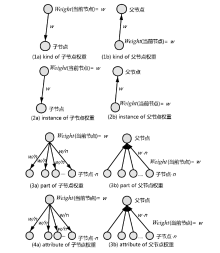
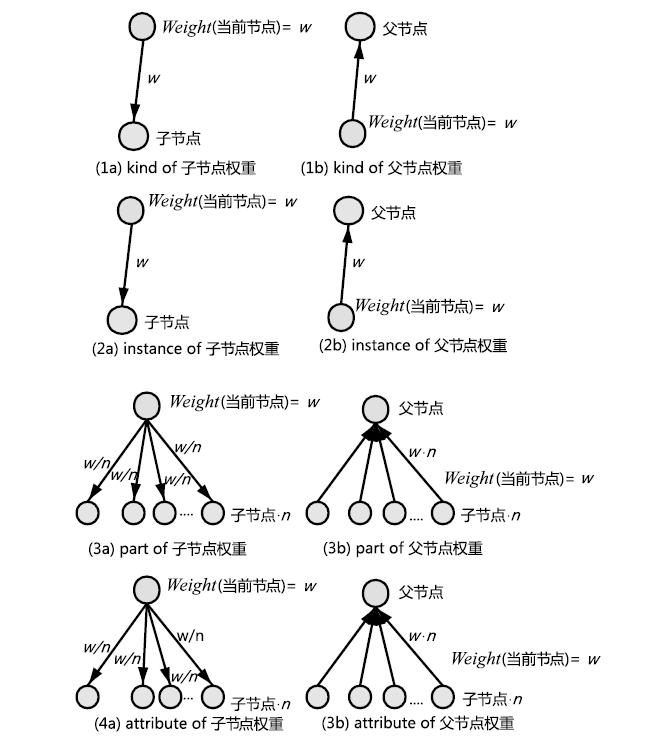
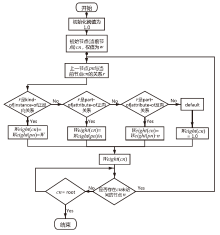
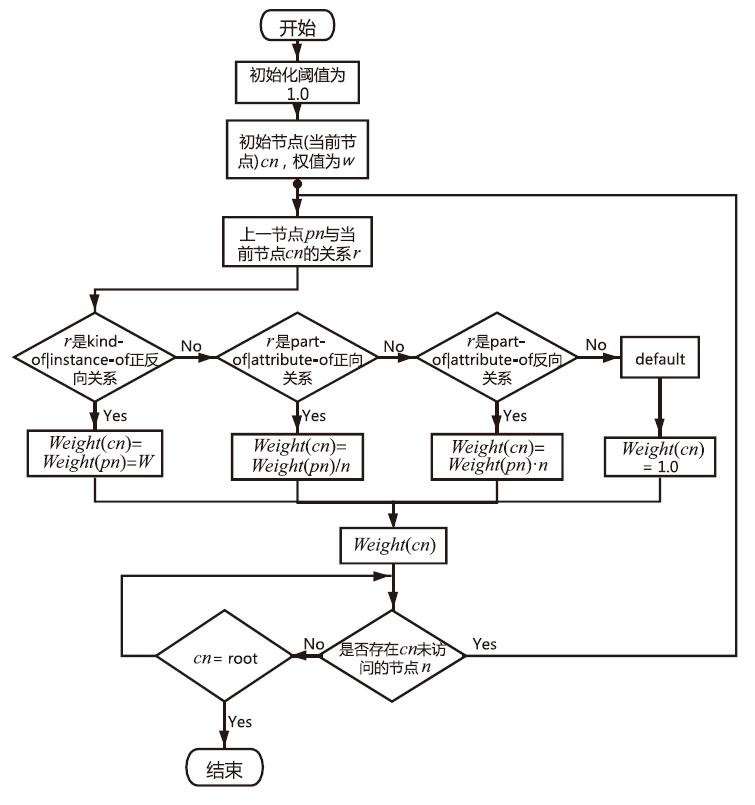
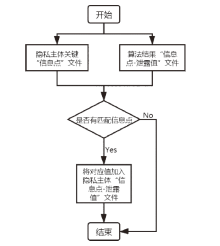
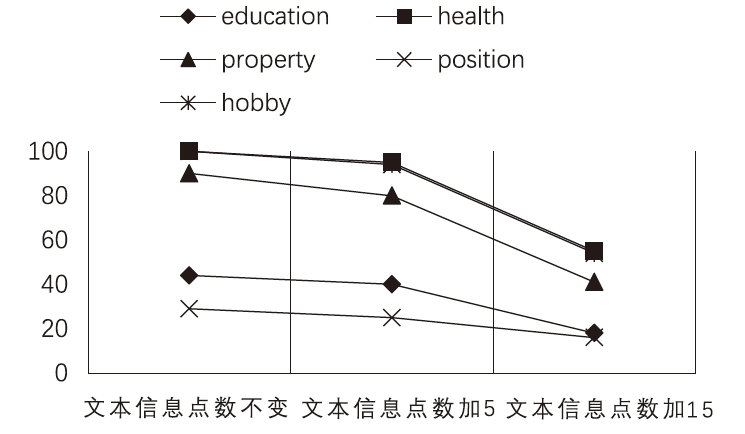
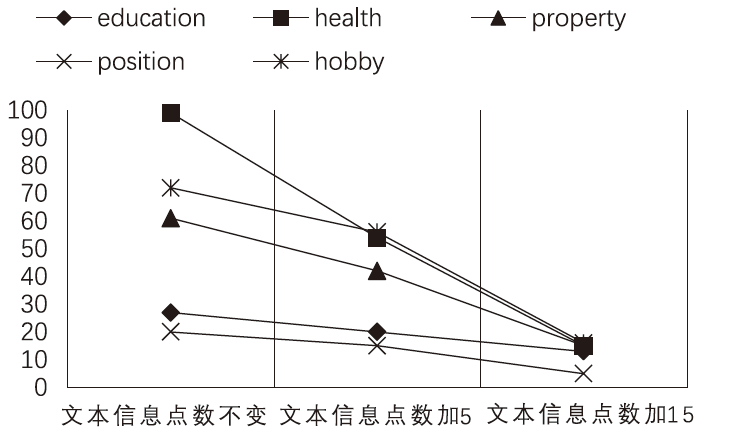
Netinfo Security ›› 2021, Vol. 21 ›› Issue (8): 52-61.doi: 10.3969/j.issn.1671-1122.2021.08.007
Previous Articles Next Articles
Research on Privacy Protection Access Control Mechanism Based on Ontology Reasoning
JIN Shuting, HE Jingsha, ZHU Nafei( ), PAN Shijia
), PAN Shijia
- Faculty of Information Technology, Beijing University of Technology, Beijing 100124, China
-
Received:2021-03-18Online:2021-08-10Published:2021-09-01 -
Contact:ZHU Nafei E-mail:znf@bjut.edu.cn
CLC Number:
Cite this article
JIN Shuting, HE Jingsha, ZHU Nafei, PAN Shijia. Research on Privacy Protection Access Control Mechanism Based on Ontology Reasoning[J]. Netinfo Security, 2021, 21(8): 52-61.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.08.007
| [1] | LOBO J. Relationship-based Access Control: More Than a Social Network Access Control Model[J]. Wiley Interdisciplinary Reviews-data Mining and Knowledge Discovery, 2019, 9(2):1-17. |
| [2] | SANHU R, COYNE E. Role based Access Control Models[J]. IEEE Computer, 1996, 29(2):38-47. |
| [3] | LI Fenghua, SU Mang, SHI Guozhen, et al. Research Status and Development Trends of Access Control Model[J]. Chinese Journal of Electronics, 2012, 40(4):805-813. |
