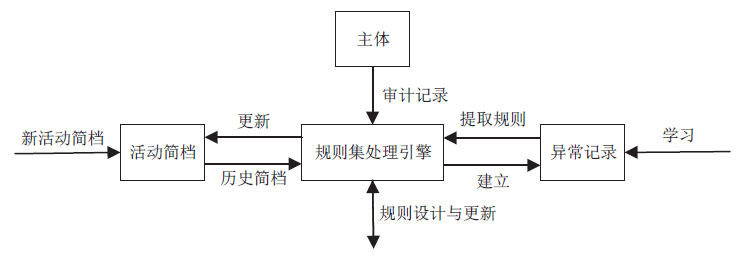
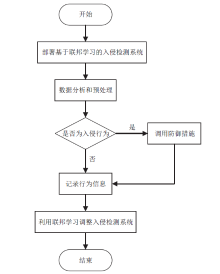
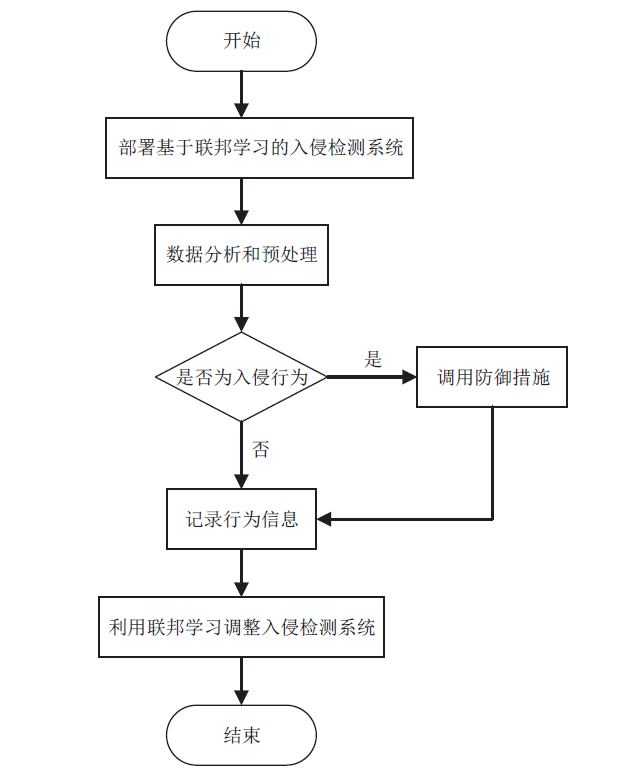
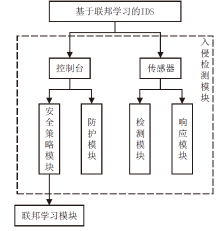
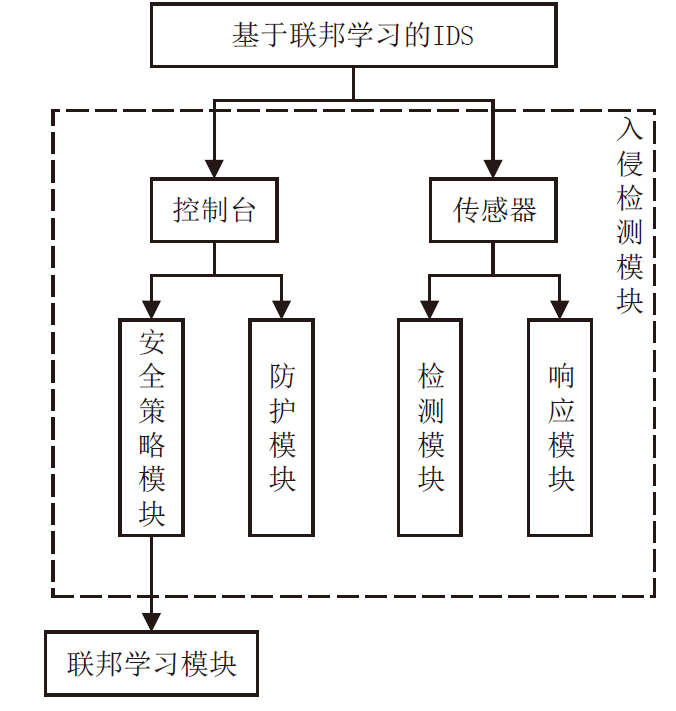
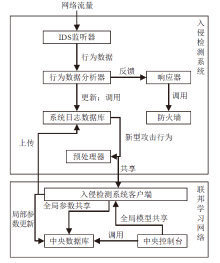
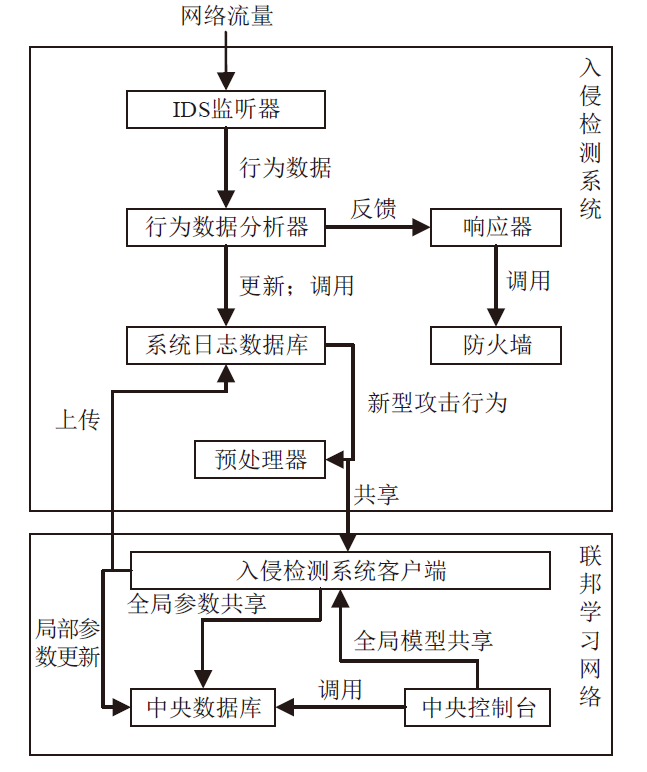
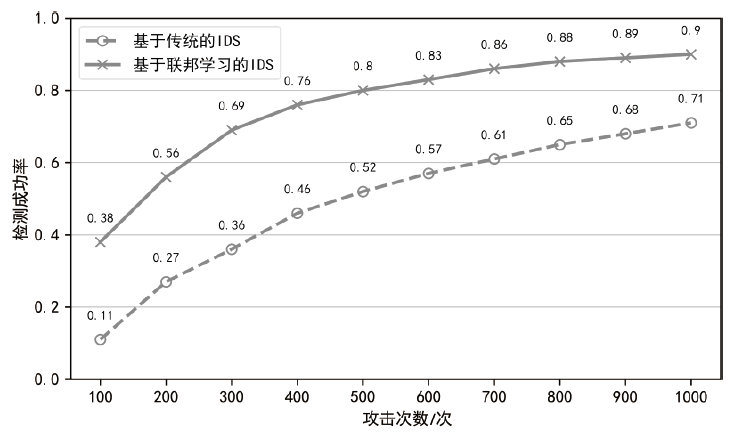
Netinfo Security ›› 2022, Vol. 22 ›› Issue (1): 46-54.doi: 10.3969/j.issn.1671-1122.2022.01.006
Previous Articles Next Articles
Research on Intrusion Detection Mechanism Based on Federated Learning
BAI Hongpeng1, DENG Dongxu2, XU Guangquan1( ), ZHOU Dexiang3
), ZHOU Dexiang3
- 1. College of Intelligence and Computing, Tianjin University, Tianjin 300350, China
2. China Electronic System Technology Co.,Ltd., Beijing 100070, China
3. Great Wall Motor Company Limited, Baoding 071000, China
-
Received:2021-09-16Online:2022-01-10Published:2022-02-16 -
Contact:XU Guangquan E-mail:losin@tju.edu.cn
CLC Number:
Cite this article
BAI Hongpeng, DENG Dongxu, XU Guangquan, ZHOU Dexiang. Research on Intrusion Detection Mechanism Based on Federated Learning[J]. Netinfo Security, 2022, 22(1): 46-54.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.01.006
| [1] | MA Aiping. AI Training Meets Privacy Problem Federal Learning Opens up Data Island in This Way[N]. Science and Technology Daily, 2019-11-19(5). |
| 马爱平. AI训练遇隐私难题联邦学习这样打通数据孤岛[N]. 科技日报, 2019-11-19(5). | |
