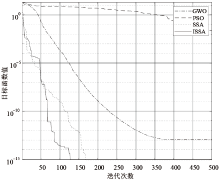
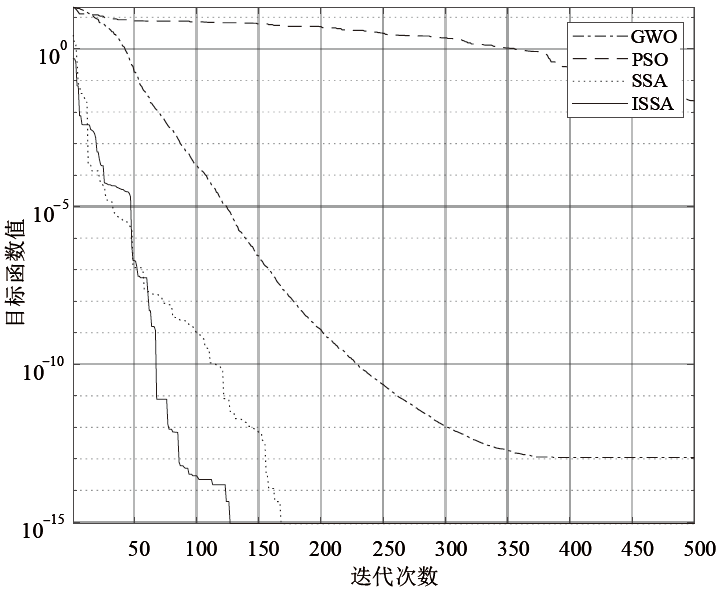
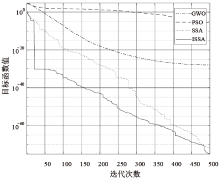
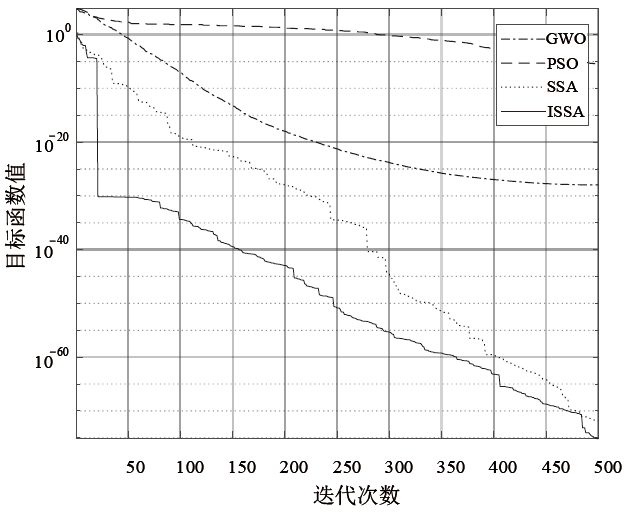
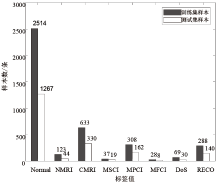
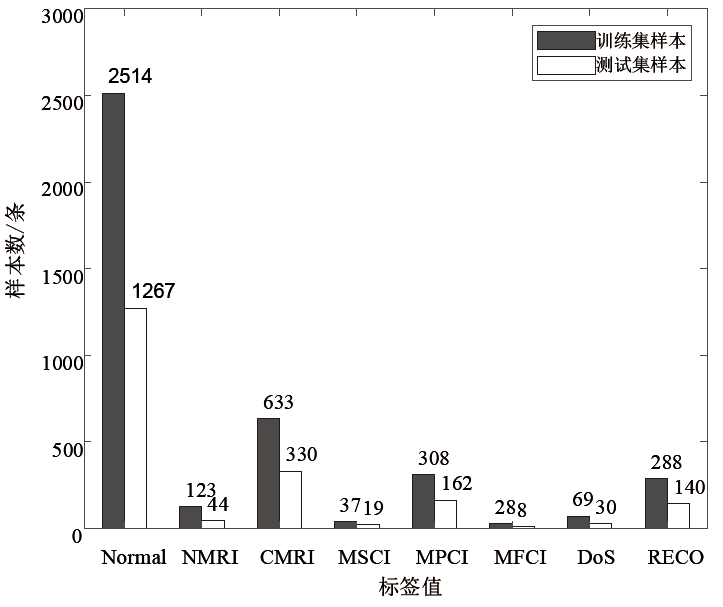
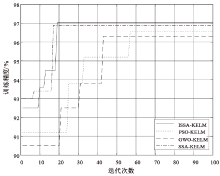
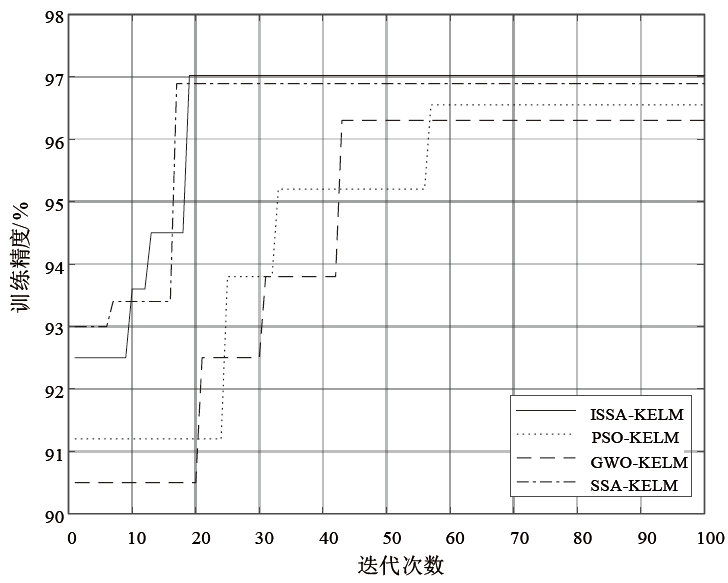
Netinfo Security ›› 2021, Vol. 21 ›› Issue (2): 1-9.doi: 10.3969/j.issn.1671-1122.2021.02.001
Previous Articles Next Articles
Industrial Control Intrusion Detection Method Based on Optimized Kernel Extreme Learning Machine
DU Ye, WANG Zimeng( ), LI Meihong
), LI Meihong
- School of Computer and Information Technology, Beijing Jiaotong University, Beijing 100044, China
-
Received:2020-09-28Online:2021-02-10Published:2021-02-23 -
Contact:WANG Zimeng E-mail:18120483@bjtu.edu.cn
CLC Number:
Cite this article
DU Ye, WANG Zimeng, LI Meihong. Industrial Control Intrusion Detection Method Based on Optimized Kernel Extreme Learning Machine[J]. Netinfo Security, 2021, 21(2): 1-9.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.02.001
| 函数名 | 表达式 | 维度 | 搜索区间 | 最小值 |
|---|---|---|---|---|
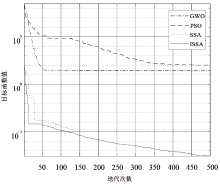
| Ackley | $\begin{array}{l}F(x)=-20 \exp \left(-0.2 \sqrt{\frac{1}{n} \sum_{i=1}^{n} x_{i}^{2}}\right)- \\\exp \left(\frac{1}{n} \sum_{i=1}^{n} \cos \left(2 \pi x_{i}\right)\right)+20+\mathrm{e}\end{array}$ | 30 | [-32,32] | 0 |
