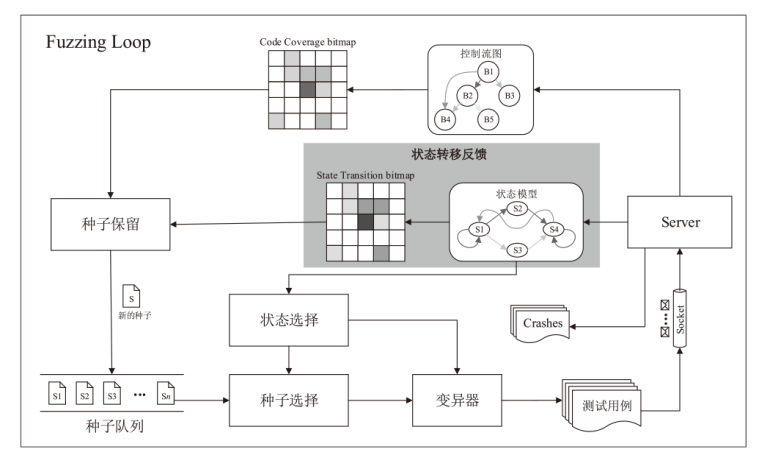
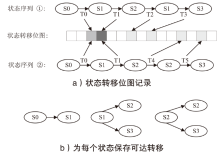
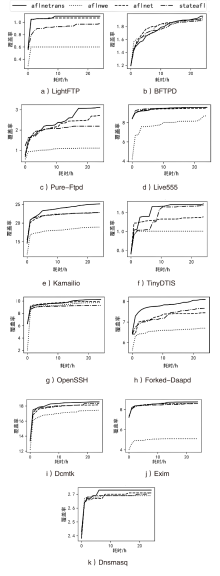
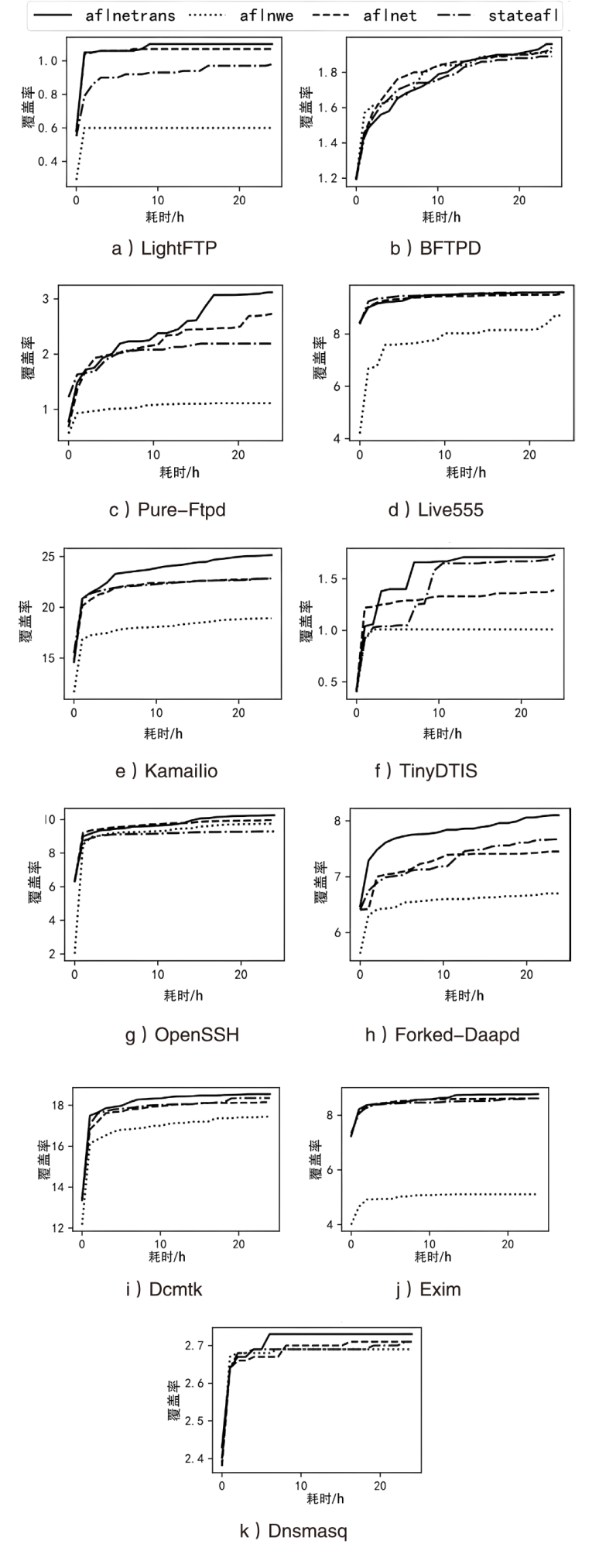
Netinfo Security ›› 2024, Vol. 24 ›› Issue (1): 121-132.doi: 10.3969/j.issn.1671-1122.2024.01.012
Previous Articles Next Articles
AFLNeTrans: Fuzzing of Protocols with State Relationship Awareness
HONG Xuanquan, JIA Peng( ), LIU Jiayong
), LIU Jiayong
- School of Cyber Science and Engineering, Sichuan University, Chengdu 610065, China
-
Received:2023-09-04Online:2024-01-10Published:2024-01-24 -
Contact:JIA Peng E-mail:pengjia@scu.edu.cn
CLC Number:
Cite this article
HONG Xuanquan, JIA Peng, LIU Jiayong. AFLNeTrans: Fuzzing of Protocols with State Relationship Awareness[J]. Netinfo Security, 2024, 24(1): 121-132.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.01.012
| 软件 | AFLNET/个 | AFLNWE/个 | StateAFL/个 | AFLNeTrans/个 |
|---|---|---|---|---|
| LightFTP | 0 | 0(-) | 0 | 0(-) |
| BTFPD | 33 | 38(15.2↑) | 40(21.2%↑) | 47(42.4%↑) |
| Pure-Ftpd | 0 | 0(-) | 0(-) | 0(-) |
| Live555 | 160 | 95(40.6%↓) | 207(29.4%↑) | 165(3.12%↑) |
| Kamailio | 1 | 0(100%↓) | 0(100%↓) | 6(500%↑) |
| TinyDTLS | 33 | 23(30.3%↓) | 35(6.1%↑) | 47(42.4%↑) |
| OpenSSH | 0 | 0(-) | 0(-) | 0(-) |
| Forked-daapd | 0 | 0(-) | 0(-) | 0(-) |
| Dcmtk | 14 | 0(100%↓) | 17(21.4%↑) | 20(42.9%↑) |
| Exim | 0 | 0(-) | 0(-) | 0(-) |
| Dnsmasq | 40 | 35(12.5%↓) | 45(12.5%↑) | 46(15.0%↑) |
| 共计 | 281 | 191(39.2%↓) | 344(22.4%↑) | 331(17.8%↑) |
| [1] | LIU Jian, SU Purui, YANG Min, et al. Software and Cyber Security-A Survey[J]. Journal of Software, 2018, 29(1): 42-68. |
| 刘剑, 苏璞睿, 杨珉, 等. 软件与网络安全研究综述[J]. 软件学报, 2018, 29(1): 42-68. | |
| [2] | BEYONDT. Microsoft Vulnerabilities Report 2023[EB/OL]. [2023-08-26]. https://assets.beyondtrust.com/assets/documents/2023-Microsoft-Vulnerability-Report_BeyondTrust.pdf. |
