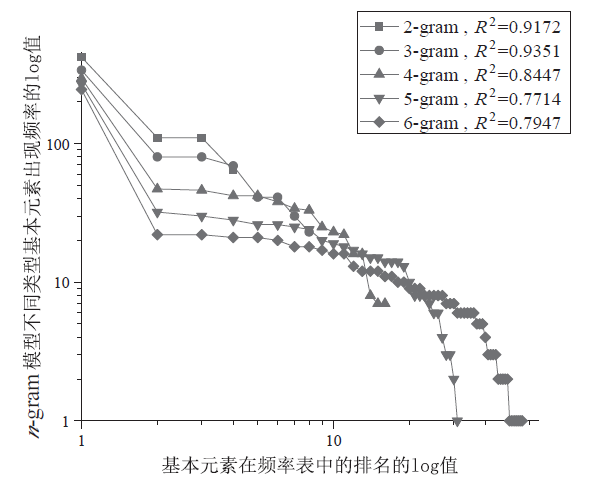
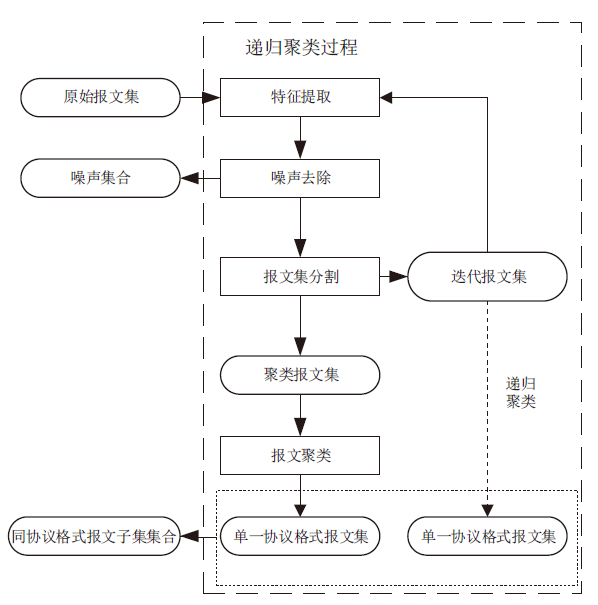
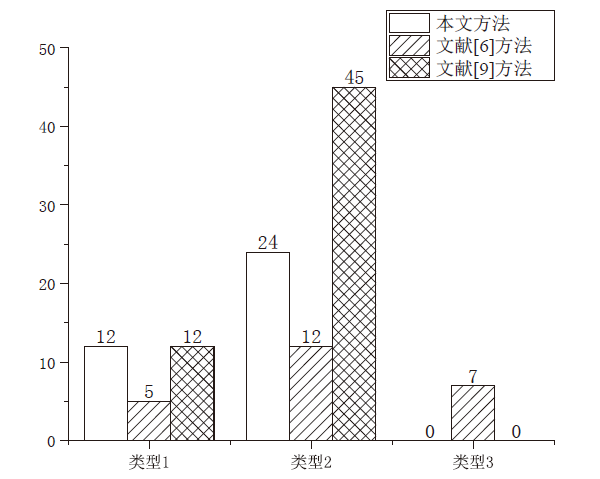
Netinfo Security ›› 2021, Vol. 21 ›› Issue (7): 72-79.doi: 10.3969/j.issn.1671-1122.2021.07.009
Previous Articles Next Articles
Anti-noise Application Layer Binary Protocol Format Reverse Method
FANG Minzhi1,2( ), CHENG Guang1,2, KONG Panyu1,2
), CHENG Guang1,2, KONG Panyu1,2
- 1. School of Cyber Science and Engineering, Southeast University, Nanjing 211189, China
2. International Governance Research Base of Cyberspace, Southeast University, Nanjing 211189, China
-
Received:2021-02-04Online:2021-07-10Published:2021-07-23 -
Contact:FANG Minzhi E-mail:mzfang@njnet.edu.cn
CLC Number:
Cite this article
FANG Minzhi, CHENG Guang, KONG Panyu. Anti-noise Application Layer Binary Protocol Format Reverse Method[J]. Netinfo Security, 2021, 21(7): 72-79.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.07.009
| value p | 001 | 010 | 110 |
|---|---|---|---|
| 1 | ${{C}_{\left( 001,1 \right)}}$ | ${{C}_{\left( 010,1 \right)}}$ | ${{C}_{\left( 110,1 \right)}}$ |
| 2 | ${{C}_{\left( 001,2 \right)}}$ | ${{C}_{\left( 010,2 \right)}}$ | ${{C}_{\left( 110,2 \right)}}$ |
| 3 | ${{C}_{\left( 001,3 \right)}}$ | ${{C}_{\left( 010,3 \right)}}$ | ${{C}_{\left( 110,3 \right)}}$ |
| [1] | Wireshark. Network Protocol Analyzer[EB/OL]. http://www.wireshark.org, 2020-08-15. 2020-08-15 |
| [2] | CABALLERO J, YIN Heng, LIANG Zhenkai, et al. Polyglot: Automatic Extraction of Protocol Message Format Using Dynamic Binary Analysis[C]// ACM. The 14th ACM Conference on Computer and Communications Security, October 29-November 2, 2007, Alexandria, Virginia, USA. New York: ACM, 2007: 31-329. |
| [3] | LIN Zhiqiang, JIANG Xuxian, XU Dongyan, et al. Automatic Protocol Format Reverse Engineering through Context-aware Monitored Execution[C]// NDSS. The 15th Network and Distributed System Security Symposium, February 10-13, 2008, San Diego, California, USA. Reston: Internet Society, 2008: 1-15. |
| [4] | PAN Fan, WU Lifa, DU Youxiang, et al. Overviews on Protocol Reverse Engineering[J]. Application Research of Computers, 2011, 28(8):2801-2806. |
