Netinfo Security ›› 2024, Vol. 24 ›› Issue (9): 1432-1443.doi: 10.3969/j.issn.1671-1122.2024.09.011
Previous Articles Next Articles
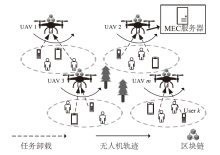
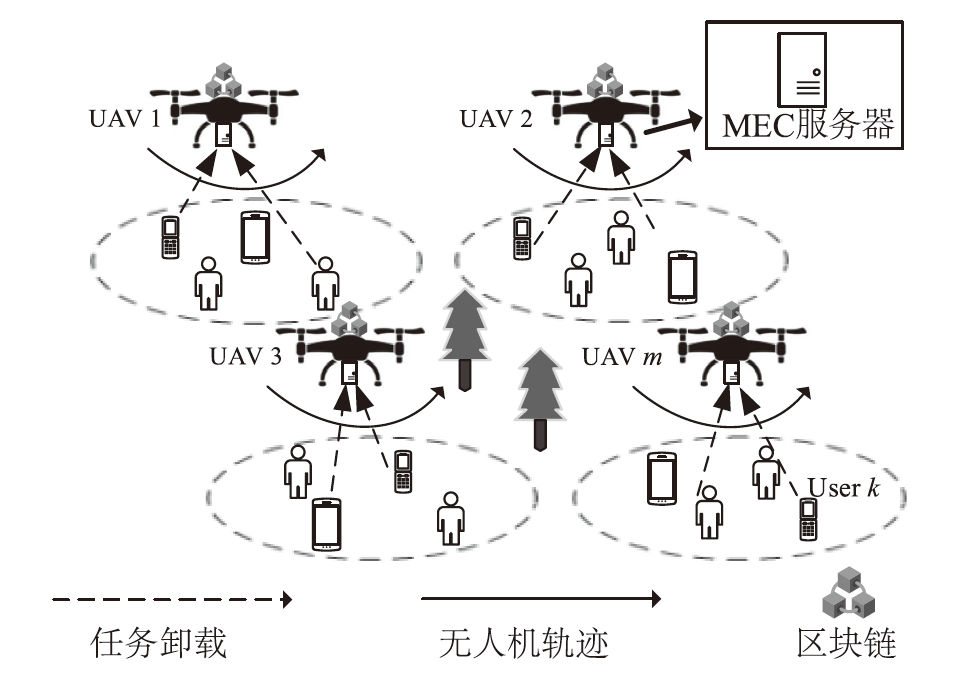
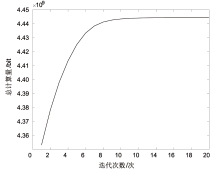
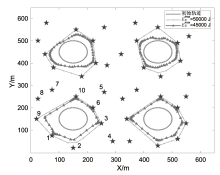
Performance Optimization of Blockchain-Assisted Unmanned Aerial Vehicle Mobile Edge Computing System
YU Lisu, LI Biao, YAO Yuanzhi, WEN Jiajin, LI Zipeng( ), WANG Zhen
), WANG Zhen
- School of Information Engineering, Nanchang University, Nanchang 330031, China
-
Received:2024-05-20Online:2024-09-10Published:2024-09-27
CLC Number:
Cite this article
YU Lisu, LI Biao, YAO Yuanzhi, WEN Jiajin, LI Zipeng, WANG Zhen. Performance Optimization of Blockchain-Assisted Unmanned Aerial Vehicle Mobile Edge Computing System[J]. Netinfo Security, 2024, 24(9): 1432-1443.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.09.011
| 参数含义/符号 | 取值 |
|---|---|
| UAV个数 | |
| 聚类用户个数 | |
| UAV飞行周期 | |
| 时隙个数 | |
| 时隙 | |
| UAV飞行高度 | |
| UAV最大飞行速度 | |
| UAV噪声功率 | |
| 参考距离 | |
| GU的发射功率 | |
| UAV的发射功率 | |
| MEC服务器计算频率 | |
| UAV的质量 | |
| 上行卸载链路总带宽 | |
| MEC服务器的电容系数 | |
| GU的电容系数 | |
| MEC每 | |
| GU每 |
| [1] | LIU Xiaolin, WEI Bowen, LUO Yuhua, et al. Simulation and Evaluation of Obstacle Clearance of Large Power Generation Equipment Transportation Line Based on UAV LiDAR and BIM Technology[J]. Journal of Nanchang University (Engineering and Technology), 2023, 45(1): 77-84. |
| 刘小林, 魏博文, 罗育华, 等. 基于无人机载LiDAR与BIM技术的巨大发电装备运输线路通障模拟评估[J]. 南昌大学学报(工科版), 2023, 45(1):77-84. | |
| [2] | HUANG Yangchao, AN Qi, HU Hang, et al. Sum Communication Rate Optimization in Multi-UAV Assisted Relaying System with NOMA[J]. Journal of Huazhong University of Science and Technology (Natural Science Edition), 2023, 51(11): 105-113. |
| 黄仰超, 安琪, 胡航, 等. 多无人机辅助的NOMA中继系统总通信速率优化[J]. 华中科技大学学报(自然科学版), 2023, 51(11):105-113. | |
| [3] |
ZHANG Tiankui, XU Yu, LIU Yuanwei, et al. UAV-Assisted MEC Systems: Architecture, Key Technology, and Future Challenges[J]. Telecommunications Science, 2022, 38(8): 3-16.