| [3] | CARVALHO M, DeMott J, FORD R, et al. Heartbleed 101[J]. IEEE Security & Privacy, 2014, 12(4): 63-67. |
| [4] | GOODIN D. NSA-Leaking Shadow Brokers Just Dumped Its Most Damaging Release Yet[EB/OL]. (2017-04-15) [2023-08-26]. https://arstechnica.com/security/2017/04/nsa-leaking-shadow-brokers-just-dumped-its-most-damaging-release-yet/. |
| [5] | MICHAL Z. AFL(American Fuzzy Lop)[EB/OL]. [2023-08-26] https://github.com/google/AFL. |
| [6] | LLVM Organization. Libfuzzer- A Library for Coverage-Guided Fuzz Testing[EB/OL]. [2023-08-26]. https://llvm.org/docs/LibFuzzer.html. |
| [7] | GOOGLE Inc. HonggFuzz: A Security-Oriented, Feedback-Driven, Evolutionary, Easy-to-Use Fuzzer with Interesting Analysis Options[EB/OL]. [2023-08-26]. https://github.com/google/honggfuzz. |
| [8] | MICHAEL E. Peach Fuzzing Platform[EB/OL]. [2023-08-26]. https://gitlab.com/peachtech/peach-fuzzer-community. |
| [9] | JTPEREYDA. Boofuzz: Network Protocol Fuzzing for Humans[EB/OL]. [2023-08-26]. https://github.com/jtpereyda/boofuzz. |
| [10] | PHAM V, BÖHME M, ROYCHOUDHURY A. AFLNet: A Greybox Fuzzer for Network Protocols[C]// IEEE. 2020 IEEE 13th International Conference on Software Testing, Validation and Verification (ICST). New York: IEEE, 2020: 460-465. |
| [11] | WIKIPEDIA. Multi-Armed Bandit Problem[EB/OL]. [2023-08-26]. https://en.wikipedia.org/wiki/Multi-armed_bandit. |
| [12] | KULESHOV V, PRECUP D. Algorithms for Multi-Armed Bandit Problems[EB/OL]. (2014-02-25) [2023-08-26]. https://doi.org/10.48550/arXiv.1402.6028. |
| [13] | BÖHME M, PHAM V T, ROYCHOUDHURY A. Coverage-Based Greybox Fuzzing as Markov Chain[C]// ACM. Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 1032-1043. |
| [14] | GAN Shuitao, ZHANG Chao, QIN Xiaojun, et al. Collafl: Path Sensitive Fuzzing[C]// IEEE. 2018 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2018: 679-696. |
