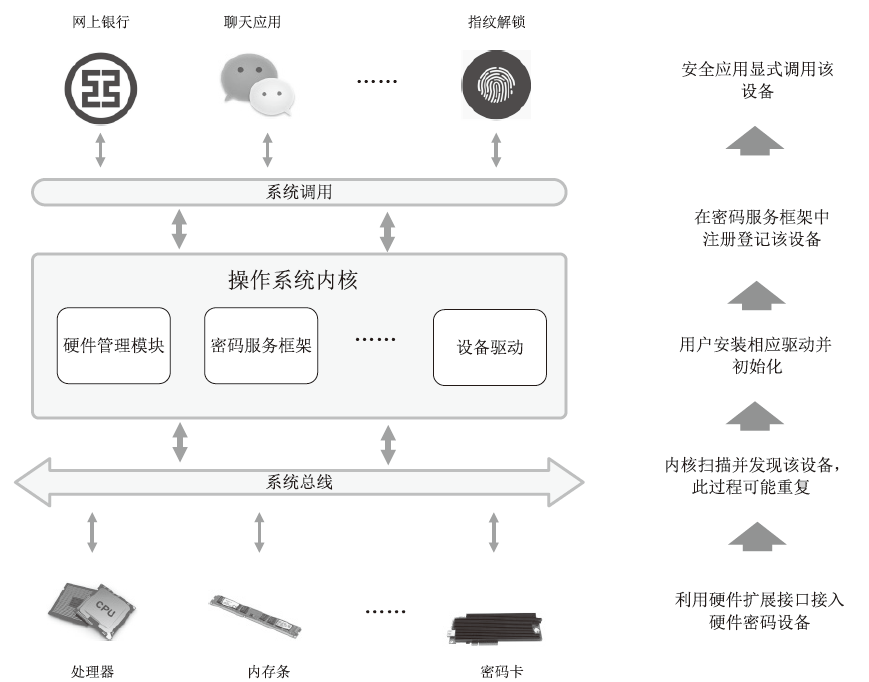
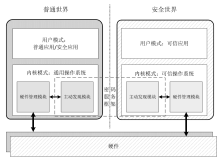
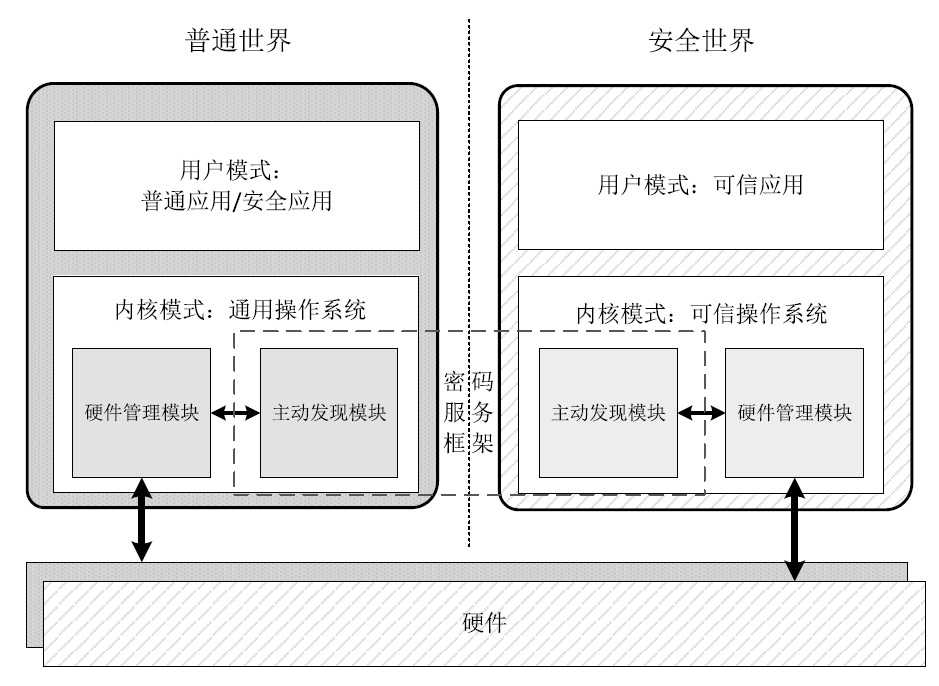
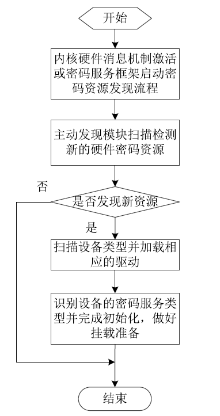
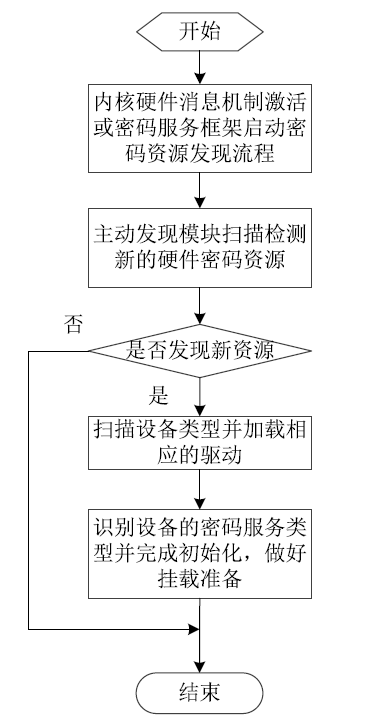
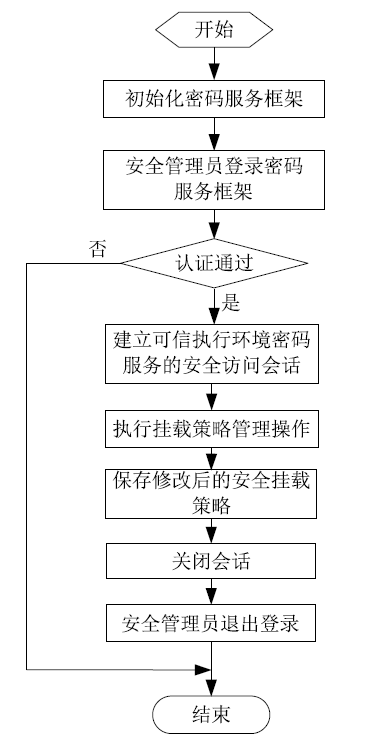
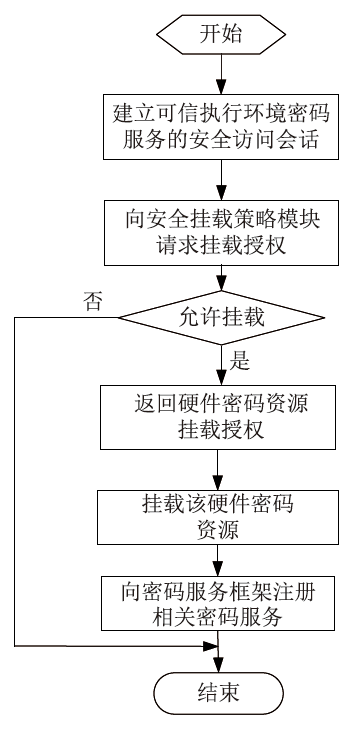
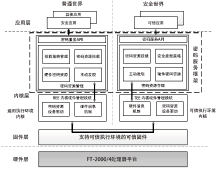
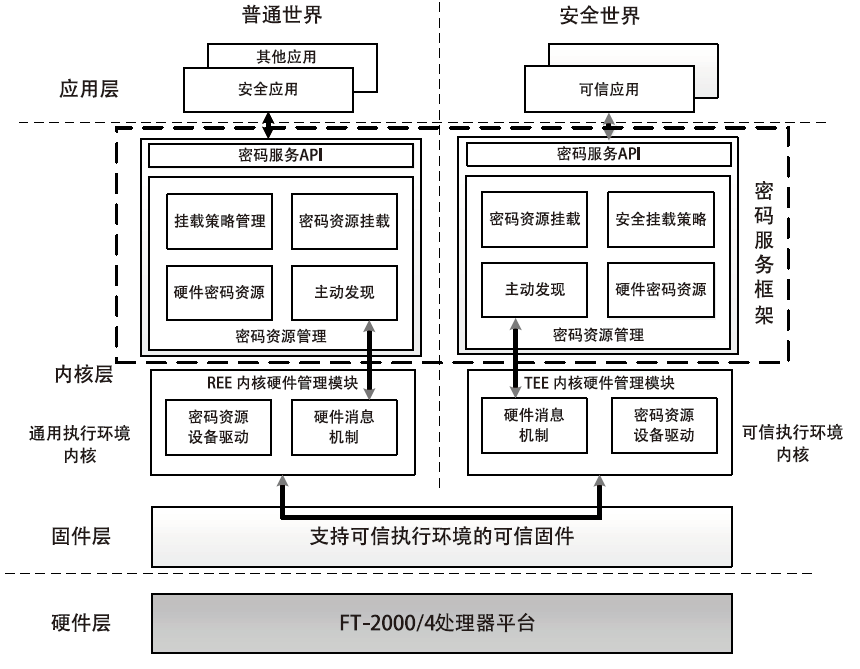
Netinfo Security ›› 2020, Vol. 20 ›› Issue (8): 47-54.doi: 10.3969/j.issn.1671-1122.2020.08.006
Previous Articles Next Articles
An Active Discovering and Secure Using Method of Hardware Cryptographic Resources Based on TrustZone
YUAN Lu1, HUANG Chenlin1( ), LI Yun1, CHENG Hua2
), LI Yun1, CHENG Hua2
- 1. Academy of Computer Science, National University of Defense Technology, Changsha 410073, China
2. State Key Laboratory of Mathematical Engineering and Advanced Computing, Wuxi 214083, China
-
Received:2020-06-01Online:2020-08-10Published:2020-10-20 -
Contact:HUANG Chenlin E-mail:huangchenlin76@gmail.com
CLC Number:
Cite this article