| 潘璠, 吴礼发, 杜有翔, 等. 协议逆向工程研究进展[J]. 计算机应用研究, 2011, 28(8):2801-2806. | |
| [5] |
LI Min, YU Shunzheng. Anti-noise Optimal Segmentation Method for Unknown Application Layer Protocol Message Format[J]. Journal of Software, 2013, 24(3):604-617.
doi: 10.3724/SP.J.1001.2013.04243 URL |
| 黎敏, 余顺争. 抗噪的未知应用层协议报文格式最佳分段方法[J]. 软件学报, 2013, 24(3):604-617. | |
| [6] | BEDDOE M A. Network Protocol Analysis Using Bioinformatics Algorithms[EB/OL]. https://www.researchgate.net/publication/228531955_Network_protocol_analysis_using_bioinformatics_algorithms, 2020-08-15. |
| [7] |
LI Weiming, ZHANG Aifang, LIU Jiancai, et al. Automatic Fuzzy Test Vulnerability Mining Method for Network Protocol[J]. Chinese Journal of Computers, 2011, 34(2):242-255.
doi: 10.3724/SP.J.1016.2011.00242 URL |
| 李伟明, 张爱芳, 刘建财, 等. 网络协议的自动化模糊测试漏洞挖掘方法[J]. 计算机学报, 2011, 34(2):242-255. | |
| [8] |
TAO Y, YU Hongyi, LI Qing. Bit-oriented Format Extraction Approach for Automatic Binary Protocol Reverse Engineering[J]. IET Communications, 2016, 10(6):709-716.
doi: 10.1049/cmu2.v10.6 URL |
| [9] | CUI Weidong, KANNAN J, WANG H J. Discover: Automatic Protocol Reverse Engineering from Network Traces[C]// USENIX. The 16th Usenix Security Symposium, August 6-10, 2007, Boston, MA, USA. New York: Usenix Association, 2007: 1-17. |
| [10] | LUO Jianzhen, YU Shunzheng. Position-based Automatic Reverse Engineering of Network Protocols[J]. Journal of Network & Computer Applications, 2013, 36(3):1070-1077. |
| [11] | HEI Xinhong, BAI Binbin, WANG Yichuan, et al. Feature Extraction Optimization for Bitstream Communication Protocol Format Reverse Analysis[C]// IEEE. 2019 18th IEEE International Conference on Trust, Security And Privacy In Computing And Communications/13th IEEE International Conference on Big Data Science And Engineering (TrustCom/BigDataSE), August 5-8, 2019, Rotorua, New Zealand. NJ: IEEE, 2019: 662-669. |
| [12] | SHIM K S, GOO Y H, LEE M S, et al. Clustering Method in Protocol Reverse Engineering for Industrial Protocols[J]. International Journal of Network Management, 2020, 30(6):1-15. |
| [13] |
LI Wentian. Random Texts Exhibit Zipf’s-law-like Word Frequency Distribution[J]. IEEE Transactions on Information Theory, 1992, 38(6):1842-1845.