| [15] | LYU Chenyang, JI Shouling, ZHANG Chao, et al. MOPT: Optimized Mutation Scheduling for Fuzzers[C]// USENIX. USENIX Security Symposium. New York: USENIX Association, 2019: 1949-1966. |
| [16] | WANG Yanhao, JIA Xiangkun, LIU Yuwei, et al. Not All Coverage Measurements Are Equal: Fuzzing by Coverage Accounting for Input Prioritization[C]// USENIX. Network and Distributed System Security 2020 (NDSS 2020). New York: USENIX Association, 2020: 1-20. |
| [17] | GAN Shuitao, ZHANG Chao, CHEN Peng, et al. GREYONE: Data Flow Sensitive Fuzzing[C]// USENIX. USENIX Security Symposium. New York: USENIX Association, 2020: 2577-2594. |
| [18] | YUN I, LEE S, XU Meng, et al. QSYM: A Practical Concolic Execution Engine Tailored for Hybrid Fuzzing[C]// USENIX. 27th USENIX Security Symposium (USENIX Security 2018). New York: USENIX Association, 2018: 745-761. |
| [19] | CORNELIUS A, SERGEJ S, ALI A, et al. Ijon: Exploring Deep State Spaces via Fuzzing[C]// IEEE. 2020 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2020: 1597-1612. |
| [20] | PEDRAM A. Sulley: A Pure-Python Fully Automated and Unattended Fuzzing Framework[EB/OL]. (2019-02-15) [2023-08-26]. https://github.com/OpenRCE/sulley. |
| [21] | THUAN P. AFLNWE[EB/OL]. (2020-10-01) [2023-08-26]. https://github.com/thuanpv/aflnwe. |
| [22] | LIU Dongge, PHAM V T, ERNST G, et al. State Selection Algorithms and Their Impact on The Performance of Stateful Network Protocol Fuzzing[C]// IEEE. 2022 IEEE International Conference on Software Analysis, Evolution and Reengineering (SANER). New York: IEEE, 2022: 720-730. |
| [23] |
NATELLA R. StateAFL: Greybox Fuzzing for Stateful Network Servers[J]. Empirical Software Engineering, 2022, 27(7): 1-12.
doi: 10.1007/s10664-021-10043-z |
| [24] |
LI Junqiang, LI Senyi, SUN Gang, et al. SNPSFuzzer: A Fast Greybox Fuzzer for Stateful Network Protocols Using Snapshots[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 2673-2687.
