信息网络安全 ›› 2021, Vol. 21 ›› Issue (4): 62-72.doi: 10.3969/j.issn.1671-1122.2021.04.007
基于漏洞动态可利用性的网络入侵路径分析方法
- 1.国防科技大学电子对抗学院,合肥 230037
2.中国酒泉卫星发射中心,酒泉 732750
3.网络空间安全态势感知与评估安徽省重点实验室,合肥 230037
-
收稿日期:2020-08-11出版日期:2021-04-10发布日期:2021-05-14 -
通讯作者:刘京菊 E-mail:jingjul@aliyun.com -
作者简介:张凯(1992—),男,安徽,硕士研究生,主要研究方向为网络空间安全态势感知|刘京菊(1974—),女,湖北,教授,博士,主要研究方向为网络空间安全态势感知和安全检测 -
基金资助:国家重点研发计划(2017YFB0802905)
Network Attack Path Analysis Method Based on Vulnerability Dynamic Availability
ZHANG Kai1,2,3, LIU Jingju1,3( )
)
- 1. College of Electronic Engineering, National University of Defense Technology, Hefei 230037, China
2. Jiuquan Satellite Launch Center, Jiuquan 732750, China
3. Anhui Province Key Laboratory of Cyberspace Security Situation Awareness and Evaluation, Hefei 230037, China
-
Received:2020-08-11Online:2021-04-10Published:2021-05-14 -
Contact:LIU Jingju E-mail:jingjul@aliyun.com
摘要:
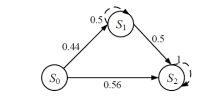
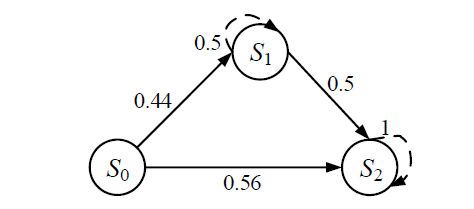
