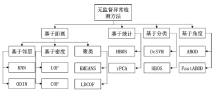
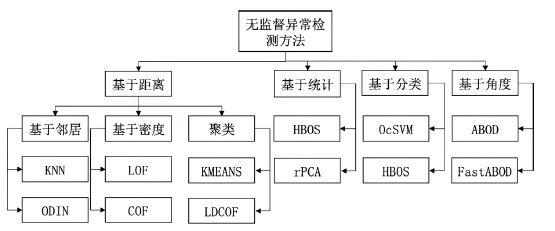
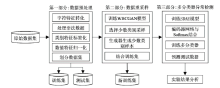
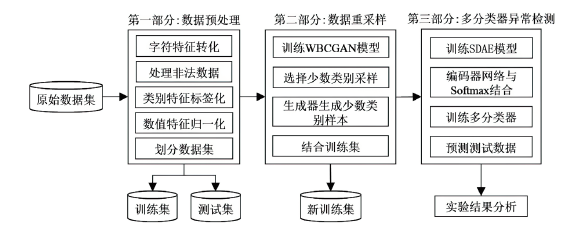
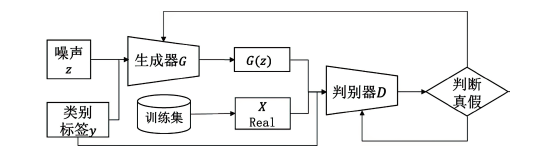
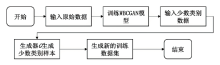
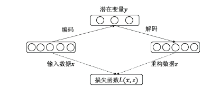
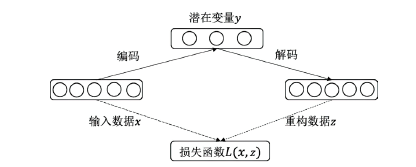
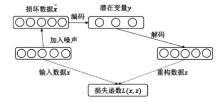
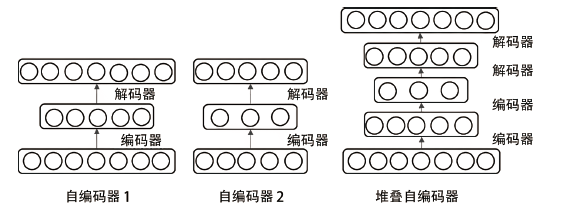
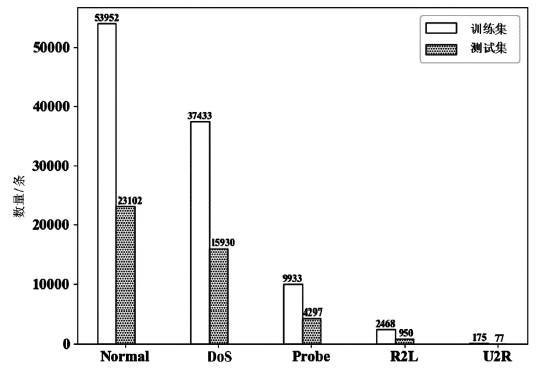
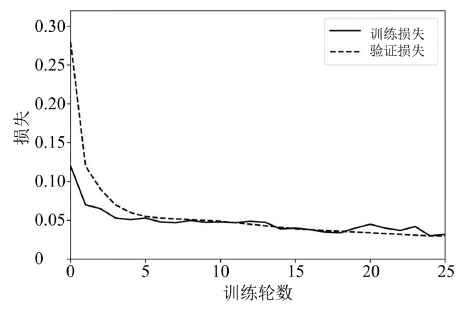
Netinfo Security ›› 2022, Vol. 22 ›› Issue (12): 7-15.doi: 10.3969/j.issn.1671-1122.2022.12.002
Previous Articles Next Articles
Anomaly Detection Model Based on Generative Adversarial Network and Autoencoder
GUO Sensen, WANG Tongli, MU Dejun( )
)
- Research & Development Institute of Northwestern Polytechnical University in Shenzhen, Shenzhen 518057, China
-
Received:2022-07-05Online:2022-12-10Published:2022-12-30 -
Contact:MU Dejun E-mail:mudejun@nwpu.edu.cn
CLC Number:
Cite this article
GUO Sensen, WANG Tongli, MU Dejun. Anomaly Detection Model Based on Generative Adversarial Network and Autoencoder[J]. Netinfo Security, 2022, 22(12): 7-15.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.12.002
| [1] | China Internet Network Information Center. Statistical Report on Internet Development in China[EB/OL]. (2021-09-15) [2022-06-20]. http://www.cnnic.cn/n4/2022/0401/c88-1132.html. |
| [2] | National Internet Emergency Center. Internet Security Threat Report[EB/OL]. (2022-01-08) [2022-06-20]. https://www.cert.org.cn/publish/main/45/2022/20220118143459813267244/20220118143459813267244_.html. |
| [3] |
KHRAISAT A, GONDAL I, VAMPLEW P, et al. Survey of Intrusion Detection Systems: Techniques, Datasets and Challenges[J]. Cybersecurity, 2019, 2(1): 1-22.
