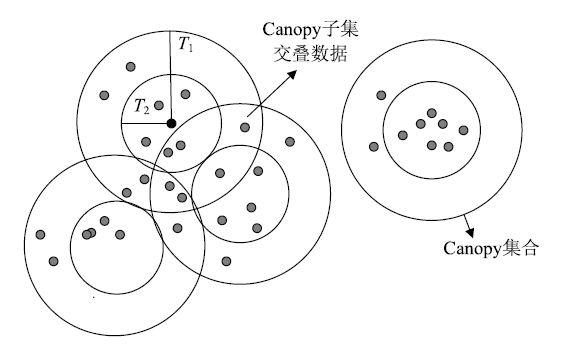
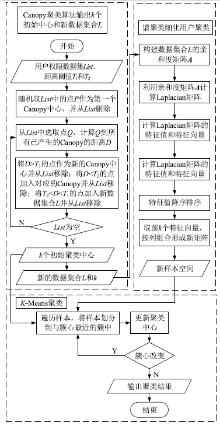
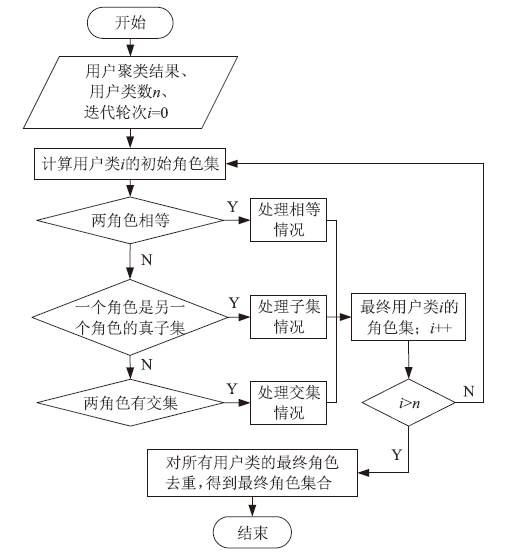
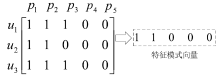| [1] |
MITRA B, SURAL S, VAIDYA J, et al. A Survey of Role Mining[J]. ACM Computing Surveys, 2016, 48(4): 1-37.
|
| [2] |
LIU Zhengtao, GU Wen, XIA Jinyue. Review of Access Control Model[J]. Journal of Cyber Security, 2019, 1(1): 43-50.
|
| [3] |
LI Hao, ZHANG Min, FENG Dengguo, et al. Research on Access Control of Big Data[J]. Chinese Journal of Computers, 2017, 40(1): 72-91.
|
|
李昊, 张敏, 冯登国, 等. 大数据访问控制研究[J]. 计算机学报, 2017, 40(1):72-91.
|
| [4] |
BAI Wei, PAN Zhisong, GUO Shize, et al. RMMDI: A Novel Framework for Role Mining Based on the Multi-Domain Information[EB/OL]. (2019-06-11)[2022-05-11]. .
|
| [5] |
KUHLMANN M, SHOHAT D, SCHIMPF G. Role Mining-Revealing Business Roles for Security Administration Using Data Mining Technology[C]// ACM. 8th ACM Symposium on Access Control Models and Technologies. New York: ACM, 2003: 179-186.
|
| [6] |
YUAN Xuebin, LI Wenping, LIU Shengcheng, et al. Role Mining Algorithm in RBAC[J]. Communications Technology, 2020, 53(8): 1994-2001.
|
|
袁学斌, 李文萍, 刘生成, 等. RBAC中角色挖掘算法研究[J]. 通信技术, 2020, 53(8):1994-2001.
|
| [7] |
BLUNDO C, CIMATO S, SINISCALCHI L. Role Mining Heuristics for Permission-Role-Usage Cardinality Constraints[J]. The Computer Journal, 2022, 65(6): 1386-1411.
doi: 10.1093/comjnl/bxaa186
URL
|
| [8] |
WANG Jingyu, CUI Yongjiao, TAN Yuesheng. Role Mining Algorithm Based on Double Cardinality Constraints[J]. Computer Engineering and Design, 2020, 41(6): 1599-1604.
|
|
王静宇, 崔永娇, 谭跃生. 基于双重约束的角色挖掘算法[J]. 计算机工程与设计, 2020, 41(6):1599-1604.
|
| [9] |
CUI Yongjiao. Research on Role Mining Algorithm for Access Control[D]. Baotou: Inner Mongolia University of Science & Technology, 2020.
|
|
崔永娇. 面向访问控制的角色挖掘算法研究[D]. 包头: 内蒙古科技大学, 2020.
|
| [10] |
ZHOU Chao, REN Zhiyu, WU Wenchao. Semantic Roles Mining Algorithms Based on Formal Concept Analysis[J]. Computer Science, 2018, 45(12): 117-122,129.
doi: 10.11896/j.issn.1002-137X.2018.12.018
|
|
周超, 任志宇, 毋文超. 基于形式概念分析的语义角色挖掘算法[J]. 计算机科学, 2018, 45(12):117-122,129.
doi: 10.11896/j.issn.1002-137X.2018.12.018
|
| [11] |
VAIDYA J, ATLURI V, GUO Qi. The Role Mining Problem: Finding A Minimal Descriptive Set of Roles[C]// ACM. 12th ACM Symposium on Access Control Models and Technologies. New York: ACM, 2007: 175-184.
|
| [12] |
LU Haibing, VAIDYA J, ATLURI V. Optimal Boolean Matrix Decomposition: Application to Role Engineering[C]// IEEE. 24th International Conference on Data Engineering. New York: IEEE, 2008: 297-306.
|
| [13] |
MOLLOY I, LI Ninghui, QI Yuan, et al. Mining Roles with Noisy Data[C]// ACM. 15th ACM Symposium on Access Control Models and Technologies. New York: ACM, 2010: 45-54.
|
| [14] |
MENG Deyu, XU Zongben, ZHANG Lei, et al. A Cyclic Weighted Median Method for l1 Low-Rank Matrix Factorization with Missing Entries[C]// AAAI. 27th AAAI Conference on Artificial Intelligence. Washington: AAAI, 2013: 704-710.
|
| [15] |
PAN Ning. Research on Several Key Technologies of Role Mining[D]. Zhengzhou: PLA Strategic Support Force Information Engineering University, 2018.
|
|
潘宁. 角色挖掘若干关键技术研究[D]. 郑州: 战略支援部队信息工程大学, 2018.
|
| [16] |
FANG Liang, YIN Lihua, LI Fenghua, et al. Spectral-Clustering-Based Abnormal Permission Assignments Hunting Framework[J]. Journal on Communications, 2017, 38(12): 63-72.
|
|
房梁, 殷丽华, 李凤华, 等. 基于谱聚类的访问控制异常权限配置挖掘机制[J]. 通信学报, 2017, 38(12):63-72.
|
| [17] |
MOLLOY I, CHEN Hong, LI Tiancheng, et al. Mining Roles with Multiple Objectives[J]. ACM Transactions on Information and System Security, 2010, 13(4): 1-35.
|