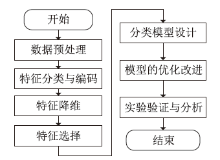
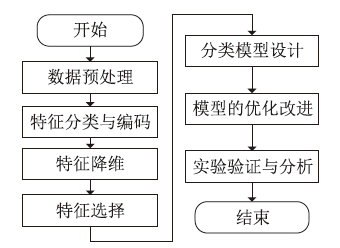
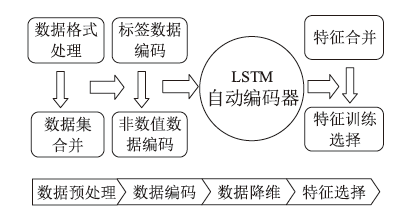
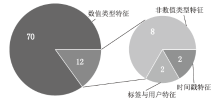
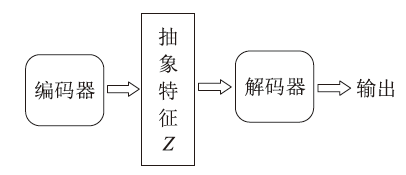
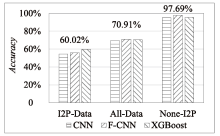
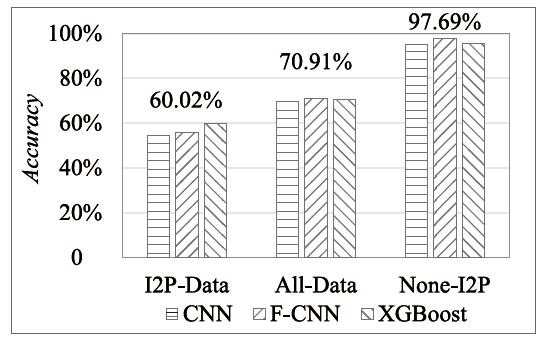
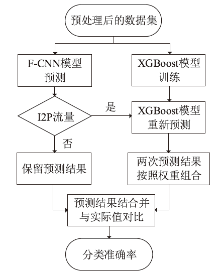
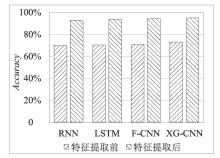
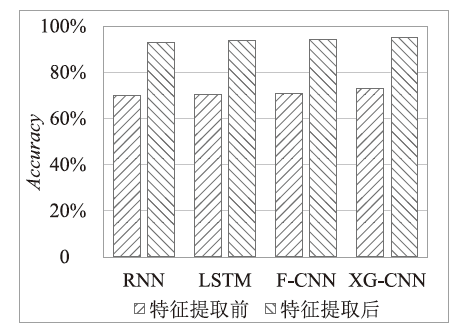
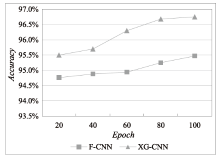
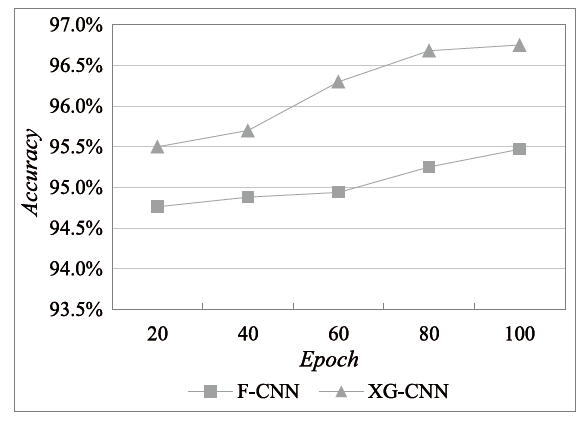
Netinfo Security ›› 2023, Vol. 23 ›› Issue (5): 1-10.doi: 10.3969/j.issn.1671-1122.2023.05.001
Previous Articles Next Articles
Research on Anonymous Traffic Classification Method Based on Machine Learning
ZHAO Xiaolin, WANG Qiyao, ZHAO Bin, XUE Jingfeng( )
)
- School of Computer Science & Technology, Beijing Institute of Technology, Beijing 100081, China
-
Received:2022-10-27Online:2023-05-10Published:2023-05-15 -
Contact:XUE Jingfeng E-mail:xuejf@bit.edu.cn
CLC Number:
Cite this article
ZHAO Xiaolin, WANG Qiyao, ZHAO Bin, XUE Jingfeng. Research on Anonymous Traffic Classification Method Based on Machine Learning[J]. Netinfo Security, 2023, 23(5): 1-10.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.05.001
| [1] | SHIN Y, YASUDA H, MAEDA K, et al. Anonymous Communication System and Method for Subscribing to Said Communication System: Japan, US15772985[P]. 2019-05-16. |
| [2] | TEAM T M. Onion Services-Tor Metrics[EB/OL]. (2018-10-01)[2022-09-27]. http://metrics.torpro ject.org. |
| [3] | CAO Shimin, WANG Juan. Review of the Special Network Traffic Identification[J]. Computer Knowledge and Technology, 2018, 14(17): 22-26, 30. |
| [4] | SINGH A, JANG-JACCARD J. Autoencoder-Based Unsupervised Intrusion Detection Using Multi-Scale Convolutional Recurrent Networks[EB/OL]. [2022-09-27]. https://doi.org/10.48550/arXiv.2204.03779. |
| [5] | WEI Songjie, LI Chenghao, SHEN Haotong, et al. Research and Application of Network Hidden Traffic Detection Method Based on Deep Forest[J]. Netinfo Security, 2022, 22(8): 64-71. |
| 魏松杰, 李成豪, 沈浩桐, 等. 基于深度森林的网络匿流量检测方法研究与应用[J]. 信息网络安全, 2022, 22(8):64-71. | |
| [6] | WANG Xirui, LU Tianliang, ZHANG Jianling, et al. Tor Anonymous Traffic Identification Method Based on Weighted Stacking Ensemble Learning[J]. Netinfo Security, 2021, 21(12): 118-125. |
| 王曦锐, 芦天亮, 张建岭, 等. 基于加权Stacking集成学习的Tor匿名流量识别方法[J]. 信息网络安全, 2021, 21(12):118-125. | |
| [7] |
THABTAH F, KAMALOV F, HAMMOUD S, et al. Least Loss: A Simplified Filter Method for Feature Selection[J]. Information Sciences, 2020, 534: 1-15.
doi: 10.1016/j.ins.2020.05.017 URL |
