信息网络安全 ›› 2022, Vol. 22 ›› Issue (10): 98-107.doi: 10.3969/j.issn.1671-1122.2022.10.014
智能穿戴设备的安全与隐私威胁研究
- 1.江苏警官学院计算机信息与网络安全系,南京 210031
2.江苏省电子数据取证分析工程研究中心,南京 210031
-
收稿日期:2022-08-11出版日期:2022-10-10发布日期:2022-11-15 -
通讯作者:倪雪莉 E-mail:nixueli@jspi.edu.cn -
作者简介:倪雪莉(1990—),女,江苏,讲师,硕士,主要研究方向为信息安全、电子数据取证|王群(1971—),男,甘肃,教授,博士,主要研究方向为网络空间安全治理、电子数据取证|梁广俊(1982—),男,安徽,讲师,博士,主要研究方向为电子数据取证、网络空间安全 -
基金资助:江苏省高校自然科学研究重大项目(20KJA520004);江苏省公安厅科技研究项目(2020KX008)
Research on Security and Privacy Threats of Smart Wearable Devices
NI Xueli1,2( ), WANG Qun1,2, LIANG Guangjun1,2
), WANG Qun1,2, LIANG Guangjun1,2
- 1. Department of Computer Information and Cyber Security, Jiangsu Police Institute, Nanjing 210031, China
2. Jiangsu Electronic Data Forensics and Analysis Engineering Research Center, Nanjing 210031, China
-
Received:2022-08-11Online:2022-10-10Published:2022-11-15 -
Contact:NI Xueli E-mail:nixueli@jspi.edu.cn
摘要:
