Netinfo Security ›› 2021, Vol. 21 ›› Issue (7): 35-42.doi: 10.3969/j.issn.1671-1122.2021.07.005
Previous Articles Next Articles
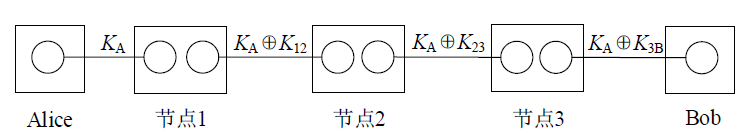
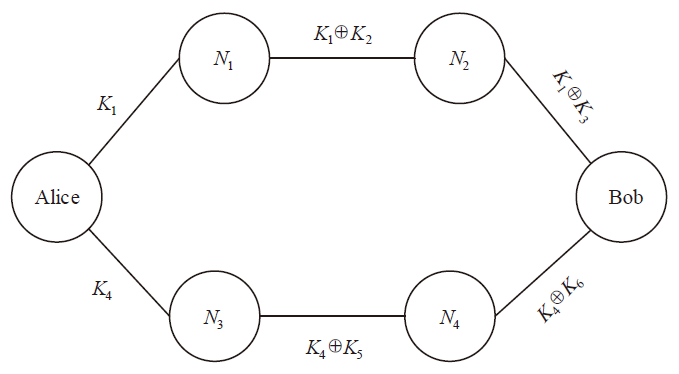
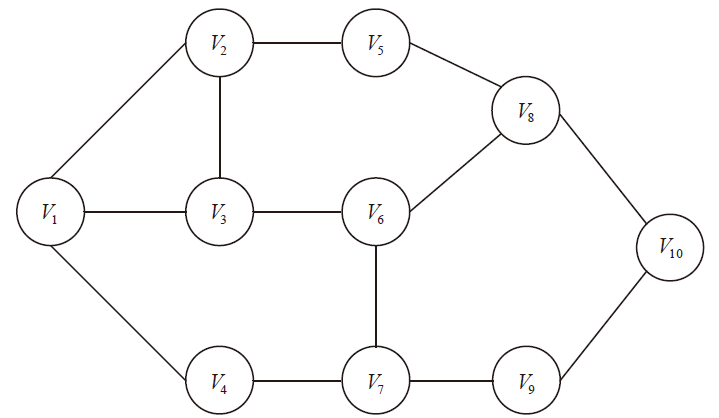
A Multiple Paths Routing Scheme with Least Number of Public Nodes Based on Trust Relaying Quantum Key Distribution Network
XIE Sijiang1, GAO Qiong2( ), FENG Yan1
), FENG Yan1
- 1. Beijing Electronic Science & Technology Institute, Beijing 100070, China
2. Xidian University, Xi’an 710071, China
-
Received:2021-01-30Online:2021-07-10Published:2021-07-23 -
Contact:GAO Qiong E-mail:1131886741@qq.com
CLC Number:
Cite this article
XIE Sijiang, GAO Qiong, FENG Yan. A Multiple Paths Routing Scheme with Least Number of Public Nodes Based on Trust Relaying Quantum Key Distribution Network[J]. Netinfo Security, 2021, 21(7): 35-42.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.07.005
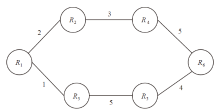
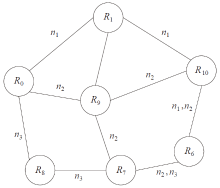
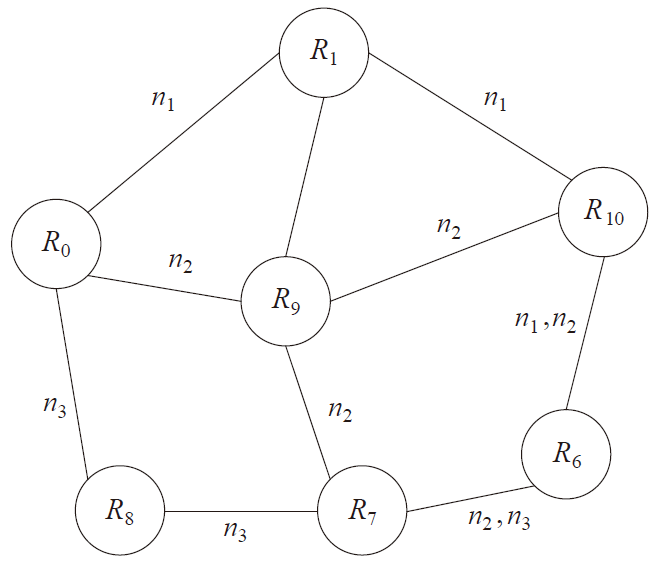
| 随机路由 | 最少公共节点多路径路由 | |
|---|---|---|
| R1,R7 | $\frac{1}{6}$ | $\frac{1}{3}$ |
| R1,R8 | $\frac{1}{3}$ | $\frac{2}{3}$ |
| R1,R9 | $\frac{1}{3}$ | $\frac{2}{3}$ |
| R1,R10 | $\frac{1}{2}$ | 1 |
| R7,R8 | $\frac{1}{2}$ | 1 |
| R7,R9 | $\frac{1}{3}$ | $\frac{2}{3}$ |
| R7,R10 | 0 | 0 |
| R8,R9 | $\frac{1}{3}$ | $\frac{2}{3}$ |
| R8,R10 | $\frac{1}{6}$ | $\frac{1}{3}$ |
| R9,R10 | $\frac{1}{3}$ | $\frac{2}{3}$ |
| 总安全性 | $\frac{3}{10}$ | $\frac{6}{10}$ |
| [1] | CAO Yuan, ZHAO Yongli. Research Progress of Quantum Communication Networks[J]. Laser Journal, 2019, 40(9):1-7. |
| 曹原, 赵永利. 量子通信网络研究进展[J]. 激光杂志, 2019, 40(9):1-7. | |
| [2] | WU Zhangbin, CHEN Guang, YANG Bojun. Analysis of Quantum Key Distribution Networks[J]. Study on Optical Communications, 2009, 35(2):22-24. |
| 吴张斌, 陈光, 杨伯君. 量子密钥分配网络分析[J]. 光通信研究, 2009, 35(2):22-24. | |
| [3] | SHI Lei, SU Jinhai, GUO Yixi. Optimal Routing Selection Algorithm of End-to-end Key Agreement in Quantum Key Distribution Network[J]. Journal of Computer Applications, 2015, 35(12):3336-3340, 3397. |
| 石磊, 苏锦海, 郭义喜. 量子密钥分发网络端端密钥协商最优路径选择算法[J]. 计算机应用, 2015, 35(12):3336-3340,3397. | |
| [4] | YANG Huike. Research on the Dynamic Routing in Quantum Cryptography Communication Network and Entangled Bell State Measurement[D]. Xi’an: Xidian University, 2015. |
| 杨会科. 量子保密通信网络的动态路由及纠缠贝尔态测量的研究[D]. 西安:西安电子科技大学, 2015. | |
| [5] | WANG Xuan. Research on the Dynamic Routing and Application Access in Quantum Cryptography Communication Network[D]. Xi’an: Xidian University, 2014. |