doi: 10.11959/j.issn.1000-0801.2022237 |
|
张天魁, 徐瑜, 刘元玮, 等. 无人机辅助MEC系统:架构、关键技术与未来挑战[J]. 电信科学, 2022, 38(8):3-16.
doi: 10.11959/j.issn.1000-0801.2022237 |
|
| [4] | ZHANG Yanhua, ZHAO Chengze, LI Meng, et al. Empower MEC and Blockchain to Resource Optimization for UAV-Assisted IoT[J]. Journal of Beijing University of Technology, 2022, 48(9): 935-943. |
| 张延华, 赵铖泽, 李萌, 等. MEC和区块链赋能无人机辅助的物联网资源优化[J]. 北京工业大学学报, 2022, 48(9):935-943. | |
| [5] | PORAMBAGE P, OKWUIBE J, LIYANAGE M, et al. Survey on Multi-Access Edge Computing for Internet of Things Realization[J]. IEEE Communications Surveys & Tutorials, 2018, 20(4): 2961-2991. |
| [6] | ZHANG Tiankui, XU Yu, LOO J, et al. Joint Computation and Communication Design for UAV-Assisted Mobile Edge Computing in IoT[J]. IEEE Transactions on Industrial Informatics, 2019, 16(8): 5505-5516. |
| [7] | NING Zhaolong, HU Hao, WANG Xiaojie, et al. Mobile Edge Computing and Machine Learning in the Internet of Unmanned Aerial Vehicles: A Survey[J]. ACM Computing Surveys, 2023, 56(1): 1-31. |
| [8] | TIAN Jie, WANG Di, ZHANG Haixia, et al. Service Satisfaction-Oriented Task Offloading and UAV Scheduling in UAV-Enabled MEC Networks[J]. IEEE Transactions on Wireless Communications, 2023, 22(12): 8949-8964. |
| [9] | QIN Xintong, SONG Zhengyu, HOU Tianwei, et al. Joint Optimization of Resource Allocation, Phase Shift and UAV Trajectory for Energy-Efficient RIS-Assisted UAV-Enabled MEC Systems[J]. IEEE Transactions on Green Communications and Networking, 2023, 7(4): 1778-1792. |
| [10] | CHIGULLAPALLY S, MURTHY C S R. Joint Energy and Throughput Optimization for MEC-Enabled Multi-UAV IoRT Networks[J]. Computer Communications, 2023, 201: 1-19. |
| [11] | ZHENG Xiangdong, WU Yuxin, ZHANG Lianhong, et al. Priority-Aware Path Planning and User Scheduling for UAV-Mounted MEC Networks: A Deep Reinforcement Learning Approach[EB/OL]. (2023-11-01)[2024-04-30]. https://www.semanticscholar.org/paper/Priority-aware-path-planning-and-user-scheduling-A-Zheng-Wu/4ab13c9341cbf75ec2b4e150fd4d68adb2ea82ad. |
