Netinfo Security ›› 2023, Vol. 23 ›› Issue (10): 48-57.doi: 10.3969/j.issn.1671-1122.2023.10.007
Previous Articles Next Articles
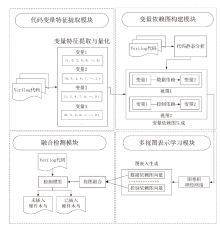
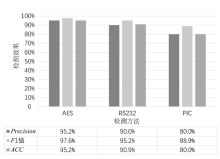
A Multi-View Hardware Trojan Detection Method Based on Static Analysis
CHEN Xingren( ), XIONG Yan, HUANG Wenchao, FU Guilu
), XIONG Yan, HUANG Wenchao, FU Guilu
- School of Computer Science and Technology, University of Science and Technology of China, Hefei 230026, China
-
Received:2023-06-14Online:2023-10-10Published:2023-10-11
CLC Number:
Cite this article
CHEN Xingren, XIONG Yan, HUANG Wenchao, FU Guilu. A Multi-View Hardware Trojan Detection Method Based on Static Analysis[J]. Netinfo Security, 2023, 23(10): 48-57.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.10.007
| [1] |
HU Wei, HONG C C, ANIRBAN S, et al. An Overview of Hardware Security and Trust: Threats, Countermeasures, and Design Tools[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2021, 40(6): 1010-1038.
doi: 10.1109/TCAD.2020.3047976 URL |
| [2] | TAMZIDUL H, JONATHAN C, PRABUDDHA C, et al. Hardware IP Trust Validation:Learn (the Untrustworthy), and Verify[C]// IEEE. IEEE International Test Conference. New York: IEEE, 2018: 1-10. |
| [3] | LU Sian. Research on Test Architectures of Reusable IP Core and SoC (System on a Chip)[D]. Zhejiang: Zhejiang University, 2003. |
| 陆思安. 可复用 IP 核以及系统芯片 SoC 的测试结构研究[D]. 浙江大学, 2003. | |
| [4] |
SONIA A, KASEM K, MAGDY A B. A Survey on Hardware Security: Current Trends and Challenges[J]. IEEE Access, 2023, 11: 77543-77565.
doi: 10.1109/ACCESS.2023.3288696 URL |
| [5] | JOHANN K, KAVUN E B, FRANCESCO R, et al. Towards Secure Composition of Integrated Circuits and Electronic Systems: On the Role of EDA[C]// EDAA. 2020 Design, Automation & Test in Europe Conference & Exhibition. New York: IEEE, 2020: 508-513. |
| [6] |
XUE Mingfu, GU Chongyan, LIU Weiqiang, et al. Ten Years of Hardware Trojans: A Survey from the Attacker’s Perspective[J]. IET Computers & Digital Techniques, 2020, 14(6): 231-246.
doi: 10.1049/cdt2.v14.6 URL |
| [7] | SKOROBOGATOV S, WOODS C. Breakthrough Silicon Scanning Discovers Backdoor in Military Chip[C]// IACR. Cryptographic Hardware and Embedded Systems(CHES 2012)-14th International Workshop. Berlin:Springer, 2012: 23-40. |
| [8] |
NICOLE F, ISMAIL S, CETIN K K, et al. Hiding Hardware Trojan Communication Channels in Partially Specified SoC Bus Functionality[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2017, 36(9): 1435-1444.
