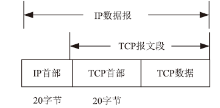
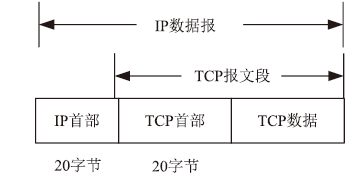
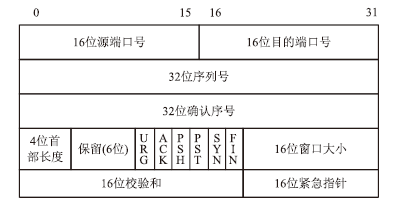
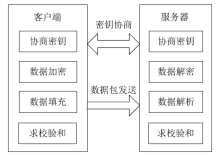
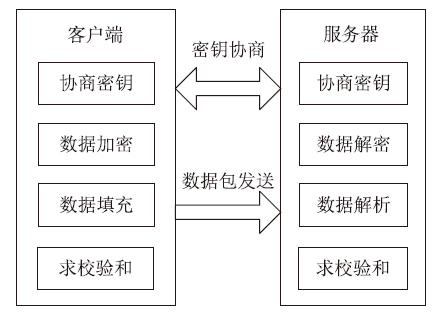
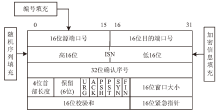
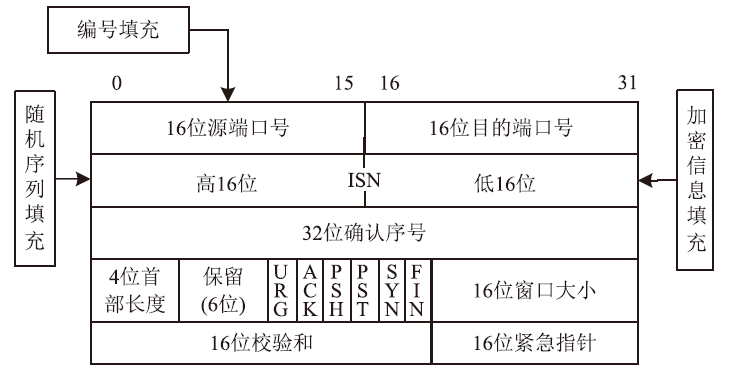
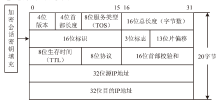
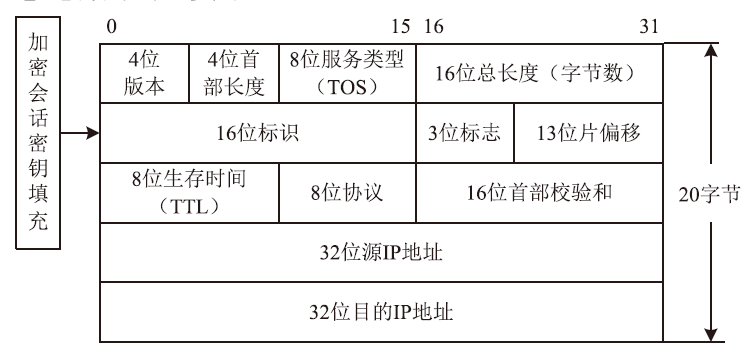
| [1] |
钱玉文,赵邦信,孔建寿,等. 一种基于Web的可靠网络隐蔽时间信道的研究[J]. 计算机研究与发展,2015,48(3):423-431.
|
| [2] |
翟江涛,段珂珂,刘光杰,等.一种改进的基于TCP协议重传的隐信道构建算法[J]. 四川大学学报:自然科学版,2010,47(增刊1):37-42.
|
| [3] |
王华翔. 基于IP数据包生存期的隐蔽信道[J]. 网络安全技术与应用,2010(6):19-21.
|
| [4] |
孙泽民,芦天亮,周阳. 基于BGP 协议的TCP MD5加密认证的破解技术分析[J]. 信息网络安全,2015(9):37-40.
|
| [5] |
CABUK S,BRODLEY C E,SHIELDS C.IP Covert Timing Channels: Design and Detection[C]//ACM. 11th ACM Conference on Computer and Communications Security, October 25-29, 2004, USA. New York: ACM , 2004: 178-187.
|
| [6] |
王鹏,兰少华,张晶,等. 一种基于TCP时间戳选项的时间隐蔽信道方法[J]. 解放军理工大学学报,2015(2):120-125.
|
| [7] |
LUO Xiapu, CHAN E W W, CHANG R K C. TCP Covert Timing Channels: Design and Detection[C]//IEEE. IEEE International Conference on Dependable Systems and Networks with FTCS and DCC, June 24-27, 2008, Anchorage. Washington: IEEE, 2008: 420-429.
|
| [8] |
王涛,胡爱群. 基于边界检测的IPSec VPN协议的一致性测试方法[J]. 信息网络安全,2014(2):7-11.
|
| [9] |
LAMPSON B W.A Note on the Confinement Problem[J]. Communications of the ACM, 1973, 16(10): 613-615.
|
| [10] |
GIRLING C G. Covert Channels in LAN’s[J]. IEEE Transactions on Software Engineering, 1987, SE-13(2): 292-296.
|
| [11] |
邹昕光,金海军,娜克成,等. 基于HTTP协议的参数排序通信隐藏算法[J]. 计算机工程,2006,32(20):147-149.
|
| [12] |
邹昕光,金海军,娜克成,等. 基于HTTP协议多维随机参数插入通信隐藏算法[J]. 计算机工程与应用,2006,42(34):127-130.
|
| [13] |
强亮,李斌,胡铭曾. 基于HTTP协议的网络隐蔽通道研究[J]. 计算机工程,2005,31(15):224-225.
|
| [14] |
李根军. 基于HTTP 协议的隧道技术的设计与实现[D]. 成都:四川大学,2004.
|
| [15] |
张令通,罗森林. 基于TCP协议首部的网络隐蔽通道技术研究[J]. 计算机工程与科学,2014,36(6):1072-1076.
|
| [16] |
卢仲君. 基于包分类的网络隐蔽信道研究[D]. 南京:南京理工大学,2009.
|
| [17] |
马文岩. HTTP协议上几种新的应用层隐蔽通道[J]. 计算机光盘软件与应用,2014(15):179-180.
|
| [18] |
武光达,蒋朝惠. 基于DPI的流量识别系统的研究[J]. 信息网络安全,2014(10):44-48.
|