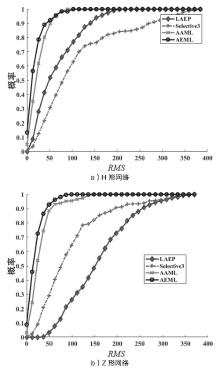
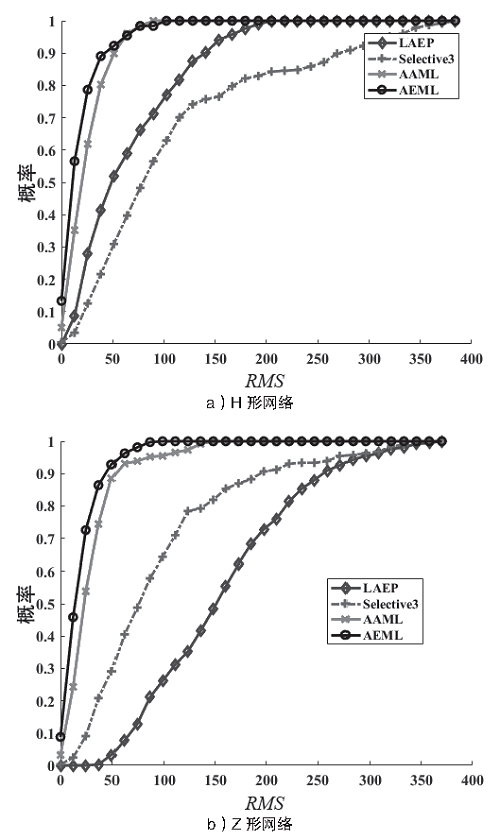
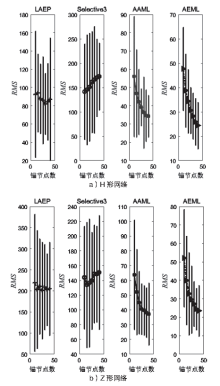
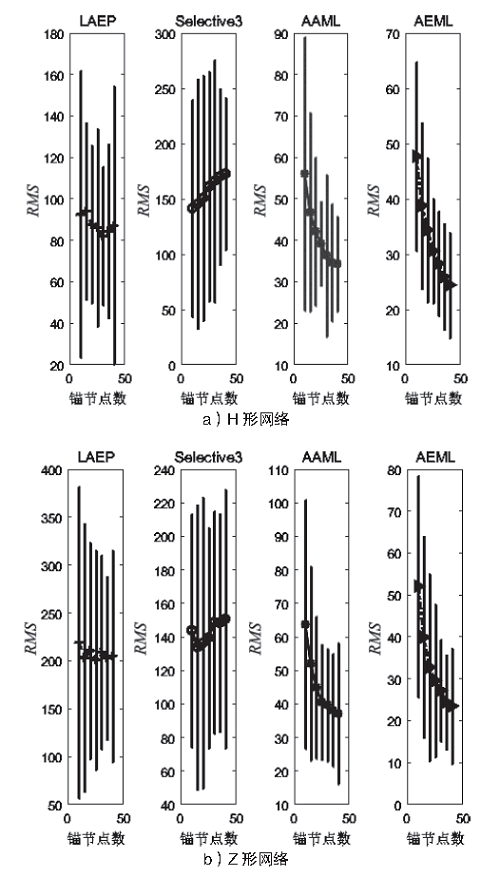
Netinfo Security ›› 2021, Vol. 21 ›› Issue (6): 11-18.doi: 10.3969/j.issn.1671-1122.2021.06.002
Previous Articles Next Articles
An Accuracy and Efficiency Multi-hop Localization for Irregular Network
ZHANG Zheng1,2( ), LIU Ya’nan1, WANG Lei1, FANG Xuming2
), LIU Ya’nan1, WANG Lei1, FANG Xuming2
- 1. Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100093, China
2. College of Network Security, Jinling Institute of Technology, Nanjing 211169, China
-
Received:2020-11-21Online:2021-06-10Published:2021-07-01 -
Contact:ZHANG Zheng E-mail:zhangzheng@jit.edu.cn
CLC Number:
Cite this article
ZHANG Zheng, LIU Ya’nan, WANG Lei, FANG Xuming. An Accuracy and Efficiency Multi-hop Localization for Irregular Network[J]. Netinfo Security, 2021, 21(6): 11-18.