| 王轩. 量子保密通信网络的动态路由及应用接入研究[D]. 西安:西安电子科技大学, 2014. | |
| [6] | SHAO Kai. Research on Topology and Routing Algorithm for Multi-user Quantum Communication Network[D]. Xi’an: Xidian University, 2014. |
| 邵凯. 多用户量子通信网络拓扑结构及路由算法研究[D]. 西安:西安电子科技大学, 2014. | |
| [7] | LI Min, QUAN Dongxiao, ZHU Changhua. Stochastic Routing in Quantum Cryptography Communication Network Based on Cognitive Resources[C]// IEEE. 8th International Conference on Wireless Communications & Signal Processing(WCSP), October 13-15, 2016, Yangzhou, China. New Jersey: IEEE, 2016: 1-4. |
| [8] | LI Min. Research on the Routing Algorithm in Quantum Cryptography Communication Network[D]. Xi’an: Xidian University, 2017. |
| 李敏. 量子保密通信网络路由算法研究[D]. 西安:西安电子科技大学, 2017. | |
| [9] | LI Huanqin. Optimization of Routing and Measurement of Available Key Rate in Quantum Cryptography Communication Network[D]. Xi’an: Xidian University, 2018. |
| 李焕芹. 量子保密通信网络路由优化与可用密钥速率测量[D]. 西安:西安电子科技大学, 2018. | |
| [10] | WEN Hao, HAN Zhengfu, ZHAO Yibo, et al. Multiple Stochastic Paths Scheme on Partially-trusted Relay Quantum Key Distribution Network[J]. Science in China(Series F: Information Sciences), 2009, 52(1):18-22. |
| [11] | MA Chenhui, GUO Yixi, SU Jinhai. A Multiple Paths Scheme with Labels for Key Distribution on Quantum Key Distribution Network[C]// IEEE. 2nd Advanced Information Technology, Electronic and Automation Control Conference(IAEAC), March 25-26, 2017, Chongqing, China. New York: IEEE, 2017: 2513-2517. |
| [12] | XU Yabin, CHEN Shujuan, LI Yanping. Research on Multipath Key Transmission in Quantum Key Distribution Network[J]. Journal of University of Electronic Science and Technology of China, 2020, 49(2):276-282. |
| 徐雅斌, 陈淑娟, 李艳平. 量子密钥分发网络的多路径密钥传输方法研究[J]. 电子科技大学学报, 2020, 49(2):276-282. | |
| [13] | HOU Baogang. Research on Topology and Routing Algorithm of Quantum Key Distribution Network[D]. Xi’an: Xidian University, 2013. |
| 侯保刚. 量子密钥分发网络拓扑结构及路由算法研究[D]. 西安:西安电子科技大学, 2013. | |
| [14] | BARNETT S M, PHOENIX S J D. Securing a Quantum Key Distribution Network Using Secret Sharing[C]// IEEE. 2011 IEEE GCC Conference and Exhibition, February 19-22, 2011, Dubai, United Arab Emirates. New Jersey: IEEE, 2011: 143-145. |
| [15] | LIU Guangcong, ZHANG Hua, WEI Dongli. Node-disjoint Multi-path Routing Algorithm Based on AODV in Ad Hoc Networks[J]. Application Research of Computers, 2011, 28(2):692-695. |
| 刘广聪, 张桦, 韦东丽. 一种基于Ad Hoc网络AODV协议的不相交节点多路径路由算法[J]. 计算机应用研究, 2011, 28(2):692-695. |