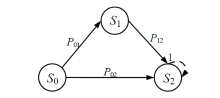
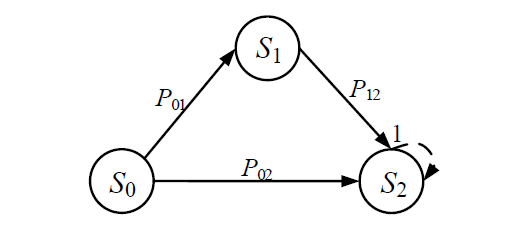
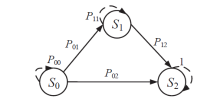
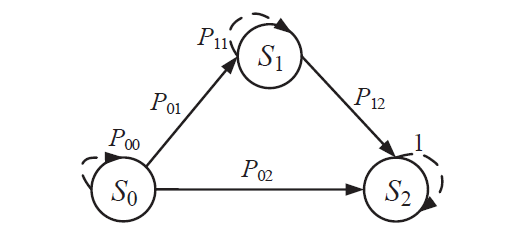
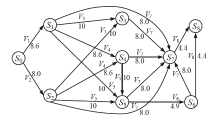
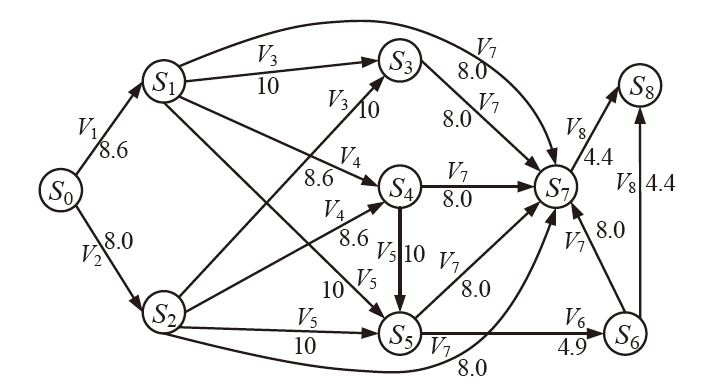
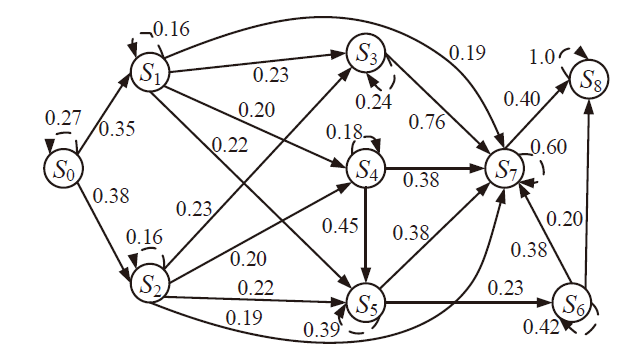
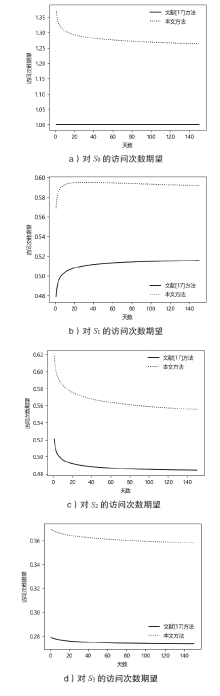
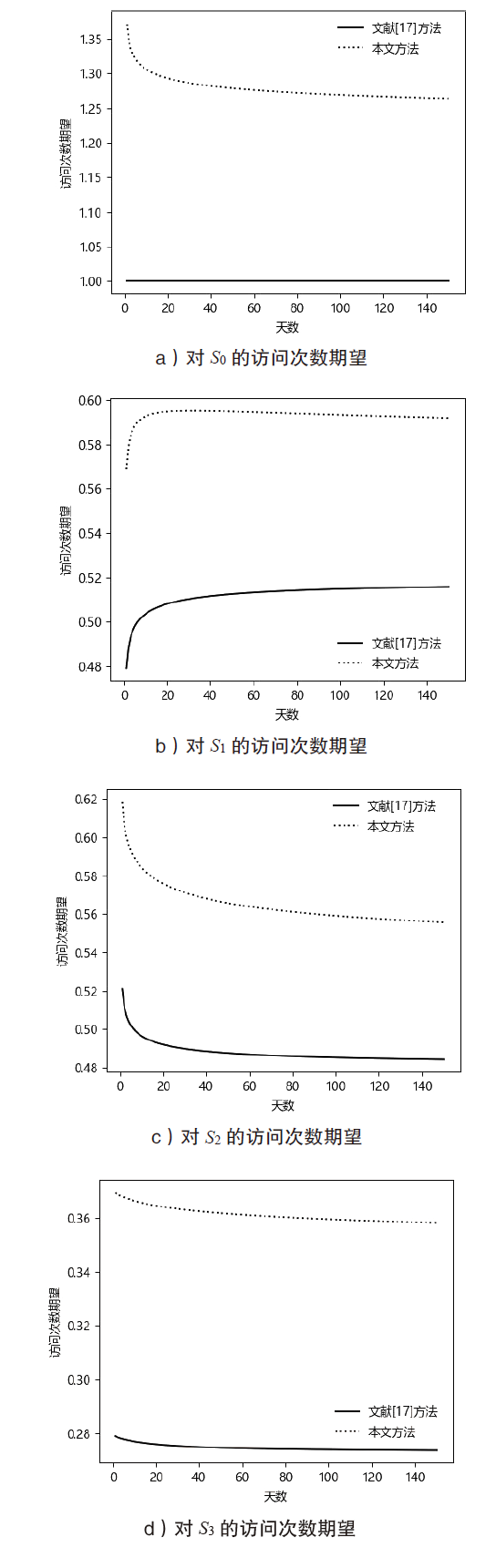
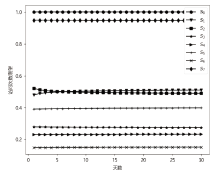
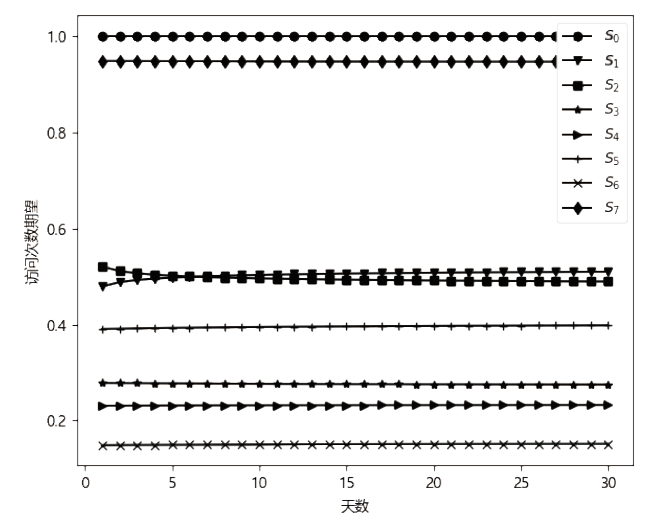
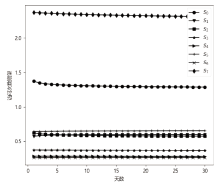
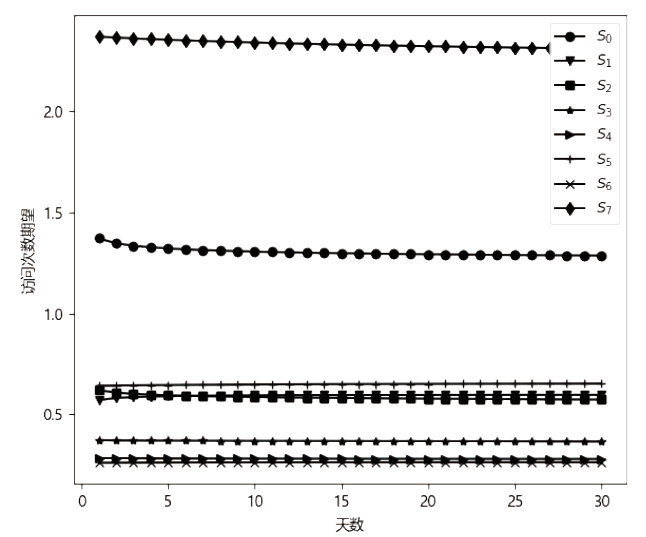
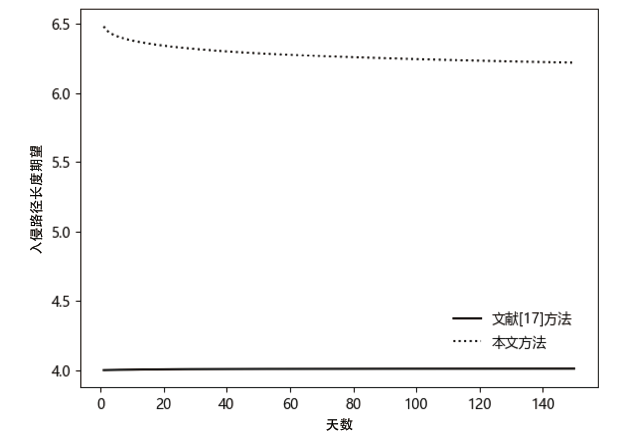
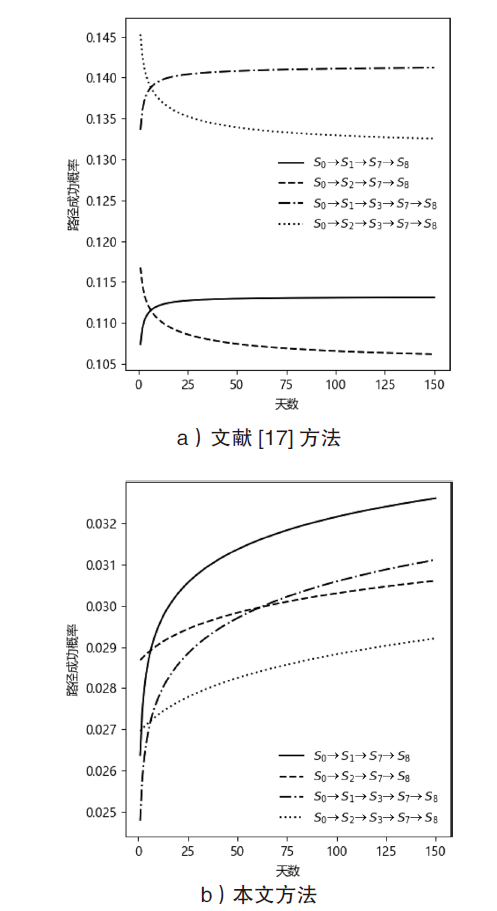
现有的网络入侵路径分析方法未考虑漏洞的动态特征,且在描述漏洞利用导致的状态转移时,未考虑漏洞利用失败的情形。通过建模漏洞可利用性随时间的变化,文章提出一种改进状态转移概率计算方法的吸收Markov链模型。该模型结合网络攻防实际,考虑漏洞利用失败的情形,合理计算状态转移概率:首先对目标网络生成攻击图,在计算漏洞动态可利用概率的基础上,构建吸收Markov链;然后利用状态转移概率矩阵的性质,计算状态节点威胁度排序、入侵路径长度期望和路径成功概率,并在时间维度上进行分析。实验分析表明,文章方法相比已有方法在节点威胁度排序上更准确,对入侵路径长度期望和路径成功概率的计算更加符合网络攻防实际。
中图分类号:
引用本文
张凯, 刘京菊. 基于漏洞动态可利用性的网络入侵路径分析方法[J]. 信息网络安全, 2021, 21(4): 62-72.