| [8] | ALI W. Phishing Website Detection Based on Supervised Machine Learning with Wrapper Features Selection[J]. International Journal of Advanced Computer Science and Applications, 2017, 8(9): 72-78. |
| [9] | HAMEED S S, PETINRIN O O, HASHI A O, et al. Filter-Wrapper Combination and Embedded Feature Selection for Gene Expression Data[J]. International Journal of Advances in Soft Computing and Its Applications, 2018, 10(1): 90-105. |
| [10] |
LI Zhiqin, DU Jianqiang, NIE Bin, et al. Overview of Feature Selection Methods[J]. Computer Engineering and Applications, 2019, 55(24): 10-19.
doi: 10.3778/j.issn.1002-8331.1909-0066 |
|
李郅琴, 杜建强, 聂斌, 等. 特征选择方法综述[J]. 计算机工程与应用, 2019, 55(24):10-19.
doi: 10.3778/j.issn.1002-8331.1909-0066 |
|
| [11] |
ZHANG Ge, WANG Jianlin. High-Dimensional Feature Selection Method Based on Hybrid ABC and CRO[J]. Computer Engineering and Applications, 2019, 55(11): 93-101.
doi: 10.3778/j.issn.1002-8331.1811-0316 |
|
张戈, 王建林. 基于混合ABC和CRO的高维特征选择方法[J]. 计算机工程与应用, 2019, 55(11):93-101.
doi: 10.3778/j.issn.1002-8331.1811-0316 |
|
| [12] | BEL O, PATA J, VLIMANT J R, et al. Diolkos: Improving Ethernet Throughput Through Dynamic Port Selection[C]// ACM. 18th ACM International Conference on Computing Frontiers. New York: ACM, 2021: 83-92. |
| [13] | THAY C, VISOOTTIVISETH V, MONGKOLLUKSAMEE S. P2P Traffic Classification for Residential Network[C]// IEEE. 2015 International Computer Science and Engineering Conference(ICSEC). New York: IEEE, 2015: 1-6. |
| [14] | CAI Manchun, WANG Tengfei, YUE Ting, et al. Fingerprint Recognition Technology of Tor Website Based on ARF[J]. Netinfo Security, 2021, 21(4): 39-48. |
| 蔡满春, 王腾飞, 岳婷, 等. 基于ARF的Tor网站指纹识别技术[J]. 信息网络安全, 2021, 21(4):39-48. | |
| [15] | SUN Zhijun, XUE Lei, XU Yangming, et al. Overview of Deep Learning Research[J]. Application Research of Computers, 2012, 29(8): 2806-2810. |
| 孙志军, 薛磊, 许阳明, 等. 深度学习研究综述[J]. 计算机应用研究, 2012, 29(8):2806-2810. | |
| [16] | NIMS. Network Information Management and Security Group[EB/OL]. [2022-09-27]. https://projects.cs.dal.ca/projectx/. |
| [17] | KHALID SHAHBAR A Z H. Anonymity Networks Dataset[EB/OL]. [2022-09-27] https://web.cs.dal.ca/-shahbar/dataset/anon17. |
| [18] | ZHANG Qian, LU Han, SAK H, et al. Transformer Transducer: A Streamable Speech Recognition Model with Transformer Encoders and RNN-t Loss[C]// IEEE. 2020 IEEE International Conference on Acoustics, Speech and Signal Processing(ICASSP). New York: IEEE, 2020: 7829-7833. |
| [19] |
OKADA S, OHZEKI M, TAGUCHI S. Efficient Partition of Integer Optimization Problems with One-Hot Encoding[J]. Scientific Reports, 2019, 9(1): 1-12.
