信息网络安全 ›› 2023, Vol. 23 ›› Issue (2): 35-44.doi: 10.3969/j.issn.1671-1122.2023.02.005
基于可信服务的云资源智能优化与决策方法
- 江南大学物联网应用教育部工程研究中心,无锡 214122
-
收稿日期:2022-11-26出版日期:2023-02-10发布日期:2023-02-28 -
通讯作者:王艳 E-mail:wangyan88@jiangnan.edu.cn -
作者简介:王艳(1978—),女,江苏,教授,博士,主要研究方向为网络化控制系统|张坤鹏(1998—),男,安徽,硕士研究生,主要研究方向为云资源配置优化与决策|纪志成(1959—),男,浙江,教授,博士,主要研究方向为网络化控制系统 -
基金资助:国家自然科学基金(61973138)
Intelligent Optimization and Decision Method of Cloud Resources Based on Trusted Service
WANG Yan( ), ZHANG Kunpeng, JI Zhicheng
), ZHANG Kunpeng, JI Zhicheng
- Engineering Research Center of Internet of Things Technology Applications Ministry of Education, Jiangnan University, Wuxi 214122, China
-
Received:2022-11-26Online:2023-02-10Published:2023-02-28 -
Contact:WANG Yan E-mail:wangyan88@jiangnan.edu.cn
摘要:
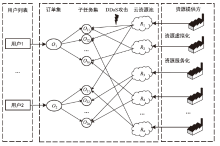
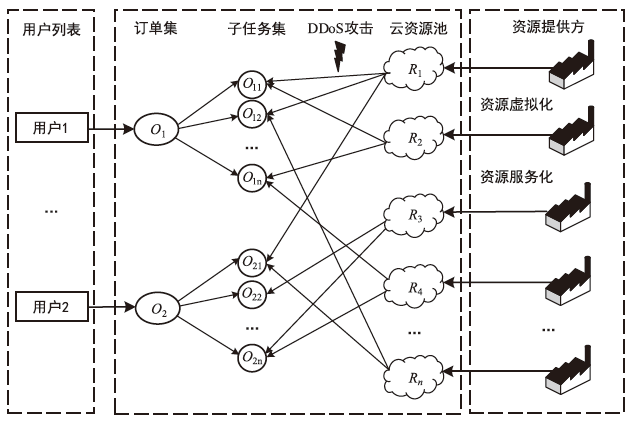
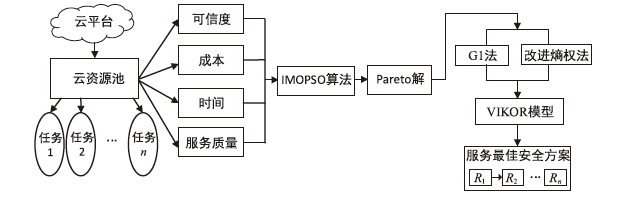
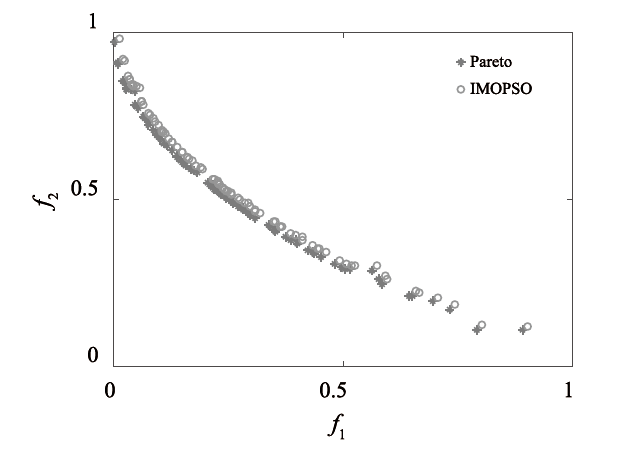
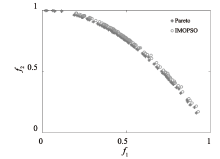
