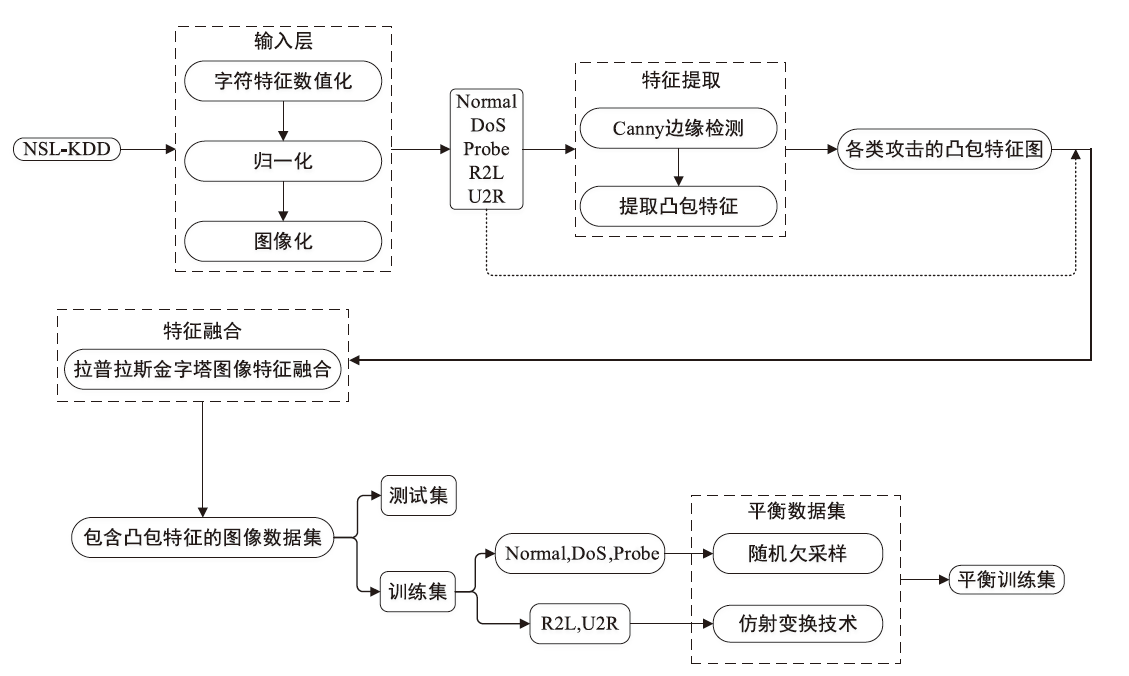
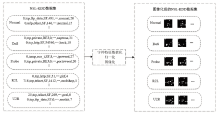
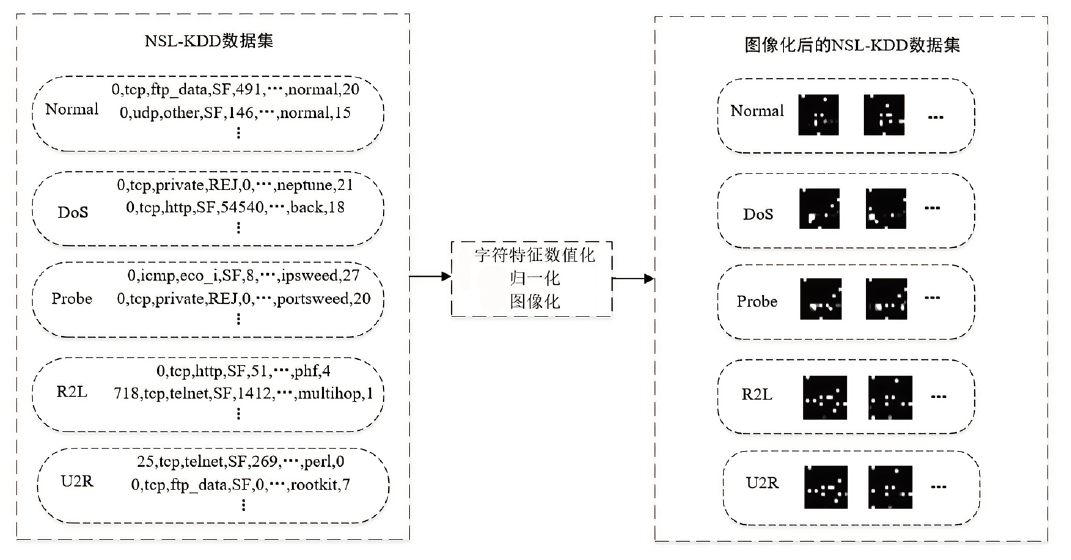
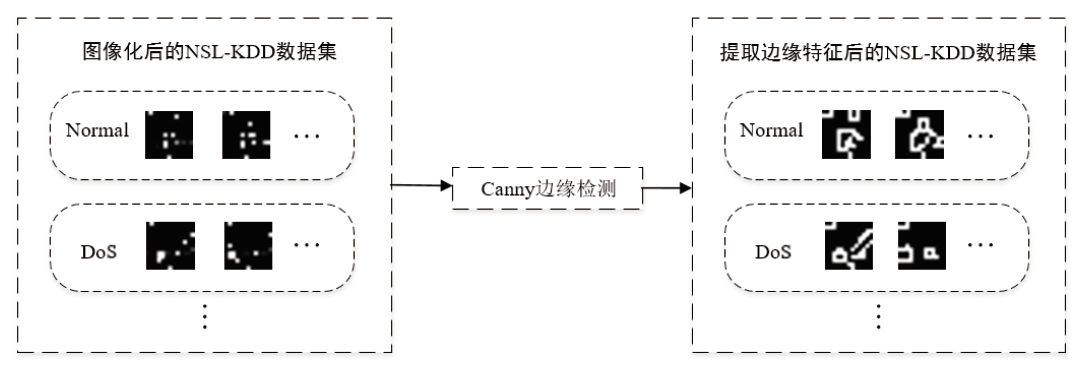
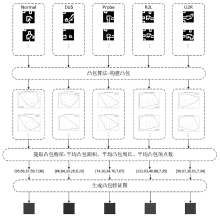
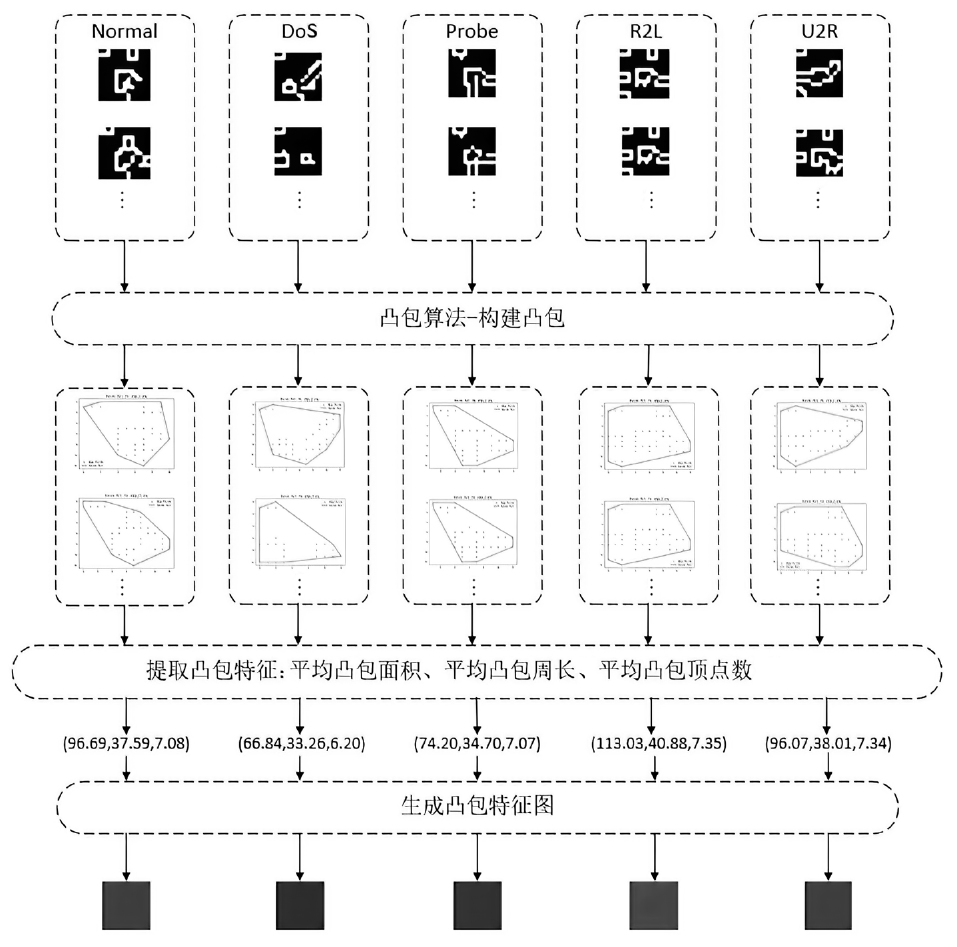
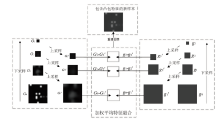
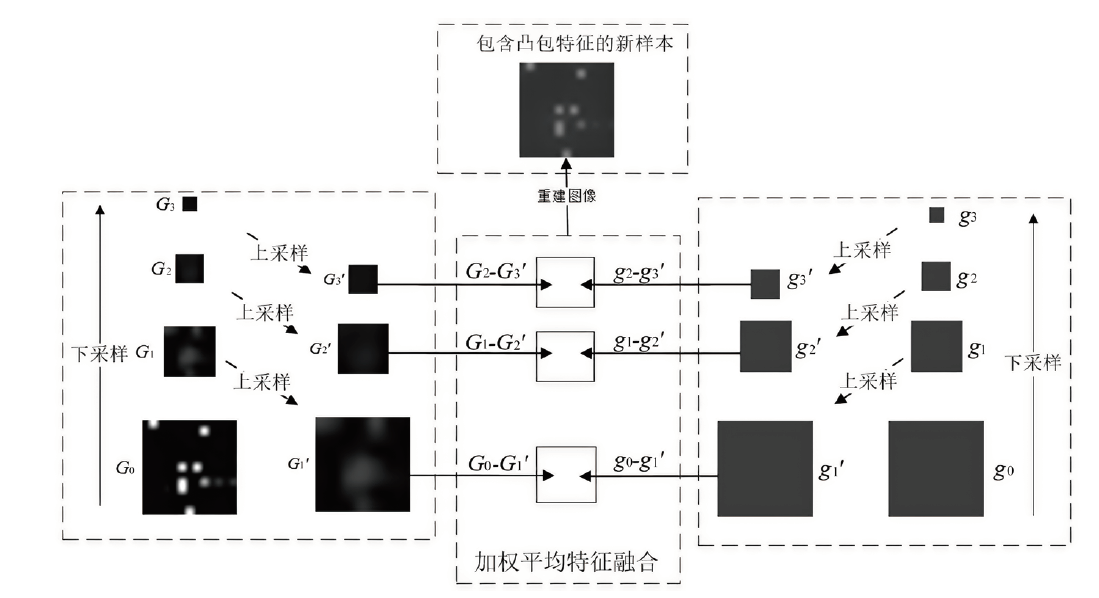
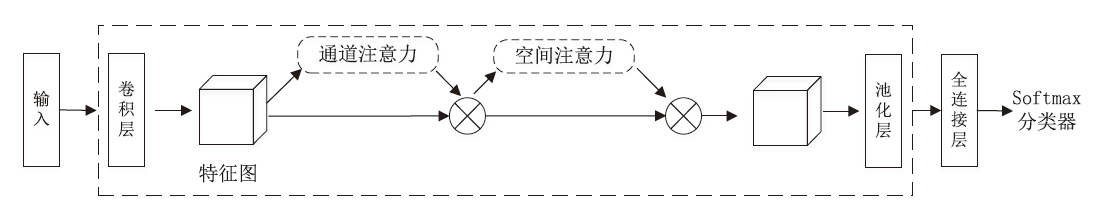
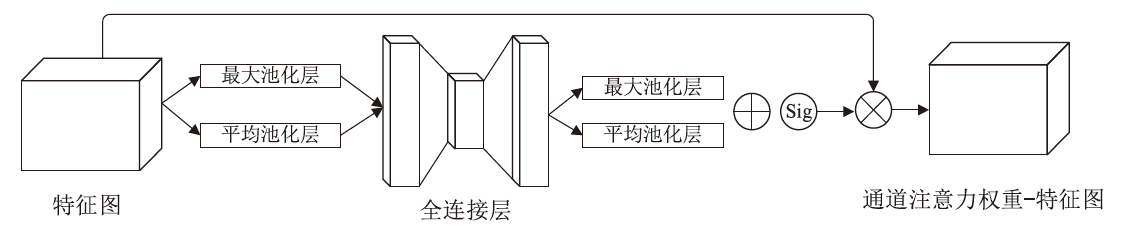
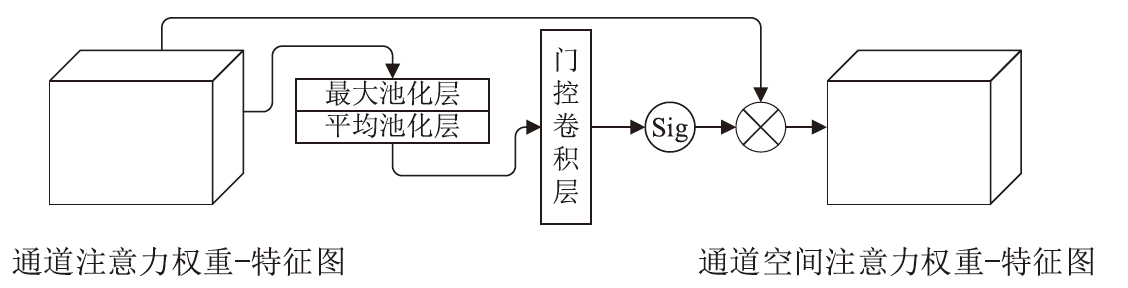
针对入侵检测领域中多分类准确率较低和模型训练时间较长的问题,文章根据现有的基准数据集NSL-KDD的特点,提出一种新颖且有效的预处理方法。首先,对数据集进行字符特征数值化和归一化处理,并转化成RGB图像数据集;其次,使用Canny边缘检测算法提取图像数据集中的各种攻击类型的边缘特征,根据图像的边缘特征使用凸包算法构建凸包,并计算各类攻击的平均凸包面积、平均凸包周长和平均顶点数,将这3项指标作为RGB的3个通道,分别生成各种攻击类型的凸包特征图;再次,使用拉普拉斯金字塔图像特征融合算法将原始图像数据集与凸包特征图进行融合,构建包含凸包特征的图像数据集,并对训练集中的多数类样本采用随机欠采样,对少数类样本进行仿射变换,生成平衡训练集;最后,基于CBAM-CNN模型进行多分类实验。文章模型在NSL-KDD数据集上的准确率和F1分数分别达到了96.20%和86.71%,优于传统的网络入侵检测方法,且比其他深度学习模型具有更好的检测性能。
中图分类号:
引用本文
刘联海, 黎汇业, 毛冬晖. 基于图像凸包特征的CBAM-CNN网络入侵检测方法[J]. 信息网络安全, 2024, 24(9): 1422-1431.
LIU Lianhai, LI Huiye, MAO Donghui. CBAM-CNN Network-Based Intrusion Detection Method Using Image Convex Hull Features[J]. Netinfo Security, 2024, 24(9): 1422-1431.
| [1] | ALJABRI M, ALJAMEEL S S, MOHAMMAD R M A, et al. Intelligent Techniques for Detecting Network Attacks: Review and Research Directions[EB/OL]. (2021-06-09)[2024-02-25]. https://doi.org/10.3390/s21217070. |