| [2] | WANG Yakun. Survey of Federated Learning Technology for Data Sharing and Exchange[J]. Unmanned Systems Technology, 2019, 2(6):58-62. |
| 王亚珅. 面向数据共享交换的联邦学习技术发展综述[J]. 无人系统技术, 2019, 2(6):58-62. | |
| [3] | WANG Rong, MA Chunguang, WU Peng. Intrusion Detection Method Based on Federal Learning and Convolutional Neural Network[J]. Netinfo Security, 2020, 20(4):47-54. |
| 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4):47-54. | |
| [4] | YANG Qiang. Federal Learning: the Last Mile of AI[EB/OL]. http://kns.cnki.net/kcms/detail/23.1538.tp.20200317.1133.002.html, 2020-05-20. |
| 杨强. 联邦学习:人工智能的最后一公里[EB/OL]. http://kns.cnki.net/kcms/detail/23.1538.tp.20200317.1133.002.html, 2020-05-20. | |
| [5] | PAN Biying, QIU Haihua, ZHANG Jialun. Research on Federated Machine Learning with Different Data Distribution[C]// TD Industry Association. Proceedings of 5G Network Innovation Seminar (2019), August 15, 2019, Beijing, China. Beijing: Mobile Communications, 2019: 271-276. |
| [6] | PAN Rusheng, HAN Dongming, PAN Jiacheng, et al. Visualization of Federated Learning: Challenges and Framework[J]. Journal of Computer-aided Design & Computer Graphics, 2020, 32(4):513-519. |
| 潘如晟, 韩东明, 潘嘉铖, 等. 联邦学习可视化:挑战与框架[J]. 计算机辅助设计与图形学学报, 2020, 32(4):513-519. | |
| [7] | HUANG Zhenhao. Design and Implementation of Network Intrusion Detection[J]. Bulletin of Science and Technology, 2019, 35(12):82-86. |