ZHANG Kai, LIU Jingju. Network Attack Path Analysis Method Based on Vulnerability Dynamic Availability[J]. Netinfo Security, 2021, 21(4): 62-72.
使用本文
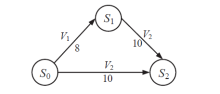
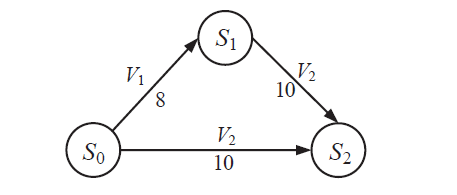
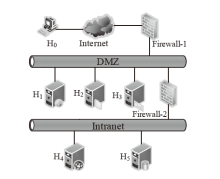
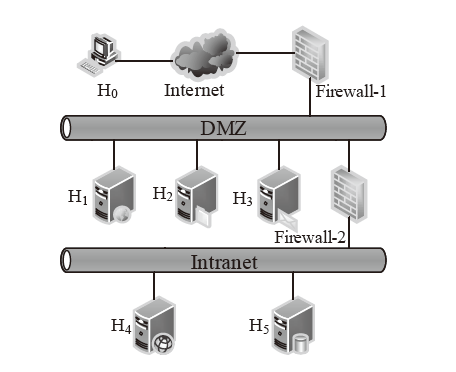
表2
主机配置信息和漏洞信息
| 主机 | 服务/应用 | 漏洞 | 编号 | 可利用性得分 | 披露时间 |
|---|---|---|---|---|---|
| H1 | openSSh | CVE-2019-6111 | V1 | 8.6 | 2019.1.31 |
| Apache ATS 6.2.2 | CVE-2018-8004 | V2 | 8.0 | 2018.8.29 | |
| H2 | TFTP Server | CVE-2018-8476 | V3 | 10 | 2018.11.13 |
| H3 | Oracle E-Business Suite 12.1.1 | CVE-2019-2491 | V4 | 8.6 | 2019.1.17 |
| H4 | IBM Security Key Lifecycle Manager 3.0 | CVE-2018-1751 | V5 | 10 | 2019.1.23 |
| Windows Server 2008 R2 | CVE-2018-8345 | V6 | 4.9 | 2018.8.15 | |
| H5 | MySQL Server 8.0.12 | CVE-2018-3286 | V7 | 8.0 | 2018.10.16 |
| CVE-2019-2503 | V8 | 4.4 | 2019.1.16 |
| [1] | LIU Xinran, LI Baisong, CHANG Anqi, et al. The Current Network Security Situation and Emergency Network Response[J]. Strategic Study of CAE, 2016,18(6):83-88. |