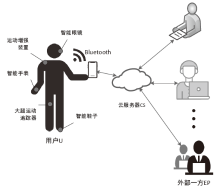
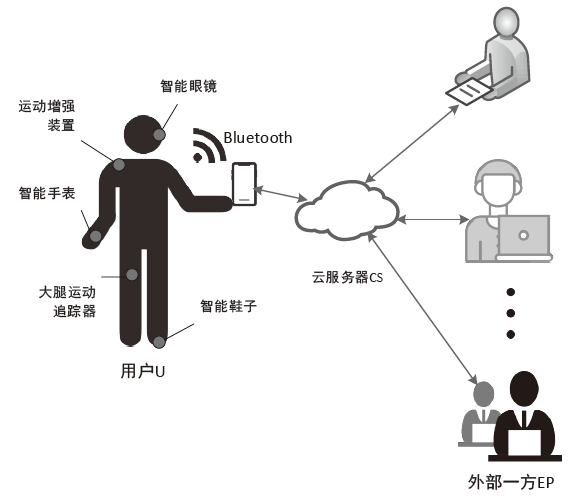
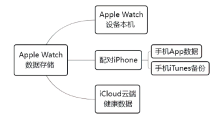
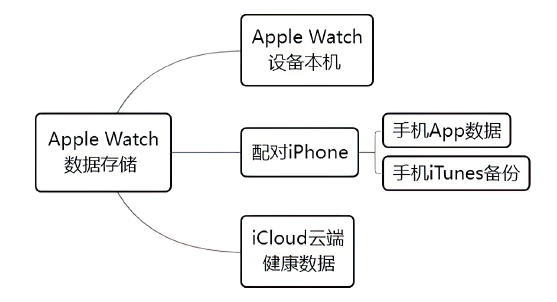
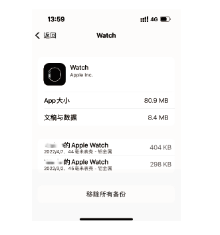
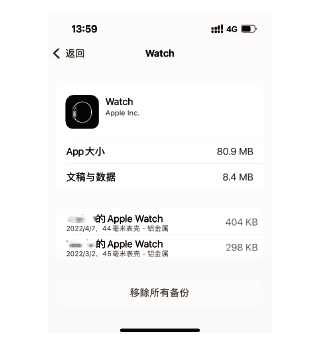
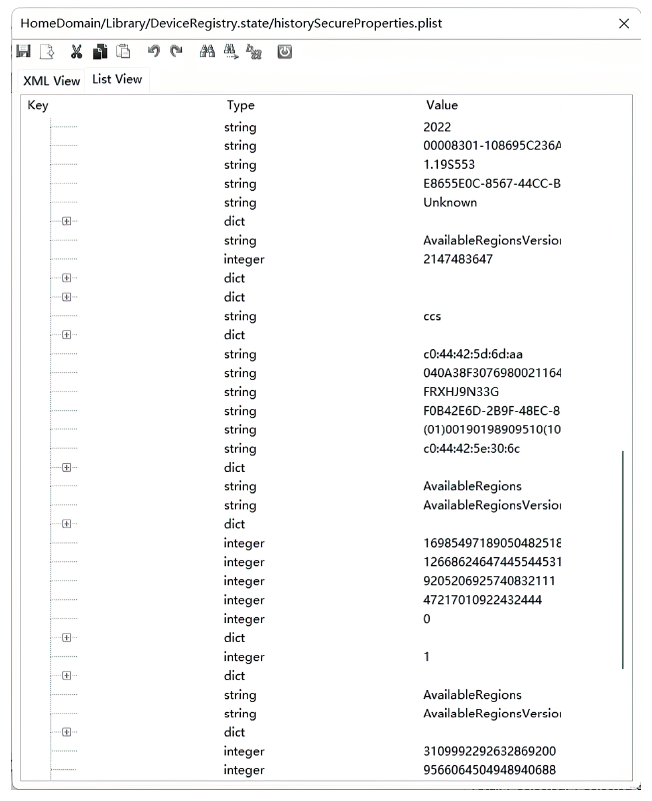
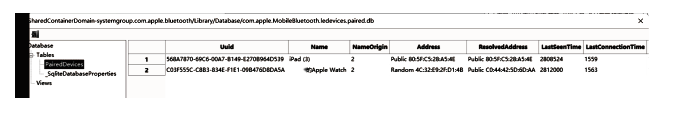
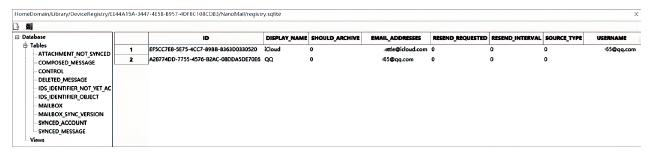
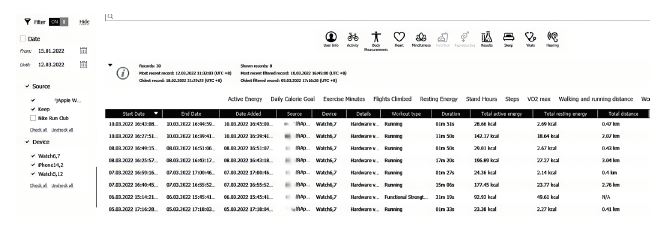
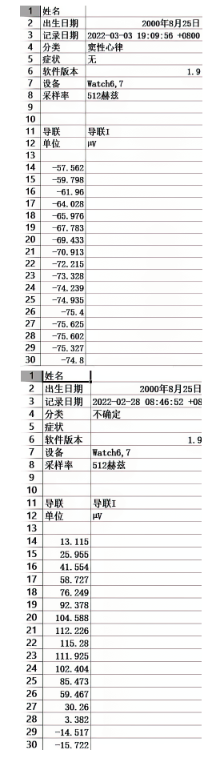
文章从设备架构和数据通信两方面研究了智能穿戴设备广泛存在的安全问题。以Apple Watch为例,基于智能手表上敏感数据的存储和传输方式,提出敏感数据的提取模型,该模型创新性地结合设备本机及配对设备来分析智能穿戴设备收集存储的敏感数据存在的安全风险。文章通过提取实例验证了模型的有效性,智能手表类穿戴计算设备不仅具有采集大量敏感数据的能力,且在数据存储和配对机制方面存在安全与隐私威胁。文章提出的模型及实验验证过程对进一步研究物联网环境下的各类智能终端设备安全具有重要意义。
中图分类号:
引用本文
倪雪莉, 王群, 梁广俊. 智能穿戴设备的安全与隐私威胁研究[J]. 信息网络安全, 2022, 22(10): 98-107.
NI Xueli, WANG Qun, LIANG Guangjun. Research on Security and Privacy Threats of Smart Wearable Devices[J]. Netinfo Security, 2022, 22(10): 98-107.
