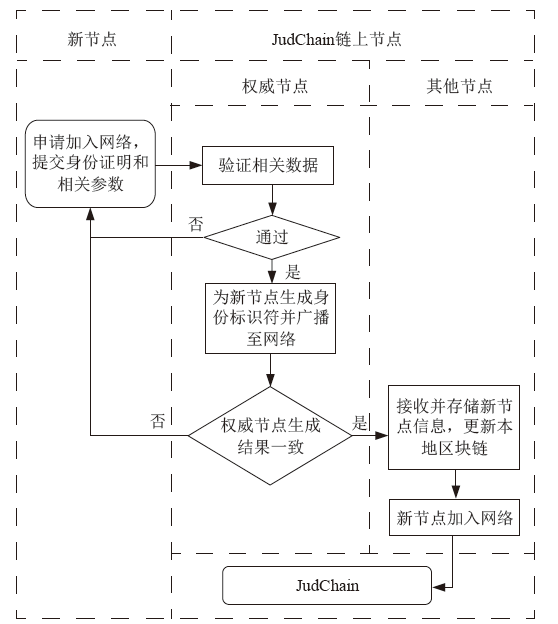
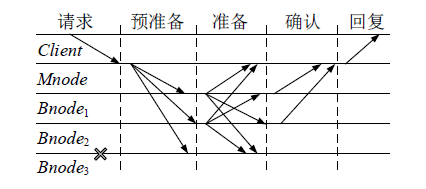
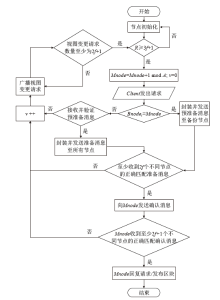
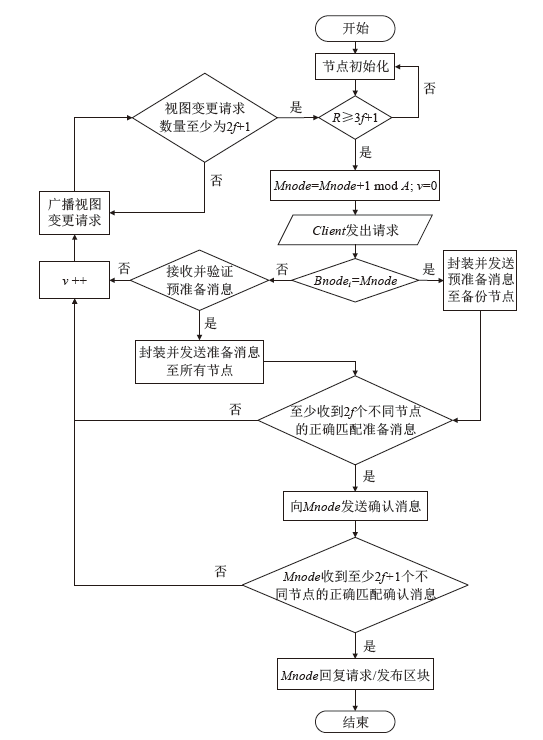
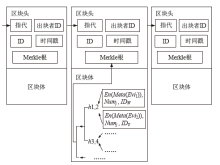
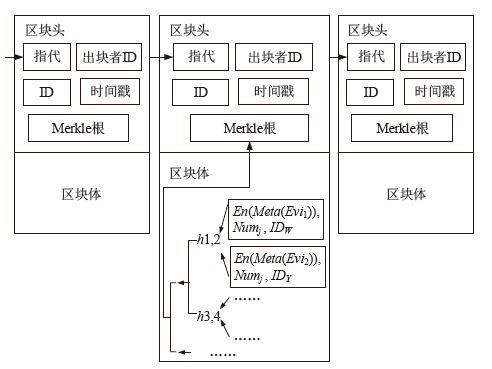
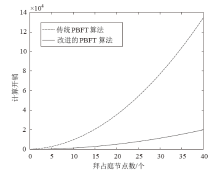
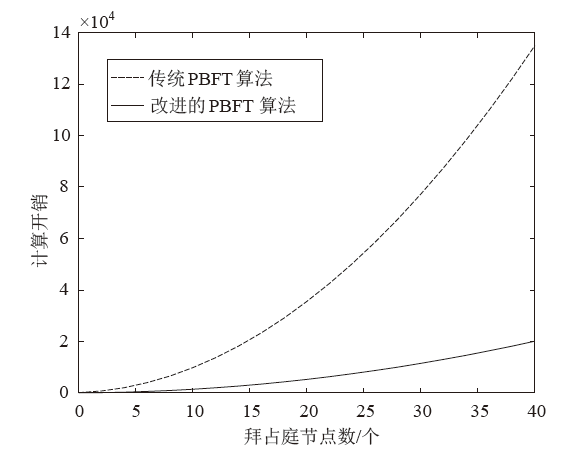
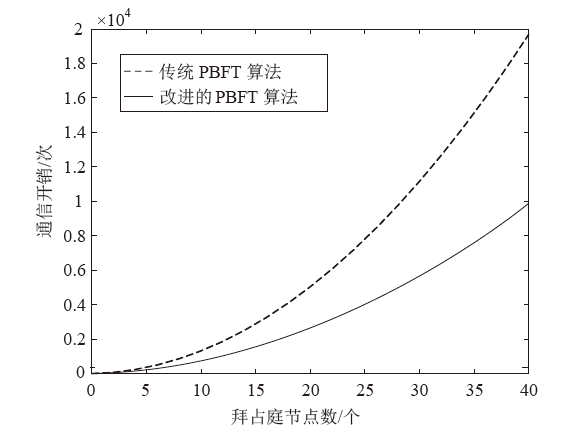
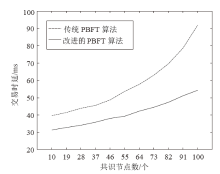
Netinfo Security ›› 2022, Vol. 22 ›› Issue (2): 21-31.doi: 10.3969/j.issn.1671-1122.2022.02.003
Previous Articles Next Articles
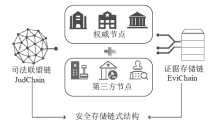
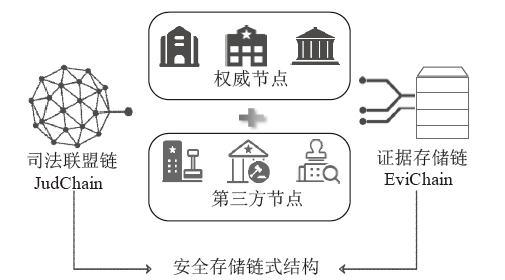
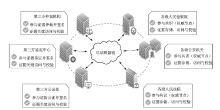
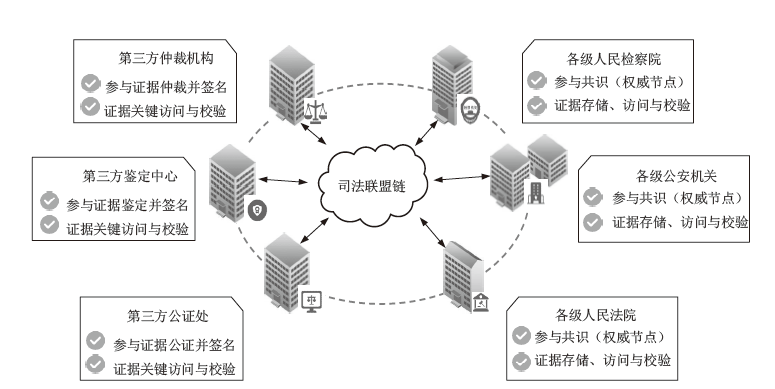
Blockchain-based Mechanism for Judicial Data Management and Electronic Evidence Storage
WANG Jian1( ), ZHANG Yunjia1,2, LIU Jiqiang1, CHEN Zhihao3
), ZHANG Yunjia1,2, LIU Jiqiang1, CHEN Zhihao3
- 1. Beijing Key Laboratory of Security and Privacy in Intelligent Transportation, Beijing Jiaotong University, Beijing 100044, China
2. Information Technology Institute, China Rail Way TaiYuan Group Co., Ltd., Taiyuan 030013, China
3. Beijing Institute of Computer Technology and Applications, Beijing 100854, China