| 刘欣然, 李柏松, 常安琪, 等. 当前网络安全形势与应急响应[J]. 中国工程科学, 2016,18(6):83-88. | |
| [2] | YANG Junnan, ZHANG Hongqi, ZHANG Chuanfu, et al. Intrusion Path Prediction Based on Incomplete Information Multi-stage Game[J]. Application Research of Computers, 2019,36(2):519-524. |
| 杨峻楠, 张红旗, 张传富, 等. 基于不完全信息多阶段博弈的入侵路径预测[J]. 计算机应用研究, 2019,36(2):519-524. | |
| [3] | KORDY B, PIÈTRE-CAMBACÉDÈS L, SCHWEITZER P. DAG-based Attack and Defense Modeling: Don't Miss the Forest for the Attack Trees(Review)[J]. Computer Science Review, 2014,13(11):1-38. |
| [4] | YANG Yingjie, LENG Qiang, CHANG Dexian, et al. Research on Network Dynamic Threat Analysis Technology Based on Attribute Attack Graph[J]. Journal of Electronics & Information Technology, 2019,41(8):1838-1846. |
| 杨英杰, 冷强, 常德显, 等. 基于属性攻击图的网络动态威胁分析技术研究[J]. 电子与信息学报, 2019,41(8):1838-1846. | |
