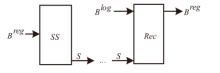
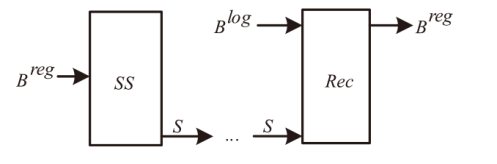
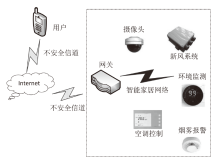
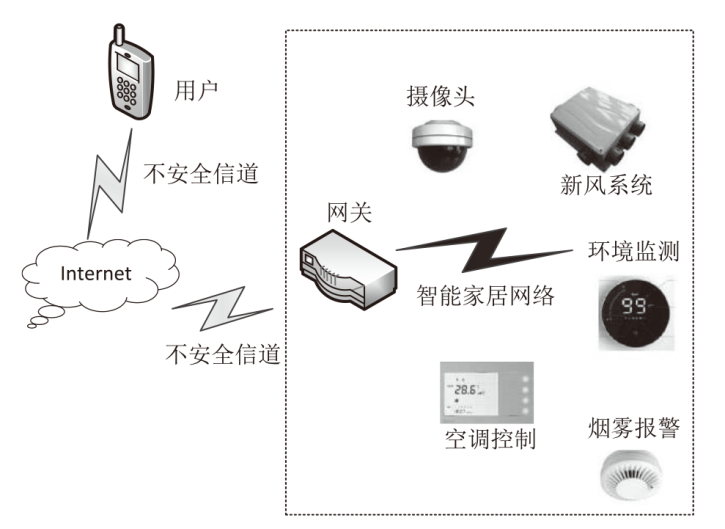
Netinfo Security ›› 2024, Vol. 24 ›› Issue (1): 133-142.doi: 10.3969/j.issn.1671-1122.2024.01.013
Previous Articles Next Articles
Research on Multi-Factor Authenticated Key Agreement Protocol for Smart Home Networks
ZHANG Min1,2, FENG Yongqiang3,4, XU Chunxiang1, ZHANG Jianhua2( )
)
- 1. School of Cyberspace Security, University of Electronic Science and Technology of China, Chengdu 611731, China
2. School of Computer Science and Engineer, Southwest Minzu University, Chengdu 610225, China
3. PipeChina North Pipeline Company, Langfang 065000, China
4. Northeast Petroleum University, Daqing 163318, China
-
Received:2023-10-22Online:2024-01-10Published:2024-01-24 -
Contact:ZHANG Jianhua E-mail:xnmdzjh@swun.edu.cn
CLC Number:
Cite this article
ZHANG Min, FENG Yongqiang, XU Chunxiang, ZHANG Jianhua. Research on Multi-Factor Authenticated Key Agreement Protocol for Smart Home Networks[J]. Netinfo Security, 2024, 24(1): 133-142.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.01.013
| 用户端/ms | 智能家居设备/ms | GWN/ms | 合计/ms | |
|---|---|---|---|---|
| Wazid-Das 方案 | ||||
| FAR[ 等人方案 | ||||
| LI[ 等人方案 | ||||
| ZOU[ 等人方案 | ||||
| 本文方案 |
| 用户端/bit | 智能家居设备/bit | GWN/bit | 合计/bit | |
|---|---|---|---|---|
| Wazid-Das 方案 | LID+2LH+LT=480 | 3LH+LT=512 | 2LE+3LH+ 3LT=1088 | 2088 |
| FAR[ 等人方案 | 3LH+3LP=960 | 3LH=480 | 6Lh+LP+ 2LR=1440 | 2944 |
| LI[ 等人方案 | 3LH+LP=640 | 4LH+2LP=960 | 2LH+LP=480 | 2080 |
| ZOU[ 等人方案 | LID+2LH+LT+ LP+LR=800 | 4LH+LT+ LP=832 | 2LID+4LH+ LT+LP+LR=1248 | 2880 |
| 本文方案 | LM+LT+ 4LH=800 | LE+LT+ LH+LM=576 | LE=256 | 1600 |
| [1] | JEONG J, CHUNG M Y, CHOO H. Integrated OTP-Based User Authentication Scheme Using Smart Cards in Home Networks[C]// IEEE. The 41st Annual Hawaii International Conference on System Sciences(HICSS 2008). New York: IEEE, 2008: 123-133. |
| [2] |
VAIDYA B, PARK J H, YEO S, et al. Robust One-Time Password Authentication Scheme Using Smart Card for Home Network Environment[J]. Computer Communications, 2011, 34(3): 326-336.