-
Received:2021-09-09Online:2022-02-10Published:2022-02-16 -
Contact:WANG Jian E-mail:wangjian@bjtu.edu.cn
CLC Number:
Cite this article
WANG Jian, ZHANG Yunjia, LIU Jiqiang, CHEN Zhihao. Blockchain-based Mechanism for Judicial Data Management and Electronic Evidence Storage[J]. Netinfo Security, 2022, 22(2): 21-31.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.02.003
| [1] | VOLONINO L. Computer Forensics and Electronic Evidence[EB/OL]. https://aisel.aisnet.org/amcis2003/426/, 2021-02-22. |
| [2] |
LOSAVIO M, ADAMS J, ROGERS M. Gap Analysis: Judicial Experience and Perception of Electronic Evidence[J]. Journal of Digital Forensic Practice, 2006, 1(1):13-17.
doi: 10.1080/15567280500541462 URL |
| [3] |
SIN J M, SON H R. Dealing with the Problem of Collection and Analysis of Electronic Evidence[J]. International Journal of Electronic Security and Digital Forensics, 2019, 11(3):363-377.
doi: 10.1504/IJESDF.2019.100497 URL |
| [4] |
INSA F. The Admissibility of Electronic Evidence in Court(A.E.E.C.): Fighting against High-tech Crime-results of a European Study[J]. Journal of Digital Forensic Practice, 2007, 1(4):285-289.
doi: 10.1080/15567280701418049 URL |