YUAN Lu, HUANG Chenlin, LI Yun, CHENG Hua. An Active Discovering and Secure Using Method of Hardware Cryptographic Resources Based on TrustZone[J]. Netinfo Security, 2020, 20(8): 47-54.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2020.08.006
| [1] | STINSON D R, PATERSON M. Cryptography: Theory and Practice[M]. Boca Raton: CRC Press, 2018. |
| [2] | LÜ Yao, LI Dongge. Interpretation and Impact Analysis of the Cryptography Law[J]. Cyberspace Security, 2019,10(11):74-78. |
| 吕尧, 李东格. 《密码法》解读及影响分析[J]. 网络空间安全, 2019,10(11):74-78. | |
| [3] | PINTO S, SANTOS N. Demystifying Arm TrustZone: A Comprehensive Survey[J]. ACM Computing Surveys (CSUR), 2019,51(6):1-36. |
| [4] | LE A V, MATYAS S M, JOHNSON D B J, et al. A Public Key Extension to the Common Cryptographic Architecture[J]. IBM Systens Journal, 1993,32(3):461-485. |
| [5] |
LIN A, BROWN R. The Application of Security Policy to Role-based Access Control and the Common Data Security Architecture[J]. Computer Communications, 2000,23(17):1584-1593.
doi: 10.1016/S0140-3664(00)00244-9 URL |
| [6] | DELAUNE S, KREMER S, STEEL G. Formal analysis of PKCS# 11[C]// IEEE. 21st IEEE Computer Security Foundations Symposium, June 23-25, 2008, Pittsburgh, PA, USA. Piscataway: IEEE, 2008: 331-344. |