doi: 10.1186/s42400-018-0018-3 URL |
| [4] |
MODI C, PATEL D, BORISANIYA B, et al. A Survey of Intrusion Detection Techniques in Cloud[J]. Journal of Network and Computer Applications, 2013, 36(1): 42-57.
doi: 10.1016/j.jnca.2012.05.003 URL |
| [5] | ZHAI Diqing, LYU Qi, YANG Huairen, et al. Machine Learning Based Network Anomaly Detection and Security Threat Level Prediction[J]. Computer Knowledge and Technology, 2021, 17(34): 10-12. |
| [6] |
AMBUSAIDI M A, HE X, NANDA P, et al. Building an Intrusion Detection System Using a Filter-Based Feature Selection Algorithm[J]. IEEE Transactions on Computers, 2016, 65(10): 2986-2998.
doi: 10.1109/TC.2016.2519914 URL |
| [7] | LEI Yang. Network Anomaly Traffic Detection Algorithm Based on SVM[C]// IEEE.2017 International Conference on Robots & Intelligent System (ICRIS). New York: IEEE, 2017: 217-220. |
| [8] | GOLDSTEIN M, UCHIDA S. A Comparative Evaluation of Unsupervised Anomaly Detection Algorithms for Multivariate Data[EB/OL].(2016-04-19) [2022-06-20]. https://journals.plos.org/plosone/article?id=10.1371/journal.pone.0152173. |
| [9] | DROMARD J, ROUDIERE G, OWEZARSKI P. Online and Scalable Unsupervised Network Anomaly Detection Method[J]. IEEE Transactions on Network & Service Management, 2016, 14(1): 34-47. |
| [10] |
BIGDELI E, MOHAMMADI M, RAAHEMI B, et al. Incremental Anomaly Detection Using Two-Layer Cluster-Based Structure[J]. Information Sciences, 2018, 429: 315-331.
doi: 10.1016/j.ins.2017.11.023 URL |
| [11] | AN J, CHO S. Variational Autoencoder Based Anomaly Detection Using Reconstruction Probability[J]. Special Lecture on IE, 2015, 2(1): 1-18. |
| [12] | SHAH S, MUHURI P S, YUAN X, et al. Implementing a Network Intrusion Detection System Using Semi-Supervised Support Vector Machine and Random Forest[C]// ACM. Proceedings of the 2021 ACM Southeast Conference. New York: ACM, 2021: 180-184. |
| [13] |
ABDEL-BASSET M, HAWASH H, CHAKRABORTTY R K, et al. Semi-Supervised Spatio-Temporal Deep Learning for Intrusions Detection in IoT Networks[J]. IEEE Internet of Things Journal, 2021, 8(15): 12251-12265.
