Netinfo Security ›› 2024, Vol. 24 ›› Issue (1): 150-159.doi: 10.3969/j.issn.1671-1122.2024.01.015
Previous Articles Next Articles
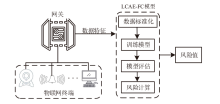
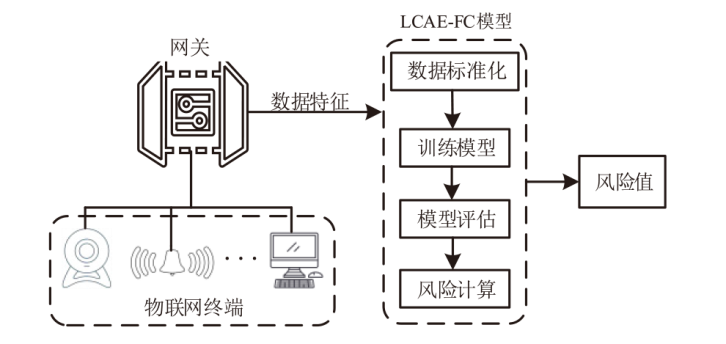
IoT Terminal Risk Assessment Model Based on Improved CAE
WANG Junyan1, YI Peng2, JIA Hongyong1( ), ZHANG Jianhui1,3
), ZHANG Jianhui1,3
- 1. School of Cyber Science and Engineering, Zhengzhou University, Zhengzhou 450001, China
2. Institute of Information Technology, PLA Strategic Support Force Information Engineering University, Zhengzhou, 450001, China
3. Songshan Laboratory, Zhengzhou 450001, China
-
Received:2023-08-12Online:2024-01-10Published:2024-01-24 -
Contact:JIA Hongyong E-mail:hyjia@zzu.edu.cn
CLC Number:
Cite this article
WANG Junyan, YI Peng, JIA Hongyong, ZHANG Jianhui. IoT Terminal Risk Assessment Model Based on Improved CAE[J]. Netinfo Security, 2024, 24(1): 150-159.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.01.015
| 数据来源 | 数据 | 统计量 | 总数/个 |
|---|---|---|---|
| Source IP | Packet size(only outbound) | Mean, variance | 3 |
| Packet count(only outbound) | Integer | ||
| Source MAC-IP | Packet size(only outbound) | Mean, variance | 3 |
| Packet count | Integer | ||
| Channel | Packet size(only outbound) | Mean, variance | 10 |
| Packet count | Integer | ||
| Amount of time betweenpacket arrivals | Mean, variance, | ||
| Packet size(both inbound and outbound) | Magnitude, radius, covariance, correlation coefficient | ||
| Socket | Packet size(only outbound) | Mean, variance | 7 |
| Packet count | Integer | ||
| Packet size(both inbound and outbound) | Magnitude, radius, covariance, correlation coefficient |
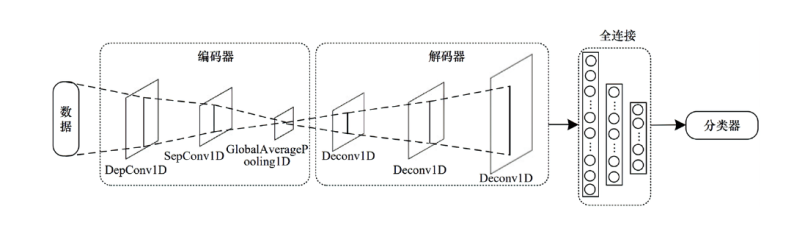
| 层 | 各层输出大小 | 参数量/个 |
|---|---|---|
| Input1 | (115,0) | 0 |
| DephwiseConv1D | (115,1) | 129 |
| SeparableConv1D | (115,32) | 96 |
| GlobalAveragePooling1D | (None,32) | 0 |
| Deconv1DTranspose | (115,32) | 2080 |
| Deconv1DTranspose | (115,64) | 4160 |
| Deconv1DTranspose | (115,115) | 14835 |
| Flatten | (None,32) | 0 |
| Dense | (None,115) | 3795 |
| Dense | (None,64) | 7424 |
| Dense | (None,32) | 2080 |
| Dense | (None,1) | 33 |
| 合计 | — | 34632 |
| 层 | 参数设置 |
|---|---|
| DephwiseConv1D | Kernel_size:2,num_filters:64,activation:relu,padding: same |
| SeparableConv1D | Kernel_size:2,num_filters:32, activation:relu,padding: same |
| GlobalAveragePooling1D | data_format=channels_last |
| Conv1DTranspose | filters=32, kernel_size=2, activation=relu padding=same, |
| Conv1DTranspose | filters=64, kernel_size=2, activation=relupadding=same, |
| Conv1DTranspose | filters=115, kernel_size=2, padding=same, activation=linear |