| [5] | Satoshi Nakamoto. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. https://bitcoin.org/bitcoin.pdf, 2021-05-03. |
| [6] | KOSBA A, MILLER A, SHI E, et al. Hawk: The Blockchain Model of Cryptography and Privacy-preserving Smart Contracts[C]//IEEE. 2016 IEEE Symposium on Security and Privacy(SP), May 22-26, 2016, San Jose, CA, USA. New Jersey: IEEE, 2016: 839-858. |
| [7] | KARAME G. On the Security and Scalability of Bitcoin’s Blockchain[C]//ACM. 2016 ACM SIGSAC Conference on Computer and Communications Security, October 24-28, 2016, Vienna, Austria. New York: ACM, 2016: 1861-1862. |
| [8] | MACIÁ-FERNÁNDEZ G, GÓMEZ-HERNÁNDEZ J A, ROBLES M, et al. Blockchain-based Forensic System for Collection and Preservation of Network Service Evidences-ScienceDirect[EB/OL]. https://doi.org/10.1016/j.diin.2019.01.023, 2021-02-22. |
| [9] | XIONG Yu, DU Jiang. Electronic Evidence Preservation Model Based on Blockchain[C]//ACM. 3rd International Conference on Cryptography, Security and Privacy, January 19-21, 2019, Kuala Lumpur, Malaysia. New York: ACM, 2019: 1-5. |
| [10] |
WEILBACH W T, MOTARA Y M. Applying Distributed Ledger Technology to Digital Evidence Integrity[J]. Saiee Africa Research Journal, 2019, 110(2):77-93.
