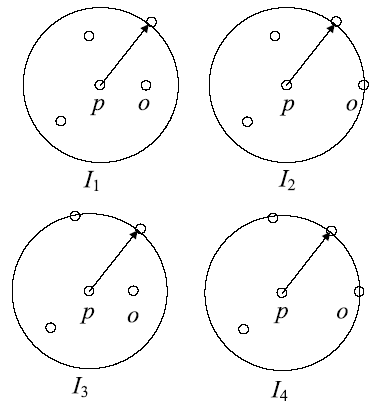
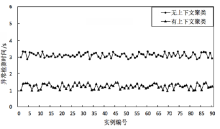
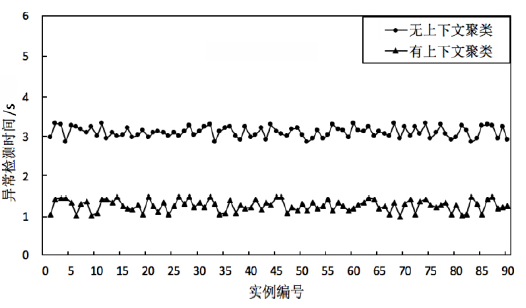
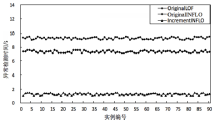
Netinfo Security ›› 2018, Vol. 18 ›› Issue (12): 54-65.doi: 10.3969/j.issn.1671-1122.2018.12.008
Previous Articles Next Articles
Detection and Recognition Strategy for Anomaly of Cloud Virtual Machine Based on Context Clustering
- College of Computer, Chongqing University of Posts and Telecommunications, Chongqing 400065, China
-
Received:2018-09-30Online:2018-12-20Published:2020-05-11
CLC Number:
Cite this article
Li HE, Yuanhui YAO. Detection and Recognition Strategy for Anomaly of Cloud Virtual Machine Based on Context Clustering[J]. Netinfo Security, 2018, 18(12): 54-65.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2018.12.008
| 属性类型 | 属性名称 | 属性解释 |
|---|---|---|
| 上下文 参数 | stageType | 运行任务所属阶段类型,如shuffleStage |
| ShuffleRead | 运行任务的shuffle数据读取量 | |
| shuffleWrite | 运行任务的shuffle数据发送量 | |
| remoteSent | 运行任务的远程数据发送量 | |
| remoteReceive | 运行任务的远程数据接收量 | |
| 性能 指标 | User% | 虚拟机在用户模型下的CPU使用率 |
| Mem% | 虚拟机的内存使用率 | |
| Ioread/s | 虚拟机每秒钟对磁盘读取的数据量 | |
| Iowrite/s | 虚拟机每秒钟对磁盘写入的数据量 | |
| Rxbyt/s | 虚拟机每秒钟通过网络接收的数据量 | |
| Txbyt/s | 虚拟机每秒钟通过网络发送的数据量 |
| [1] | PANNU H S, LIU Jianguo, FU Song.AAD: Adaptive Anomaly Detection System for Cloud Computing Infrastructures[C]// IEEE. 31st Symposium on Reliable Distributed Systems, October 8-11, 2012, Irvine, CA, USA. New Jersey: IEEE, 2013: 396-397. |
| [2] | PANNU H S, LIU Jianguo, GUAN Qiang, et al.AFD: Adaptive Failure Detection System for Cloud Computing Infrastructures[C]// IEEE. 31st International Performance Computing and Communications Conference, December, 1-3, 2012, Austin, TX, USA. New Jersey: IEEE, 2013: 71-80. |
| [3] | ZHENG Dequan, LI Fenghuan, ZHAO Tiejun. Self-adaptive Statistical Process Control for Anomaly Detection in Time Series[EB/OL]. , 2018-4-11. |
| [4] | YE Xiaoming, CHEN Xinghua, WANG Haizhou, et al.An Anomalous Behavior Detection Model in Cloud Computing[J]. Tsinghua Science & Technology, 2016, 21(3): 322-332. |
| [5] | SHIRAZI S N, SIMPSON S, GOUGLIDIS A, et al.Anomaly Detection in the Cloud Using Data Density[C]// IEEE. 9th Internation Conference on Cloud Computing, June 27-July 2, 2016, San Francisco, CA, USA. New Jersey: IEEE, 2016: 616-623. |
| [6] | GURUMDIMMA N, JHUMKA A, LIAKATA M, et al.CRUDE: Combining Resource Usage Data and Error Logs for Accurate Error Detection in Large-Scale Distributed Systems[C]// IEEE. 35th Symposium on Reliable Distributed Systems, September 26-29, 2016, Budapest, Hungary. Jersey: IEEE, 2016: 51-60. |
| [7] | SMRITHY G S, MUNIRATHINAM S, BALAKRISHNAN R.Online Anomaly Detection Using Non-parametric Technique for Big Data Streams in Cloud Collaborative Environment[C]// IEEE. 2016 IEEE International Conference on Big Data, December 5-8, 2016, Washington, DC, USA. Jersey: IEEE, 2016: 1950-1955. |
| [8] | GUAN Qiang, FU Song, DEBARDELEBEN N, et al.Exploring Time and Frequency Domains for Accurate and Automated Anomaly Detection in Cloud Computing Systems[C]// IEEE. 19th Pacific Rim International Symposium on Dependable Computing, December 2-4, 2013, Vancouver, BC, Canada. Jersey: IEEE, 2013: 196-205. |