doi: 10.1038/s41598-018-37186-2 |
| [20] |
MONTIERI A, CIUONZO D, BOVENZI G, et al. A Dive into the Dark Web: Hierarchical Traffic Classification of Anonymity Tools[J]. IEEE Transactions on Network Science and Engineering, 2019, 7(3): 1043-1054.
doi: 10.1109/TNSE.6488902 URL |
| [21] | CHEN Tianqi, GUESTRIN C. XGBoost: A Scalable Tree Boosting System[C]// ACM. 22nd ACM Sigkdd International Conference on Knowledge Discovery and Data Mining. New York: ACM, 2016: 785-794. |
| [1] | ZHAO Caidan, CHEN Jingqian, WU Zhiqiang. Automatic Modulation Recognition Algorithm Based on Multi-Channel Joint Learning [J]. Netinfo Security, 2023, 23(4): 20-29. |
| [2] | HU Zhijie, CHEN Xingshu, YUAN Daohua, ZHENG Tao. Static Detection Method of Android Adware Based on Improved Random Forest Algorithm [J]. Netinfo Security, 2023, 23(2): 85-95. |
| [3] | LIU Xiangyu, LU Tianliang, DU Yanhui, WANG Jingxiang. Lightweight IoT Intrusion Detection Method Based on Feature Selection [J]. Netinfo Security, 2023, 23(1): 66-72. |
| [4] | QIN Baodong, YU Peihang, ZHENG Dong. Decision Tree Classification Model Based on Double Trapdoor Homomorphic Encryption [J]. Netinfo Security, 2022, 22(7): 9-17. |
| [5] | WANG Juan, WANG Yunru, WENG Bin, GONG Jiaxin. Survey on Application of Machine Learning in Disassembly on x86 Binaries [J]. Netinfo Security, 2022, 22(6): 9-25. |
| [6] | NIU Yinuo, ZHANG Yifei, GAO Neng, MA Cunqing. Design of Log-Based Anomaly Detection System Based on Temporal and Logical Relationship [J]. Netinfo Security, 2022, 22(11): 1-6. |
| [7] | DUAN Xiaoyi, LI You, LINGHU Yunxing, HU Ronglei. Research on the Method of Side Channel Attack Based on RF Algorithm [J]. Netinfo Security, 2022, 22(1): 19-26. |
| [8] | GUO Chun, CAI Wenyan, SHEN Guowei, ZHOU Xuemei. Research on SQL Injection Attacks Detection Method Based on the Truncated Key Payload [J]. Netinfo Security, 2021, 21(7): 43-53. |
| [9] | MA Xiao, CAI Manchun, LU Tianliang. Malicious Domain Name Training Data Generation Technology Based on Improved CNN Model [J]. Netinfo Security, 2021, 21(10): 69-75. |
| [10] | XU Yu, ZHOU You, LIN Lu, ZHANG Cong. Applied Research of Unsupervised Machine Learning in Game Anti-fraud [J]. Netinfo Security, 2020, 20(9): 32-36. |
| [11] | GUO Chun, CHEN Changqing, SHEN Guowei, JIANG Chaohui. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [12] | DU Yifeng, GUO Yuanbo. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [13] | TAN Yang, LIU Jiayong, ZHANG Lei. Malware Familial Classification of Deep Auto-encoder Based on Mixed Features [J]. Netinfo Security, 2020, 20(12): 72-82. |
| [14] | Jian KANG, Jie WANG, Zhengxu LI, Guangda ZHANG. A Model for Anomaly Intrusion Detection with Different Feature Extraction Strategies in IoT [J]. Netinfo Security, 2019, 19(9): 21-25. |
| [15] | Zewen MA, Yang LIU, Hongping XU, Hang YI. DoS Traffic Identification Technology Based on Integrated Learning [J]. Netinfo Security, 2019, 19(9): 115-119. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||