| [5] | WANG Hui, RU Xinxin, DAI Tianwang, et al. Attack Profit Path Prediction Algorithm Based on NAPG Model[J]. Journal of Jilin University(Science Edition), 2019,37(5):1169-1178. |
| 王辉, 茹鑫鑫, 戴田旺, 等. 基于NAPG模型的攻击增益路径预测算法[J]. 吉林大学学报(理学版), 2019,37(5):1169-1178. | |
| [6] | HU Hao, LIU Yuling, ZHANG Hongqi, et al. Route Prediction Method for Network Intrusion Using Absorbing Markov Chain[J]. Journal of Computer Research and Development, 2018,55(4):831-845. |
| 胡浩, 刘玉岭, 张红旗, 等. 基于吸收Markov链的网络入侵路径预测方法[J]. 计算机研究与发展, 2018,55(4):831-845. | |
| [7] | WANG Fan. Research on Network Security Risk Assessment Method Based on Bayesian Attack Graph[D]. Xi’an: Northwest University, 2018. |
| 王帆. 基于贝叶斯攻击图的网络安全风险评估方法研究[D]. 西安:西北大学, 2018. | |
| [8] | LIU Yu, MAN Hong. Network Vulnerability Assessment Using Bayesian Networks[EB/OL]. https://spie.org/Publications/Proceedings/Paper/10.1117/12.604240, 2020-05-31. |
| [9] |
POOLSAPPASIT N, DEWRI R, RAY I. Dynamic Security Risk Management Using Bayesian Attack Graphs[J]. IEEE Transactions on Dependable and Secure Computing, 2012,9(1):61-74.
