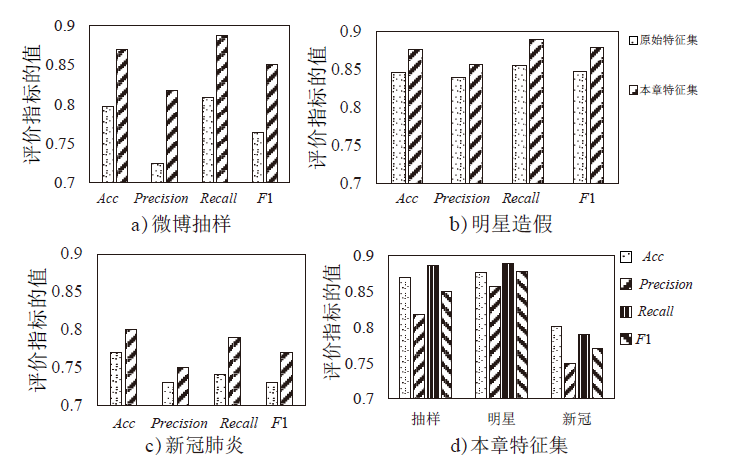
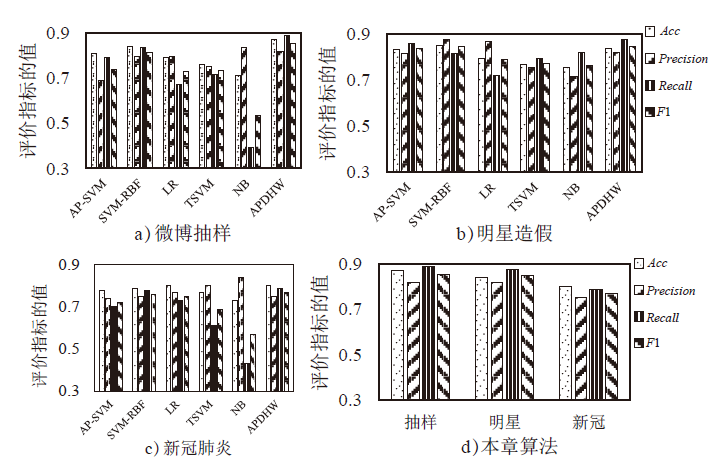
Netinfo Security ›› 2022, Vol. 22 ›› Issue (3): 85-96.doi: 10.3969/j.issn.1671-1122.2022.03.010
Previous Articles Next Articles
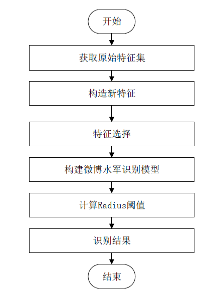
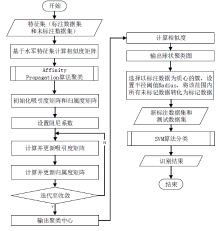
Internet Hirelings Semi-supervised Detection of Weibo Based on Affinity Propagation Algorithm
LIN Yijun1, WU Yu1( ), LI Hongbo2
), LI Hongbo2
- 1. School of Cyber Security and Information Law, Chongqing University of Posts and Telecommunications, Chongqing 400065, China
2. School of Innovation and Enterpreneurship, Chongqing University of Posts and Telecommunications, Chongqing 400065, China
-
Received:2021-08-18Online:2022-03-10Published:2022-03-28 -
Contact:WU Yu E-mail:Wuyu@cqupt.edu.cn
CLC Number:
Cite this article
LIN Yijun, WU Yu, LI Hongbo. Internet Hirelings Semi-supervised Detection of Weibo Based on Affinity Propagation Algorithm[J]. Netinfo Security, 2022, 22(3): 85-96.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.03.010
| 序号 | 特征描述 | p值 | 序号 | 特征描述 | p值 |
|---|---|---|---|---|---|
| 1 | 是否VIP | 1.04E-20 | 12 | 平均被转发数 | 2.36E-03 |
| 2 | 用户活跃度 | 4.28E-17 | 13 | 关注粉丝比 | 5.47E-03 |
| 3 | 平均URL数 | 1.66E-13 | 14 | 平均被点赞数 | 6.97E-03 |
| 4 | 微博内容合理度 | 1.16E-08 | 15 | 是否认证 | 1.24E-02 |
| 5 | 平均被评论数 | 1.75E-07 | 16 | 粉丝数 | 4.93E-02 |
| 6 | 用户身份可靠度 | 2.17E-07 | 17 | 关注数 | 9.37E-02 |
| 7 | 用户行为合理度 | 2.39E-06 | 18 | 性别 | 1.20E-01 |
| 8 | 平均话题数 | 1.46E-05 | 19 | 用户名长度 | 3.58E-01 |
| 9 | 平均提及数 | 2.89E-05 | 20 | 平均图片数 | 3.79E-01 |
| 10 | 用户等级数 | 3.47E-05 | 21 | 微博数 | 4.17E-01 |
| 11 | 微博相似度 | 2.32E-04 | 22 | 平均微博数 | 5.33E-01 |
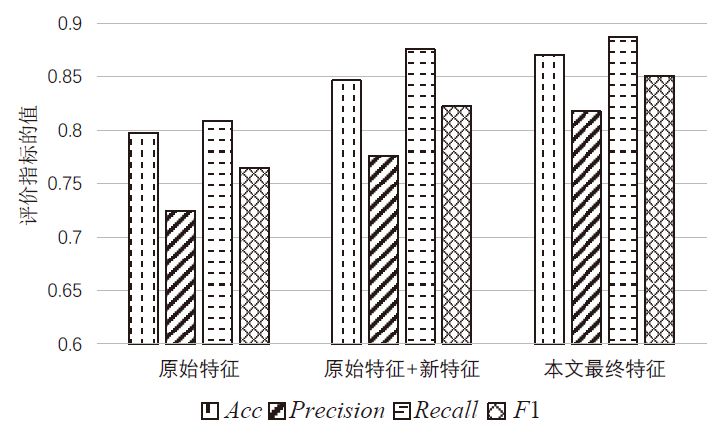
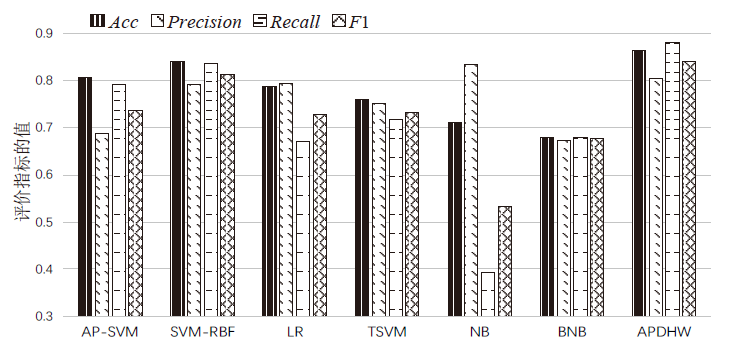
| 模型 | 类别 | 准确率 | 精确度 | 召回率 | F1 |
|---|---|---|---|---|---|
| AP-SVM | 0 | 0.807 | 0.884 | 0.815 | 0.848 |
| 1 | 0.688 | 0.791 | 0.736 | ||
| SVM-RBF | 0 | 0.847 | 0.907 | 0.827 | 0.865 |
| 1 | 0.776 | 0.876 | 0.823 | ||
