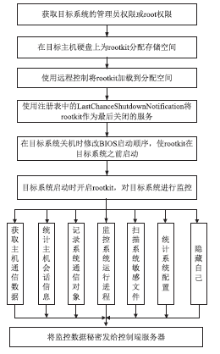
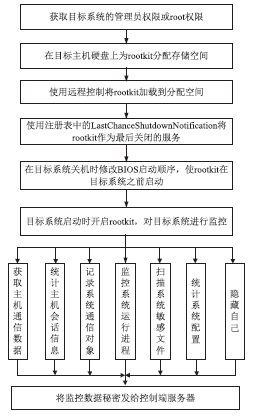
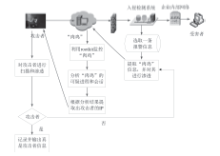
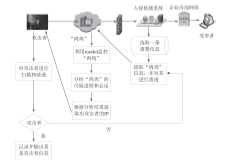
| [1] |
LU G, ZHONG H L, ZHANG Y, et al.Automatically Mining Application Signatures for Lightweight Deep Packet Inspection[J]. Network Technology and Application, 2013, 10(6): 86-99.
|
| [2] |
LENKA R K, RANJAN P.A Comparative Study on DFA-Based Pattern Matching for Deep Packet Inspection[C]//2012 Third International Conference on Computer and Communication Technology, 2012: 255-260.
|
| [3] |
VASHIST A, POYLISHER A, GHOSH A, et al.Managing high volume data for network attack detection using real-time flow filtering[J]. Wireless Communication Over Zigbee for Automotive Inclination Measurement China Communications, 2013, 10(3): 56-66.
|
| [4] |
ISO/IEC. Information technology -- Open Systems Interconnection -- Basic Reference Model: The Basic Model[EB/OL]. .
|
| [5] |
SILVA S S C, SILVA R M P, PINTO R C G, et al. Botnets: A survey[J]. Computer Networks, 2013, 57(2): 378-403.
|
| [6] |
ZHAO D, TRAORE I, SAYED B, et al.Botnet detection based on traffic behavior analysis and flow intervals[J]. Computers & Security, 2013,39(4): 2-16.
|
| [7] |
WEBER T. Criminals may overwhelm the web[N]. BBC News, 2007-02-25.
|
| [8] |
RFC 2827 Network Ingress Filtering: Defeating Denial of Service Attacks which employ IP Source Address Spoofing[S]. Network Working Group, 2000.
|
| [9] |
SAVAGE S, WETHERALL D, KARLIN A, et al.Network Support for IP Traceback[J]. IEEE/ACM Transactions on Networking, 2001, 9(3): 226-237.
|
| [10] |
STONE R.CenterTrack: An IP overlay network for tracking DoS floods[C]//in Proc. 2000 USENIX Security Syrup, 2000: 199-212.
|
| [11] |
LODI G, ANIELLO L, LUNA G A D, et al. An event-based platform for collaborative threats detection and monitoring[J]. Information Systems, 2014, 39(1): 175-195.
|
| [12] |
ZHANG L, YU S, W D, et al. A Survey on Latest Botnet Attack and Defense[C]//IEEE International Conference on Trust, Security & Privacy in Computing & Communications, 2011: 5-60
|
| [13] |
YU W, ZHANG N, FU X W, et al.Localization Attacks to Internet Threat Monitors: Modeling and Countermeasures[J]. IEEE Transactions on Computers, 2010,59(12): 1655-1668.
|
| [14] |
李娜,杜彦辉,高峰. 移动僵尸网络综述[J]. 信息网络安全,2015,(4):19-27.
|
| [15] |
肖云,王选宏. 支持向量机理论及其在网络安全中的应用[M]. 西安:西安电子科技大学出版社,2011.
|
| [16] |
何鹏程,方勇. 一种基于Web日志和网站参数的入侵检测和风险评估模型的研究[J]. 信息网络安全,2015,(1):61-65.
|
| [17] |
Denning D E.An Intrusion-Detection Model[J]. IEEE Transactions on Software Engineering, 1987, 13(2): 222-232.
|
| [18] |
蒋建春,马恒太,任党恩,等. 网络安全入侵检测研究综述[J]. 软件学报,2000,11(11):1460-1466.
|
| [19] |
戚名钰,刘铭,傅彦铭. 基于PCA的SVM网络入侵检测研究[J]. 信息网络安全,2015,(2):15-18.
|
| [20] |
MANGANARIS S, CHRISTENSEN M, ZERKLE D, et al.A data mining analysis of RTID alarms[J]. Computer Networks, 2000,34(4): 571-577.
|
| [21] |
ABOUABDALLA O, EL-TAJ H, MANASRAH A, et al.False positive reduction in intrusion detection system: a survey[C]//Proceedings of the 2009 2nd IEEE International Conference on Broadband Network & Multimedia Technology (IC-BNMT), 2009: 463-466.
|
| [22] |
BARAPATRE P, TARAPORE N Z, PUKALE S G, et al.Training MLP neural network to reduce false alerts in IDS[C]//Proceedings of the 2008 International Conference on Computing, Communication and Networking, 2008: 1-7.
|
| [23] |
段新东,林玉香,张鑫. 基于智能化自学习方式的入侵检测防护系统设计与实现[J]. 信息网络安全,2014,(2):20-26.
|
 ), Zheng-yong XIE, Wei CUI
), Zheng-yong XIE, Wei CUI