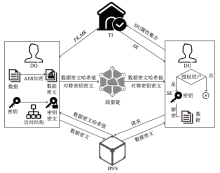
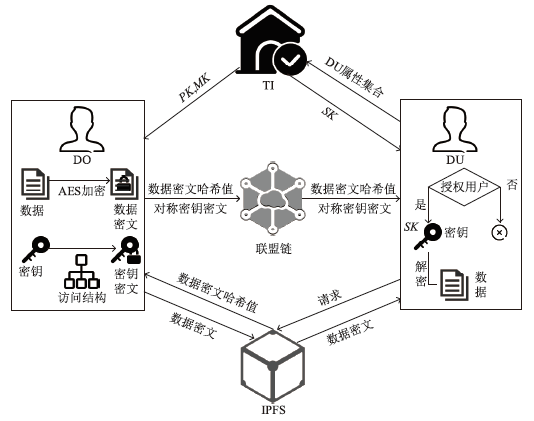
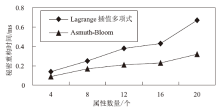
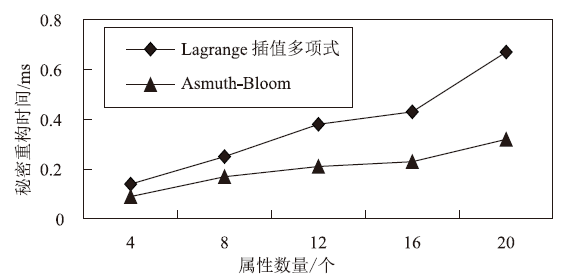
Netinfo Security ›› 2022, Vol. 22 ›› Issue (11): 17-23.doi: 10.3969/j.issn.1671-1122.2022.11.003
Previous Articles Next Articles
Data Sharing Scheme Based on Consortium Blockchain and Asmuth-Bloom Secret Sharing Algorithm
ZHANG Xuewang1,2, YAO Yaning1( ), LI Zhihong1, ZHANG Hao1
), LI Zhihong1, ZHANG Hao1
- 1. School of Software Engineering, Chongqing University of Posts and Telecommunications, Chongqing 400065, China
2. College of Microelectronic and Communication Engineering, Chongqing University, Chongqing 400004, China
-
Received:2022-06-18Online:2022-11-10Published:2022-11-16 -
Contact:YAO Yaning E-mail:2832644550@qq.com
CLC Number:
Cite this article
ZHANG Xuewang, YAO Yaning, LI Zhihong, ZHANG Hao. Data Sharing Scheme Based on Consortium Blockchain and Asmuth-Bloom Secret Sharing Algorithm[J]. Netinfo Security, 2022, 22(11): 17-23.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.11.003
| [1] | DING Xiaowei, SU Xinning. Financial Security Intelligence Analysis Based on Blockchain Driven Trustable Big Data and AI[J]. Journal of the China Society for Scientific and Technical Information, 2019, 38(12): 1297-1309. |
| 丁晓蔚, 苏新宁. 基于区块链可信大数据人工智能的金融安全情报分析[J]. 情报学报, 2019, 38(12):1297-1309. | |
| [2] |
WANG Zhijie, HUANG Dijiang, ZHU Yan, et al. Efficient Attribute-Based Comparable Data Access Control[J]. IEEE Transactions on Computers, 2015, 64(12): 3430-3443.
doi: 10.1109/TC.2015.2401033 URL |
| [3] |
JUNG T, LI Xiangyang, WAN Zhiguo, et al. Control Cloud Data Access Privilege and Anonymity with Fully Anonymous Attribute-Based Encryption[J]. IEEE Transactions on Information Forensics and Security, 2014, 10(1): 190-199.
doi: 10.1109/TIFS.2014.2368352 URL |
| [4] |
GAO Sheng, PIAO Guirong, ZHU Jianming, et al. TrustAccess: A Trustworthy Secure Ciphertext-Policy and Attribute Hiding Access Control Scheme Based on Blockchain[J]. IEEE Transactions on Vehicular Technology, 2020, 69(6): 5784-5798.
doi: 10.1109/TVT.2020.2967099 URL |
| [5] | HUANG Sui, CHEN Liwei, FAN Bingbing. Data Security Sharing Method Based on CP-ABE and Blockchain[J]. Computer System & Applications, 2019, 28(11): 79-86. |
| 黄穗, 陈丽炜, 范冰冰. 基于CP-ABE和区块链的数据安全共享方法[J]. 计算机系统应用, 2019, 28(11):79-86. | |
| [6] | JEMEL M, SERHROUCHNI A. Decentralized Access Control Mechanism with Temporal Dimension Based on Blockchain[C]// IEEE. 2017 IEEE 14th International Conference on E-Business Engineering(ICEBE). New York:IEEE, 2017: 177-182. |
| [7] | LI Xuelian, ZHANG Xiachuan, GAO Juntao, et al. Blockchain Data Sharing Scheme Supporting Attribute and Proxy Re-Encryption[J]. Journal of Xidian University, 2022, 49(1): 1-16. |
| 李雪莲, 张夏川, 高军涛, 等. 支持属性和代理重加密的区块链数据共享方案[J]. 西安电子科技大学学报, 2022, 49(1):1-16. | |
| [8] |
WANG Mengyu, YIN Xinchun, NING Jianting. Lightweight Medical Data Sharing Scheme with Access Policy Hiding and Key Tracking[J]. Computer Science, 2022, 49(3): 77-85.