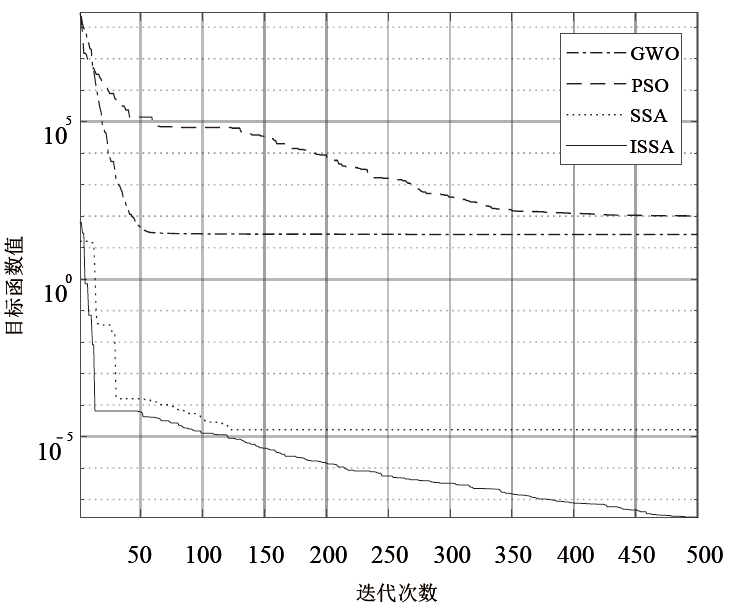
| Sphere | $F(x)=\sum_{i=1}^{n} x_{i}^{2}$ | 30 | [-100,100] | 0 |
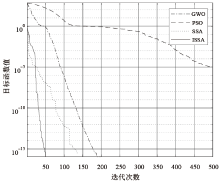
| Rosenbrock | $F(x)=\sum_{i=1}^{n-1}\left[100\left(x_{i+1}-x_{i}^{2}\right)^{2}+\left(x_{i}-1\right)^{2}\right]$ | 30 | [-30,30] | 0 |
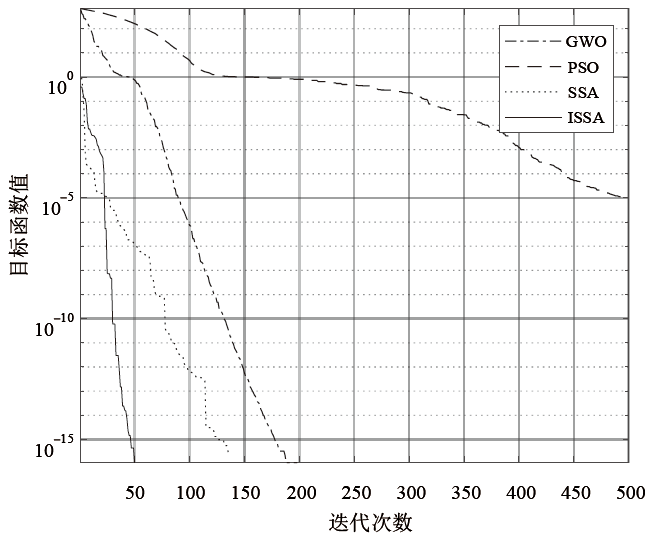
| Girewank | $F(x)=\frac{1}{4000} \sum_{i=1}^{n} x_{i}^{2}-\prod_{i=1}^{n} \cos \left(\frac{x_{i}}{\sqrt{i}}\right)+1$ | 30 | [-600,600] | 0 |
| [1] | YANG An, SUN Limin, WANG Xiaoshan, et al. Intrusion Detection Techniques for Industrial Control Systems[J]. Journal of Computer Research and Development, 2016,53(9):2039-2054. |
| 杨安, 孙利民, 王小山, 等. 工业控制系统入侵检测技术综述[J]. 计算机研究与发展, 2016,53(9):2039-2054. | |
| [2] | CHEN Hanyu, WANG Huazhong, YAN Bingyong. Application of CUDA and Cuckoo Algorithm-based SVM in Industrial Control System Intrusion Detection[J]. Journal of East China University of Science and Technology (Natural Science Edition), 2019,45(1):101-109. |
| 陈汉宇, 王华忠, 颜秉勇. 基于CUDA和布谷鸟算法的SVM在工控入侵检测中的应用[J]. 华东理工大学学报(自然科学版), 2019,45(1):101-109. | |
| [3] | CHEN Wanzhi, XU Dongsheng, ZHANG Jing, et al. Intrusion Detection Method for Industrial Control System with Optimized Support Vector Machine and K-means++[J]. Journal of Computer Applications, 2019,39(4):1089-1094. |
| 陈万志, 徐东升, 张静, 等. 结合优化支持向量机与K-means++的工控系统入侵检测方法[J]. 计算机应用, 2019,39(4):1089-1094. | |
