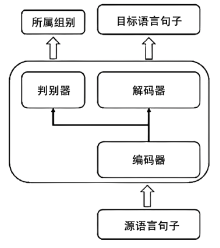
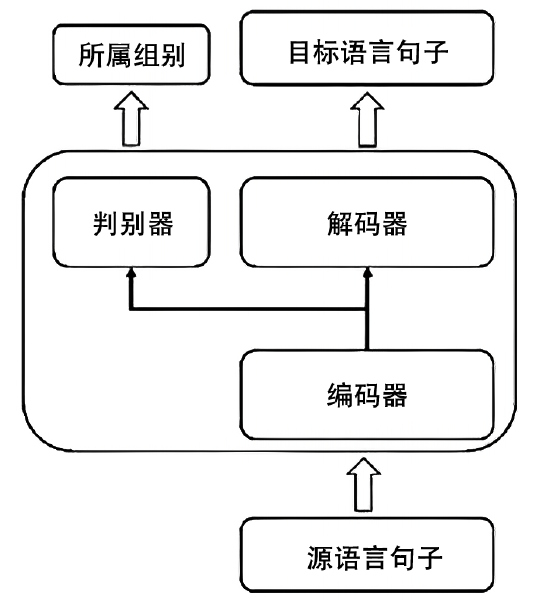
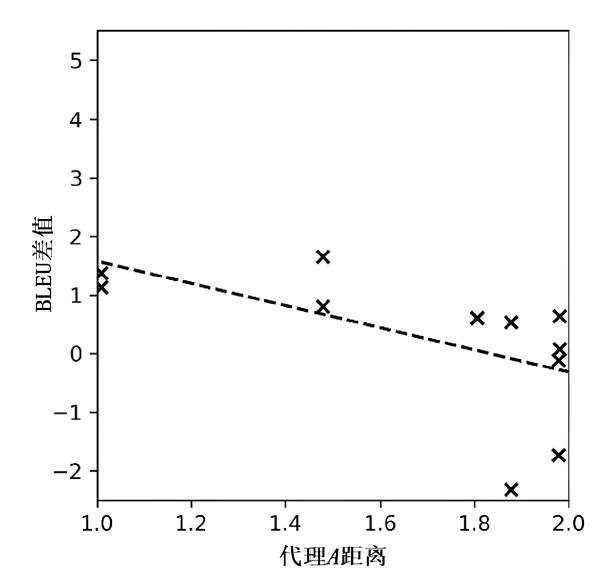
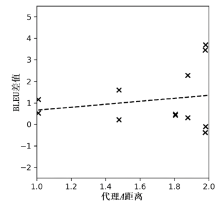
Netinfo Security ›› 2021, Vol. 21 ›› Issue (7): 63-71.doi: 10.3969/j.issn.1671-1122.2021.07.008
Previous Articles Next Articles
Research on English-Chinese Machine Translation Based on Sentence Grouping
- School of Electronic Information and Electrical Engineering, Shanghai Jiao Tong University, Shanghai 200240, China
-
Received:2021-04-15Online:2021-07-10Published:2021-07-23 -
Contact:MENG Kui E-mail:mengkui@sjtu.edu.cn
CLC Number:
Cite this article
ZHAO Yuran, MENG Kui. Research on English-Chinese Machine Translation Based on Sentence Grouping[J]. Netinfo Security, 2021, 21(7): 63-71.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.07.008
| [1] | KALCHBRENNER N, BLUNSOM P. Recurrent Continuous Translation Models[C]// ACL. Proceedings of the 2013 Conference on Empirical Methods in Natural Language Processing, October 18-21, 2013, Washington, Stroudsburg: ACL, 2013: 1700-1709. |
| [2] | SUTSKEVER I, VINYALS O, LE Q V. Sequence to Sequence Learning with Neural Networks[C]// Neural Information Processing Systems Foundation. Proceedings of the 27th International Conference on Neural Information Processing Systems, December 8-13, 2014, Montreal, Quebec, Canada. New York: Curran Associates, 2014: 3104-3112. |
| [3] | VASWANI A, SHAZEER N, PARMAR N, et al. Attention is All you Need[C]// Neural Information Processing Systems Foundation. Proceedings of the 31st International Conference on Neural Information Processing Systems, December 4-9, 2017, Long Beach, CA, USA. New York: Curran Associates, 2017: 5998-6008. |
| [4] | DEVLIN J, CHANG M W, LEE K, et al. BERT: Pre-training of Deep Bidirectional Transformers for Language Understanding[C]// ACL. Proceedings of the 2019 Conference of the North American Chapter of the Association for Computational Linguistics, June 2-7, 2019, Minneapolis, MN, USA. Stroudsburg: ACL, 2019: 4171-4186. |
| [5] |
SALTON G, FOX E A, WU H. Extended Boolean Information Retrieval[J]. Communications of the ACM, 1983, 26(11):1022-1036.