| [12] | MAO Weihao, XIONG Ke, LU Yang, et al. Energy Consumption Minimization in Secure Multi-Antenna UAV-Assisted MEC Networks with Channel Uncertainty[J]. IEEE Transactions on Wireless Communications, 2023, 22(11): 7185-7200. |
| [13] | LI Guoqi, HONG Sheng, LAN Xueting, et al. The Security Reference Model of the Multi-Rotor UAV System[J]. Netinfo Security, 2022, 22(3): 10-19. |
| 李国旗, 洪晟, 兰雪婷, 等. 多旋翼无人机系统的信息安全参考模型[J]. 信息网络安全, 2022, 22(3):10-19. | |
| [14] | ZHANG Min, XU Chunxiang, ZHANG Jianhua. Research on Authentication Key Agreement Protocol Based on Multi-Factor in Internet of Drones[J]. Netinfo Security, 2022, 22(9): 21-30. |
| 张敏, 许春香, 张建华. 无人机网络中基于多因子的认证密钥协商协议研究[J]. 信息网络安全, 2022, 22(9):21-30. | |
| [15] | CHEN C, DENG Y, ZHU Shunzhi, et al. An IoT and Blockchain Based Logistics Application of UAV[J]. Multimedia Tools and Applications, 2024, 83(1): 655-684. |
| [16] | ZHOU Jie, LUO Ming, SONG Lixin, et al. A Dynamic Group Key Agreement Scheme for UAV Networks Based on Blockchain[EB/OL]. (2023-10-01)[2024-04-30]. https://dlnext.acm.org/doi/10.1016/j.pmcj.2023.101844. |
| [17] | FENG Houze, WANG Jingjing, FANG Zhengru, et al. Age of Information in UAV Aided Wireless Sensor Networks Relying on Blockchain[J]. IEEE Transactions on Vehicular Technology, 2023, 72(9): 12430-12435. |
| [18] | HUANG Xiaoge, LIU Xin, HE Yong, et al. Research on Optimization Scheme of Task Offloading in Blockchain-Enabled Fog Networks[J]. Journal of Electronics and Information Technology, 2022, 44(7): 2440-2448. |
| 黄晓舸, 刘鑫, 何勇, 等. 基于区块链的雾网络中的任务卸载优化方案研究[J]. 电子与信息学报, 2022, 44(7):2440-2448. | |
| [19] | SINAGA K P, KRISTINA P, MIIN-SHEN Y. Unsupervised K-Means Clustering Algorithm[J]. IEEE Access, 2020, 8: 80716-80727. |
| [20] |
XIONG Jingyu, GUO Hongzhi, LIU Jiajia. Task Offloading in UAV-Aided Edge Computing: Bit Allocation and Trajectory Optimization[J]. IEEE Communications Letters, 2019, 23(3): 538-541.