| [4] | LI Yi, LI Yongzhong. Intrusion Detection Algorithm for Industrial Control Networks Based on Auto-encoder and Extreme Learning Machine[J]. Journal of Nanjing University of Science and Technology, 2019,43(4):408-413. |
| 李熠, 李永忠. 基于自编码器和极限学习机的工业控制网络入侵检测算法[J]. 南京理工大学学报, 2019,43(4):408-413. | |
| [5] | ZHAO Guoxin, CHEN Zhilian, WEI Zhanhong, et al. Intrusion Detection of Industrial Control System Based on Optimized Extreme Learning Machine[J]. Computer Engineering and Design, 2020,41(3):608-613. |
| 赵国新, 陈志炼, 魏战红, 等. 基于优化极限学习机的工业控制系统入侵检测[J]. 计算机工程与设计, 2020,41(3):608-613. | |
| [6] | CHEN Wanzhi, LI Dongzhe. Intrusion Detection Method in Industrial Control Network Combining White List Filtering and Neural Network[J]. Journal of Computer Applications, 2018,38(2):363-369. |
| 陈万志, 李东哲. 结合白名单过滤和神经网络的工业控制网络入侵检测方法[J]. 计算机应用, 2018,38(2):363-369. | |
| [7] | SHI Leyi, ZHU Hongqiang, LIU Yihao, et al. Intrusion Detection of Industrial Control System Based on Correlation Information Entropy and CNN-BiLSTM[J]. Journal of Computer Research and Development, 2019,56(11):2330-2338. |
| 石乐义, 朱红强, 刘祎豪, 等. 基于相关信息熵和CNN-BiLSTM的工业控制系统入侵检测[J]. 计算机研究与发展, 2019,56(11):2330-2338. | |
| [8] | XUE Jiankai, SHEN Bo. A Novel Swarm Intelligence Optimization Approach: Sparrow Search Algorithm[J]. Systems Science & Control Engineering, 2020,8(1):22-34. |