| [9] | XIA Yuming, HU Shaoyong, ZHU Shaomin, et al.Research on the Method of Network Attack Detection Based on Convolution Neural Network[J]. Netinfo Security, 2017, 17(11): 32-36. |
| 夏玉明,胡绍勇,朱少民,等. 基于卷积神经网络的网络攻击检测方法研究[J]. 信息网络安全,2017,17(11):32-36. | |
| [10] | HE Mingliang, CHEN Zemao, ZUO Jin.Cluster Anomaly Detection Algorithm Based on Multi-windows Mechanism[J]. Netinfo Security, 2016, 16(11): 33-39. |
| 何明亮,陈泽茂,左进. 基于多窗口机制的聚类异常检测算法[J]. 信息网络安全,2016,16(11):33-39. | |
| [11] | PANDEESWARI N, KUMAR G.Anomaly Detection System in Cloud Environment Using Fuzzy Clustering Based ANN[J]. Mobile Networks and Applications, 2016, 21(3): 494-505. |
| [12] | PANNU H S, LIU Jianguo, FU Song.A Self-Evolving Anomaly Detection Framework for Developing Highly Dependable Utility Clouds[C]// IEEE. 2012 IEEE Global Communications Conference, December 3-7, 2012, Anaheim, CA, USA. Jersey: IEEE, 2012: 1605-1610. |
| [13] | BREUNIG M M, KRIEGEL H P, NG R T.LOF: Identifying Density-based Local Outliers[C]// ACM. 2000 ACM SIGMOD International Conference on Management of Data, May 15-18, 2000, Dallas, Texas, USA. New York: ACM, 2000: 93-104. |
| [14] | LIN Weiming.Research on Methods for Detecting Virtual Machine Abnormal Behaviors in Cloud Computing Platforms[D]. Chongqing: Chongqing University, 2014. |
| 林铭炜. 面向云平台的虚拟机异常行为检测方法研究[D]. 重庆:重庆大学,2014. | |
| [15] | ZHAO Gang, YAO Xingren.Anomaly Detection Model Based on User Portrait[J]. Netinfo Security, 2017, 17(7): 18-24. |
| 赵刚,姚兴仁. 基于用户画像的异常行为检测模型[J]. 信息网络安全,2017,17(7):18-24. | |
| [16] | WANG Jun, XIA Limin.Abnormal Behavior Detection in Videos Using Deep Learning[J]. Cluster Computing, 2018(11): 1-11. |
| [17] | GNOUMA M, EJBALI R, ZAIED M.Abnormal Events’ Detection in Crowded Scenes[J]. Multimedia Tools & Applications, 2018(3):1-22. |
| [18] | SHARIFZADEH S, BIRO I, LOHSE N, et al. Abnormality Detection Strategies for Surface Inspection Using Robot Mounted Laser Scanners[EB/OL]. , 2018-4-12. |
| [19] | KARAMI A. An Anomaly-based Intrusion Detection System in Presence of Benign Outliers with Visualization Capabilities[EB/OL]. , 2018-4-12. |
| [20] | FARSHCHI M, SCHNEIDER J G, WEBER I, et al. Metric Selection and Anomaly Detection for cloud Operations Using Log and Metric Correlation Analysis[EB/OL]. , 2018-4-12. |
| [21] | WANG Tao, XU Jiwei, ZHANG Wenbo, et al. Self-adaptive Cloud Monitoring with Online Anomaly Detection[EB/OL]. , 2018-4-12. |
| [22] | ZHOU Yizhou, WANG Bin, XIE Xiaoquan.Design of Software Defined Intrusion Detection System in Cloud[J]. Netinfo Security, 2015, 15(9): 191-195. |
| 周益周,王斌,谢小权. 云环境下软件定义入侵检测系统设计[J]. 信息网络安全,2015,15(9):191-195. | |
| [23] | JIN Wen, TUNG A K H, HAN Jiawei, et al. Ranking Outliers Using Symmetric Neighborhood Relationship[C]//Springer. Pacific-Asia Conference on Knowledge Discovery and Data Mining, April 9-12, 2006, Singapore. Heidelberg: Springer, 3918: 577-593. |
| [24] | WHITE T, CUTTING D.Hadoop: the Definitive Guide[J]. Sebastopol: O’reilly Media Inc, 2009. |