| [2] | AMANOUL S V, ABDULAZEEZ A M. Intrusion Detection System Based on Machine Learning Algorithms: A Review[C]// IEEE.2022 IEEE 18th International Colloquium on Signal Processing & Applications (CSPA). New York: IEEE, 2022: 79-84. |
| [3] | THAKKAR, ANKIT, RITIKA L. Fusion of Statistical Importance for Feature Selection in Deep Neural Network-Based Intrusion Detection System[J]. Network Daily News, 2023: 353-363. |
| [4] | LI Shudong, JIANG Laiyuan, WANG Zhen, et al. A Malicious Mining Code Detection Method Based on Multi-Features Fusion[J]. IEEE Transactions on Network Science and Engineering, 2022: 2731-2739. |
| [5] | ALGHANAM O A, ALMOBAIDEEN W, SAADEH M, et al. An Improved PIO Feature Selection Algorithm for IoT Network Intrusion Detection System Based on Ensemble Learning[EB/OL]. (2023-08-12)[2024-02-25]. https://doi.org/10.1016/j.eswa.2022.118745. |
| [6] | WEN Tingke, XIAO Yuanxing, WANG Anqi, et al. A Novel Hybrid Feature Fusion Model for Detecting Phishing Scam on Ethereum Using Deep Neural Network[J]. Expert Systems with Applications, 2023, 211: 63-74. |
| [7] | AHMAD R S, ALI A H, KAZIM S M, et al. A GAF and CNN Based Wi-Fi Network Intrusion Detection System[C]// IEEE. IEEE INFOCOM 2023-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). New York: IEEE, 2023: 1-6. |
| [8] | KIM J, KIM J, KIM H, et al. CNN-Based Network Intrusion Detection against Denial-of-Service Attacks[EB/OL]. (2020-06-01)[2024-02-25]. https://doi.org/10.3390/electronics9060916. |