share this article
| [1] |
GAO Demin, SUN Quan, HU Bin, et al. A Framework for Agricultural Pest and Disease Monitoring Based on Internet-of-Things and Unmanned Aerial Vehicles[J]. Sensors, 2020,20(5):1487-1504.
doi: 10.3390/s20051487 URL |
| [2] |
ZHANG Shuo, GAO Demin, LIN Haifeng, et al. Wildfire Detection Using Sound Spectrum Analysis Based on the Internet of Things[J]. Sensors, 2019,19(23):5093-5113.
doi: 10.3390/s19235093 URL |
| [3] | YANG Zheng, WU Chenshu, LIU Yunhao. Location-based Computing: Localization and Localizability of Wireless Networks[M]. Beijing: Tsinghua University Press, 2014. |
| 杨铮, 吴陈沭, 刘云浩. 位置计算: 无线网络定位与可定位性[M]. 北京: 清华大学出版社, 2014. | |
| [4] | FAHEEM Z, ATHANASIOS G, KIN K. Leung. A Survey of Indoor Localization Systems and Technologies[J]. IEEE CST, 2019,21(3):2568-2599. |
| [5] | YANG Zhong, YAN Xiaoyong. Research on Node Localization Technology of Sensor Network[M]. Beijing: Science Press, 2018. |
| 杨忠, 严筱永. 传感网节点定位技术研究[M]. 北京: 科学出版社, 2018. | |
| [6] | DOU Rulin, HU Bo, SHI Weijuan. Incremental Multi-hop Localization Algorithm Based on Regularized Weighted Least Squares[J]. International Journal of Pattern Recognition & Artificial Intelligence, 2019,33(9):1-21. |
| [7] |
NICULESCU Dragos, NATH Badri. DV Based Positioning in Ad Hoc Networks[J]. Telecommun. Syst. , 2003,22(1-4):267-280.
doi: 10.1023/A:1023403323460 URL |
| [8] |
WANG Yun, WANG Xiaodong, WANG Demin. Range-free Localization Using Expected Hop Progress in Wireless Sensor Networks[J]. IEEE Transactions on Parallel and Distributed Systems, 2009,20(10):1540-1552.
doi: 10.1109/TPDS.2008.239 URL |
| [9] |
GUI Linqing, VAL Thierry, WEI Anne, et al. Improvement of Range-free Localization Technology by a Novel DV-hop Protocol in Wireless Sensor Networks[J]. Ad Hoc Networks, 2015,24(7):55-73.
doi: 10.1016/j.adhoc.2014.07.025 URL |
| [10] | YAN Xiaoyong, CAO Jiannong, SUN Lijuan, et al. Accurate Analytical-based Multi-hop Localization with Low Energy Consumption for Irregular Networks[J]. IEEE TVT, 2020,69(2):2021-2033. |
| [11] | KLEINROCK Leonard, SILVESTER John. Optimum Transmission Radii for Packet Radio Network or Why Six Is a Magic Number[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=170v0xf0ye1d02r0rc700v300b441211&site=xueshu_se, 2020 -10-19. |
| [12] | QIAN Zhihong, SUN Dayang, LEUNG V. A Survey on Localization Model in Wireless Network[J]. Chinese Journal of Computers, 2016,39(6):1237-1256. |
| 钱志鸿, 孙大洋, LEUNG V. 无线网络定位综述[J]. 计算机学报, 2016,39(6):1237-1256. | |
| [13] | WANG Chenyong. Introduction of Linear Regression Analysis[M]. Beijing: China Machine Press, 2016. |
| 王辰勇. 线性回归分析导论[M]. 北京: 机械工业出版社, 2016. | |
| [14] | YE Zhongfu. Statistical Signal Processing[M]. Hefei: University of Science and Technology of China Press, 2009. |
| 叶中付. 信号统计分析与处理[M]. 合肥: 中国科技大学出版社, 2009. | |
| [15] | SIMICS S N., SASTRY Shankar. Distributed Localization in Wireless Ad Hoc Networks[EB/OL]. , 2001 -12-07. |
| [16] |
YAN Xiaoyong, SUN Lijuan, ZHOU Jian, et al. DV-hop Localisation Algorithm Based on Optimal Weighted Least Square in Irregular Areas[J]. Electronics Letters, 2018,54(21):1243-1245.
