信息网络安全 ›› 2015, Vol. 15 ›› Issue (7): 58-63.doi: 10.3969/j.issn.1671-1122.2015.07.009
基于内核日志的移动终端恶意软件检测
- 北京邮电大学计算机学院,北京 100876
Detection of Mobile Terminal Malware Based on Kernel Log
LI Jian-yi, LI Hui( ), HUANG Meng-yuan
), HUANG Meng-yuan
- School of Computer Science, Beijing University of Posts and Telecommunications, Beijing 100876, China
摘要:
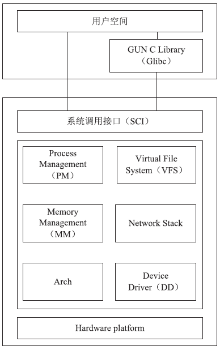
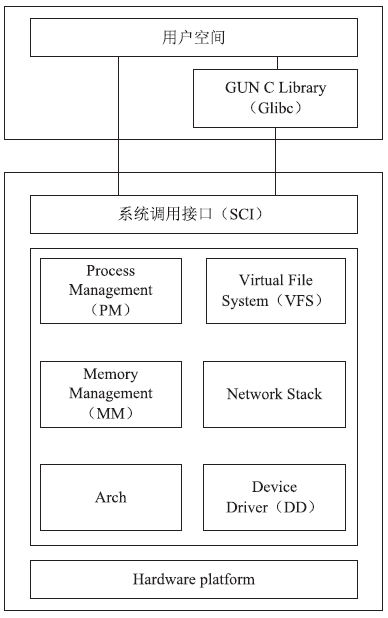
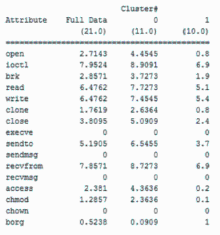
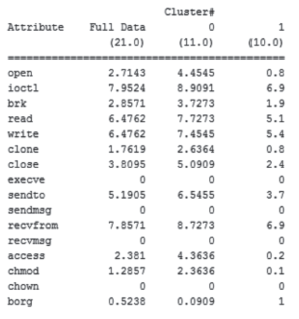
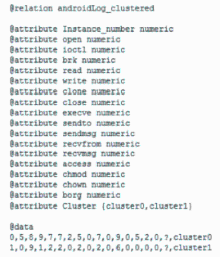
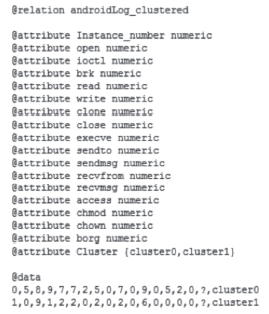
随着移动终端的智能化,移动终端上存储了大量个人隐私信息,由于移动终端上日益增多的恶意应用以及对恶意应用缺乏有效的检测机制,导致个人隐私信息的泄露,造成个人财产、名誉的损害。为防止这种危害的发生,文章提出了基于系统内核调用日志信息来识别应用行为的方法。首先下载恶意应用与良性应用,运行并收集它们的系统内核调用日志信息,统计出系统调用的频数信息作为原始数据;然后将原始数据进行规格化处理,生成可供分析的输入数据并生成输入向量;最后使用K-Means聚类算法对输入向量进行聚类处理,生成两个聚类簇,分别为恶意与良性应用的聚类簇,再将一些未知应用类型的内核调用信息作为验证数据生成输入向量,判断出该应用属于哪个聚类簇,便可知道该应用是否存在恶意行为。文章通过机器学习工具WEKA对提出的方法进行实验,实验结果证明该方法能有效地区分恶意应用与良性应用。
中图分类号: