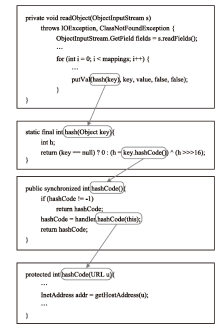
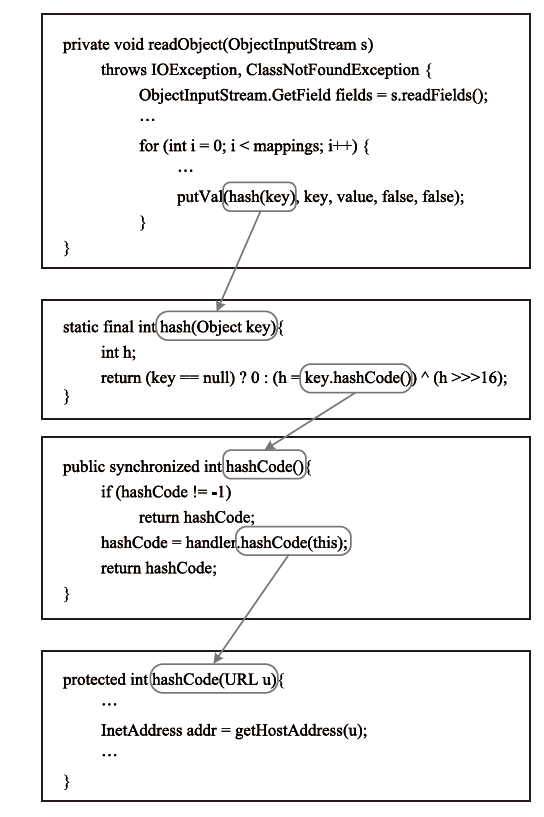
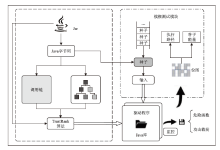
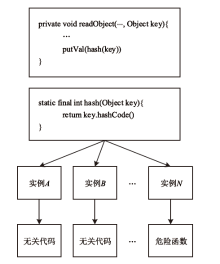
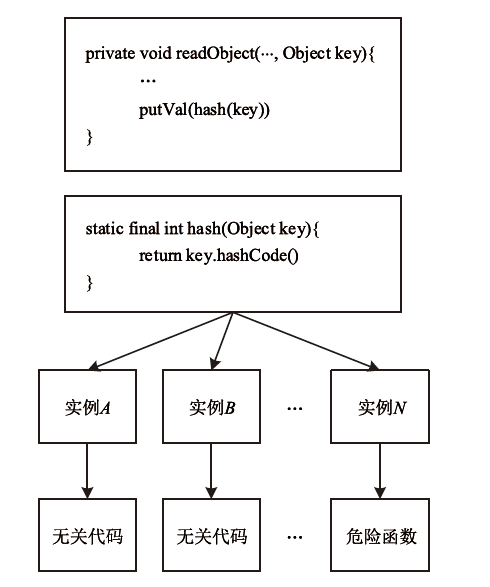
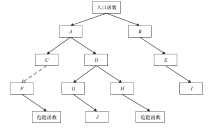
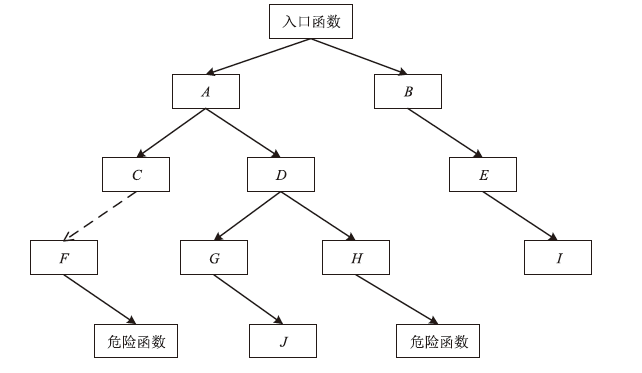
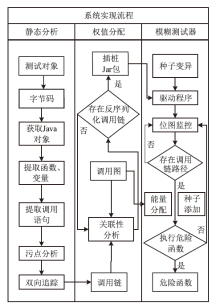
| [1] |
YSoSerial. A Proof-of-Concept Tool for Generating Payloads that Exploit Unsafe Java Object Deserialization[EB/OL]. (2022-10-29)[2024-04-06]. https://github.com/frohoff/ysoserial.
|
| [2] |
HAKEN I. Automated Discovery of Deserialization Gadget Chains[EB/OL]. (2020-04-29)[2024-04-06]. https://i.blackhat.com/us-18/Thu-August-9/us-18-Haken-Automated-Discovery-of-Deserialization-Gadget-Chains-wp.pdf.