| Dense | activation=relu |
| Dense | activation=relu |
| Dense | activation=relu |
| Dense | activation=sigmoid |
| epoch | 200 |
| batch_size | 100 |
| 层 | 各层输出大小 | 参数/个 |
|---|---|---|
| Input1 | (115,0) | 0 |
| Conv1D | (115,64) | 14784 |
| MaxPooling1D | (57, 64) | 0 |
| Conv1D | (57, 32) | 4128 |
| MaxPooling1D | (28, 32) | 0 |
| Deconv1D | (28, 32) | 2080 |
| UpSampling1D | (57, 32) | 0 |
| Deconv1D | (57,64) | 4160 |
| UpSampling1D | (115,64) | 0 |
| Deconv1D | (115,115) | 14755 |
| Flatten | (None,32) | 0 |
| Dense | (115,0) | 1539115 |
| Dense | (None,64) | 741504 |
| Dense | (None,32) | 2080 |
| Dense | (None,1) | 33 |
| 合计 | — | 2322639 |
| [1] | LIN Meiyu, WANG Yazhong. Research on Security Capability of IoT Terminal[J]. Information and Communication Technology and Policy, 2020, (10): 93-96. |
| 林美玉, 王亚忠. 物联网终端安全能力研究[J]. 信息通信技术与政策, 2020, (10): 93-96. | |
| [2] | CHEN Lin, CUI Tao. Research on Terminal Security in Massive Machine Communication Scenarios[J]. Information and Communication Technology and Policy, 2021, (12): 93-96. |
| 陈琳, 崔涛. 海量机器类通信场景终端安全问题研究[J]. 信息通信技术与政策, 2021, (12): 93-96. | |
| [3] |
MARUDHADEVI D, DHATCHAYANI V N, SRIRAM V S S. A Trust Evaluation Model for Cloud Computing Using Service Level Agreement[J]. The Computer Journal, 2014, 58(10): 2225-2232.
doi: 10.1093/comjnl/bxu129 URL |
| [4] | JOSANG A. Subjective Logic: A Formalism for Reasoning Under Uncertainty[M]. Springer: Nature, 2016. |
| [5] | FENG Jingyu, YU Tingting, WANG Ziying, et al. Edge Zero Trust Model Against Lost Terminal Threat in Power Iot Scenario[J]. Journal of Computer Research and Development, 2022, 59(5): 1120-1132. |
| 冯景瑜, 于婷婷, 王梓莹, 等. 电力物联场景下抗失陷终端威胁的边缘零信任模型[J]. 计算机研究与发展, 2022, 59(5): 1120-1132. | |
| [6] | WANG Jingwen, JING Xuyang, YAN Zhengyan, et al. A Survey on Trust Evaluation Based on Machine Learning[J]. ACM Computing Surveys, 2020, 53(5): 1-36. |
| [7] | ALHANDI S A, KAMALUDIN H, ALDUAIS N A M. Trust Evaluation Model in IoT Environment: A Comprehensive Survey[J]. IEEE Access, 2023: 11165-11182 |
| [8] | TANG Xianzhi, DING Chunyan. Information Security Terminal Architecture of Power Transportation Mobile Internet of Things Based on Big Data Analysis[J]. Wireless Communications and Mobile Computing, 2021, 2021: 1-9. |
| [9] | ZHAO Yifan. Application of Machine Learning in Network Security Situational Awareness[C]// IEEE.2021 World Conference on Computing and Communication Technologies. New York: IEEE, 2021: 39-46. |
| [10] |
ABBASI M, SHAHRAKI A, TAHERKORDI A. Deep Learning for Network Traffic Monitoring and Analysis (NTMA): A Survey[J]. Computer Communications, 2021, 170: 19-41.