| [9] | LÜ Xin, MU Xiaodong, ZHANG Jun, et al. Chaos Sparrow Search Optimization Algorithm[EB/OL]. https://doi.org/10.13700/j.bh.1001-5965.2020.0298, 2020-08-31. |
| 吕鑫, 慕晓冬, 张钧, 等. 混沌麻雀搜索优化算法[EB/OL]. https://doi.org/10.13700/j.bh.1001-5965.2020.0298, 2020-08-31. | |
| [10] | WANG Zhendong, LIU Yaodi, YANG Shuxin, et al. Network Intrusion Detection Based BSO and Improved RELM[EB/OL]. https://doi.org/10.16383/j.aas.c190851, 2020-04-14. |
| 王振东, 刘尧迪, 杨书新, 等. 基于天牛群优化与改进正则化极限学习机的网络入侵检测[EB/OL]. https://doi.org/10.16383/j.aas.c190851, 2020-04-14. | |
| [11] | WANG Peichong. Dynamic Fireworks Explosion Search Algorithm Integrating Good-point Set[J]. Computer Applications and Software, 2015,32(8):248-251, 299. |
| 王培崇. 融合佳点集机制的动态搜索烟花爆炸搜索算法[J]. 计算机应用与软件, 2015,32(8):248-251,299. | |
| [12] | ZHANG Yue, SUN Huixiang, WEI Zhenglei, et al. Chaotic Gray Wolf Optimization Algorithm with Adaptive Adjustment Strategy[J]. Computer Science, 2017,44(S2):119-122, 159. |
| 张悦, 孙惠香, 魏政磊, 等. 具有自适应调整策略的混沌灰狼优化算法[J]. 计算机科学, 2017,44(S2):119-122,159. | |
| [13] | BAMAKAN S M H, WANG Huadong, TIAN Yingjie, et al. An Effective Intrusion Detection Framework Based on MCLP/SVM Optimized by Time-varying Chaos Particle Swarm Optimization[J]. Neurocomputing, 2016,199(7):90-102. |
| [14] |
RASHID T A, ABBAS D K, TUREL Y K, et al. A Multi Hidden Recurrent Neural Network with a Modified Grey Wolf Optimizer[J]. Plos One, 2019,14(3).