doi: 10.1109/JIOT.2021.3060878 URL |
| [14] | TAVALLAEE M, BAGHERI E, LU W, et al. A Detailed Analysis of the KDD CUP 99 Data Set[C]// IEEE. 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications. New York: IEEE, 2009: 1-6. |
| [15] | GULRAJANI I, AHMED F, ARJOVSKY M, et al. Improved Training of Wasserstein GANs[C]// NIPS.Proceedings of the 31st International Conference on Neural Information Processing Systems. New York: NIPS, 2017: 5768-5778. |
| [16] | VINCENT P, LAROCHELLE H, LAJOIE I, et al. Stacked Denoising Autoencoders: Learning Useful Representations in a Deep Network with a Local Denoising Criterion[J]. Journal of Machine Learning Research, 2010, 11(12): 3371-3408. |
| [17] | AYGUN R C, YAVUZ A G. Network Anomaly Detection with Stochastically Improved Autoencoder Based Models[C]// IEEE. 2017 IEEE 4th International Conference on Cyber Security and Cloud Computing (CSCloud). New York: IEEE, 2017: 193-198. |
| [1] | GAO Bo, CHEN Lin, YAN Yingjian. Research on Side Channel Attack Based on CNN-MGU [J]. Netinfo Security, 2022, 22(8): 55-63. |
| [2] | GU Zhaojun, LIU Tingting, GAO Bing, SUI He. Anomaly Detection of Imbalanced Data in Industrial Control System Based on GAN-Cross [J]. Netinfo Security, 2022, 22(8): 81-89. |
| [3] | ZHOU Jingyi, LI Hongjiao. False Data Injection Attack Detection Method against PMU Measurements [J]. Netinfo Security, 2022, 22(5): 75-83. |
| [4] | ZHENG Yaohao, WANG Liming, YANG Jing. A Defense Method against Adversarial Attacks Based on Neural Architecture Search [J]. Netinfo Security, 2022, 23(3): 70-77. |
| [5] | CHEN Binjie, WEI Fushan, GU Chunxiang. Blockchain Abnormal Transaction Detection with Privacy-preserving Based on KNN [J]. Netinfo Security, 2022, 23(3): 78-84. |
| [6] | XU Ruzhi, LYU Changran, LONG Yan, LIU Yuanbin. Defense Research of High-Hidden Data Attack in Industry Control System [J]. Netinfo Security, 2022, 22(12): 34-46. |
| [7] | NIU Yinuo, ZHANG Yifei, GAO Neng, MA Cunqing. Design of Log-Based Anomaly Detection System Based on Temporal and Logical Relationship [J]. Netinfo Security, 2022, 22(11): 1-6. |
| [8] | ZHANG Zhi, LI Xin, YE Naifu, HU Kaixi. CAPTCHA Security Enhancement Method Incorporating Multiple Style Migration and Adversarial Examples [J]. Netinfo Security, 2022, 22(10): 129-135. |
| [9] | LIU Shuo, ZHANG Xinglan. Intrusion Detection System Based on Dual Attention [J]. Netinfo Security, 2022, 22(1): 80-86. |
| [10] | YI Xiaoyang, ZHANG Jian. Image-based Phishing Email Detection Method and Implementation [J]. Netinfo Security, 2021, 21(9): 52-58. |
| [11] | QIN Zhongyuan, HU Ning, FANG Lanting. Network Anomaly Detection Method Based on Immune Bionic Mechanism and Graph Neural Network [J]. Netinfo Security, 2021, 21(8): 10-16. |
| [12] | ZHU Xintong, TANG Yunqi, GENG Pengzhi. Detection Algorithm of Tamper and Deepfake Image Based on Feature Fusion [J]. Netinfo Security, 2021, 21(8): 70-81. |
| [13] | XU Hongping, MA Zewen, YI Hang, ZHANG Longfei. Network Traffic Anomaly Detection Technology Based on Convolutional Recurrent Neural Network [J]. Netinfo Security, 2021, 21(7): 54-62. |
| [14] | LI Jiawei, WU Kehe, ZHANG Bo. Research on Anomaly Detection of Power Industrial Control System Based on Gaussian Mixture Clustering [J]. Netinfo Security, 2021, 21(3): 53-63. |
| [15] | LU Honglin, WANG Liming. User-oriented Data Privacy Preserving Method for Federated Learning that Supports User Disconnection [J]. Netinfo Security, 2021, 21(3): 64-71. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||