| [9] | SIDDIQI, MURTAZA A, WOOGUIL P. Tier-Based Optimization for Synthesized Network Intrusion Detection System[J]. IEEE Access, 2022: 108530-108544. |
| [10] | LIU Yang, KANG Jian, LI Yiran, et al. A Network Intrusion Detection Method Based on CNN and CBAM[C]// IEEE. 2021-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). New York: IEEE, 2021: 1-6. |
| [11] | WANG Zhen, FUAD A G. An Attention-Based Convolutional Neural Network for Intrusion Detection Model[J]. IEEE Access, 2023: 43116-43127. |
| [12] | SARHAN M, SIAMAK L, MARIUS P. Towards a Standard Feature Set for Network Intrusion Detection System Datasets[J]. Mobile Networks and Applications, 2022: 1-14. |
| [13] | WU Fangsheng, ZHU Changan, MW B, et al. Research on Image Text Recognition Based on Canny Edge Detection Algorithm and K-Means Algorithm[J]. International Journal of System Assurance Engineering and Management, 2022: 72-80. |
| [14] | LEI Chao, BU Siqi, ZHONG Jun, et al. Distribution Network Reconfiguration: A Disjunctive Convex Hull Approach[J]. IEEE Transactions on Power Systems, 2023: 5926-5929. |
| [15] | LUO Xing, FU Guizhong, YANG Jiangxin, et al. Multi-Modal Image Fusion via Deep Laplacian Pyramid Hybrid Network[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2023: 7354-7369. |
| [16] | GHOSH K, SARKAR A, BANERJEE A, et al. Performance Improvement of Convolutional Neural Network Using Random under Sampling[C]// Springer. Advances in Smart Communication Technology and Information Processing:OPTRONIX 2020. Heidelberg: Springer, 2021: 207-217. |