doi: 10.1109/LCOMM.2019.2891662 |
| [21] | KUMAR G, SAHA R, RAI M K, et al. Proof-of-Work Consensus Approach in Blockchain Technology for Cloud and Fog Computing Using Maximization-Factorization Statistics[J]. IEEE Internet of Things Journal, 2019, 6(4): 6835-6842. |
| [22] | WANG Siming, YE Dongdong, HUANG Xumin, et al. Consortium Blockchain for Secure Resource Sharing in Vehicular Edge Computing: A Contract-Based Approach[J]. IEEE Transactions on Network Science and Engineering, 2020, 8(2): 1189-1201. |
| [23] | XU Chenhan, WANG Kun, LI Peng, et al. Making Big Data Open in Edges: A Resource-Efficient Blockchain-Based Approach[J]. IEEE Transactions on Parallel and Distributed Systems, 2018, 30(4): 870-882. |
| [1] | LYU Qiuyun, ZHOU Lingfei, REN Yizhi, ZHOU Shifei, SHENG Chunjie. A Lifecycle-Manageable Public Data Sharing Scheme [J]. Netinfo Security, 2024, 24(8): 1291-1305. |
| [2] | ZHANG Jiwei, WANG Wenjun, NIU Shaozhang, GUO Xiangkuo. Blockchain Scaling Solutions: ZK-Rollup Review [J]. Netinfo Security, 2024, 24(7): 1027-1037. |
| [3] | GUO Rui, YANG Xin, WANG Junming. Verifiable and Revocable Attribute Encryption Scheme Based on Blockchain [J]. Netinfo Security, 2024, 24(6): 863-878. |
| [4] | LING Zhi, YANG Ming, YU Jiangyin. Research on Power Security Trading Platform Based on IPFS and Blockchain Technology [J]. Netinfo Security, 2024, 24(6): 968-976. |
| [5] | TIAN Zhao, NIU Yajie, SHE Wei, LIU Wei. A Reputation Evaluation Method for Vehicle Nodes in V2X [J]. Netinfo Security, 2024, 24(5): 719-731. |
| [6] | SHI Runhua, YANG Jingyi, WANG Pengbo, LIU Huawei. Online/Off line Cross-Domain Identity Authentication Scheme Based on Blockchain in Vehicle to Grid [J]. Netinfo Security, 2024, 24(4): 587-601. |
| [7] | HU Haiyang, LIU Chang, WANG Dong, WEI Xu. Clean Energy Data Traceability Mechanism Based on Blockchain [J]. Netinfo Security, 2024, 24(4): 626-639. |
| [8] | XUE Mingzhu, HU Liang, WANG Ming, WANG Feng. TAP Rule Processing System Based on Federated Learning and Blockchain Technology [J]. Netinfo Security, 2024, 24(3): 473-485. |
| [9] | ZHAI Peng, HE Jingsha, ZHANG Yu. An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment [J]. Netinfo Security, 2024, 24(2): 179-187. |
| [10] | HE Yefeng, QUAN Jiahui, LIU Yan. A Location Privacy Protection Scheme Based on Hybrid Blockchain [J]. Netinfo Security, 2024, 24(2): 229-238. |
| [11] | WANG Nan, YUAN Ye, YANG Haoran, WEN Zhouzhi, SU Ming, LIU Xiaoguang. Privacy Computing in Environmental Big Data on Blockchain [J]. Netinfo Security, 2024, 24(10): 1515-1527. |
| [12] | WU Haotian, LI Yifan, CUI Hongyan, DONG Lin. Federated Learning Incentive Scheme Based on Zero-Knowledge Proofs and Blockchain [J]. Netinfo Security, 2024, 24(1): 1-13. |
| [13] | ZHU Guocheng, HE Debiao, AN Haoyang, PENG Cong. The Proxy Voting Scheme Based on the Blockchain and SM9 Digital Signature [J]. Netinfo Security, 2024, 24(1): 36-47. |
| [14] | GONG Pengfei, XIE Sijiang, CHENG Andong. The Multi-Leader Consensus Algorithm Based on Improvements to HotStuff [J]. Netinfo Security, 2023, 23(9): 108-117. |
| [15] | ZHOU Quan, CHEN Minhui, WEI Kaijun, ZHENG Yulong. Blockchain Access Control Scheme with SM9-Based Attribute Encryption [J]. Netinfo Security, 2023, 23(9): 37-46. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||