doi: 10.23919/SAIEE.8475037 URL |
| [11] | WANG Jinmiao, XIE Yongheng, WANG Guowei, et al. A Method of Privacy Preserving and Access Control in Blockchain Based on Attribute-based Encryption[J]. Netinfo Security, 2020, 20(9):47-51. |
| 汪金苗, 谢永恒, 王国威, 等. 基于属性基加密的区块链隐私保护与访问控制方法[J]. 信息网络安全, 2020, 20(9):47-51. | |
| [12] | BONOMI S, CASINI M, CICCOTELLI C. B-CoC: A Blockchain-based Chain of Custody for Evidences Management in Digital Forensics[EB/OL]. https://arxiv.org/abs/1807.10359, 2018-07-26. |
| [13] | LONE A H, MIR R N. Forensic-chain: Blockchain Based Digital Forensics Chain of Custody with PoC in Hyperledger Composer[EB/OL]. https://doi.org/10.1016/j.diin.2019.01.002, 2021-03-11. |
| [14] | TIAN Zhihong, LI Mohan, QIU Meikang, et al. Block-DEF: A Secure Digital Evidence Framework Using Blockchain[EB/OL]. https://doi.org/10.1016/j.ins.2019.04.011, 2021-03-12. |
| [15] | WANG Mingming, WU Qianhong, QIN Bo, et al. Lightweight and Manageable Digital Evidence Preservation System on Bitcoin[J]. Journal of Computer Science & Technology, 2018, 33(3):568-586. |
| [16] | POURVAHAB M, EKBATANIFARD G. Digital Forensics Architecture for Evidence Collection and Provenance Preservation in IaaS Cloud Environment Using SDN and Blockchain Technology[EB/OL]. https://ieeexplore.ieee.org/document/8865056, 2019-10-11. |
| [17] | ALI O, JARADAT A, KULAKLI A, et al. A Comparative Study: Blockchain Technology Utilization Benefits, Challenges and Functionalities[EB/OL]. https://ieeexplore.ieee.org/document/9317729, 2021-01-08. |
| [18] | ZHANG Xiaoshuai, POSLAD S, MA Zixiang. Block-based Access Control for Blockchain-based Electronic Medical Records(EMRs) Query in eHealth[C]//IEEE. 2018 IEEE Global Communications Conference, December 9-13, 2018, Abu Dhabi, United Arab Emirates. New Jersey: IEEE, 2018: 1-7. |
| [19] | KIM M G, LEE A R, KWON H J, et al. Sharing Medical Questionnaries Based on Blockchain[C]//IEEE. 2018 IEEE International Conference on Bioinformatics and Biomedicine(BIBM), December 3-6, 2018, Madrid, Spain. New Jersey: IEEE, 2018: 2767-2769. |
| [20] | ALSHARIF A, NABIL M. A Blockchain-based Medical Data Marketplace with Trustless Fair Exchange and Access Control[C]//IEEE. IEEE Global Communications Conference(GLOBECOM 2020), December 7-11, 2020, Taiwan, China. New Jersey: IEEE, 2020: 1-6. |
| [21] | YANG Xiaodong, LI Ting, PEI Xizhen, et al. Medical Data Sharing Scheme Based on Attribute Cryptosystem and Blockchain Technology[EB/OL]. https://ieeexplore.ieee.org/document/9016179, 2020-02-27. |
| [22] | ZHU Yan, QIN Yao, ZHOU Zhiyuan, et al. Digital Asset Management with Distributed Permission over Blockchain and Attribute-based Access Control[C]//IEEE. IEEE International Conference on Services Computing(SCC), July 2-7, 2018, San Francisco, CA, USA. New Jersey: IEEE, 2018: 193-200. |
| [23] | GOURU N, VADLAMANI N L. DistProv-data Provenance in Distributed Cloud for Secure Transfer of Digital Assets with Ethereum Blockchain Using ZKP[J]. International Journal of Open Source Software and Processes, 2019, 10(3):1-18. |
| [24] |
LIN Chao, HE Debiao, KUMAR N, et al. HomeChain: A Blockchain-based Secure Mutual Authentication System for Smart Homes[J]. IEEE Internet of Things Journal, 2020, 7(2):818-829.