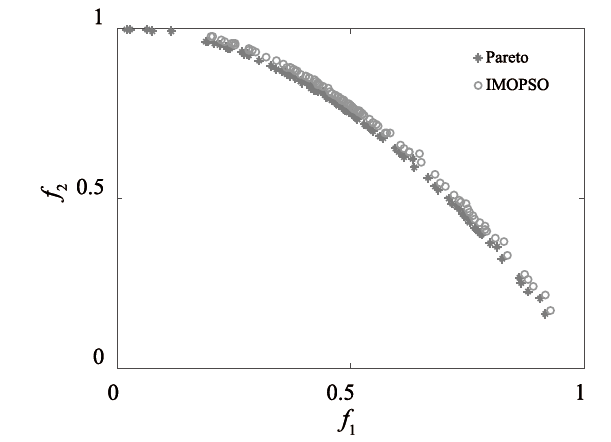
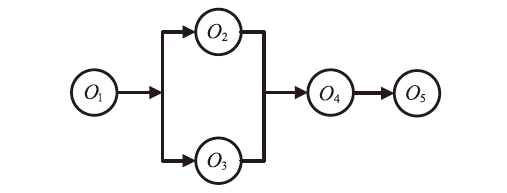
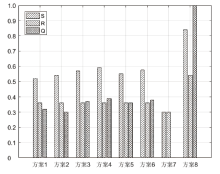
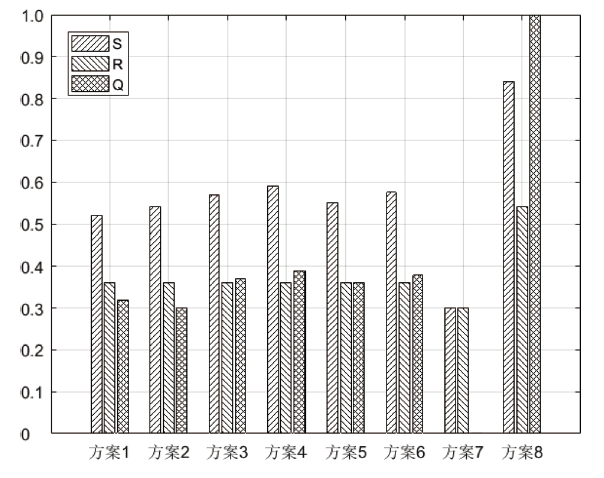
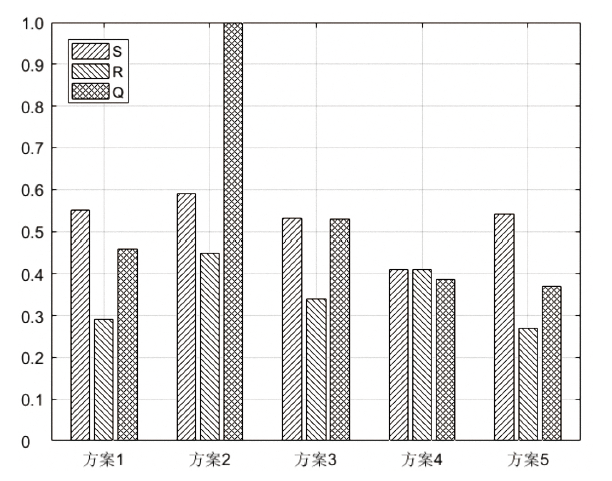
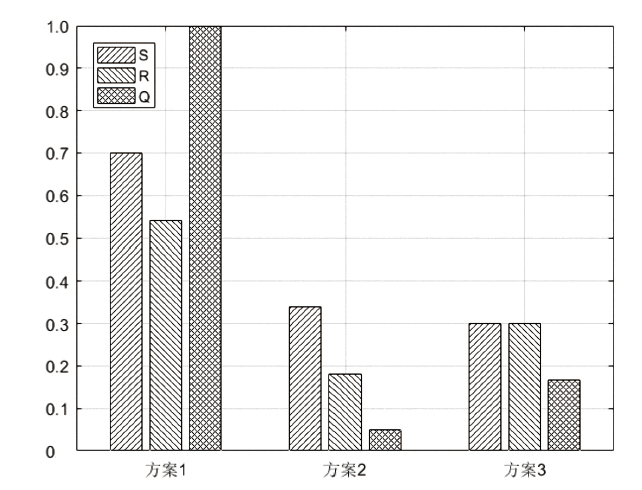
随着云计算的应用与发展,云安全问题备受关注。云资源在受到恶意攻击时会导致无法匹配,合理分配云资源是云安全的前提。为了解决资源可信服务、资源配置优化和安全方案评估的问题,文章提出了基于可信服务的云资源安全智能优化与决策方法。首先,建立资源安全可信度、时间、成本和服务质量的多目标优化模型;然后,采用改进粒子群算法对其求解,并利用基于G1-改进熵权法主客观组合赋权法的VIKOR评估方法选取最佳云安全方案,同时为了克服粒子群早熟收敛,融合动态惯性权值及速度扰动策略改进算法;最后,仿真实验表明,改进算法相对其他算法的解集更广泛,收敛性更好,并验证了可信服务下评估方法的有效性,提高了云资源服务的安全性。
中图分类号:
引用本文
王艳, 张坤鹏, 纪志成. 基于可信服务的云资源智能优化与决策方法[J]. 信息网络安全, 2023, 23(2): 35-44.
WANG Yan, ZHANG Kunpeng, JI Zhicheng. Intelligent Optimization and Decision Method of Cloud Resources Based on Trusted Service[J]. Netinfo Security, 2023, 23(2): 35-44.
使用本文
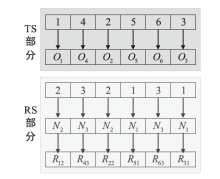
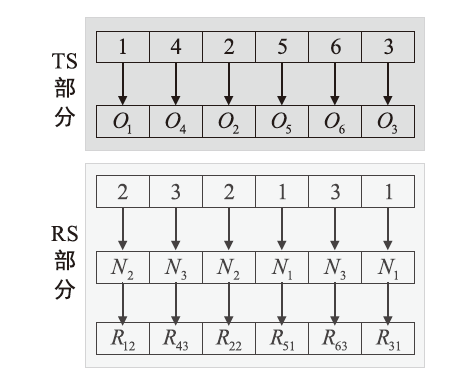
表2
任务信息
| 子任务 | 加工时间(h)/加工成本(元)/服务质量/可信度 | |||||
|---|---|---|---|---|---|---|
  |   |   |   |   |   | |