doi: 10.1109/TCAD.2016.2638439 URL |
| [9] | HUANG Zhao, WANG Quan, YANG Pengfei. Hardware Trojan: Research Progress and New Trends on Key Problems[J]. Chinese Journal of Computers, 2019, 42(5): 993-1017. |
| 黄钊, 王泉, 杨鹏飞. 硬件木马:关键问题研究进展及新动向[J]. 计算机学报, 2019, 42(5): 993-1017. | |
| [10] | CHAKRABORTY R S, WOLFF F, PAUL S, et al. MERO: A Statistical Approach for Hardware Trojan Detection[C]// IACR. Cryptographic Hardware and Embedded Systems (CHES 2009). Berlin:Springer, 2009: 396-410. |
| [11] | SAHA S, CHAKRABORTY R S, NUTHAKKI S S, et al. Improved Test Pattern Generation for Hardware Trojan Detection Using Genetic Algorithm and Boolean Satisfiability[C]// IACR. Cryptographic Hardware and Embedded Systems (CHES 2015)-17th International Workshop. Berlin:Springer, 2015: 577-596. |
| [12] | LYU Y, MISHRA P. Automated Trigger Activation by Repeated Maximal Clique Sampling[C]// IEEE. 25th Asia and South Pacific Design Automation Conference. New York: IEEE, 2020: 482-487. |
| [13] | SUBRAMANYAN P, ARORA D. Formal Verification of Taint-Propagation Security Properties in a Commercial SoC Design[C]// IEEE. Design Automation & Test in Europe Conference & Exhibition (DATE 2014). New York: IEEE, 2014: 1-2. |
| [14] | RAJENDRAN J, VEDULA V, KARRI R. Detecting Malicious Modifications of Data in Third-Party Intellectual Property Cores[C]// ACM. Proceedings of the 52nd Annual Design Automation Conference. New York: ACM, 2015: 1-112. |
| [15] | RAJENDRAN J, DHANDAYUTHAPANY A M, VEDULA V, et al. Formal Security Verification of Third Party Intellectual Property Cores for Information Leakage[C]// IEEE. 29th International Conference on VLSI Design and 15th International Conference on Embedded Systems. New York: IEEE, 2016: 547-522. |
| [16] | GUO Xiaolong, DUTTA R G, MISHRA P, et al. Scalable SoC Trust Verification Using Integrated Theorem Proving and Model Checking[C]// IEEE. 2016 IEEE International Symposium on Hardware Oriented Security and Trust. New York: IEEE, 2016: 124-129. |
| [17] | NAHIYAN A, SADI M, VITTAl R, et al. Hardware Trojan Detection Through Information Flow Security Verification[C]// IEEE. IEEE International Test Conference (ITC 2017). New York: IEEE, 2017: 1-10. |
| [18] | NAHIYAN A, XIAO Kan, YANG Kun, et al. AVFSM: A Framework for Identifying and Mitigating Vulnerabilities in FSMs[C]// DAC EC. Proceedings of the 53rd Annual Design Automation Conference. New York: ACM, 2016: 1-89. |
| [19] | WAKSMAN A, SUOZZO M, SETHUMADHAVAN S. FANCI: Identification of Stealthy Malicious Logic Using Boolean Functional Analysis[C]// ACM. 2013 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2013: 697-708. |
| [20] | ZHANG Jie, YUAN Feng, WEI Lingxiao, et al. VeriTrust: Verification for Hardware Trust[C]// ACM. The 50th Annual Design Automation Conference 2013. New York: ACM, 2013: 1-61. |
| [21] | ZHANG Jie, YUANFeng, XUQiang. Detrust: Defeating Hardware Trust Verifi- Cation with Stealthy Implicitly-Triggered Hardware Trojans[C]// ACM. Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2014: 153-166. |
| [22] | PICCOLBONI L, MENON A, PRAVADELLI G. Efficient Control-Flow Subgraph Matching for Detecting Hardware Trojans in RTL Models[J]. ACM Transactions on Embedded Computing Systems, 2017, 16 (5S): 1-19. |
| [23] | DEMROZI F, ZUCCHELLI R, PRAVADELLI G. Exploiting Sub-graph Isomorphism and Probabilistic Neural Networks for the Detection of Hardware Trojans at RTL[C]// IEEE. 2017 IEEE International High Level Design Validation and Test Workshop. New York: IEEE, 2017: 67-73. |
| [24] | HAN Tao, WANGYuze, LIUPeng. Hardware Trojans Detection at Register Transfer Level Based on Machine Learning[C]// IEEE. IEEE International Symposium on Circuits and Systems (ISCAS 2019). New York: IEEE, 2019: 1-5. |
| [25] | HASEGAWA K, YANAGISAWA M, TOGAWA N. Hardware Trojans Classification for Gate-Level Netlists Using Multi-Layer Neural Networks[C]// IEEE. 23rd IEEE International Symposium on on-Line Testing and Robust System Design. New York: IEEE, 2017: 227-232. |
| [26] | FARHATH Z, ROBERT K. Detecting RTL Trojans Using Artificial Immune Systems and High Level Behavior Classification[C]// AHSC. Asian Hardware Oriented Security and Trust Symposium (AsianHOST 2018). New York: ACM, 2018: 68-73. |
| [27] | YASAEI R, YU S Y, FARUQUE M A A. GNN4TJ: Graph Neural Networks for Hardware Trojan Detection at Register Transfer Level[C]// ECSI. Design Automation & Test in Europe Conference & Exhibition (DATE 2021). New York: IEEE, 2021: 1504-1509. |
| [28] |
SHAKYA B, HE T, SALMANI H, et al. Benchmarking of Hardware Trojans and Maliciously Affected Circuits[J]. Journal of Hardware and Systems Security, 2017, 1(1): 85-102.
doi: 10.1007/s41635-017-0001-6 |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||