|
| [3] |
Alibaba. Fastjson 2.0[EB/OL]. (2022-06-13)[2024-04-06]. https://github.com/alibaba/fastjson.
|
| [4] |
Google. Gson: A Java Serialization/Deserialization Library to Convert Java Objects into JSON and Back[EB/OL]. (2023-01-12)[2024-04-06]. https://github.com/google/gson.
|
| [5] |
XStream. About XStream[EB/OL]. (2022-12-24)[2024-04-06]. https://x-stream.github.io/index.html.
|
| [6] |
Oracle. Class XMLDecoder[EB/OL]. (2023-03-03)[2024-04-06]. https://docs.oracle.com/javase/8/docs/api/java/beans/XMLDecoder.html.
|
| [7] |
XU Wenyuan. The Design and Implementation of Static Code Analysis System Based on Machine Learning for Java[D]. Nanjing: Nanjing University, 2020.
|
|
徐文远. 基于机器学习的Java静态漏洞扫描系统的设计与实现[D]. 南京: 南京大学, 2020.
|
| [8] |
ALHUZALI A, GJOMEMO R, ESHETE B, et al. NAVEX: Precise and Scalable Exploit Generation for Dynamic Web Applications[C]// USENIX. 27th USENIX Security Symposium (USENIX Security 18). Berlin:USENIX, 2018: 377-392.
|
| [9] |
DOS S J P R, DA S K P, GONCALVES B P, et al. Selenium as a Free Tool to Test for Java Web Application[J]. International Journal of Advanced Engineering Research and Science, 2020, 7(4): 135-139.
|
| [10] |
KERSTEN R, LUCKOW K, PĂSĂREANU C S. POSTER: AFL-Based Fuzzing for Java with Kelinci[C]// ACM. Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 2511-2513.
|
| [11] |
MICHAL Z. American Fuzzy Lop[EB/OL]. (2014-06-12)[2024-04-06]. http://lcamtuf.coredump.cx/afl.
|
| [12] |
ZHU Hong. JFuzz: A Tool for Automated Java Unit Testing Based on Data Mutation and Metamorphic Testing Methods[C]// IEEE. 2015 Second International Conference on Trustworthy Systems and Their Applications. New York: IEEE, 2015: 8-15.
|
| [13] |
PADHYE R, LEMIEUX C, SEN K. JQF: Coverage-Guided Property-Based Testing in Java[C]// ACM. Proceedings of the 28th ACM SIGSOFT International Symposium on Software Testing and Analysis. New York: ACM, 2019: 398-401.
|
| [14] |
SPI Dynamics. Pentest: Web Application Testing with SPI Fuzzer White Paper[EB/OL]. (2005-04-07)[2024-04-06]. https://seclists.org/pen-test/2005/Apr/25.
|
| [15] |
XU Ling. Web Software Vulnerability Test of WebFuzz[J]. Software Guide(Educational Technology), 2012, 11(8): 84-85.
|
|
徐玲. WebFuzz的Web软件漏洞测试[J]. 软件导刊(教育技术), 2012, 11(8): 84-85.
|
| [16] |
LAWRENCE G. Marshalling Pickles[EB/OL]. (2020-04-29)[2024-04-06]. http://frohoff.github.io/appseccali-marshalling-pickles.
|
| [17] |
MUNOZ A. Friday the 13th: JSON Attacks[EB/OL]. (2017-06-12)[2024-04-06]. https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-JSON-Attacks-wp.pdf.
|
| [18] |
QChiLan. Soserial[EB/OL]. (2019-03-19)[2024-04-06]. https://github.com/QChiLan/soserial.
|
| [19] |
Mbechler. Marshalsec[EB/OL]. (2017-03-22)[2024-04-06]. https://github.com/mbechler/marshalsec.
|
| [20] |
CARETTONI L. Defending against Java Deserialization Vulnerabi-lities[EB/OL]. (2016-03-21)[2024-04-06]. https://www.ikkisoft.com/stuff/Defending_against_Java_Deserialization_Vulnerabilities.pdf.
|
| [21] |
DU Xiaoyu, YE He, WEN Weiping. Java Deserialization Vulnerability Gadget Chain Discovery Method Based on Bytecode Search[J]. Netinfo Security, 2020, 20(7): 19-29.
|
|
杜笑宇, 叶何, 文伟平. 基于字节码搜索的Java反序列化漏洞调用链挖掘方法[J]. 信息网络安全, 2020, 20(7): 19-29.
|
 ), ZHANG Boxian1,2, ZHANG Zhijie1,2, XIE Haining1,2, FU Jintao3, WANG Yang3
), ZHANG Boxian1,2, ZHANG Zhijie1,2, XIE Haining1,2, FU Jintao3, WANG Yang3