doi: 10.11896/jsjkx.210800001 |
|
王梦宇, 殷新春, 宁建廷. 支持访问策略隐藏和密钥追踪的轻量级医疗数据共享方案[J]. 计算机科学, 2022, 49(3):77-85.
doi: 10.11896/jsjkx.210800001 |
|
| [9] | NIU Shufen, SONG Mi, FANG Lizhi, et al. Cloud Storage Data Sharing Based on Attribute Encryption in Smart Healthcare[J]. Journal of Electronics & Information Technology, 2022, 44(1): 107-117. |
| 牛淑芬, 宋蜜, 方丽芝, 等. 智慧医疗中基于属性加密的云存储数据共享[J]. 电子与信息学报, 2022, 44(1):107-117. | |
| [10] | FENG Jingyu, WANG Tao, YU Tingting, et al. A Secure Medical Data Scheme Based on Multi-Clouds and Multi-Chains Collaboration[J]. Netinfo Security, 2022, 22(1): 9-18. |
| 冯景瑜, 汪涛, 于婷婷, 等. 基于多云多链协同的医疗数据安全共享机制[J]. 信息网络安全, 2022, 22(1):9-18. | |
| [11] | ZHANG Lei, ZHENG Zhiyong, YUAN Yong. A Controllable Sharing Model for Electronic Health Records Based on Blockchain[J]. Acta Automatica Sinica, 2021, 47(9): 2143-2153. |
| 张磊, 郑志勇, 袁勇. 基于区块链的电子医疗病历可控共享模型[J]. 自动化学报, 2021, 47(9):2143-2153. | |
| [12] | YING Zuobin, SI Yuanping, MA Jianfeng, et al. Blockchain-Based Distributed HER Fine-Grained Traceability Scheme[J]. Journal of Communications, 2021, 42(5): 205-215. |
| 应作斌, 斯元平, 马建峰, 等. 基于区块链的分布式EHR细粒度可追溯方案[J]. 通信学报, 2021, 42(5):205-215. | |
| [13] | TAN Haibo, ZHOU Tong, ZHAO He, et al. Archival Data Protection and Sharing Method Based on Blockchain[J]. Journal of Software, 2019, 30(9): 2620-2635. |
| 谭海波, 周桐, 赵赫, 等. 基于区块链的档案数据保护与共享方法[J]. 软件学报, 2019, 30(9):2620-2635. | |
| [14] | PENG Peifu, ZHANG Guifang, HU Bin. Watermarking Algorithm of Database Based on Expanded Asmuth-Bloom Scheme[J]. Computer Engineering and Application, 2007(7): 179-181. |
| 彭沛夫, 张桂芳, 胡斌. 基于扩展的Asmuth-Bloom体系的数据库水印算法[J]. 计算机工程与应用, 2007(7):179-181. | |
| [15] | ZHANG Guifang, PENG Peifu. A Watermarking Algorithm of Database Based on Improved Sharing Secret Scheme[C]// IEEE. 2010 International Conference on Multimedia Technology. New York: IEEE, 2010: 1-2. |
| [16] | LUO Yangxia, MA Jun, ZHANG Zhigang, et al. Dynamic Graph Software Watermark Algorithm Based on Threshold Scheme[J]. Computer Engineering, 2009, 35(1): 153-155, 167. |
| 罗养霞, 马君, 张志刚, 等. 基于门限方案的动态图软件水印算法[J]. 计算机工程, 2009, 35(1):153-155,167. | |
| [17] | ZHU Jianzhong, YAO Zhiqiang. Digital Watermarking Technique Based on Asmuth-Bloom in Wavelet Domain[J]. Netinfo Security, 2012, 12(12): 15-17. |
| 朱建忠, 姚志强. 基于Asmuth-Bloom门限方案的小波域数字水印技术[J]. 信息网络安全, 2012, 12(12):15-17. | |
| [18] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. [2022-03-11]. |
| [19] | RESHMA V, GLADWIN S J, THIRUVENKATESAN C. Pairing-Free CP-ABE based Cryptography Combined with Steganography for Multimedia Applications[C]// IEEE. 2019 International Conference on Communication and Signal Processing(ICCSP). New York:IEEE, 2019: 501-505. |
| [20] | LI Ning, YAN Zheng, WANG Minjun, et al. Securing Communication Data in Pervasive Social Networking Based on Trust with KP-ABE[J]. ACM Transactions on Cyber-Physical Systems, 2018, 3(1): 1-23. |
| [21] |
ASMUTH C, BLOOM J. A Modular Approach to Key Safeguarding[J]. IEEE Transactions on Information Theory, 1983, 29(2): 208-210.
