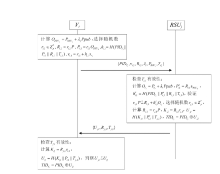
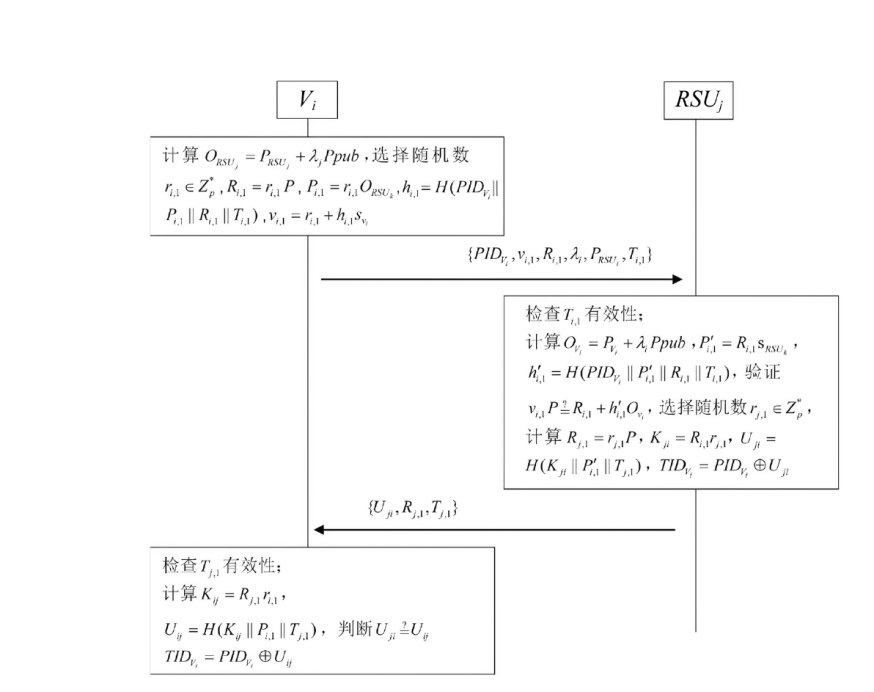
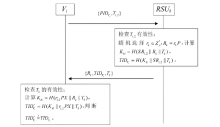
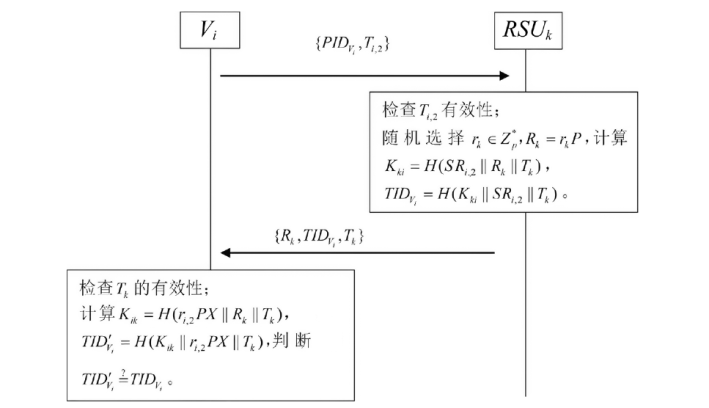
| [1] |
DUREJA A, SANGWAN S. A Review: Efficient Transportation—Future Aspects of IoV[J]. Evolving Technologies for Computing, Communication and Smart World, 2020, 694: 97-108.
|
| [2] |
FAROOQ S M, HUSSAIN S M S, USTUN T S. A Survey of Authentication Techniques in Vehicular Ad-hoc Networks[J]. IEEE Intelligent Transportation Systems Magazine, 2020, 13(2): 39-52.
doi: 10.1109/MITS.2020.2985024
URL
|
| [3] |
ZHANG Jing, CUI Jie, ZHONG Hong, et al. PA-CRT: Chinese Remainder Theorem Based Conditional Privacy-Preserving Authentication Scheme in Vehicular Ad-hoc Networks[J]. IEEE Transactions on Dependable and Secure Computing, 2019, 18(2): 722-735.
doi: 10.1109/TDSC.8858
URL
|
| [4] |
XIE Qi, DING Zixuan, ZHENG Panpan. Provably Secure and Anonymous V2I and V2V Authentication Protocol for VANETs[J]. IEEE Transactions on Intelligent Transportation Systems, 2023, 24(7): 1-10.
|
| [5] |
KUMAR P, OM H. Secure and Efficient Cache-Based Authentication Scheme for Vehicular Ad-Hoc Networks[J]. Wireless Networks, 2022, 28(7): 2821-2836.