| [25] | KARAU H, KONWINSKI A, WENDELL P, et al.Learning Spark: Lightning-Fast Big Data Analysis[M]. Sebastopol: O’reilly Media Inc, 201. |
| [26] | CAMPELLO R J G B. A Fuzzy Extension of the Rand Index and other Related Indexes for Clustering and Classification Assessment[J]. Pattern Recognition Letters, 2007, 28(7): 833-841. |
| [1] | Yuan LIU, Wei QIAO. Research and Optimization of Container Network Based on Kubernetes Cluster System in Cloud Environment [J]. Netinfo Security, 2020, 20(3): 36-44. |
| [2] | Xiao WANG, Jun ZHAO, Jianbiao ZHANG. Research on Dynamic Monitoring Mechanism for Virtual Machine Based on Trusted Software Base [J]. Netinfo Security, 2020, 20(2): 7-13. |
| [3] | Jiameng BAI, Yingshuai KOU, Zeyi LIU, Daren ZHA. Docker-based RBAC Task Management System [J]. Netinfo Security, 2020, 20(1): 75-82. |
| [4] | Liangqin REN, Wei WANG, Qiongxiao WANG, Linli LU. A New Cloud Cryptographic Computing Platform Architecture and Implementation [J]. Netinfo Security, 2019, 19(9): 91-95. |
| [5] | Yi YU, Liangshuang LV, Xiaojian LI, Tianbo WANG. Dynamic Network Topology Description Language for Mobile Cloud Computing Scenario [J]. Netinfo Security, 2019, 19(9): 120-124. |
| [6] | Zixuan WANG, Liangshuang LV, Xiaojian LI, Tianbo WANG. A Shared Storage-based Virtual Machine Application Distribution Strategy for OpenStack [J]. Netinfo Security, 2019, 19(9): 125-129. |
| [7] | Yanpeng CUI, Luming FENG, Zheng YAN, Huaqing LIN. Research on Software Security Model of Cloud Computing Based on Program Slicing Technology [J]. Netinfo Security, 2019, 19(7): 31-41. |
| [8] | Xinrui GE, Wei CUI, Rong HAO, Jia YU. Verifiable Keywords Ranked Search Scheme over Encrypted Cloud Data [J]. Netinfo Security, 2019, 19(7): 82-89. |
| [9] | Chunqi TIAN, Jing LI, Wei WANG, Liqing ZHANG. A Method for Improving the Performance of Spark on Container Cluster Based on Machine Learning [J]. Netinfo Security, 2019, 19(4): 11-19. |
| [10] | Wei WANG, Xudong SHEN. Research on Transfer Time Series Anomaly Detection Algorithm Based on Instance [J]. Netinfo Security, 2019, 19(3): 11-18. |
| [11] | Pu ZHAO, Wei CUI, Rong HAO, Jia YU. A Secure Outsourcing Computation Scheme for El-Gamal Signature Generation [J]. Netinfo Security, 2019, 19(3): 81-86. |
| [12] | Weichao YANG, Yuanbo GUO, Ya ZHONG, Shuaihui ZHEN. IoT Traffic Anomaly Detection Based on Device Type Identification and BP Neural Network [J]. Netinfo Security, 2019, 19(12): 53-63. |
| [13] | Zhenfeng ZHANG, Zhiwen ZHANG, Ruichao WANG. Model of Cloud Computing Security and Compliance Capability for Classified Protection of Cybersecurity 2.0 [J]. Netinfo Security, 2019, 19(11): 1-7. |
| [14] | ZHU Haiqi, JIANG Feng. Research and Analysis of Anomaly Detection Technology for Operation and Maintenance Data in the Era of Artificial Intelligence [J]. Netinfo Security, 2019, 19(11): 24-35. |
| [15] | Hailian DENG, Yujing LIU, Yixuan GE, Jinshu SU. Research on Inter-domain Routing Anomaly Detection Technology [J]. Netinfo Security, 2019, 19(11): 63-70. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||