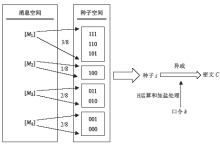
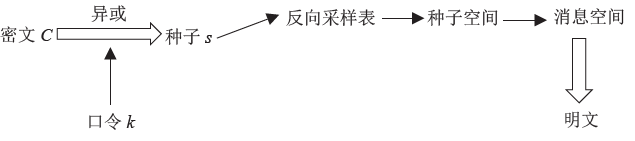
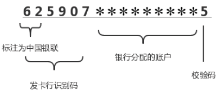
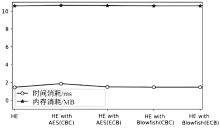
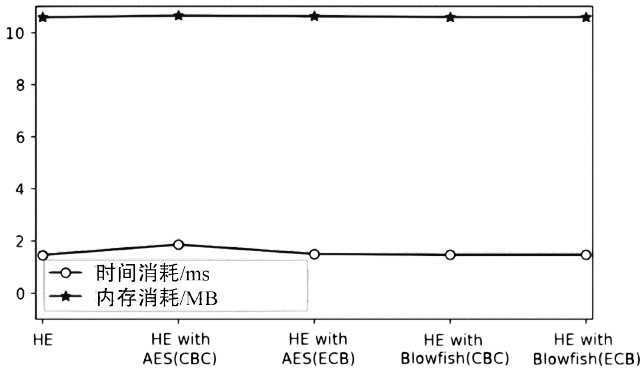
Netinfo Security ›› 2019, Vol. 19 ›› Issue (12): 38-46.doi: 10.3969/j.issn.1671-1122.2019.12.005
Previous Articles Next Articles
Privacy Data Protection Based on the Honey Encryption
- School of Computer, Central China Normal University, Wuhan Hubei 430079, China
-
Received:2019-05-20Online:2019-12-10Published:2020-05-11
CLC Number:
Cite this article
Yajun GUO, Dongqi PU. Privacy Data Protection Based on the Honey Encryption[J]. Netinfo Security, 2019, 19(12): 38-46.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2019.12.005
| [1] | BONNEAU J.The Science of Guessing: Analyzing an Anonymized Corpus of 70 Million Passwords[C]//IEEE. 2012 IEEE Symposium on Security and Privacy, May 20-23, 2012, San Francisco, California, USA. New York: IEEE, 2012: 538-552. |
| [2] | KU Weichi, CHEN Shuaimin.Weaknesses and Improvements of an Efficient Password Based Remote User Authentication Scheme Using Smart Cards[J]. IEEE Transactions on Consumer Electronics, 2004, 50(1): 204-207. |
| [3] | JUELS A, RISTENPART T.Honey Encryption: Security Beyond the Brute-Force Bound[C]//Springer. 33rd Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 11-15, 2014, Copenhagen, Denmark. Heidelberg: Springer, 2014: 293-310. |
| [4] | JUELS A, RIVEST R L.Honeywords: Making Password-Cracking Detectable[C]//ACM. Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, November 04-08, 2013, Berlin, Germany. New York: ACM, 2013: 145-160. |
| [5] | ERGULER I.Achieving Flatness: Selecting the Honeywords from Existing User Passwords[J]. IEEE Transactions on Dependable and Secure Computing, 2015, 13(2): 284-295. |
| [6] | RAO S.Data and System Security with Failwords: U.S. Patent Application 11/039, 577[P].2006-7-20. |
| [7] | YOU Jianzhou, ZHANG Yueyang, LV Shichao, et al.Method of ICS Honeypot Identification Based on Packet-Sharding[J]. Journal of Cyber Security, 2019, 4(3):83-92. |
| 游建舟,张悦阳,吕世超,等. 基于数据包分片的工控蜜罐识别方法[J]. 信息安全学报,2019,4(3):83-92. | |
| [8] | BOJINOV H, BURSZTEIN E, BOYEN X, et al.Kamouflage: Loss-Resistant Password Management[C]// Springer. European Symposium on Research in Computer Security, September 20-22, 2010, Athens, Greece. Heidelberg: Springer, 2010: 286-302. |
| [9] | GENC Z A, KARDAŞ S, KIRAZ M S.Examination of a New Defense Mechanism: Honeywords[C]//Springer. IFIP International Conference on Information Security Theory and Practice, September 28-29, 2017, Heraklion, Crete, Greece. Heidelberg: Springer, 2017: 130-139. |
| [10] | YUILL J, ZAPPE M, DENNING D, et al.Honeyfiles: Deceptive Files for Intrusion Detection[C]//IEEE. Proceedings from the Fifth Annual IEEE SMC Information Assurance Workshop, June 10-11, 2004, West Point, NY, USA. New York: IEEE, 2004: 116-122. |
| [11] | VINAYAK P P, NAHALA M A.Avoiding Brute Force Attack in MANET Using Honey Encryption[J]. International Journal of Science and Research, 2015, 4(3): 83-85. |
| [12] | TYAGI N, WANG J, WEN K, et al. Honey Encryption Applications[EB/OL]. , 2019-4-30. |
| [13] | YIN Wei, ZHOU Hongjian, XING Guoqiang.Application of Honey Encryption Mechanism in Protection of Private Data[J]. Journal of Computer Applications, 2017, 37(12): 3406-3411. |
| 银伟,周红建,邢国强. 蜜罐加密技术在私密数据保护中的应用[J]. 计算机应用,2017,37(12):3406-3411. | |
| [14] | HUANG Z, AYDAY E, FELLAY J, et al.GenoGuard: Protecting Genomic Data Against Brute-Force Attacks[C]//IEEE. 2015 IEEE Symposium on Security and Privacy, May 17-21, 2015, San Jose, CA, USA. New York: IEEE, 2015: 447-462. |
| [15] | YOON J W, KIM H, JO H J, et al.Visual Honey Encryption: Application to Steganography[C]//ACM. Proceedings of the 3rd ACM Workshop on Information Hiding and Multimedia Security, June 17-19, 2015, Portland, Oregon, USA. New York: ACM, 2015: 65-74. |
| [16] | JAEGER J, RISTENPART T, TANG Q.Honey Encryption Beyond Message Recovery Security[C]//Springer. Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 8-12, 2016, Vienna, Austria. Heidelberg: Springer, 2016: 758-788. |
| [17] | CORON J S, DODIS Y, MANDAL A, et al.A Domain Extender for the Ideal Cipher[C]//Springer. Theory of Cryptography Conference, February 9-11, 2010, Zurich, Switzerland. Heidelberg: Springer, 2010: 273-289. |
| [18] | NICK. PIN Number Analysis[EB/OL]. , 2019-4-30. |
| [19] | BELLARE M, RISTENPART T, TESSARO S.Multi-instance Security and Its Application to Password-based Cryptography[C]//Springer. Annual Cryptology Conference, August 19-23, 2012, Santa Barbara, CA, USA. Heidelberg: Springer, 2012: 312-329. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||