| [17] | SAYED W S, RADWAN A G, FAHMY H, et al. Trajectory Control and Image Encryption Using Affine Transformation of Lorenz System[J]. Egyptian Informatics Journal, 2021: 155-166. |
| [18] | DHANABAL L, SHANTHARAJAH S P. A Study on NSL-KDD Dataset for Intrusion Detection System Based on Classification Algorithms[J]. International Journal of Advanced Research in Computer and Communication Engineering, 2015, 4(6): 446-452. |
| [19] | MEENA G, CHOUDHARY R R. A Review Paper on IDS Classification Using KDD 99 and NSL KDD Dataset in WEKA[C]// IEEE. 2017 International Conference on Computer, Communications and Electronics (Comptelix). New York: IEEE, 2017: 553-558. |
| [20] | MOHAMMADPOUR L, LING T C, LIEW C S, et al. A Survey of CNN-Based Network Intrusion Detection[EB/OL]. (2022-05-23)[2024-02-27]. https://doi.org/10.3390/app12168162. |
| [21] | PFLUGFELDER D, SCHARR H. Practically Lossless Affine Image Transformation[J]. IEEE Transactions on Image Processing, 2020: 5367-5373. |
| [22] | HU Jianwei, LIU Chenshuo, CUI Yanpeng. An Improved CNN Approach for Network Intrusion Detection System[J]. International Journal of Network Security, 2021: 569-575. |
| [23] | ZHENG Shiji. Network Intrusion Detection Model Based on Convolutional Neural Network[C]// IEEE. 2021 IEEE 5th Advanced Information Technology, Electronic and Automation Control Conference (IAEAC). New York: IEEE, 2021: 634-637. |