表1
智能穿戴设备的主要通信方式及安全威胁
| 通信方式 | 安全威胁 |
|---|---|
| USB连接 | 若攻击者感染了穿戴设备所连接的设备(如手机、PC等)或拥有该设备的物理访问权限,则有可能通过USB连接获得穿戴设备上的所有数据 |
| 蓝牙 | 蓝牙低能耗(Bluetooth Low Energy, BLE)技术因其超低能耗、高数据传输速度、易于开发等特点,已成为物联网和智能穿戴设备的实际通信协议。由于该协议设计简单,所以存在大量的安全和隐私漏洞[ |
| NFC | 最新的穿戴设备可以通过近场通信(Near Field Communication,NFC)技术进行通信。攻击者在近距离内会尝试以窃听、篡改、伪造身份[ |
| WiFi | 较新的穿戴设备能够直接连接WiFi网络,在针对WiFi环境的网络攻击行为持续演化和升级的态势下[ |
| 蜂窝移动 网络 | 部分功能较强大的穿戴设备具备蜂窝移动网络功能(如Apple Watch),针对无线空口的各类攻击与漏洞不断出现并被公开披露[ |
| [1] | SUN Wen, LIU Jiajia, ZHANG Haibin. When Smart Wearables Meet Intelligent Vehicles: Challenges and Future Directions[J]. IEEE Wireless Communications, 2017, 24(3): 58-65. |
| [2] | WALTER C, HALE M L, GAMBLE R F. Imposing Security Awareness on Wearables[C]// IEEE. 2016 IEEE/ACM 2nd International Workshop on Software Engineering for Smart Cyber-Physical Systems (SEsCPS). Austin: IEEE, 2016: 29-35. |
| [3] | QIU Yue. Security Analysis for the Information of Wearable Devices[J]. Netinfo Security, 2016, 16(9): 79-83. |
| 裘玥. 智能可穿戴设备信息安全分析[J]. 信息网络安全, 2016, 16(9): 79-83. | |
| [4] | MICHAEL K, MICHAEL M G. Apple Watch Temptation: Just Visit the App Store[J]. IEEE Consumer Electronics Magazine, 2015, 4(4): 120-122. |
| [5] | HATHALIYA J J, TANWAR S. An Exhaustive Survey on Security and Privacy Issues in Healthcare 4.0[J]. Computer Communications, 2020, 153: 311-335. |
| [6] | DO Q, MARTINI B, CHOO K. Is the Data on Your Wearable Device Secure? An Android Wear Smartwatch Case Study[J]. Software: Practice and Experience, 2017, 47(3): 391-403. |
| [7] | ZHANG Chi, SHAHRIAR H, RIAD A. Security and Privacy Analysis of Wearable Health Device[C]// IEEE. 2016 IEEE/ACM 2nd International Workshop on Software Engineering for Smart Cyber-Physical Systems (SEsCPS). Madrid: IEEE, 2020: 1767-1772. |
| [8] | BARUA A, ALAMIN A A, HOSSAIN S, et al. Security and Privacy Threats for Bluetooth Low Energy in IoT and Wearable Devices: A Comprehensive Survey[J]. IEEE Open Journal of the Communications Society, 2022, 3: 251-281. |
| [9] | YANG Minghui, GUO Junqi, ZHAO Ziyun, et al. Teenager Health Oriented Data Security and Privacy Protection Research for Smart Wearable Device[J]. Procedia Computer Science, 2020, 174: 333-339. |
| [10] | DAS A K, WAZID M, KUMAR N, et al. Design of Secure and Lightweight Authentication Protocol for Wearable Devices Environment[J]. IEEE Journal of Biomedical and Health Informatics, 2018, 22(4): 1310-1322. |
| [11] | SIBONI S, SHABTAI A, TIPPENHAUER N O, et al. Advanced Security Testbed Framework for Wearable IoT Devices[J]. ACM Transactions on Internet Technology, 2016, 16(4): 1-26. |
| [12] | AHMAD M, ALQARNI M A, KHAN A, et al. Smartwatch-Based Legitimate User Identification for Cloud-Based Secure Services[EB/OL]. (2018-08-14)[2022-05-03]. https://www.hindawi.com/journals/misy/2018/5107024/. |