| 黄振昊. 网络入侵检测的设计和实现方案[J]. 科技通报, 2019, 35(12):82-86. | |
| [8] | WANG Yan. Design of Network Intrusion Data Detection System Based on Big Data Analysis[J]. Computer Knowledge and Technology, 2019, 15(19):56-58. |
| 王岩. 基于大数据分析的网络入侵数据检测系统设计[J]. 电脑知识与技术, 2019, 15(19):56-58. | |
| [9] | ZHANG Weihua. Design and Development of Network Intrusion Testing System[J]. Network Security Technology & Application, 2020, 20(1):11-14. |
| 张卫华. 网络入侵测试系统的设计与开发[J]. 网络安全技术与应用, 2020, 20(1):11-14. | |
| [10] | HU Jian, SU Yongdong, LI Chao, et al. Research on Intrusion Detection System Based on Machine Learning[J]. Information & communication, 2019, 26(11):163-164. |
| 胡健, 苏永东, 李超, 等. 基于机器学习的入侵检测系统探究[J]. 信息通信, 2019, 26(11):163-164. | |
| [11] | YANG Qiang, LIU Yang, CHEN Tianjian, et al. Federated Machine Learning: Concept and Applications[J]. ACM Transactions on Intelligent Systems and Technology (TIST), 2019, 10(2):1-19. |
| [12] | CHAUHAN H, KUMAR V, PUNDIR S, et al. A Comparative Study of Classification Techniques for Intrusion Detection[C]// IEEE. 2013 International Symposium on Computational and Business Intelligence,August 24-26,2013,New Delhi, India. New York: IEEE, 2013: 40-43. |
| [13] |
MULAY S A, DEVALE P R, GARJE G V. Intrusion Detection System Using Support Vector Machine and Decision Tree[J]. International Journal of Computer Applications, 2010, 3(3):40-43.