  | 20/125/ 0.75/0.98 | — | 30/100/ 0.6/0.95 | — | 25/110/ 0.7/0.95 | — |
  | — | 35/100/ 0.7/0.95 | — | 20/120/ 0.7/0.97 | — | 30/130/ 0.8/0.95 |
  | 30/110/ 0.7/0.95 | 25/100/ 0.6/0.95 | 30/120/ 0.85/0.95 | — | — | 40/120/ 0.86/0.98 |
  | — | 30/90/ 0.5/0.96 | — | 60/120/ 0.9/0.96 | 50/100/ 0.7/0.93 | — |
  | 25/105/ 0.85/0.97 | — | 30/110/ 0.8/0.99 | — | — | 40/110/ 0.9/0.94 |
| [1] |
CHEN Chiyuan, WU H M, WANG Lei, et al. Practical Integrity Preservation for Data Streaming in Cloud-Assisted Healthcare Sensor Systems[J]. Computer Networks, 2017, 129(5): 472-480.
doi: 10.1016/j.comnet.2017.05.032 URL |
| [2] |
TIAN Junfeng, WANG Ziwei. Cloud Data Assured Deletion Scheme Based on Dynamic Sliding Window[J]. Peer to Peer Networking and Applications, 2022, 15: 1817-1833.
doi: 10.1007/s12083-022-01318-3 URL |
| [3] |
YU Ying, LI Shan, MA Jing. Time-Aware Cloud Manufacturing Service Selection Using Unknown QoS Prediction and Uncertain User Preferences[J]. Concurrent Engineering, 2021, 29(4): 370-385.