| [13] | LEE J, PARK S, KIM Y G, et al. Advanced Authentication Method by Geometric Data Analysis Based on User Behavior and Biometrics for IoT Device with Touchscreen[J]. Electronics, 2021, 10(21): 1-13. |
| [14] | LIU Wei, LIU Hong, WAN Yueliang, et al. The Yoking-Proof-Based Authentication Protocol for Cloud-Assisted Wearable Devices[J]. Personal & Ubiquitous Computing, 2016, 20(3): 469-479. |
| [15] | LIU Sha, HU Shun, WENG Jian, et al. A Novel Asymmetric Three-party Based Authentication Scheme in Wearable Devices Environment[J]. Journal of Network & Computer Applications, 2016, 60: 144-154. |
| [16] | DEY S, ROY N, XU W, et al. AccelPrint: Imperfections of Accelerometers Make Smartphones Trackable[C]// ISOC. 2014 Network and Distributed System Security Symposium. San Diego: ISOC, 2014: 1-16. |
| [17] | MICHALEVSKY Y, BONEH D, NAKIBLY G. Gyrophone: Recognizing Speech From Gyroscope Signals[C]// USENIX Association. 23rd USENIX Security Symposium. San Diego: USENIX, 2014: 1053-1067. |
| [18] | ZHANG Chen. NFC Lightweight Security Authentication Method in Internet of Things[D]. Xi’an: Xidian University, 2019. |
| 张晨. 物联网下NFC轻量级安全认证方法研究[D]. 西安: 西安电子科技大学, 2019. | |
| [19] | WANG Ting, WANG Na, CUI Yunpeng, et al. The Optimization Method of Wireless Network Attacks Detection Based on Semi-Supervised Learning[J]. Journal of Computer Research and Development, 2020, 57(4): 791-802. |
| 王婷, 王娜, 崔运鹏, 等. 基于半监督学习的无线网络攻击行为检测优化方法[J]. 计算机研究与发展, 2020, 57(4): 791-802. | |
| [20] | ZHAO Haoming. Research on Security Flaws and Attack Verification of Mobile Communication[D]. Chongqing: Chongqing University of Posts and Telecommunications, 2021. |
| 赵昊明. 移动通信网络安全缺陷研究与攻击验证[D]. 重庆: 重庆邮电大学, 2021. |
| [1] | 于晶, 袁曙光, 袁煜琳, 陈驰. 基于k匿名数据集的鲁棒性水印技术研究[J]. 信息网络安全, 2022, 22(9): 11-20. |
| [2] | 张敏, 许春香, 张建华. 无人机网络中基于多因子的认证密钥协商协议研究[J]. 信息网络安全, 2022, 22(9): 21-30. |
| [3] | 张学旺, 刘宇帆. 可追踪身份的物联网感知层节点匿名认证方案[J]. 信息网络安全, 2022, 22(9): 55-62. |
| [4] | 刘芹, 张标, 涂航. 基于twisted Edwards曲线的无证书盲签名方案[J]. 信息网络安全, 2022, 22(8): 19-25. |
| [5] | 胡艺, 佘堃. 基于区块链和智能合约的双链车联网系统[J]. 信息网络安全, 2022, 22(8): 26-35. |
| [6] | 王健, 黄俊. 基于智能合约的日志安全存储与公平访问方法[J]. 信息网络安全, 2022, 22(7): 27-36. |
| [7] | 于成丽, 张阳, 贾世杰. 云环境中数据安全威胁与防护关键技术研究[J]. 信息网络安全, 2022, 22(7): 55-63. |
| [8] | 秦宝东, 余沛航, 郑东. 基于双陷门同态加密的决策树分类模型[J]. 信息网络安全, 2022, 22(7): 9-17. |
| [9] | 洪晟, 李雷, 原义栋, 高欣妍. 处理器微架构存储体系侧信道协同安全技术研究[J]. 信息网络安全, 2022, 22(6): 26-37. |
| [10] | 赵洪, 李姗, 左珮良, 魏占祯. 基于强化学习的物联网安全资源分配方法[J]. 信息网络安全, 2022, 22(6): 44-52. |
| [11] | 于克辰, 郭莉, 阴宏伟, 燕雪松. 面向数据中心场景的基于区块链与博弈论的高价值数据共享模型[J]. 信息网络安全, 2022, 22(6): 73-85. |
| [12] | 王鹃, 王蕴茹, 翁斌, 龚家新. 机器学习在x86二进制反汇编中的应用研究综述[J]. 信息网络安全, 2022, 22(6): 9-25. |
| [13] | 孙鹏宇, 谭晶磊, 李晨蔚, 张恒巍. 基于时间微分博弈的网络安全防御决策方法[J]. 信息网络安全, 2022, 22(5): 64-74. |
| [14] | 金波, 唐前进, 唐前临. CCF计算机安全专业委员会2022年网络安全十大发展趋势解读[J]. 信息网络安全, 2022, 22(4): 1-6. |
| [15] | 李国旗, 洪晟, 兰雪婷, 张虹. 多旋翼无人机系统的信息安全参考模型[J]. 信息网络安全, 2022, 23(3): 10-19. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||