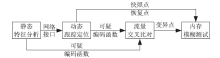
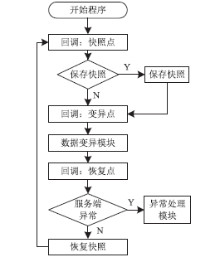
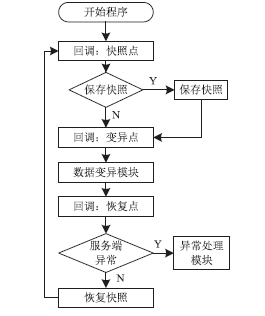
| [1] |
史记,曾昭龙,杨从保,等. Fuzzing测试技术综述[J]. 信息网络安全,2014(3):87-91.
|
| [2] |
Topsec. Alphafuzz[EB/OL]. .
|
| [3] |
Rodrigomarcos. Taof[EB/OL]. .
|
| [4] |
Michael Eddington. Peach[EB/OL]. .
|
| [5] |
王涛,胡爱群. 基于边界检测的IPSec VPN协议的一致性测试方法[J]. 信息网络安全,2014(2):7-11.
|
| [6] |
YANG Huan, ZHANG Yuqing, HU Yupu, et al.IKE Vulnerability Discovery Based on Fuzzing[J]. Security & Communication Networks, 2013, 6(7): 889-901.
|
| [7] |
LAHMADI A, BRANDIN C, FESTOR O.A Testing Framework for Discovering Vulnerabilities in 6LoWPAN Networks[C]//IEEE. 2013 IEEE International Conference on Distributed Computing in Sensor Systems, May 16-18, 2012, Hangzhou. New Jersey: IEEE, 2012: 335-340.
|
| [8] |
夏戈明,史立哲,周文,等. 轻量级RFID双向通信认证协议优化方案[J]. 信息网络安全,2014(2):58-62.
|
| [9] |
MA R, JI W, HU C, et al.Fuzz Testing Data Generation for Network Protocol Using Classification Tree[C]//CSC. Communications Security Conference 2014, May 22-24, 2014, Beijing. London: IET, 2014: 1-5.
|
| [10] |
CAI Jun, ZOU Peng, XIONG Dapeng, et al.A Guided Fuzzing Approach for Security Testing of Network Protocol Software[C]//IEEE. 6th IEEE International Conference on Software Engineering and Service Science (ICSESS), September 23-25, 2015, Beijing. New Jersey: IEEE, 2015: 726-729.
|
| [11] |
CABALLERO J, JOHNSON N M, MCCAMANT S, et al.Binary Code Extraction and Interface Identification for Security Applications[C]//ISOC. Network and Distributed System Security Symposium, NDSS 2010, February 28-March 3, 2010, San Diego, California, USA. Virginia: ISOC, 2010: 14-21.
|
| [12] |
TSANKOV P, DASHTI M T, BASIN D.SECFUZZ: Fuzz-testing Security Protocols[C]//IEEE. Automation of Software Test (AST), 7th International Workshop on, June 2-3, 2012, Zurich. New Jersey: IEEE, 2012:1-7.
|
| [13] |
WANG Tielei, WEI Tao, GU Guofei, et al.TaintScope: A Checksum-Aware Directed Fuzzing Tool for Automatic Software Vulnerability Detection[C]//IEEE. 2010 IEEE Symposium on Security and Privacy, May 16-19, 2010, Berkeley, California, USA. New Jersey: IEEE, 2010: 497-512.
|
| [14] |
CABALLERO J, POOSANKAM P, KREIBICH C, et al.Dispatcher: Enabling Active Botnet Infiltration Using Automatic Protocol Reverse-engineering[C]//ACM. ACM Conference on Computer & Communications Security, November 9-13, 2009, Chicago, Illinois, USA. New York: ACM, 2009: 621-634.
|
| [15] |
Sion Berkowits (Intel). Pin-A Dynamic Binary Instrumentation Tool[EB/OL]. https://software.intel.com/en-us/articles/pin-a-dynamic-binary-instrumentation-tool, 2012-6-13.
|
| [16] |
孙哲,刘大光,武学礼,等. 基于模糊测试的网络协议自动化漏洞挖掘工具设计与实现[J]. 信息网络安全,2014(6):23-30.
|
 )
)