doi: 10.1177/1063293X211019503 URL |
| [4] |
FENG Chenwei, WANG Yan. Optimization of Parallel Task Scheduling in Cloud Manufacturing System[J]. Journal of System Simulation, 2019, 31(12): 2626-2635.
doi: 10.16182/j.issn1004731x.joss.19-FZ0275 |
|
冯晨微, 王艳. 云制造系统并行任务优化调度[J]. 系统仿真学报, 2019, 31(12):2626-2635.
doi: 10.16182/j.issn1004731x.joss.19-FZ0275 |
|
| [5] |
VERMA P, TAPASWI S, GODFREY W. AVDR: A Framework for Migration Policy to Handle DDoS Attacked VM in Cloud[J]. Wireless Personal Communications, 2020, 115(2): 1335-1361.
doi: 10.1007/s11277-020-07630-6 URL |
| [6] | LIN Chuang, SU Wenbo, MENG Kun, et al. Cloud Computing Security: Architecture, Mechanism and Model Evaluation[J]. Chinese Journal of computer science, 2013, 36(9): 1765-1784. |
| 林闯, 苏文博, 孟坤, 等. 云计算安全:架构、机制与模型评价[J]. 计算机学报, 2013, 36(9):1765-1784. | |
| [7] | YU Chengli, ZHANG Yang, JIA Shijie. Research on Data Security Threats and Protection of Key Technologies in Cloud Environment[J]. Netinfo Security, 2022, 22(7): 55-63. |
| 于成丽, 张阳, 贾世杰. 云环境中数据安全威胁与防护关键技术研究[J]. 信息网络安全, 2022, 22(7):55-63. | |
| [8] | ZHANG Yuqing, WANG Xiaofei, LIU Xuefeng, et al. Survey on Cloud Computing Security[J]. Journal of Software, 2016, 27(6): 1328-1348. |
| 张玉清, 王晓菲, 刘雪峰, 等. 云计算环境安全综述[J]. 软件学报, 2016, 27(6):1328-1348. | |
| [9] | LU Hongwei, REN Lixia, CHEN Yizhong, et al. A Cloud Model Based Multi-Attribute Decision Making Approach for Selection and Evalution of Groundwater Management Schemes[J]. Journal of Hydrology, 2017(555): 881-893. |
| [10] | WANG Lijing, WANG Xingwei, HUANG Min. Research on a Cloud Resource Allocation Mechanism Based on Double Auction and Cell Membrane Optimization Algorithm[J]. Netinfo Security, 2016, 16(12): 51-59. |
| 王梨静, 王兴伟, 黄敏. 一种基于双向拍卖和细胞膜优化的云资源分配机制的研究[J]. 信息网络安全, 2016, 16 (12):51-59. | |
| [11] |
YU Chunxia, ZHANG Luping, ZHAO Wenfan, et al. A Blockchain-Based Service Composition Architecture in Cloud Manufacturing[J]. International Journal of Computer Integrated Manufacturing, 2020, 33(7): 701-715.
doi: 10.1080/0951192X.2019.1571234 URL |
| [12] | BARENJI R V. A Blockchain Technology Based Trust System for Cloud Manufacturing[J]. Journal of Intelligent Manufacturing, 2021: 1-15. |
| [13] |
SIMEONE A, CAGGIANO A, DENG Bin, et al. A Deep Learning Based-Decision Support Tool for Solution Recommendation in Cloud Manufacturing Platforms[J]. Procedia CIRP, 2019, 86: 68-73.
doi: 10.1016/j.procir.2020.01.019 URL |
| [14] | ZHAO Daozhi, LI Rui. Two-Sided Matching Mechanism with Agents’ Expectation for Cloud Manufacturing Resource[J]. Control and Decision, 2017, 32(5): 871-878. |
| 赵道致, 李锐. 考虑主体心理预期的云制造资源双边匹配机制[J]. 控制与决策, 2017, 32(5):871-878. | |
| [15] |
JIN Hong, YAO Xifan, CHEN Yong. Correlation-Aware QoS Modeling and Manufacturing Cloud Service Composition[J]. Journal of Intelligent Manufacturing, 2017, 28(8): 1947-1960.