doi: 10.1145/182.358466 URL |
| [6] | MIKOLOV T, SUTSKEVER I, CHEN K, et al. Distributed Representations of Words and Phrases and their Compositionality[C]// Neural Information Processing Systems Foundation. Proceedings of the 26th International Conference on Neural Information Processing Systems, December 5-8, 2013, Lake Tahoe, Nevada, USA. New York: Curran Associates, 2013: 3111-3119. |
| [7] | PENNINGTON J, SOCHER R, MANNING C D. Glove: Global Vectors for Word Representation[C]// ACL. Proceedings of the 2014 Conference on Empirical Methods in Natural Language Processing, October 25-29, 2014, Doha, Qatar. Stroudsburg: ACL, 2014: 1532-1543. |
| [8] | DAI A M, LE Q V. Semi-supervised Sequence Learning[C]// Neural Information Processing Systems Foundation. Proceedings of the 28th International Conference on Neural Information Processing Systems, December 7-12, 2015, Montreal, Quebec, Canada. New York: Curran Associates, 2015: 3079-3087. |
| [9] | PETERS M, NEUMANN M, IYYER M, et al. Deep Contextualized Word Representations[C]// ACL. Proceedings of the 2018 Conference of the North American Chapter of the Association for Computational Linguistics, June 1-6, 2018, New Orleans, USA. Stroudsburg: ACL, 2018: 2227-2237. |
| [10] | CHEN T, GUESTRIN C. Xgboost: A Scalable Tree Boosting System[C]// ACM. Proceedings of the 22nd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, August 13-17, 2016, San Francisco, CA, USA. New York: ACM, 2016: 785-794. |
| [11] | CORTES C, VAPNIK V. Support-vector Networks[J]. Machine Learning, 1995, 20(3):273-297. |
| [12] | LIU P, QIU X, HUANG X. Recurrent Neural Network for Text Classification with Multi-task Learning[C]// IJCAI. Proceedings of the 25th International Joint Conference on Artificial Intelligence, July 9-15, 2016, New York. Menlo Park: AAAI, 2016: 2873-2879. |
| [13] | KIM Y. Convolutional Neural Networks for Sentence Classification[C]// ACL. Proceedings of the 2014 Conference on Empirical Methods in Natural Language Processing, October 25-29, 2014, Doha, Qatar. Stroudsburg: ACL, 2014: 1746-1751. |
| [14] |
LLOYD S. Least Squares Quantization in PCM[J]. IEEE Transactions on Information Theory, 1982, 28(2):129-136.