| [1] | LIU Xin, YANG Haorui, GUO Zhenbin, WANG Jiayin. An Authentication Protocol Achieving Online Registration and Privilege Separation for Industrial Internet of Things [J]. Netinfo Security, 2021, 21(7): 1-9. |
| [2] | FANG Minzhi, CHENG Guang, KONG Panyu. Anti-noise Application Layer Binary Protocol Format Reverse Method [J]. Netinfo Security, 2021, 21(7): 72-79. |
| [3] | HU Bowen, ZHOU Chunjie, LIU Lu. Coordination of Functional Safety and Information Security for Intelligent Instrument Based on Fuzzy Multi-objective Decision [J]. Netinfo Security, 2021, 21(7): 10-16. |
| [4] | WEN Weiping, FANG Ying, YE He, CHEN Xiarun. A Code Obfuscation System against Symbolic Execution Attacks [J]. Netinfo Security, 2021, 21(7): 17-26. |
| [5] | REN Tao, JIN Ruochen, LUO Yongmei. Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning [J]. Netinfo Security, 2021, 21(7): 27-34. |
| [6] | GUO Chun, CAI Wenyan, SHEN Guowei, ZHOU Xuemei. Research on SQL Injection Attacks Detection Method Based on the Truncated Key Payload [J]. Netinfo Security, 2021, 21(7): 43-53. |
| [7] | XU Hongping, MA Zewen, YI Hang, ZHANG Longfei. Network Traffic Anomaly Detection Technology Based on Convolutional Recurrent Neural Network [J]. Netinfo Security, 2021, 21(7): 54-62. |
| [8] | ZHAO Yuran, MENG Kui. Research on English-Chinese Machine Translation Based on Sentence Grouping [J]. Netinfo Security, 2021, 21(7): 63-71. |
| [9] | CHEN Bowei, XIA Xuan, ZHONG Weidong, WU Liqiang. The Defense Scheme of S-box on LBlock Based on Secret Sharing [J]. Netinfo Security, 2021, 21(7): 80-86. |
| [10] | HUANG Ziyi, QIN Yuhai. Malicious Mining Web Page Detection and Forensics Based on Multi-feature Recognition [J]. Netinfo Security, 2021, 21(7): 87-94. |
| [11] | LIU Xin, GUO Zhenbin, SONG Yuchen. An Authentication Scheme Based on SGX for Industrial Internet of Things [J]. Netinfo Security, 2021, 21(6): 1-10. |
| [12] | ZHANG Zheng, LIU Ya’nan, WANG Lei, FANG Xuming. An Accuracy and Efficiency Multi-hop Localization for Irregular Network [J]. Netinfo Security, 2021, 21(6): 11-18. |
| [13] | SHEN Zhuowei, GAO Peng, XU Xinyu. Design of DDS Secure Communication Middleware Based on Security Negotiation [J]. Netinfo Security, 2021, 21(6): 19-25. |
| [14] | LIU Jing*, ZHANG Yuchen, ZHANG Hongqi. Automatic Intrusion Response Decision-making Method Based on Q-Learning [J]. Netinfo Security, 2021, 21(6): 26-35. |
| [15] | WU Yi, ZHONG Sheng. Research on Raft Consensus Algorithm for Blockchain [J]. Netinfo Security, 2021, 21(6): 36-44. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||