doi: 10.1016/j.comcom.2021.01.021 URL |
| [11] | LI Da, FUXingzhen, ZANYanzhu. MPTEM: A Reliable Trust Evaluation Model for Forest IoT System[C]/IEEE. 2022 7th International Conference on Computer and Communication Systems. New York: IEEE, 2022: 690-694. |
| [12] | BERGAMASCO L, SAHA S, BOVOLO F, et al. Unsupervised Change-Detection Based on Convolutional-Autoencoder Feature Extraction[C]// SPIE. 2019, Image and Signal Processing for Remote Sensing XXV. Edinburgh: SPIE, 2019: 352-332. |
| [13] |
JAYASINGHE U, LEE G M, UM T-W, et al. Machine Learning Based Trust Computational Model for IoT Services[J]. IEEE Transactions on Sustainable Computing, 2019, 4(1): 39-52.
doi: 10.1109/TSUSC.2018.2839623 URL |
| [14] | HE Chaoxun, PENG Weifeng, LI Yanfei, et al. Improved on Service Trust Model Based on Machine Learning[J]. Computer Engineering and Design, 2022(5): 1335-1343. |
| 何超勋, 彭伟锋, 李燕飞, 等. 基于机器学习的改进型物联网服务信任模型[J]. 计算机工程与设计, 2022(5): 1335-1343. | |
| [15] | LIAO Junkai, CHENG Yongxin, ZHANG Jianhui. Construction of Access Control System Based on Dynamic Trust[J]. Communications Technology, 2022(4): 473-479. |
| 廖竣锴, 程永新, 张建辉. 基于动态信任的接入管控体系构建[J]. 通信技术, 2022(4): 473-479. | |
| [16] |
LIU Liang, XU Xiangyu, LIU Yulei, et al. A Detection Framework Against CPMA Attack Based on Trust Evaluation and Machine Learning in IoT Network[J]. IEEE Internet of Things Journal, 2021, 8(20): 15249-15258.
doi: 10.1109/JIOT.2020.3047642 URL |
| [17] | KHAN M A, ALGHAMDI N S. A Neutrosophic WPM-Based Machine Learning Model for Device Trust in Industrial Internet of Things[J]. Journal of Ambient Intelligence and Humanized Computing, 2023: 3003-3017 |
| [18] | FRAGKOS G, JOHNSON J, TSIROPOULOU E. Dynamic Role-Based Access Control Policy for Smart Grid Applications: An Offline Deep Reinforcement Learning Approach[J]. IEEE Transactions on Human-Machine Systems, 2022: 1-13. |
| [19] |
ALGHOFAILI Y, RASSAM M A. A Trust Management Model for IoT Devices and Services Based on the Multi-Criteria Decision-Making Approach and Deep Long Short-Term Memory Technique[J]. Sensors, 2022, 22(2): 634-660.
doi: 10.3390/s22020634 URL |
| [20] |
MA Wei, WANG Xing, HU Mingsheng, et al. Machine Learning Empowered Trust Evaluation Method for IoT Devices[J]. IEEE Access, 2021, 9: 65066-65077.
doi: 10.1109/ACCESS.2021.3076118 URL |
| [21] |
RAO M, CHAUDHARY P, SHEORAN K, et al. A Secure Routing Protocol Using Hybrid Deep Regression Based Trust Evaluation and Clustering for Mobile Ad-Hoc Network[J]. Peer-to-Peer Networking and Applications, 2023, 16(6): 2794-2810.
doi: 10.1007/s12083-023-01560-3 |
| [22] |
MEIDAN Y, BOHADANA M, MATHOV Y, et al. N-Baiot—Network-Based Detection of IoT Botnet Attacks Using Deep Autoencoders[J]. IEEE Pervasive Computing, 2018, 17(3): 12-22.
doi: 10.1109/MPRV.2018.03367731 URL |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||