doi: 10.1016/j.comcom.2010.03.013 URL |
| [3] | KIM H J, KIM H S. AUTHHOTP-HOTP Based Authentication Scheme over Home Network Environment[C]// Springer. International Conference on Computational Science and Its Applications. Heidelberg: Springer, 2011: 622-637. |
| [4] | HANUMANTHAPPA P, SINGH S. Privacy Preserving and Ownership Authentication in Ubiquitous Computing Devices Using Secure Three Way Authentication[C]// IEEE. 2012 International Conference on Innovations in Information Technology(IIT). New York: IEEE, 2012: 107-112. |
| [5] |
KUMAR P, GURTOV A, IINATTI J, et al. Lightweight and Secure Session-Key Establishment Scheme in Smart Home Environments[J]. IEEE Sensors Journal, 2016, 16(1): 254-264.
doi: 10.1109/JSEN.2015.2475298 URL |
| [6] | VISHWAKARMA S K, UPADHYAYA P, KUMARI B, et al. Smart Energy Efficient Home Automation System Using IoT[C]// IEEE. 4th International Conference on Internet of Things:Smart Innovation and Usages(IoT-SIU). New York: IEEE, 2019: 1-4. |
| [7] |
WAZID M, DAS A K, ODELU V, et al. Secure Remote User Authenticated Key Establishment Protocol for Smart Home Environment[J]. IEEE Transactions on Dependable and Secure Computing, 2020, 17(2): 391-406.
doi: 10.1109/TDSC.8858 URL |
| [8] |
SAHOO S S, MOHANTY S, SAHOO K S, et al. A Three-Factor-Based Authentication Scheme of 5G Wireless Sensor Networks for IoT System[J]. IEEE Internet of Things Journal, 2023, 10(17): 15087-15099.
doi: 10.1109/JIOT.2023.3264565 URL |
| [9] | ZHANG Min, XU Chunxiang, ZHANG Jianhua. Research on Authentication Key Agreement Protocol Based on Multi-Factor in Internet of Drones[J]. Netinfo Security, 2022, 22(9): 21-30. |
| 张敏, 许春香, 张建华. 无人机网络中基于多因子的认证密钥协商协议研究[J]. 信息网络安全, 2022, 22(9):21-30. | |
| [10] | DODIS Y, REYZIN L, SMITH A. Fuzzy Extractors: How to Generate Strong Keys from Biometrics and Other Noisy Data[C]// Springer. EUROCRYPT 2004. Heidelberg: Springer, 2004: 524-540. |
| [11] | RIVLIN T J. Chebyshev Polynomials[M]. New York: Courier Dover Publications, 2020. |
| [12] |
ZHANG Linhua. Cryptanalysis of the Public Key Encryption Based on Multiple Chaotic Systems[J]. Chaos Solitons & Fractals, 2008, 37(3): 669-674.
doi: 10.1016/j.chaos.2006.09.047 URL |
| [13] | ZHU Yixin, MIAO Zhangwang, GAN Jinghong, et al. Design of Ransomware Defense System Based on Fine-Grained Access Control Scheme[J]. Netinfo Security, 2023, 23(10): 31-38. |
| 朱怡昕, 苗张旺, 甘静鸿, 等. 基于细粒度访问控制的勒索软件防御系统设计[J]. 信息网络安全, 2023, 23(10):31-38. | |
| [14] | GAO Bo, CHEN Lin, YAN Yingjian. Research on Side Channel Attack Based on CNN-MGU[J]. Netinfo Security, 2022, 22(8): 55-63. |
| 高博, 陈琳, 严迎建. 基于CNN-MGU的侧信道攻击研究[J]. 信息网络安全, 2022, 22(8):55-63. | |
| [15] |
FAR H, BAYAT M, DAS A K, et al. Pournaghi, and M. Doostari, LAPTAS: Lightweight Anonymous Privacy-Preserving Three-Factor Authentication Scheme for WSN-Based IIoT[J]. Wireless Network, 2021, 27(2): 1389-1412.