doi: 10.1109/TIT.1983.1056651 URL |
| [22] | YU Jingang, ZHANG Hong, LI Shu, et al. Data Sharing Model for Internet of Things Based on Blockchain[J]. Journal of Chinese Computer Systems, 2019, 40(11): 2324-2329. |
| 于金刚, 张弘, 李姝, 等. 基于区块链的物联网数据共享模型[J]. 小型微型计算机系统, 2019, 40(11):2324-2329. | |
| [23] |
LI Ruixuan, SHEN Chenglin, HE Heng, et al. A Lightweight Secure Data Sharing Scheme for Mobile Cloud Computing[J]. IEEE Transactions on Cloud Computing, 2017, 6(2): 344-357.
doi: 10.1109/TCC.2017.2649685 URL |
| [24] | SHEN Xueli, LYU Yingnan. Research on File Hierarchy Attribute Encryption of Hidden Access Structure[J]. Application Research of Computers, 2019, 36(1): 239-242. |
| 沈学利, 吕莹楠. 一种隐藏访问结构的文件层次属性加密研究[J]. 计算机应用研究, 2019, 36(1):239-242. | |
| [25] | CHENG Xiwen, QU Fengzhong. Ocean Data Sharing Based on Blockchain[C]// IEEE. 2021 IEEE 6th International Conference on Big Data Analytics(ICBDA). New York:IEEE, 2021: 155-159. |
| [26] |
JIA Xingxing, GUO Yusheng, LUO Xiangyang, et al. A Perfect Secret Sharing Scheme for General Access Structures[J]. Information Sciences, 2022, 595: 54-69.
doi: 10.1016/j.ins.2022.02.016 URL |
| [1] | YU Kechen, GUO Li, YIN Hongwei, YAN Xuesong. The High-Value Data Sharing Model Based on Blockchain and Game Theory for Data Centers [J]. Netinfo Security, 2022, 22(6): 73-85. |
| [2] | CUI Haoyu, MA Limin, WANG Jiahui, ZHANG Wei. Research on the Security Model of Multi-Authority for Attribute Encryption Based on Blockchain [J]. Netinfo Security, 2022, 22(5): 84-93. |
| [3] | CHEN Binjie, WEI Fushan, GU Chunxiang. Blockchain Abnormal Transaction Detection with Privacy-preserving Based on KNN [J]. Netinfo Security, 2022, 23(3): 78-84. |
| [4] | HOU Yutong, MA Zhaofeng, LUO Shoushan. Research and Implementation of Data Security Sharing and Controlled Distribution Technology Based on Blockchain [J]. Netinfo Security, 2022, 22(2): 55-63. |
| [5] | LU Xiaofeng, FU Songbing. A Trusted Data Access Control Scheme Combining Attribute-based Encryption and Blockchain [J]. Netinfo Security, 2021, 21(3): 7-8. |
| [6] | YU Kechen, GUO Li, YAO Mengmeng. Design of Blockchain-based High-value Data Sharing System [J]. Netinfo Security, 2021, 21(11): 75-84. |
| [7] | WANG Jinmiao, XIE Yongheng, WANG Guowei, LI Yiting. A Method of Privacy Preserving and Access Control in Blockchain Based on Attribute-based Encryption [J]. Netinfo Security, 2020, 20(9): 47-51. |
| [8] | LI Li, ZENG Qingxian, WEN Yihong, WANG Shicheng. Data Sharing Scheme Based on the Blockchain and the Proxy Re-encryption [J]. Netinfo Security, 2020, 20(8): 16-24. |
| [9] | SHI Guofeng, ZHANG Xinglan. An Attribute-based Encryption Scheme for Cloud Storage Supporting Range Ciphertext Search [J]. Netinfo Security, 2020, 20(6): 75-81. |
| [10] | LIU Peng, HE Qian, LIU Wangyang, CHENG Xu. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [11] | PENG Ruyue, MA Zhaofeng, LUO Shoushan. Research and Implementation of Digital Content Service and Security Supervision Technology Based on Blockchain [J]. Netinfo Security, 2020, 20(10): 49-56. |
| [12] | XU Shengwei, WANG Feijie. Attribute-based Encryption Scheme Traced Under Multi-authority [J]. Netinfo Security, 2020, 20(1): 33-39. |
| [13] | Jinmiao WANG, Guowei WANG, Mei WANG, Ruijin ZHU. Achieving Privacy Preserving and Flexible Access Control in Fog Computing [J]. Netinfo Security, 2019, 19(9): 41-45. |
| [14] | Shengyu WANG, Jinmiao WANG, Qingfeng DONG, Ruijin ZHU. A Survey of Attribute-based Encryption Technology [J]. Netinfo Security, 2019, 19(9): 76-80. |
| [15] | Min ZHENG, Hong WANG, Hong LIU, Chong TAN. Survey on Consensus Algorithms of Blockchain [J]. Netinfo Security, 2019, 19(7): 8-24. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||