| APDHW | 0 | 0.864 | 0.911 | 0.853 | 0.881 |
| 1 | 0.805 | 0.881 | 0.841 | ||
| LR | 0 | 0.788 | 0.785 | 0.873 | 0.827 |
| 1 | 0.793 | 0.671 | 0.727 | ||
| TSVM | 0 | 0.760 | 0.767 | 0.796 | 0.781 |
| 1 | 0.750 | 0.717 | 0.733 | ||
| NB | 0 | 0.710 | 0.680 | 0.943 | 0.790 |
| 1 | 0.833 | 0.392 | 0.533 | ||
| BNB | 0 | 0.679 | 0.685 | 0.678 | 0.682 |
| 1 | 0.672 | 0.679 | 0.676 |
| [1] | MO Qian, YANG Ke. Overview of Web Spammer Detection[J]. Journal of Software, 2014, 25(7):1505-1526. |
| 莫倩, 杨珂. 网络水军识别研究[J]. 软件学报, 2014, 25(7):1505-1526. | |
| [2] | XIE Zhonghong, ZHANG Ying, ZHANG Lin. The Recognition of Public Opinion Viruses of Micro-blog Based on Logistic Regression[J]. Microcomputer & Its Applications, 2017, 36(16):67-69. |
| [3] | ZHANG Yanmei, HUANG Yingying, GAN Shijie, et al. Weibo Spammers’ Identification Algorithm Based on Bayesian Model[J]. Journal on Communications, 2017, 38(1):44-53. |
| 张艳梅, 黄莹莹, 甘世杰, 等. 基于贝叶斯模型的微博网络水军识别算法研究[J]. 通信学报, 2017, 38(1):44-53. | |
| [4] | CHEN Kan, CHEN Liang, ZHU Peidong, et al. Interaction Based on Method for Spam Detection in Online Social Networks[J]. Journal on Communications, 2015, 36(7):120-127. |
| 陈侃, 陈亮, 朱培栋, 等. 基于交互行为的在线社会网络水军检测方法[J]. 通信学报, 2015, 36(7):120-127. | |
| [5] | GAO Hongyu, HU Jun, HUANG Tuo, et al. Security Issues in Online Social Networks[J]. IEEE Internet Computing, 2011, 15(4):56-63. |
| [6] | QU Qiang, YU Hongtao, HUANG Ruiyang. Spammer Detection Technology of Social Network Based on Graph Convolution Network[J]. Chinese Journal of Network and Information Security, 2018, 4(5):39-46. |
| [7] | LI Yan, DENG Shengchun, LIN Jian. Dynamic Behavior Analysis and Online Detection of Spammer User in Social Network[J]. Computer Engineering, 2019, 45(8):287-295. |
| [8] | WANG Lei, REN Hang, WANG Zhiyi. Microblog Spammer Identification Method Based on Cost-sensitive Learning in Latent Space[J]. Computer Engineering, 2018, 44(9):159-163, 170. |