doi: 10.1007/s10845-015-1080-2 URL |
| [16] |
LI Li, WANG Wanliang, LI Weikun, et al. A Novel Ranking-Based Optimal Guides Selection Strategy in MOPSO[J]. Procedia Computer Science, 2016, 91(1): 1001-1010.
doi: 10.1016/j.procs.2016.07.135 URL |
| [17] |
FAIK B, FULYA Z, MIRAC F, et al. The Evaluation of Renewable Energy Alternatives for Sustainable Development in Turkey Using Intuitionistic Fuzzy-TOPSIS Method[J]. Renewable Energy, 2022, 189:1443-1458.
doi: 10.1016/j.renene.2022.03.058 URL |
| [18] |
SUN Yan, LIN Fuhong, XU Haitao. Multi-Objective Optimization of Resource Scheduling in Fog Computing Using an Improved NSGA-II[J]. Wireless Personal Communications, 2018, 102(2): 1369-1385.
doi: 10.1007/s11277-017-5200-5 URL |
| [1] | 孔嘉琪, 王利明, 葛晓雪. 基于模拟退火和粒子群混合改进算法的数据库水印技术[J]. 信息网络安全, 2022, 22(5): 37-45. |
| [2] | 陈妍, 韦湘, 陆臻. 云计算环境下网络安全产品检测方法研究[J]. 信息网络安全, 2022, 22(12): 1-6. |
| [3] | 尹梦梦, 王磊, 姚昌华, 武欣嵘. 基于VIKOR模型的复杂网络节点重要度评估[J]. 信息网络安全, 2022, 22(1): 87-94. |
| [4] | 宋玉龙, 王磊, 武欣嵘, 曾维军. 基于模拟退火自适应粒子群算法的WSN拓扑抗毁性方法研究[J]. 信息网络安全, 2021, 21(6): 89-96. |
| [5] | 郑禄鑫, 张健. 云安全面临的威胁和未来发展趋势[J]. 信息网络安全, 2021, 21(10): 17-24. |
| [6] | 余小军, 吴亚飚, 张玉清. 云安全体系结构设计研究[J]. 信息网络安全, 2020, 20(9): 62-66. |
| [7] | 徐玉伟, 赵宝康, 时向泉, 苏金树. 容器化安全服务功能链低延迟优化编排研究[J]. 信息网络安全, 2020, 20(7): 11-18. |
| [8] | 王晓, 赵军, 张建标. 基于可信软件基的虚拟机动态监控机制研究[J]. 信息网络安全, 2020, 20(2): 7-13. |
| [9] | 梅东晖, 李红灵. 基于多目标混合粒子群算法的虚拟机负载均衡研究[J]. 信息网络安全, 2018, 18(2): 78-83. |
| [10] | 张健, 高铖, 宫良一, 顾兆军. 虚拟机自省技术研究[J]. 信息网络安全, 2017, 17(9): 63-68. |
| [11] | 杨艳萍. 基于双向加权图的社交网络用户可信度算法研究[J]. 信息网络安全, 2017, 17(7): 40-44. |
| [12] | 张雪博, 刘敬浩, 付晓梅. 基于改进Logistic回归算法的抗Web DDoS攻击模型的设计与实现[J]. 信息网络安全, 2017, 17(6): 62-67. |
| [13] | 王文旭, 张健, 常青, 顾兆军. 云计算虚拟化平台安全问题研究[J]. 信息网络安全, 2016, 16(9): 163-168. |
| [14] | 廖子渊, 陈明志, 邓辉. 基于评价可信度的云计算信任管理模型研究[J]. 信息网络安全, 2016, 16(2): 33-39. |
| [15] | 卿斯汉. 关键基础设施安全防护[J]. 信息网络安全, 2015, 15(2): 1-6. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 109
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 240
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||