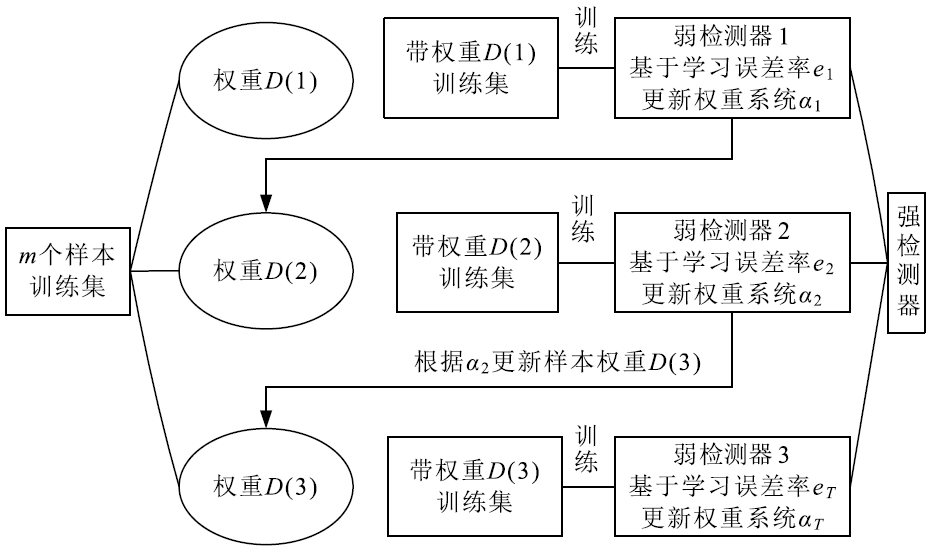
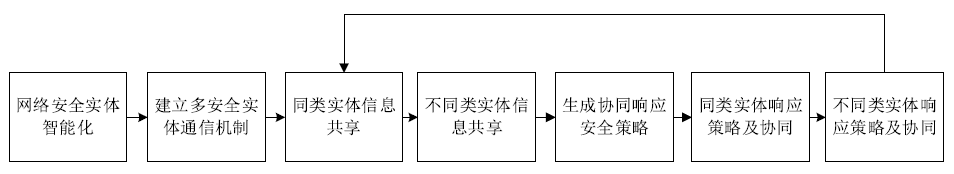
Netinfo Security ›› 2020, Vol. 20 ›› Issue (9): 52-56.doi: 10.3969/j.issn.1671-1122.2020.09.011
Previous Articles Next Articles
Research on Collaborative Defense Technology of Network Security Based on Swarm Intelligence
ZENG Yingming( ), WANG Bin, GUO Min
), WANG Bin, GUO Min
- Beijing Institute of Computer Technology and Applications, Beijing 100854, China
-
Received:2020-07-16Online:2020-09-10Published:2020-10-15 -
Contact:Yingming ZENG E-mail:yingmingblue@163.com
CLC Number:
Cite this article
ZENG Yingming, WANG Bin, GUO Min. Research on Collaborative Defense Technology of Network Security Based on Swarm Intelligence[J]. Netinfo Security, 2020, 20(9): 52-56.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2020.09.011
| [1] | ZHANG Sicong, XIE Xiaoyao, XU Yang. Intrusion Detection Method Based on a Deep Convolutional Neural Network[J]. Journal of Tsinghua University(Science and Technology), 2019,59(1):46-54. |
| 张思聪, 谢晓尧, 徐洋. 基于dCNN的入侵检测方法[J]. 清华大学学报(自然科学版), 2019,59(1):46-54. | |
| [2] | SHONE N, NGOC T N, PHAIV D, et al. A Deep Learning Approach to Network Instrusion Detection[J]. IEEE Transations on Emerging Topics in Computational Intelligence, 2018,2(1):41-50. |
| [3] | WOLD S, ESBENSSEN K, GELADL P. Principal Component Analysis[J]. Chemometrics & Intelligent Laboratory System, 1987,2(1):37-52. |
| [4] | YAN Qiao, YU F R, GONG Qingxiang, et al. Software-defined Networking(SDN) and Distributed Denial of Service(DDoS) Attacks in Cloud Computing Environments: A Survey, Some Research Issues, and Challenges[J]. IEEE Communications Surveys \$ Tutorials, 2015,18(1):602-622. |
| [5] | SAHAY R, BLANC G, ZHANG Zonghua, et al. Towards Autonomic DDoS Mitigation Using Software Defined Networking[EB/OL]. https://hal.archives-ouvertes.fr/hal-01257899, 2019-9-10. |
| [6] | BRAGA R, MOTA E, PASSITO A. Lightweight DDoS Flooding Attack Detection Using NOX/OpenFlow[C]// IEEE. IEEE Local Computer Network Conference, October 10-14, 2010, Denver, CO, USA. New Jersey: IEEE, 2010: 408-415. |
| [7] |
SYLVESTER E V A, BENTZEN P, BRADBURYIR, et al. Applications of Random Forest Feature Selection for Fine-Scale Genetic Population Assignment[J]. Evolutionary Applications, 2018,11(2):153-165.