| 李凤华, 苏铓, 史国振, 等. 访问控制模型研究进展及发展趋势[J]. 电子学报, 2012, 40(4):805-813. | |
| [4] | HARNAL S, CHAUHAN R. Efficient and Flexible Role-based Access Control (EFRBAC) Mechanism for Cloud[J]. ICST Transactions on Scalable Information Systems, 2018, 7(26):8-48. |
| [5] | DU Yifeng, GUO Yuanbo. A Dynamic Access Control Method for Fog Computing Based on Trust Value[J]. Netinfo Security, 2020, 20(4):65-72. |
| 杜义峰, 郭渊博. 一种基于信任值的雾计算动态访问控制方法[J]. 信息网络安全, 2020, 20(4):65-72. | |
| [6] |
MUNOZ A, LOPEZ S, POZO A, et al. An Architecture for Providing Data Usage and Access Control in Data Sharing Ecosystems[J]. Procedia Computer Science, 2019, 160(6):590-597.
doi: 10.1016/j.procs.2019.11.042 URL |
| [7] | FANG Liang, YIN Lihua, GUO Yunchuan, et al. A Survey of Key Technologies in Attribute-based Access Control Scheme[J]. Chinese Journal of computers, 2017, 40(7):1680-1698. |
| 房梁, 殷丽华, 郭云川, 等. 基于属性的访问控制关键技术研究综述[J]. 计算机学报, 2017, 40(7):1680-1698. | |
| [8] |
ANNIKA B. Online Privacy Concerns: A Broad Approach to Understanding the Concerns of Different Groups for Different Uses[J]. Computers in Human Behavior, 2015, 53(7):419-426.
doi: 10.1016/j.chb.2015.07.025 URL |
| [9] |
SWEENEY L. K-Anonymity: A Model for Protecting Privacy[J]. International Journal on Uncertainty, Fuzziness and Knowledge-based Systems, 2002, 10(5):557-570.