doi: 10.1109/TIT.1982.1056489 URL |
| [15] | ARTHUR D, VASSILVITSKII S. K-means++: The Advantages of Careful Seeding[C]// ACM. Proceedings of the 18th Annual ACM-SIAM Symposium on Discrete Algorithms, January 7-9, 2007, New Orleans, Louisiana, USA. Philadelphia: SIAM, 2007: 1027-1035. |
| [16] | SCULLEY D. Web-scale K-means Clustering[C]// ACM. Proceedings of the 19th International Conference on World Wide Web, April 26-30, 2010, Raleigh, North Carolina, USA. New York: ACM, 2010: 1177-1178. |
| [17] | BRITZ D, LE Q, PRYZANT R. Effective Domain Mixing for Neural Machine Translation[C]// ACL. Proceedings of the Second Conference on Machine Translation, September 7-8, 2017, Copenhagen, Denmark. Stroudsburg: ACL, 2017: 118-126. |
| [18] | KIFER D, BEN-DAVID S, GEHRKE J. Detecting Change in Data Streams[C]// VLDB. Proceedings of the Thirtieth International Conference on Very Large Data Bases, August 31-September 3, 2004, Toronto, Canada. Trondheim, Norway: VLDB Endowment, 2004: 180-191. |
| [19] | BEND S, EIRON N, LONG P M. On the Difficulty of Approximately Maximizing Agreements[J]. Journal of Computer and System Sciences, 2003, 3(66):496-514. |
| [20] | BEND S, BLITZER J, CRAMMER K, et al. Analysis of Representations for Domain Adaptation[C]// Neural Information Processing Systems Foundation. Proceedings of the 20th Annual Conference on Neural Information Processing Systems, December 4-7, 2006, Vancouver, British Columbia, Canada. Cambridge, USA: MIT Press, 2007: 137-144. |
| [21] | HEWITT J, MANNING C D. A Structural Probe for Finding Syntax in Word Representations[C]// ACL. Proceedings of the 2019 Conference of the North American Chapter of the Association for Computational Linguistics, June 2-7, 2019, Minneapolis, MN, USA. Stroudsburg: ACL, 2019: 4129-4138. |
| [1] | XIE Sijiang, GAO Qiong, FENG Yan. A Multiple Paths Routing Scheme with Least Number of Public Nodes Based on Trust Relaying Quantum Key Distribution Network [J]. Netinfo Security, 2021, 21(7): 35-42. |
| [2] | LIU Xin, YANG Haorui, GUO Zhenbin, WANG Jiayin. An Authentication Protocol Achieving Online Registration and Privilege Separation for Industrial Internet of Things [J]. Netinfo Security, 2021, 21(7): 1-9. |
| [3] | FANG Minzhi, CHENG Guang, KONG Panyu. Anti-noise Application Layer Binary Protocol Format Reverse Method [J]. Netinfo Security, 2021, 21(7): 72-79. |
| [4] | HU Bowen, ZHOU Chunjie, LIU Lu. Coordination of Functional Safety and Information Security for Intelligent Instrument Based on Fuzzy Multi-objective Decision [J]. Netinfo Security, 2021, 21(7): 10-16. |
| [5] | WEN Weiping, FANG Ying, YE He, CHEN Xiarun. A Code Obfuscation System against Symbolic Execution Attacks [J]. Netinfo Security, 2021, 21(7): 17-26. |
| [6] | REN Tao, JIN Ruochen, LUO Yongmei. Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning [J]. Netinfo Security, 2021, 21(7): 27-34. |
| [7] | GUO Chun, CAI Wenyan, SHEN Guowei, ZHOU Xuemei. Research on SQL Injection Attacks Detection Method Based on the Truncated Key Payload [J]. Netinfo Security, 2021, 21(7): 43-53. |
| [8] | XU Hongping, MA Zewen, YI Hang, ZHANG Longfei. Network Traffic Anomaly Detection Technology Based on Convolutional Recurrent Neural Network [J]. Netinfo Security, 2021, 21(7): 54-62. |
| [9] | CHEN Bowei, XIA Xuan, ZHONG Weidong, WU Liqiang. The Defense Scheme of S-box on LBlock Based on Secret Sharing [J]. Netinfo Security, 2021, 21(7): 80-86. |
| [10] | HUANG Ziyi, QIN Yuhai. Malicious Mining Web Page Detection and Forensics Based on Multi-feature Recognition [J]. Netinfo Security, 2021, 21(7): 87-94. |
| [11] | LIU Xin, GUO Zhenbin, SONG Yuchen. An Authentication Scheme Based on SGX for Industrial Internet of Things [J]. Netinfo Security, 2021, 21(6): 1-10. |
| [12] | ZHANG Zheng, LIU Ya’nan, WANG Lei, FANG Xuming. An Accuracy and Efficiency Multi-hop Localization for Irregular Network [J]. Netinfo Security, 2021, 21(6): 11-18. |
| [13] | SHEN Zhuowei, GAO Peng, XU Xinyu. Design of DDS Secure Communication Middleware Based on Security Negotiation [J]. Netinfo Security, 2021, 21(6): 19-25. |
| [14] | LIU Jing*, ZHANG Yuchen, ZHANG Hongqi. Automatic Intrusion Response Decision-making Method Based on Q-Learning [J]. Netinfo Security, 2021, 21(6): 26-35. |
| [15] | WU Yi, ZHONG Sheng. Research on Raft Consensus Algorithm for Blockchain [J]. Netinfo Security, 2021, 21(6): 36-44. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||