doi: 10.1371/journal.pone.0214587 URL pmid: 30925170 |
| [15] | MORRIS T, GAO W. Industrial Control System Traffic Data Sets for Intrusion Detection Research[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=29c45c9e93b60cec841ad8c05f28b746&site=xueshu_se, 2020-08-16. |
| [16] | CHEN Hanyi. Research on Intrusion Detection Method of Industrial Control System[D]. Guilin: Guilin University of Electronic Technology, 2019. |
| 陈汉宜. 工业控制系统入侵检测方法研究[D]. 桂林:桂林电子科技大学, 2019. |
| [1] | SHI Leyi, XU Xinghua, LIU Yihao, LIU Jia. An Improved Probabilistic Neural Network Method of Security Situation Assessment for Industrial Control System [J]. Netinfo Security, 2021, 21(3): 15-25. |
| [2] | LI Jiawei, WU Kehe, ZHANG Bo. Research on Anomaly Detection of Power Industrial Control System Based on Gaussian Mixture Clustering [J]. Netinfo Security, 2021, 21(3): 53-63. |
| [3] | WANG Huazhong, CHENG Qi. Research on Intrusion Detection of Industrial Control System Based on Improved Whale Algorithm [J]. Netinfo Security, 2021, 21(2): 53-60. |
| [4] | SHEN Yeming, LI Beibei, LIU Xiaojie, OUYANG Yuankai. Research on Active Learning-based Intrusion Detection Approach for Industrial Internet [J]. Netinfo Security, 2021, 21(1): 80-87. |
| [5] | LI Qiao, LONG Chun, WEI Jinxia, ZHAO Jing. A Hybrid Model of Intrusion Detection Based on LMDR and CNN [J]. Netinfo Security, 2020, 20(9): 117-121. |
| [6] | LI Shibin, LI Jing, TANG Gang, LI Yi. Method of Network Security States Prediction and Risk Assessment for Industrial Control System Based on HMM [J]. Netinfo Security, 2020, 20(9): 57-61. |
| [7] | XU Guotian. Research on K-Nearest Neighbor High Speed Matching Algorithm in Network Intrusion Detection [J]. Netinfo Security, 2020, 20(8): 71-80. |
| [8] | JIANG Nan, CUI Yaohui, WANG Jian, WU Jinchao. Context-based Attack Scenario Reconstruction Model for IDS Alarms [J]. Netinfo Security, 2020, 20(7): 1-10. |
| [9] | ZHANG Xiaoyu, WANG Huazhong. Intrusion Detection of ICS Based on Improved Border-SMOTE for Unbalance Data [J]. Netinfo Security, 2020, 20(7): 70-76. |
| [10] | PENG Zhonglian, WAN Wei, JING Tao, WEI Jinxia. Research on Intrusion Detection Method Based on Modified CGANs [J]. Netinfo Security, 2020, 20(5): 47-56. |
| [11] | WANG Rong, MA Chunguang, WU Peng. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [12] | LUO Wenhua, XU Caidian. Network Intrusion Detection Based on Improved MajorClust Clustering [J]. Netinfo Security, 2020, 20(2): 14-21. |
| [13] | HE Jingsha, HAN Song, ZHU Nafei, GE Jiake. Research and Optimization of Intrusion Detection Based on Improved V-detector Algorithm [J]. Netinfo Security, 2020, 20(12): 19-27. |
| [14] | Jian KANG, Jie WANG, Zhengxu LI, Guangda ZHANG. A Model for Anomaly Intrusion Detection with Different Feature Extraction Strategies in IoT [J]. Netinfo Security, 2019, 19(9): 21-25. |
| [15] | Wenying FENG, Xiaobo GUO, Yuanye HE, Cong XUE. Intrusion Detection Model Based on Feedforward Neural Network [J]. Netinfo Security, 2019, 19(9): 101-105. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||