| [24] | ZHANG Xiaoqing, YANG Fei, HU Yue, et al. RANet: Network Intrusion Detection with Group-Gating Convolutional Neural Network[EB/OL]. (2022-07-03)[2024-02-27]. https://doi.org/10.1016/j.jnca.2021.103266. |
| [25] | ABDULGANIYU O H, TCHAKOUCHT T A, SAHEED Y K. A Systematic Literature Review for Network Intrusion Detection System (IDS)[J]. International Journal of Information Security, 2023: 1125-1162. |
| [26] | JIANG Kaiyuan, WANG Wenya, WANG Aili, et al. Network Intrusion Detection Combined Hybrid Sampling with Deep Hierarchical Network[J]. IEEE Access, 2020: 32464-32476. |
| [27] | KANAKARAJAN N K, MUNIASAMY K. Improving the Accuracy of Intrusion Detection Using GAR-Forest with Feature Selection[C]// Springer. The 4th International Conference on Frontiers in Intelligent Computing:Theory and Applications (FICTA) 2015. Heidelberg: Springer, 2016: 539-547. |
| [28] | IERACITANO C, ADEEL A, MORABITO F C, et al. A Novel Statistical Analysis and Autoencoder Driven Intelligent Intrusion Detection Approach[J]. Neurocomputing, 2020: 51-62. |
| [29] | WISANWANICHTHAN T, THAMMAWICHAI M. A Double-Layered Hybrid Approach for Network Intrusion Detection System Using Combined Naive Bayes and SVM[J]. IEEE Access, 2021: 138432-138450. |