doi: 10.1007/s11276-022-03003-y
|
| [6] |
YANG Anjia, WENG Jian, YANG Kan, et al. Delegating Authentication to Edge: A Decentralized Authentication Architecture for Vehicular Networks[J]. IEEE Transactions on Intelligent Transportation Systems, 2020, 23(2): 1284-1298.
doi: 10.1109/TITS.2020.3024000
URL
|
| [7] |
SCOTT M. On the Efficient Implementation of Pairing-Based Protocols[C]// Springer. Cryptography and Coding:13th IMA International Conference. Berlin: Springer, 2011: 296-308.
|
| [8] |
SHAH K, CHADOTRA S, TANWAR S, et al. Blockchain for IoV in 6G Environment: Review Solutions and Challenges[J]. Cluster Computing, 2022, 25(3): 1927-1955.
doi: 10.1007/s10586-021-03492-0
|
| [9] |
ANG L M, SENG K P, IJEMARU G K, et al. Deployment of IoV for Smart Cities: Applications, Architecture, and Challenges[J]. IEEE Access, 2018, 7: 6473-6492.
doi: 10.1109/ACCESS.2018.2887076
URL
|
| [10] |
KUMAR A, DAS D. EIoVChain: Towards Authentication and Secure Communication Based Blockchain for Internet of Vehicles (IoV)[C]// IEEE. 2021 IEEE International Conference on Blockchain. New York: IEEE, 2021: 47-54.
|
| [11] |
ZENG Ping, CHEN Zhijuan, MA Yingjie, et al. Blockchain-Based Privacy-Preserving Certificateless Authentication Scheme for Internet of Vehicles[J]. Application Research of Computers, 2021, 38(10): 2919-2925.
|
|
曾萍, 陈志娟, 马英杰, 等. 基于区块链的IoV隐私保护认证方案设计[J]. 计算机应用研究, 2021, 38(10): 2919-2925.
|
| [12] |
HE Daojing, CHAN S, GUIZANI M. Handover Authentication for Mobile Networks: Security and Efficiency Aspects[J]. IEEE Network, 2015, 29(3): 96-103.
doi: 10.1109/MNET.2015.7113232
URL
|
| [13] |
DWIVEDI S K, AMIN R, VOLLALA S, et al. B-HAS: Blockchain-Assisted Efficient Handover Authentication and Secure Communication Protocol in VANETs[J]. IEEE Transactions on Network Science and Engineering, 2023, 23: 1-14.
|
| [14] |
SON S, LEE J, PARK Y, et al. Design of Blockchain-Based Lightweight V2I Handover Authentication Protocol for VANET[J]. IEEE Transactions on Network Science and Engineering, 2022, 9(3): 1346-1358.
doi: 10.1109/TNSE.2022.3142287
URL
|
| [15] |
NIRANJANAMURTHY M, NITHYA B N, JAGANNATHA S. Analysis of Blockchain Technology: Pros, Cons and SWOT[J]. Cluster Computing, 2019, 22: 14743-14757.
doi: 10.1007/s10586-018-2387-5
|
| [16] |
CHEN Zewen, ZHANG Longjun, WANG Yumin, et al. A Group Signature Scheme Based on Chinese Remainder Theorem[J]. Acta Electronica Sinica, 2004, 32(7): 1062-1065.
|
|
陈泽文, 张龙军, 王育民, 等. 一种基于中国剩余定理的群签名方案[J]. 电子学报, 2004, 32(7): 1062-1065.
|
| [17] |
PANG Liaojun, PEI Qingqi, LI Huixian, et al. Secret Sharing Technology and Its Applications[M]. Beijing: Post & Telecom Press, 2017.
|
|
庞辽军, 裴庆祺, 李慧贤, 等. 秘密共享技术及其应用[M]. 北京: 人民邮电出版社, 2017.
|
| [18] |
COPPERSMITH D. Cryptography[J]. IBM Journal of Research and Development, 1987, 31(2): 244-248.
doi: 10.1147/JRD.1987.5390134
URL
|
| [19] |
KOBLITZ N, MENEZES A J. The Random Oracle Model: A Twenty-Year Retrospective[J]. Designs, Codes and Cryptography, 2015, 77: 587-610.
doi: 10.1007/s10623-015-0094-2
URL
|
| [20] |
ALIMORADI R, ARKIAN H R, RAZAVIAN S M J, et al. Scalar Multiplication in Elliptic Curve Libraries[J]. Journal of Discrete Mathematical Sciences and Cryptography, 2021, 24(3): 657-666.
doi: 10.1080/09720529.2017.1378411
URL
|