doi: 10.1109/JIoT.6488907 URL |
| [25] | DORRI A, KANHERE S S, JURDAK R, et al. Blockchain for IoT Security and Privacy: The Case Study of a Smart Home[C]//IEEE. IEEE Annual Conference on Pervasive Computing and Communications Workshops(PerCom), March 13-17, 2017, Kona, Big Island, HI, USA. New Jersey: IEEE, 2017: 618-623. |
| [26] | ALPHAND O, AMORETTI M, CLAEYS T, et al. IoTChain: A Blockchain Security Architecture for the Internet of Things[C]//IEEE. 2018 IEEE Wireless Communications and Networking Conference(WCNC), April 15-18, 2018, Barcelona, Spain. New Jersey: IEEE, 2018: 1-6. |
| [1] | LIU Feng, YANG Chengyi, YU Xincheng, QI Jiayin. Spectral Graph Convolutional Neural Network for Decentralized Dual Differential Privacy [J]. Netinfo Security, 2022, 22(2): 39-46. |
| [2] | HOU Yutong, MA Zhaofeng, LUO Shoushan. Research and Implementation of Data Security Sharing and Controlled Distribution Technology Based on Blockchain [J]. Netinfo Security, 2022, 22(2): 55-63. |
| [3] | SUN Li. Research and Application of Information Protection Mechanism for Online Education Resource Alliance [J]. Netinfo Security, 2021, 21(9): 32-39. |
| [4] | CHEN Kaijie, XIONG Yan, HUANG Wenchao, WU Jianshuang. A Formal Analysis Method of PoS Consensus Protocol Based on Byzantine Fault Tolerance [J]. Netinfo Security, 2021, 21(8): 35-42. |
| [5] | REN Tao, JIN Ruochen, LUO Yongmei. Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning [J]. Netinfo Security, 2021, 21(7): 27-34. |
| [6] | WU Yi, ZHONG Sheng. Research on Raft Consensus Algorithm for Blockchain [J]. Netinfo Security, 2021, 21(6): 36-44. |
| [7] | LI Peng, ZHENG Tiantian, XU He, ZHU Feng. RFID Security Authentication Protocol Based on Blockchain Technology [J]. Netinfo Security, 2021, 21(5): 1-11. |
| [8] | ZHOU Yousheng, ZHONG Tianqi. Blockchain-based Fair Exchange Scheme [J]. Netinfo Security, 2021, 21(5): 19-30. |
| [9] | LIU Zi’ang, HUANG Yuanyuan, MA Jiali, ZHOU Rui. Design and Implementation of Monitoring Platform for Medical Data Abuse Based on Blockchain [J]. Netinfo Security, 2021, 21(5): 58-66. |
| [10] | LU Xiaofeng, FU Songbing. A Trusted Data Access Control Scheme Combining Attribute-based Encryption and Blockchain [J]. Netinfo Security, 2021, 21(3): 7-8. |
| [11] | ZHANG Yinghui, ZHU Tian, ZHENG Dong. Multi-keyword Fine-grained Searchable Encryption Scheme Based on Blockchain [J]. Netinfo Security, 2021, 21(2): 34-44. |
| [12] | WANG Jian, YU Hang, HAN Zhen, HAN Lei. Access Control Methods of Data Sharing in Cloud Storage Based on Smart Contract [J]. Netinfo Security, 2021, 21(11): 40-47. |
| [13] | LI Kunchang, SHI Runhua, LI En. Survey on Data Aggregation and Privacy Protection of User Query in Smart Grid [J]. Netinfo Security, 2021, 21(11): 65-74. |
| [14] | YU Kechen, GUO Li, YAO Mengmeng. Design of Blockchain-based High-value Data Sharing System [J]. Netinfo Security, 2021, 21(11): 75-84. |
| [15] | LIU Feng, YANG Jie, QI Jiayin. Two-Party ECDSA for Blockchain Based on Hash Proof Systems [J]. Netinfo Security, 2021, 21(1): 19-26. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||