doi: 10.5120/ijca URL |
| [14] | MCMAHAN H B, MOORE E, RAMAGE D, et al. Federated Learning of Deep Networks Using Model Averaging[EB/OL]. https://arxiv.org/pdf/1602.05629v1.pdf, 2016-02-17. |
| [15] | GUO Chuxu, SHI Yong, XUE Zhi. Port Scan Intrusion Detection Based on Machine Learning[J]. Communications Technology, 2020, 53(2):421-426. |
| 郭楚栩, 施勇, 薛质. 基于机器学习的端口扫描入侵检测[J]. 通信技术, 2020, 53(2):421-426. | |
| [16] | YANG Dongxiao, XIONG Ying, CHE Bichen. Network Intrusion Detection and Prevention[M]. Beijing: Tsinghua University Press, 2020. |
| 杨东晓, 熊瑛, 车碧琛. 入侵检测与入侵防御[M]. 北京: 清华大学出版社, 2020. |
| [1] | XU Shuo, ZHANG Rui, XIA Hui. Privacy-preserving Strategies for Federated Learning Based on Data Attribute Modification [J]. Netinfo Security, 2022, 22(1): 55-63. |
| [2] | HE Hongyan, HUANG Guoyan, ZHANG Bing, JIA Damiao. Intrusion Detection Model Based on Extra Trees-recursive Feature Elimination and LightGBM [J]. Netinfo Security, 2022, 22(1): 64-71. |
| [3] | LIU Shuo, ZHANG Xinglan. Intrusion Detection System Based on Dual Attention [J]. Netinfo Security, 2022, 22(1): 80-86. |
| [4] | GU Zhaojun, YAO Feng, DING Lei, SUI He. Network Security Test of Airport Fuel Supply Automatic Control System Based on Semi-physical Object [J]. Netinfo Security, 2021, 21(9): 16-24. |
| [5] | LU Honglin, WANG Liming, YANG Jing. A New Parameter Masking Federated Learning Privacy Preserving Scheme [J]. Netinfo Security, 2021, 21(8): 26-34. |
| [6] | LI Qun, DONG Jiahan, GUAN Zhitao, WANG Chao. A Clustering and Classification-based Malicious Attack Detection Method for Internet of Things [J]. Netinfo Security, 2021, 21(8): 82-90. |
| [7] | REN Tao, JIN Ruochen, LUO Yongmei. Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning [J]. Netinfo Security, 2021, 21(7): 27-34. |
| [8] | LU Honglin, WANG Liming. User-oriented Data Privacy Preserving Method for Federated Learning that Supports User Disconnection [J]. Netinfo Security, 2021, 21(3): 64-71. |
| [9] | DU Ye, WANG Zimeng, LI Meihong. Industrial Control Intrusion Detection Method Based on Optimized Kernel Extreme Learning Machine [J]. Netinfo Security, 2021, 21(2): 1-9. |
| [10] | WANG Huazhong, CHENG Qi. Research on Intrusion Detection of Industrial Control System Based on Improved Whale Algorithm [J]. Netinfo Security, 2021, 21(2): 53-60. |
| [11] | ZHAO Xiaolin, ZHAO Bin, ZHAO Jingjing, XUE Jingfeng. Research on Network Security Measurement Method Based on Attack Identification [J]. Netinfo Security, 2021, 21(11): 17-27. |
| [12] | WU Jiaming, XIONG Yan, HUANG Wenchao, WU Jianshuang. A Distance-based Fuzzing Mutation Method [J]. Netinfo Security, 2021, 21(10): 63-68. |
| [13] | JIN Zhigang, WANG Xinjian, LI Gen, YUE Shunmin. The Generation Method of Network Defense Strategy Combining with Attack Graph and Game Model [J]. Netinfo Security, 2021, 21(1): 1-9. |
| [14] | SHEN Yeming, LI Beibei, LIU Xiaojie, OUYANG Yuankai. Research on Active Learning-based Intrusion Detection Approach for Industrial Internet [J]. Netinfo Security, 2021, 21(1): 80-87. |
| [15] | DONG Qiang, LUO Guoming, SHI Hongkui, ZHANG Yongyue. Research on Authentication and Key Agreement Method of IMS-based Mobile Communication Private Network [J]. Netinfo Security, 2021, 21(1): 88-96. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||