doi: 10.1111/eva.12524 URL pmid: 29387152 |
| [8] | HART P E. The Condensed Nearest Neighbor Rule[J]. IEEE Transactions on Information Processing Systems, 2018,31(3):6638-6648. |
| [9] | JORDAN M I, BISHOP C. Neural Networks[J]. ACM Computing Surveys, 1996,28(1):73-75. |
| [1] | LU Jiali. Log Anomaly Detection Method Based on Improved Time Series Model [J]. Netinfo Security, 2020, 20(9): 1-5. |
| [2] | SHEN Jinwei, ZHAO Yi, LIANG Chunlin, ZHANG Ping. RFID Group Tag Ownership Transfer Protocol Based on Cyclic Grouping Function [J]. Netinfo Security, 2020, 20(9): 102-106. |
| [3] | ZHOU Zhining, WANG Binjun, ZHAI Yiming, TONG Xin. Spam Filtering Model Based on ALBERT Dynamic Word Vector [J]. Netinfo Security, 2020, 20(9): 107-111. |
| [4] | HAN Lei, CHEN Wuping, ZENG Zhiqiang, ZENG Yingming. Research on Hierarchical Network Structure and Application of Blockchain [J]. Netinfo Security, 2020, 20(9): 112-116. |
| [5] | LI Qiao, LONG Chun, WEI Jinxia, ZHAO Jing. A Hybrid Model of Intrusion Detection Based on LMDR and CNN [J]. Netinfo Security, 2020, 20(9): 117-121. |
| [6] | TONG Xin, WANG Luona, WANG Runzheng, WANG Jingya. A Generation Method of Word-level Adversarial Samples for Chinese Text Classification [J]. Netinfo Security, 2020, 20(9): 12-16. |
| [7] | HUANG Na, HE Jingsha, WU Yabiao, LI Jianguo. Method of Insider Threat Detection Based on LSTM Regression Model [J]. Netinfo Security, 2020, 20(9): 17-21. |
| [8] | ZHANG Runzi, LIU Wenmao, YOU Yang, XIE Feng. Research on AISecOps Automation Levels and Technology Trends [J]. Netinfo Security, 2020, 20(9): 22-26. |
| [9] | WU Zenan, TIAN Liqin, CHEN Nan. Research on Quantitative Analysis of System Security Based on Stochastic Petri Net [J]. Netinfo Security, 2020, 20(9): 27-31. |
| [10] | XU Yu, ZHOU You, LIN Lu, ZHANG Cong. Applied Research of Unsupervised Machine Learning in Game Anti-fraud [J]. Netinfo Security, 2020, 20(9): 32-36. |
| [11] | XU Huikai, LIU Yue, MA Zhenbang, DUAN Haixin. A Large-scale Measurement Study of MQTT Security [J]. Netinfo Security, 2020, 20(9): 37-41. |
| [12] | LIU Daheng, LI Hongling. Research on QR Code Phishing Detection [J]. Netinfo Security, 2020, 20(9): 42-46. |
| [13] | WANG Jinmiao, XIE Yongheng, WANG Guowei, LI Yiting. A Method of Privacy Preserving and Access Control in Blockchain Based on Attribute-based Encryption [J]. Netinfo Security, 2020, 20(9): 47-51. |
| [14] | LI Shibin, LI Jing, TANG Gang, LI Yi. Method of Network Security States Prediction and Risk Assessment for Industrial Control System Based on HMM [J]. Netinfo Security, 2020, 20(9): 57-61. |
| [15] | WU Jing, LU Tianliang, DU Yanhui. Generation of Malicious Domain Training Data Based on Improved Char-RNN Model [J]. Netinfo Security, 2020, 20(9): 6-11. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||