doi: 10.1007/s11276-020-02523-9 |
| [16] |
LI Xiong, PENG Jieyao, OBAIDAT M S, et al. A Secure Three-Factor User Authentication Protocol With Forward Secrecy for Wireless Medical Sensor Network Systems[J]. IEEE Systems Journal, 2020, 14(1): 39-50.
doi: 10.1109/JSYST.4267003 URL |
| [17] |
ZOU Shihong, CAO Qiang, WANG Chenxu. A Robust Two-Factor User Authentication Scheme-Based ECC for Smart Home in IoT[J]. IEEE Systems Journal, 2022, 16(3): 4938-4949.
doi: 10.1109/JSYST.2021.3127438 URL |
| [1] | ZHANG Min, XU Chunxiang, ZHANG Jianhua. Research on Authentication Key Agreement Protocol Based on Multi-Factor in Internet of Drones [J]. Netinfo Security, 2022, 22(9): 21-30. |
| [2] | WANG Shushuang, MA Zhaofeng, LIU Jiawei, LUO Shoushan. Research and Implementation of Cross-Chain Security Access and Identity Authentication Scheme of Blockchain [J]. Netinfo Security, 2022, 22(6): 61-72. |
| [3] | SHEN Yan, YAO Mengmeng. Research on Formal Analysis Based on Event of Group Key Agreement Protocol [J]. Netinfo Security, 2022, 22(5): 30-36. |
| [4] | WU Kehe, CHENG Rui, ZHENG Bihuang, CUI Wenchao. Research on Security Communication Protocol of Power Internet of Things [J]. Netinfo Security, 2021, 21(9): 8-15. |
| [5] | DONG Qiang, LUO Guoming, SHI Hongkui, ZHANG Yongyue. Research on Authentication and Key Agreement Method of IMS-based Mobile Communication Private Network [J]. Netinfo Security, 2021, 21(1): 88-96. |
| [6] | ZHANG Xiao, LIU Jiqiang. Multi-factor Authentication Protocol Based on Hardware Fingerprint and Biometrics [J]. Netinfo Security, 2020, 20(8): 9-15. |
| [7] | ZHAO Guofeng, ZHOU Wentao, XU Chuan, XU Lei. A Secure Identity Authentication Scheme for Space-ground Integrated Network Based on Bilinear Pairing [J]. Netinfo Security, 2020, 20(12): 33-39. |
| [8] | Ruiying CHEN, Zemao CHEN, Hao WANG. Design and Optimization of Security Monitoring and Controlling Protocol in Industrial Control Systems [J]. Netinfo Security, 2019, 19(2): 60-69. |
| [9] | Min ZHANG, Chunxiang XU, Minying HUANG. Research on Multi-server Lightweight Multi-factor Authentication Protocol in Telemedicine Environment [J]. Netinfo Security, 2019, 19(10): 42-49. |
| [10] | Qingfeng CHENG, Zhanjing RUAN, Ruijie ZHANG. Analysis of Three Pairing-free Authenticated Key Agreement Protocols [J]. Netinfo Security, 2019, 19(1): 16-26. |
| [11] | Jian ZHAO, Rui WANG, Siqi LI. Research on Smart Home Vulnerability Mining Technology Based on Taint Analysis [J]. Netinfo Security, 2018, 18(6): 36-44. |
| [12] | Baoyuan KANG, Jiaqiang WANG, Dongyang SHAO, Chunqing LI. A Secure Authentication and Key Agreement Protocol for Heterogeneous Ad Hoc Wireless Sensor Networks [J]. Netinfo Security, 2018, 18(1): 23-30. |
| [13] | SHI Jinjing, CHENG Jiajing, CHEN Hui, ZHOU Fang. Quantum Key Agreement Protocol Based on Bell Measurement and Three-particle Entanglement [J]. 信息网络安全, 2017, 17(6): 56-61. |
| [14] | Chunming TANG, Long GAO. Multi-parties Key Agreement Protocol in Block Chain [J]. Netinfo Security, 2017, 17(12): 17-21. |
| [15] | Liu WANG, Zhenfu CAO, Xiaolei DONG. Research on Application of ID-based Designated Verifier Signature in Cross-domain Authentication [J]. Netinfo Security, 2017, 17(10): 63-68. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||