| [30] | FU Yanfang, DU Yishuai, CAO Zijian, et al. A Deep Learning Model for Network Intrusion Detection with Imbalanced Data[EB/OL]. (2022-06-12)[2024-02-27]. https://doi.org/10.3390/electronics11060898. |
| [1] | 许楷文, 周翊超, 谷文权, 陈晨, 胡晰远. 基于多尺度特征融合重建学习的深度伪造人脸检测算法[J]. 信息网络安全, 2024, 24(8): 1173-1183. |
| [2] | 张浩, 谢大智, 胡云晟, 叶骏威. 基于半监督学习的网络异常检测研究综述[J]. 信息网络安全, 2024, 24(4): 491-508. |
| [3] | 江荣, 刘海天, 刘聪. 基于集成学习的无监督网络入侵检测方法[J]. 信息网络安全, 2024, 24(3): 411-426. |
| [4] | 冯光升, 蒋舜鹏, 胡先浪, 马明宇. 面向物联网的入侵检测技术研究新进展[J]. 信息网络安全, 2024, 24(2): 167-178. |
| [5] | 金志刚, 丁禹, 武晓栋. 融合梯度差分的双边校正联邦入侵检测算法[J]. 信息网络安全, 2024, 24(2): 293-302. |
| [6] | 孙红哲, 王坚, 王鹏, 安雨龙. 基于Attention-BiTCN的网络入侵检测方法[J]. 信息网络安全, 2024, 24(2): 309-318. |
| [7] | 沈华, 田晨, 郭森森, 慕志颖. 基于对抗性机器学习的网络入侵检测方法研究[J]. 信息网络安全, 2023, 23(8): 66-75. |
| [8] | 彭翰中, 张珠君, 闫理跃, 胡成林. 联盟链下基于联邦学习聚合算法的入侵检测机制优化研究[J]. 信息网络安全, 2023, 23(8): 76-85. |
| [9] | 刘长杰, 石润华. 基于安全高效联邦学习的智能电网入侵检测模型[J]. 信息网络安全, 2023, 23(4): 90-101. |
| [10] | 高庆官, 张博, 付安民. 一种基于攻击图的高级持续威胁检测方法[J]. 信息网络安全, 2023, 23(12): 59-68. |
| [11] | 姚远, 樊昭杉, 王青, 陶源. 基于多元时序特征的恶意域名检测方法[J]. 信息网络安全, 2023, 23(11): 1-8. |
| [12] | 李思聪, 王坚, 宋亚飞, 黄玮. 基于BiTCN-DLP的恶意代码分类方法[J]. 信息网络安全, 2023, 23(11): 104-117. |
| [13] | 金志刚, 刘凯, 武晓栋. 智能电网AMI领域IDS研究综述[J]. 信息网络安全, 2023, 23(1): 1-8. |
| [14] | 王华忠, 田子蕾. 基于改进CGAN算法的工控系统入侵检测方法[J]. 信息网络安全, 2023, 23(1): 36-43. |
| [15] | 刘翔宇, 芦天亮, 杜彦辉, 王靖翔. 基于特征选择的物联网轻量级入侵检测方法[J]. 信息网络安全, 2023, 23(1): 66-72. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||