doi: 10.1142/S0218488502001648 URL |
| [10] | MACHANAVAJJHALA A, GEHRKE J, KIFER D. L-diversity: Privacy beyond K-anonymity[C]//IEEE. 22nd International Conference on Data Engineering, April 3-7, 2006, Atlanta, GA, USA. New York: IEEE, 2006: 24-36. |
| [11] | LI Ninghui, LI Tiancheng. T-closeness: Privacy beyond K-anonymity and L-diversity[C]//IEEE. 23rd International Conference on Data Engineering, April 16-20, 2007, Istanbul Turkey. New York: IEEE, 2007: 106-115. |
| [12] | LI Yang, WEN Wen. Survey of Research on Differential Privacy[J]. Application Research of Computers. 2012, 29(9):3201-3205+3211. |
| 李杨, 温雯, 谢光强. 差分隐私保护研究综述[J]. 计算机应用研究, 2012, 29(9):3201-3205+3211. | |
| [13] | TANIAR D, RAHAYU J. Web Semantics and Ontology[M]. Pennsylvania: IGI Publishing, 2006. |
| [14] | JIA Junzhi, CUI Xiyan. Interoperability between Ontological Word Lists of Persons and Construction of Classification Systems[J]. Journal of The China Society for Scientific and Technical Information, 2019, 38(7):731-741. |
| 贾君枝, 崔西燕. 人物本体词表之间的互操作及分类体系构建[J]. 情报学报, 2019, 38(7):731-741. | |
| [15] |
ZHU Nafei, WANG Siyu, HE Jingsha, et al. On the Suitability of Applying Wordnet to Privacy Measurement[J]. Wireless Personal Communications, 2018, 103(1):359-378.
doi: 10.1007/s11277-018-5447-5 URL |
| [16] | TANG Lulu, CHEN Ke, WU Chaozheng, et al. Improving Semantic Analysis on Point Clouds via Auxiliary Supervision of Local Geometric Priors[J]. IEEE Transactions on Cybernetics, 2020, 10(8):1-11. |
| [17] |
HU Xinbang, YU Xuqiao, LI Shaomei, et al. Additional Knowledge Enhanced Chinese Name Entity Recognition[J]. Computer Engineering, 2021: 10(5):1-12.
doi: 10.1007/BF01206535 URL |
| 胡新棒, 于溆乔, 李邵梅, 等. 基于知识增强的中文命名实体识别[J]. 计算机工程, 2021: 10(5):1-12. |
| [1] | SHEN Zhuowei, GAO Peng, XU Xinyu. Design of DDS Secure Communication Middleware Based on Security Negotiation [J]. Netinfo Security, 2021, 21(6): 19-25. |
| [2] | LIU Zi’ang, HUANG Yuanyuan, MA Jiali, ZHOU Rui. Design and Implementation of Monitoring Platform for Medical Data Abuse Based on Blockchain [J]. Netinfo Security, 2021, 21(5): 58-66. |
| [3] | REN Hang, CHENG Xiangguo, ZHANG Rui, XIA Hui. A Novel Fraud Prevention Strategy Based on Bargaining Bayesian Game Model [J]. Netinfo Security, 2021, 21(4): 81-88. |
| [4] | ZHOU Yousheng, WANG Ming, LIU Yuanni. Privacy Protection Scheme Supporting Interval Query for LBS Outsourced Data [J]. Netinfo Security, 2021, 21(3): 26-36. |
| [5] | LU Xiaofeng, FU Songbing. A Trusted Data Access Control Scheme Combining Attribute-based Encryption and Blockchain [J]. Netinfo Security, 2021, 21(3): 7-8. |
| [6] | LIU Feng, YANG Jie, QI Jiayin. Two-Party ECDSA for Blockchain Based on Hash Proof Systems [J]. Netinfo Security, 2021, 21(1): 19-26. |
| [7] | WANG Jinmiao, XIE Yongheng, WANG Guowei, LI Yiting. A Method of Privacy Preserving and Access Control in Blockchain Based on Attribute-based Encryption [J]. Netinfo Security, 2020, 20(9): 47-51. |
| [8] | WU Yunkun, JIANG Bo, PAN Ruixuan, LIU Yuling. A SDN Access Control Mechanism Based on Zero Trust [J]. Netinfo Security, 2020, 20(8): 37-46. |
| [9] | LI Ningbo, ZHOU Haonan, CHE Xiaoliang, YANG Xiaoyuan. Design of Directional Decryption Protocol Based on Multi-key Fully Homomorphic Encryption in Cloud Environment [J]. Netinfo Security, 2020, 20(6): 10-16. |
| [10] | DU Yifeng, GUO Yuanbo. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [11] | LIU Peng, HE Qian, LIU Wangyang, CHENG Xu. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [12] | YU Lu, LUO Senlin. A Method of Internal Intrusion Detection of Database in RBAC Mode [J]. Netinfo Security, 2020, 20(2): 83-90. |
| [13] | XIAO Biao, YAN Hongqiang, LUO Haining, LI Jucheng. Research on Improvement of Bayesian Network Privacy Protection Algorithm Based on Differential Privacy [J]. Netinfo Security, 2020, 20(11): 75-86. |
| [14] | HE Jingsha, DU Jinhui, ZHU Nafei. Research on k-anonymity Algorithm for Personalized Quasi-identifier Attributes [J]. Netinfo Security, 2020, 20(10): 19-26. |
| [15] | HUANG Baohua, CHENG Qi, YUAN Hong, HUANG Pirong. K-means Clustering Algorithm Based on Differential Privacy with Distance and Sum of Square Error [J]. Netinfo Security, 2020, 20(10): 34-40. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||