doi: 10.1109/TIFS.2022.3192991 URL |
| [25] | ANDRONIDIS A, CADAR C. SnapFuzz: High-Throughput Fuzzing of Network Applications[C]// ACM. Proceedings of the 31st ACM SIGSOFT International Symposium on Software Testing and Analysis. New York: ACM, 2022: 340-351. |
| [26] | BA J, BÖHME M, MIRZAMOMEN Z, et al. Stateful Greybox Fuzzing[C]// USENIX. 31st USENIX Security Symposium (USENIX Security 22). New York: USENIX Association, 2022: 3255-3272. |
| [27] | QIN Shisong, HU Fan, MA Zheyu, et al. NSFuzz: Towards Efficient and State-Aware Network Service Fuzzing[J]. ACM Transactions on Software Engineering and Methodology, 2023, 32(6): 1-26. |
| [28] | WUNDER M, LITTMAN M L, BABES M. Classes of Multiagent Q-learning Dynamics with Epsilon-greedy Exploration[C]// ICML. Proceedings of the 27th International Conference on Machine Learning (ICML-10). New York: ICML, 2010: 1167-1174. |
| [29] | LIU Yahui, CAO Buyang, LI Hehua. Improving Ant Colony Optimization Algorithm with Epsilon Greedy and Levy Flight[J]. Complex & Intelligent Systems, 2021, 7: 1711-1722. |
| [30] | NATELLA R, PHAM V T. PROFUZZBENCH: A Benchmark for Stateful Protocol Fuzzing[C]// ACM. Proceedings of the 30th ACM SIGSOFT International Symposium on Software Testing and Analysis. New York: ACM, 2021: 662-665. |
| [31] | HFIREF0X. LightFTP[EB/OL]. (2023-07-22) [2023-08-26]. https://github.com/hfiref0x/LightFTP. |
| [32] | ROMAN G. Live555[EB/OL]. (2023-06-15) [2023-08-26]. https://github.com/rgaufman/live555. |
| [33] | DANIEL M. Kamailio-The Open Source SIP Server for Large VoIP and Real-time Communication Platforms[EB/OL].(2023-06-15) [2023-08-26]. https://github.com/rgaufman/live555. |
| [34] | CONTIKI. TinyDTLS[EB/OL]. (2022-09-13) [2023-08-26]. https://github.com/eclipse/tinydtls. |
| [35] | JESSEFRGSMITH. BFTPD[EB/OL]. [2023-08-26]. https://bftpd.sourceforge.net/index.html. |
| [36] | FRANK D. Pure-Ftpd[EB/OL]. (2022-10-01) [2023-08-26]. https://github.com/jedisct1/pure-ftpd. |
| [37] | DAMIEN M. OpenSSH-Portable[EB/OL]. [2023-08-26]. https://github.com/openssh/openssh-portable. |
| [38] | EJURGENSEN. Forked-Daapd[EB/OL]. [2023-08-26]. https://github.com/owntone/owntone-server. |
| [39] | RIESMEIER J. Dcmtk[EB/OL]. [2023-08-26]. https://github.com/Exim/exim. |
| [40] | PHIL P. Exim[EB/OL]. [2023-08-26]. https://github.com/Exim/exim. |
| [41] | SIMON K. Dnsmasq[EB/OL]. [2023-08-26]. https://thekelleys.org.uk/dnsmasq/. |
| [42] | SEREBRYANY K, BRUENING D, POTAPENKO A, et al. Addresssanitizer: A Fast Address Sanity Checker[C]// USENIX. USENIX Annual Technical Conference 2012. New York: USENIX Association, 2012: 1-10. |
| [1] | WANG Juan, ZHANG Chong, GONG Jiaxin, LI Jun’e. Review of Fuzzing Based on Machine Learning [J]. Netinfo Security, 2023, 23(8): 1-16. |
| [2] | ZHONG Yuanxin, LIU Jiayong, JIA Peng. Directed Fuzzing Based on Dynamic Time Slicing and Efficient Mutation [J]. Netinfo Security, 2023, 23(8): 99-108. |
| [3] | WU Jiaming, XIONG Yan, HUANG Wenchao, WU Jianshuang. A Distance-based Fuzzing Mutation Method [J]. Netinfo Security, 2021, 21(10): 63-68. |
| [4] | Yue ZHOU, Wei WANG, Jianhong GUO, Jingsha HE. Defensive Software Testing Service System Based on Cloud Platform [J]. Netinfo Security, 2018, 18(12): 46-53. |
| [5] | Xiajing WANG, Changzhen HU, Rui MA, Xinzhu GAO. A Survey of the Key Technology of Binary Program Vulnerability Discovery [J]. Netinfo Security, 2017, 17(8): 1-13. |
| [6] | Jian QI, Xiaoming CHEN, Weiqing YOU. Research on the Method of Network Protocol Security Evaluation Based on Fuzzing Test [J]. Netinfo Security, 2017, 17(3): 59-65. |
| [7] | Liang GUO, Senlin LUO, Limin PAN. Research on Network Protocol Test Data Generation Method Based on Cross Location of Encoding Function [J]. Netinfo Security, 2016, 16(3): 8-14. |
| [8] | Ji-zhou FENG, Ming-hui TIAN. Research on the Software Security Testing for Potential Defects [J]. Netinfo Security, 2015, 15(6): 85-90. |
| [9] | . The Design and Implementation of An Analysis System of Network Protocol [J]. , 2014, 14(7): 48-. |
| [10] | . Design and Implementation of Network Protocol Auto Vulnerability Mining Tool based on Fuzzing [J]. , 2014, 14(6): 23-. |
| [11] | . The Summary of Fuzzing Testing Technology [J]. , 2014, 14(3): 0-0. |
| [12] | . The Summary of Fuzzing Testing Technology [J]. , 2014, 14(3): 87-. |
| [13] | . Based on the FUZZING Lead to a New Mining Method Based on Windows Kernel Vulnerability [J]. , 2011, 11(12): 0-0. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||