| [9] | LIU Shuwen, XU Yang, WANG Binglu, et al. Water Army Detection of Weibo Using User Representation Learning[J]. Journal of Intelligence, 2018, 37(7):95-100, 87. |
| 刘姝雯, 徐扬, 王冰璐, 等. 基于用户表示学习的微博水军识别研究[J]. 情报杂志, 2018, 37(7):95-100, 87. | |
| [10] | YANG Lei, CAO Cuiling, SUN Jianguo. Study on an Improved Naive Bayes Algorithm in Spam Filtering[J]. Jornal on Communications, 2017, 38(4):140-148. |
| [11] |
WU Qi. Adaptive Affinity Propagation Method Based on Improved Cuckoo Search[J]. Knowledge-based Systems, 2017, 111(C):27-35.
doi: 10.1016/j.knosys.2016.07.039 URL |
| [12] |
FOTI D, HAJCAK G, DIEN J. Differentiating Neural Responses to Emotional Pictures: Evidence from Temporal-spatial PCA[J]. Psychophysiology, 2010, 46(3):521-530.
doi: 10.1111/psyp.2009.46.issue-3 URL |
| [13] |
WEN Li, ZHENG Xu, DONG Xu, et al. Domain Generalization and Adaptation Using Low Rank Exemplar SVMs[J]. IEEE Trans Pattern Anal Mach Intell, 2018, 40(5):1114-1127.
doi: 10.1109/TPAMI.2017.2704624 URL |
| [14] | WANG Shuqi, WANG Weiyang. Weibo Naval Account Identification Based on Support Vector Machine[J]. Modern Computer, 2018(9):27-31. |
| [15] | HU Sicai, SUN Jieping, JU Shenggen, et al. Chinese Emotion Feature Selection Method Based on the Extended Emotion Dictionary and the Chi-square Model[J]. Journal of Sichuan University (Nature Science Edition), 2019, 56(1):37-44. |
| 胡思才, 孙界平, 琚生根, 等. 基于扩展的情感词典和卡方模型的中文情感特征选择方法[J]. 四川大学学报(自然科学版), 2019, 56(1):37-44. | |
| [16] | ZHENG Xianghan, ZENG Zhipeng, CHEN Zheyi, et al. Detecting Spammers on Social Networks[J]. Neurocomputing, 2015, 42(1):27-34. |
| [17] | CAO Shoufu. Research on Naïve Bayes Classification Method of Social Media Big Data[D]. Changsha: Hunan University, 2016. |
| 曹守富. 社交媒体大数据的朴素贝叶斯分类方法研究[D]. 长沙:湖南大学, 2016. | |
| [18] |
CHEDDAD A. Structure Preserving Binary Image Morphing Using Delaunay Triangulation[J]. Pattern Recognition Letters, 2016, 85(1):8-14.