doi: 10.1109/18.165464 URL |
| [14] | ZHOU Aiwu, YU Yafei. The Research about Clustering Algorithm of K-Means[J]. Computer Technology And Development, 2011, 21(2):62-65. |
| 周爱武, 于亚飞. K-Means聚类算法的研究[J]. 计算机技术与发展, 2011, 21(2):62-65. | |
| [15] | ZHU Lianjiang, MA Bingxian, ZHAO Xuequan. Clustering Validity Analysis Based on Contour Coefficient[J]. Journal of Computer Applications, 2010, 30(12):139-141. |
| 朱连江, 马炳先, 赵学泉. 基于轮廓系数的聚类有效性分析[J]. 计算机应用, 2010, 30(12):139-141. |
| [1] | XIE Sijiang, GAO Qiong, FENG Yan. A Multiple Paths Routing Scheme with Least Number of Public Nodes Based on Trust Relaying Quantum Key Distribution Network [J]. Netinfo Security, 2021, 21(7): 35-42. |
| [2] | LIU Xin, YANG Haorui, GUO Zhenbin, WANG Jiayin. An Authentication Protocol Achieving Online Registration and Privilege Separation for Industrial Internet of Things [J]. Netinfo Security, 2021, 21(7): 1-9. |
| [3] | HU Bowen, ZHOU Chunjie, LIU Lu. Coordination of Functional Safety and Information Security for Intelligent Instrument Based on Fuzzy Multi-objective Decision [J]. Netinfo Security, 2021, 21(7): 10-16. |
| [4] | WEN Weiping, FANG Ying, YE He, CHEN Xiarun. A Code Obfuscation System against Symbolic Execution Attacks [J]. Netinfo Security, 2021, 21(7): 17-26. |
| [5] | REN Tao, JIN Ruochen, LUO Yongmei. Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning [J]. Netinfo Security, 2021, 21(7): 27-34. |
| [6] | GUO Chun, CAI Wenyan, SHEN Guowei, ZHOU Xuemei. Research on SQL Injection Attacks Detection Method Based on the Truncated Key Payload [J]. Netinfo Security, 2021, 21(7): 43-53. |
| [7] | XU Hongping, MA Zewen, YI Hang, ZHANG Longfei. Network Traffic Anomaly Detection Technology Based on Convolutional Recurrent Neural Network [J]. Netinfo Security, 2021, 21(7): 54-62. |
| [8] | ZHAO Yuran, MENG Kui. Research on English-Chinese Machine Translation Based on Sentence Grouping [J]. Netinfo Security, 2021, 21(7): 63-71. |
| [9] | CHEN Bowei, XIA Xuan, ZHONG Weidong, WU Liqiang. The Defense Scheme of S-box on LBlock Based on Secret Sharing [J]. Netinfo Security, 2021, 21(7): 80-86. |
| [10] | HUANG Ziyi, QIN Yuhai. Malicious Mining Web Page Detection and Forensics Based on Multi-feature Recognition [J]. Netinfo Security, 2021, 21(7): 87-94. |
| [11] | LIU Xin, GUO Zhenbin, SONG Yuchen. An Authentication Scheme Based on SGX for Industrial Internet of Things [J]. Netinfo Security, 2021, 21(6): 1-10. |
| [12] | ZHANG Zheng, LIU Ya’nan, WANG Lei, FANG Xuming. An Accuracy and Efficiency Multi-hop Localization for Irregular Network [J]. Netinfo Security, 2021, 21(6): 11-18. |
| [13] | SHEN Zhuowei, GAO Peng, XU Xinyu. Design of DDS Secure Communication Middleware Based on Security Negotiation [J]. Netinfo Security, 2021, 21(6): 19-25. |
| [14] | LIU Jing*, ZHANG Yuchen, ZHANG Hongqi. Automatic Intrusion Response Decision-making Method Based on Q-Learning [J]. Netinfo Security, 2021, 21(6): 26-35. |
| [15] | WU Yi, ZHONG Sheng. Research on Raft Consensus Algorithm for Blockchain [J]. Netinfo Security, 2021, 21(6): 36-44. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||