doi: 10.1109/TDSC.2011.34 URL |
| [10] | FANG Yan, YIN Xiaochuan, LI Jingzhi. Research of Quantitative Network Security Assessment Based on Bayesian-attack Graphs[J]. Application Research of Computers, 2013,30(9):2763-2766. |
| 方研, 殷肖川, 李景志. 基于贝叶斯攻击图的网络安全量化评估研究[J]. 计算机应用研究, 2013,30(9):2763-2766. | |
| [11] | MA Chunguang, WANG Chenghong, ZHANG Donghong, et al. A Dynamic Network Risk Assessment Model Based on Attacker’s Inclination[J]. Journal of Computer Research and Development, 2015,58(9):2056-2068. |
| 马春光, 汪诚弘, 张东红, 等. 一种基于攻击意愿分析的网络风险动态评估模型[J]. 计算机研究与发展, 2015,58(9):2056-2068. | |
| [12] | WANG Yang, WU Jianying, HUANG Jinlei, et al. Network Intrusion Intention Recognition Method Based on Bayesian Attack Graph[J]. Computer Engineering and Applications, 2019,55(22):73-79. |
| 王洋, 吴建英, 黄金垒, 等. 基于贝叶斯攻击图的网络入侵意图识别方法[J]. 计算机工程与应用, 2019,55(22):73-79. | |
| [13] | WANG Shuo, TANG Guangming, KOU Guang, et al. Attack Path Prediction Method Based on Causal Knowledge Net[J]. Journal on Communications, 2016,37(10):188-198. |
| 王硕, 汤光明, 寇广, 等. 基于因果知识网络的攻击路径预测方法[J]. 通信学报, 2016,37(10):188-198. | |
| [14] | YUSUF S E, GE M, HONG J B, et al. Evaluating the Effectiveness of Security Metrics for Dynamic Networks[C]// IEEE. 2017 IEEE Trustcom/BigDataSE/ICESS, August 1-4, 2017, Sydney, NSW, Australia. NJ: IEEE, 2017: 277-284. |
| [15] | YUSUF S E, GE M, HONG J B, et al. Security Modelling and Analysis of Dynamic Enterprise Networks[C]// IEEE. 2016 IEEE International Conference on Computer & Information Technology, December 8-10, 2016, Nadi, Fiji. NJ: IEEE, 2016: 249-256. |
| [16] | ABRAHAM S, NAIR S. Cyber Security Analytics: A Stochastic Model for Security Quantification Using Absorbing Markov Chains[J]. Journal of Communications, 2014,9(12):899-907. |
| [17] | ABRAHAM S, NAIR S. A Predictive Framework for Cyber Security Analytics using Attack Graphs[J]. International Journal of Computer Networks & Communications, 2015,7(1):1-17. |
| [18] |
FENG Pinghui, LIAN Yifeng, DAI Yingxia, et al. A Vulnerability Model of Distributed Systems Based on Reliability Theory[J]. Journal of Software, 2006,17(7):1633-1640.
