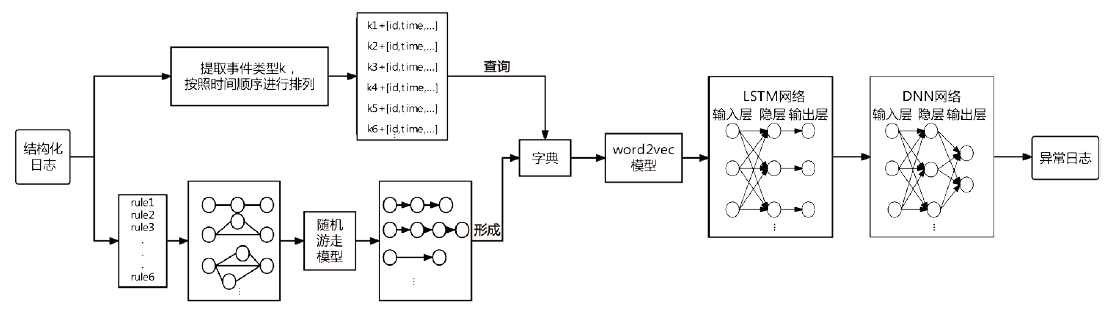
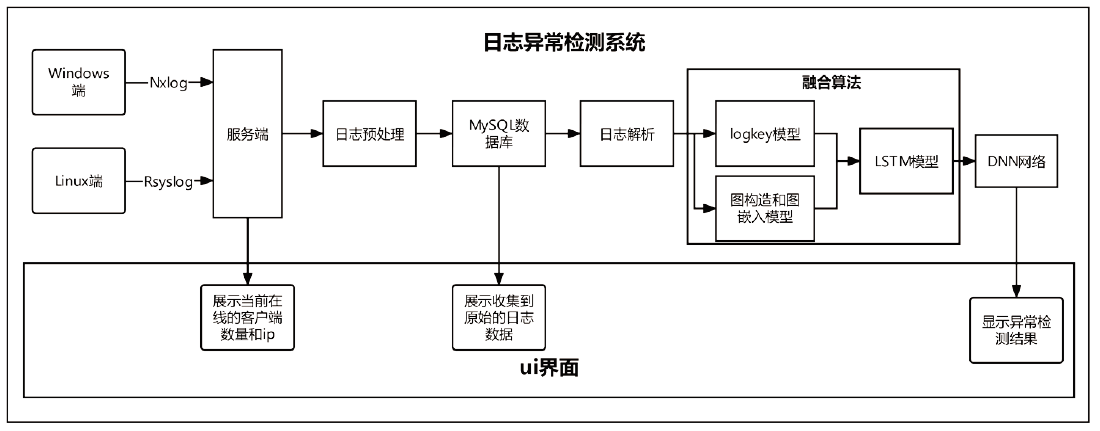
| [1] |
KONTAKI M, GOUNARIS A, Papadopoulos A N, et al. Efficient and Flexible Algorithms for Monitoring Distance-Based Outliers Over Data Streams[J]. Information Systems, 2016, 55(7): 37-53.
doi: 10.1016/j.is.2015.07.006
URL
|
| [2] |
DUAN Xiaoyu, YING Shi, YUAN Wanli, et al. A Generative Adversarial Networks for Log Anomaly Detection[J]. Computer Systems Science and Engineering, 2021(1): 135-148.
|
| [3] |
WANG Bingming, YING Shi, YANG Zhe. A Log-Based Anomaly Detection Method with Efficient Neighbor Searching and Automatic K Neighbor Selection[J]. Scientific Programming, 2020(6): 1-17.
|
| [4] |
ZHU Jieming, HE Shilin, LIU Jinyang, et al. Tools and Benchmarks for Automated Log Parsing[C]// ACM. 41st International Conference on Software Engineering:Software Engineering in Practice (ICSE-SEIP). New York:ACM, 2019: 121-130.
|
| [5] |
DU Min, LI Feifei, ZHENG Guineng, et al. DeepLog: Anomaly Detection and Diagnosis from System Logs through Deep Learning[C]// ACM. Sigsac Conference on Computer & Communications Security. New York: ACM, 2017: 1285-1298.
|
| [6] |
ESWARAN D, FALOUTSOS C, GUHA S, et al. SpotLight: Detecting Anomalies in Streaming Graphs[C]// ACM. the 24th ACM SIGKDD International Conference. New York: ACM, 2018: 1378-1386.
|
| [7] |
LIU Fucheng, WEN Yu, ZHANG Dongxue, et al. Log2vec: A Heterogeneous Graph Embedding Based Approach for Detecting Cyber Threats within Enterprise[C]// ACM. the 2019 ACM SIGSAC Conference. New York: ACM, 2019: 1777-1794.
|
| [8] |
WANG Jin, TANG Yangning, HE Shiming, et al. LogEvent2vec: LogEvent-to-Vector Based Anomaly Detection for Large-Scale Logs in Internet of Things[J]. Sensors (Basel, Switzerland), 2020, 20(9): 2451-2470.
doi: 10.3390/s20092451
URL
|
| [9] |
YANG Lin, CHEN Junjie, WANG Zan, et al. Semi-Supervised Log-Based Anomaly Detection via Probabilistic Label Estimation[C]// ACM. 43rd International Conference on Software Engineering (ICSE). New York: ACM, 2021: 1448-1460.
|
| [10] |
Wang Jin, ZHAO Changqing, HE Shiming, et al. LogUAD: Log Unsupervised Anomaly Detection Based on Word2Vec[J]. Computer Systems Science and Engineering, 2022, 41(3): 1207-1222.
doi: 10.32604/csse.2022.022365
URL
|
| [11] |
GERHARDS R, GmbH A. RFC 5424 The Syslog Protocol[EB/OL]. (2009-10-11)[2022-03-27]. .
|
| [12] |
LIN Fengxu, LIU Jinyang, ZHENG Jian, et al. The Usage of Rsyslog in Log Collection[J]. Cyberspace Security, 2019(4): 18-22.
|
| [13] |
MESSAOUDI S, PANICHELLA A, BIANCULLI D, et al. A Search-Based Approach for Accurate Identification of Log Message Formats[C]// ACM. 26th International Conference on Program Comprehension (ICPC). New York:ACM, 2018: 167-177.
|
| [14] |
HE Pinjia, ZHU Jieming, ZHENG Zibin, et al. Drain: An Online Log Parsing Approach with Fixed Depth Tree[C]// IEEE. 2017 IEEE International Conference on Web Services (ICWS). New York:IEEE, 2017: 33-40.
|
| [15] |
MA Daoying, ZHANG Aidong. An Adaptive Density-Based Clustering Algorithm for Spatial Database with Noise[C]// IEEE. International Conference on Data Mining. New York: IEEE, 2004: 467-470.
|
 ), MA Cunqing1
), MA Cunqing1