doi: 10.1016/j.patrec.2016.11.010 URL |
| [1] | PENG Cheng, FAN Wei, ZHU Dali, YANG Fen. Research on Man-in-the-Middle Attack Detection in LTE Access Network Based on Weighted Bayesian Classifier [J]. Netinfo Security, 2023, 23(2): 1-10. |
| [2] | QIN Zhongyuan, GE Zhenwei, PAN Jingwei, CHEN Liquan. Research on Integrity Measurement Scheme Based on Virtual Trusted Platform Module [J]. Netinfo Security, 2023, 23(2): 11-18. |
| [3] | ZHAO Jia, GAO Ta, ZHANG Jiancheng. Method of Local Differential Privacy Method for High-Dimensional Data Based on Improved Bayesian Network [J]. Netinfo Security, 2023, 23(2): 19-25. |
| [4] | LI Yuancheng, LUO Hao, WANG Qingle, LI Jianbin. An Advanced Persistent Threat Model of New Power System Based on ATT&CK [J]. Netinfo Security, 2023, 23(2): 26-34. |
| [5] | WANG Yan, ZHANG Kunpeng, JI Zhicheng. Intelligent Optimization and Decision Method of Cloud Resources Based on Trusted Service [J]. Netinfo Security, 2023, 23(2): 35-44. |
| [6] | LIU Jue, CHENG Kaixin, YANG Weiwei. Research on Physical Layer Security Technologies for Smart Eavesdropper Attack [J]. Netinfo Security, 2023, 23(2): 45-53. |
| [7] | XU Zhanyang, CHENG Luofei, CHENG Jianchun, XU Xiaolong. A Scheme of Optimizing Deep Learning Model Using Bi-ADMM [J]. Netinfo Security, 2023, 23(2): 54-63. |
| [8] | CHEN Depeng, LIU Xiao, CUI Jie, ZHONG Hong. Research on Membership Inference Attack Method Based on Double Threshold Function [J]. Netinfo Security, 2023, 23(2): 64-75. |
| [9] | XIA Yihang, ZHANG Zhilong, WANG Muzi, CHEN Libo. Dependency-Based Vulnerability Detection Method in Container Supply Chain [J]. Netinfo Security, 2023, 23(2): 76-84. |
| [10] | HU Zhijie, CHEN Xingshu, YUAN Daohua, ZHENG Tao. Static Detection Method of Android Adware Based on Improved Random Forest Algorithm [J]. Netinfo Security, 2023, 23(2): 85-95. |
| [11] | WANG Ming, XING Yongheng, WANG Feng. Unsupervised Matrix Factorization Based Trigger Action Programming Rules Recommendation [J]. Netinfo Security, 2023, 23(2): 96-103. |
| [12] | LI Jiyu, FU Zhangjie, ZHANG Yubin. An Image Information Hiding Algorithm Based on Cross-Domain Adversarial Adaptation [J]. Netinfo Security, 2023, 23(1): 93-102. |
| [13] | LIU Qin, GUO Kaiyuan, TU Hang. Task Data Migration Solution Based on SM2 and SM4 Under TEE [J]. Netinfo Security, 2023, 23(1): 9-17. |
| [14] | FENG Yiting, MA Zhaofeng, XU Danheng, DUAN Pengfei. Evaluation Method for Cross-Chain Security Strength Access [J]. Netinfo Security, 2023, 23(1): 84-92. |
| [15] | SHEN Chuanxin, WANG Yongjie, XIONG Xinli. DNS Covert Channel Detection Based on Graph Attention Network [J]. Netinfo Security, 2023, 23(1): 73-83. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||