doi: 10.1360/jos171633 URL |
| 冯萍慧, 连一峰, 戴英侠, 等. 基于可靠性理论的分布式系统脆弱性模型[J]. 软件学报, 2006,17(7):1633-1640. | |
| [19] | WANG Xiujuan, SUN Bo, LIAO Yanwen, et al. Computer Network Vulnerability Assessment Based on Bayesian Attribute Network[J]. Journal of Beijing University of Posts and Telecommunications, 2015,38(4):110-116. |
| 王秀娟, 孙博, 廖彦文, 等. 贝叶斯属性攻击图网络脆弱性评估[J]. 北京邮电大学学报, 2015,38(4):110-116. | |
| [20] | GRINSTEAD C M, SNELL J L. Introduction to Probability[M]. Rhodel Island: American Mathematical Soc, 2012. |
| [21] | HU Hao, YE Runguo, ZHANG Hongqi, et al. Vulnerability Life Cycle Oriented Security Risk Metric Method[J]. Journal of Software, 2018,29(5):1213-1229. |
| 胡浩, 叶润国, 张红旗, 等. 面向漏洞生命周期的安全风险度量方法[J]. 软件学报. 2018,29(5):1213-1229. | |
| [22] | FREI S. Security Econometrics: The Dynamics of (in) Security[M]. Charlton: BookSurge Publishing, 2009. |
| [23] | YOUSEFI M, MTETWA N, ZHANG Yan, et al. A Novel Approach for Analysis of Attack Graph[C]// IEEE. 2017 IEEE International Conference on Intelligence and Security Informatics, July 22-24, 2017, Beijing, China. NJ: IEEE, 2017: 7-12. |
| [1] | 张昱, 孙光民, 李煜. 基于SM9算法的移动互联网身份认证方案研究[J]. 信息网络安全, 2021, 21(4): 1-9. |
| [2] | 郑洪英, 李琳, 肖迪. 面向雾计算的压缩感知图像秘密传输和篡改恢复方案[J]. 信息网络安全, 2021, 21(4): 10-20. |
| [3] | 游文婷, 张乐友, 叶亚迪, 李晖. 多用户通信机制中支持隐私保护的属性基动态广播加密[J]. 信息网络安全, 2021, 21(4): 21-30. |
| [4] | 宋宇波, 马文豪, 胡爱群, 王俊波. 一种基于像素值偏移编解码技术的屏摄隐通道研究[J]. 信息网络安全, 2021, 21(4): 31-38. |
| [5] | 蔡满春, 王腾飞, 岳婷, 芦天亮. 基于ARF的Tor网站指纹识别技术[J]. 信息网络安全, 2021, 21(4): 39-48. |
| [6] | 王健, 赵曼莉, 陈志浩, 石波. 基于假名的智能交通条件隐私保护认证协议[J]. 信息网络安全, 2021, 21(4): 49-61. |
| [7] | 林文兵, 张敏情, 周能, 孔咏骏. 基于同态加密的密文域可逆信息隐藏技术研究[J]. 信息网络安全, 2021, 21(4): 73-80. |
| [8] | 任航, 程相国, 张睿, 夏辉. 基于议价贝叶斯博弈模型的防欺诈策略[J]. 信息网络安全, 2021, 21(4): 81-88. |
| [9] | 梁晓兵, 孔令达, 刘岩, 叶莘. 轻量级嵌入式软件动态二进制插桩算法[J]. 信息网络安全, 2021, 21(4): 89-95. |
| [10] | 石乐义, 徐兴华, 刘祎豪, 刘佳. 一种改进概率神经网络的工业控制系统安全态势评估方法[J]. 信息网络安全, 2021, 21(3): 15-25. |
| [11] | 刘延华, 刘志煌. 一种基于用户行为模式的匿名数据鉴定方法[J]. 信息网络安全, 2021, 21(3): 44-52. |
| [12] | 李佳玮, 吴克河, 张波. 基于高斯混合聚类的电力工控系统异常检测研究[J]. 信息网络安全, 2021, 21(3): 53-63. |
| [13] | 路宏琳, 王利明. 面向用户的支持用户掉线的联邦学习数据隐私保护方法[J]. 信息网络安全, 2021, 21(3): 64-71. |
| [14] | 芦效峰, 付淞兵. 属性基加密和区块链结合的可信数据访问控制方案[J]. 信息网络安全, 2021, 21(3): 7-8. |
| [15] | 于克辰, 郭莉, 姚萌萌. 基于空间及能量维度的黑盒对抗样本生成方法[J]. 信息网络安全, 2021, 21(3): 72-78. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 240
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 529
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||