doi: 10.1049/ell2.v54.21 URL |
| [1] | LIU Xin, GUO Zhenbin, SONG Yuchen. An Authentication Scheme Based on SGX for Industrial Internet of Things [J]. Netinfo Security, 2021, 21(6): 1-10. |
| [2] | SHEN Zhuowei, GAO Peng, XU Xinyu. Design of DDS Secure Communication Middleware Based on Security Negotiation [J]. Netinfo Security, 2021, 21(6): 19-25. |
| [3] | LIU Jing*, ZHANG Yuchen, ZHANG Hongqi. Automatic Intrusion Response Decision-making Method Based on Q-Learning [J]. Netinfo Security, 2021, 21(6): 26-35. |
| [4] | WU Yi, ZHONG Sheng. Research on Raft Consensus Algorithm for Blockchain [J]. Netinfo Security, 2021, 21(6): 36-44. |
| [5] | LI Dan, YAN Ting, GUO Rui. Quantum Color Image Encryption Algorithm Based on Alternating Quantum Walk [J]. Netinfo Security, 2021, 21(6): 45-51. |
| [6] | XU Guotian*, SHEN Yaotong. Multiple Classification Detection Method for Malware Based on XGBoost and Stacking Fusion Model [J]. Netinfo Security, 2021, 21(6): 52-62. |
| [7] | DING Jiawei, LIU Xiaodong. Named Entity Recognition Model of Telecommunication Network Fraud Crime Based on ELECTRA-CRF [J]. Netinfo Security, 2021, 21(6): 63-69. |
| [8] | FAN Guangyu, WANG Xingwei, JIA Jie, HUANG Min. Secure Interaction Scheme between SDN Application Plane and Control Plane [J]. Netinfo Security, 2021, 21(6): 70-79. |
| [9] | WANG Chao, HAN Yiliang, DUAN Xiaowei, LI Yu. RLWE-type Authentication Key Exchange Protocol Based on Key Encapsulation Mechanism [J]. Netinfo Security, 2021, 21(6): 80-88. |
| [10] | SONG Yulong, WANG Lei, WU Xinrong, ZENG Weijun. Research on WSN Topological Invulnerability Based on Adaptive Simulated Annealing Particle Swarm Optimization Algorithm [J]. Netinfo Security, 2021, 21(6): 89-96. |
| [11] | LI Peng, ZHENG Tiantian, XU He, ZHU Feng. RFID Security Authentication Protocol Based on Blockchain Technology [J]. Netinfo Security, 2021, 21(5): 1-11. |
| [12] | ZHENG Jun, NIE Rong, WANG Shouxin, TAN Yu’an. Attribute Weight Snapshot Selection Strategy Based on Docker Container Fault Recovery [J]. Netinfo Security, 2021, 21(5): 12-18. |
| [13] | ZHOU Yousheng, ZHONG Tianqi. Blockchain-based Fair Exchange Scheme [J]. Netinfo Security, 2021, 21(5): 19-30. |
| [14] | WU Chi, SHUAI Junlan, LONG Tao, YU Junqing. Research on Detection Method of User Abnormal Operation Based on Linux Shell Commands [J]. Netinfo Security, 2021, 21(5): 31-38. |
| [15] | GU Zhaojun, CAI Chang, WANG Ming. The Masking Method of Civil Aviation Passenger Data Based on Improved Format-preserving Encryption [J]. Netinfo Security, 2021, 21(5): 39-47. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||