| [7] | TAN Anfen, JIANG Jianguo. A Case Analyse of Security Architecture[J]. Network Security Technology & Application, 2004,9:13. |
| 谭安芬, 姜建国. 安全体系架构的一个实例分析[J]. 网络安全技术与应用, 2004,9:13. | |
| [8] | WANG Yuzhu, LÜ Shuwang, WANG Ting. Intel’s CDSA and Microsoft’s CAPI[J]. Application Research of Computers, 2001,18(5):72-74. |
| 王玉柱, 吕述望, 王挺. Intel的CDSA和Microsoft的CAPI[J]. 计算机应用研究, 2001,18(5):72-74. | |
| [9] | MENG Zhimin, LIU Jun. Research and Implementation of Key Management Mechanism Based on PKCS11[J]. Computer Security, 2012(12):50-53. |
| 蒙智敏, 刘军. PKCS11 标准下的密钥管理方式研究与实现[J]. 计算机安全, 2012(12):50-53. | |
| [10] | ZHAO Shijun, ZHANG Qianying, QIN Yu, et al. SecTEE: A Software-based Approach to Secure Enclave Architecture Using TEE[C]// ACM. The 2019 ACM SIGSAC Conference on Computer and Communications Security, November 11-15, 2019, London, UK. New York: ACM, 2019: 1723-1740. |
| [11] | SEBASTIAN D J, AGRAWAL U, TAMIMI A, et al. DER-TEE: Secure Distributed Energy Resource Operations through Trusted Execution Environments[J]. IEEE Internet of Things Journal, 2019,6(4):6476-6486. |
| [12] | RUBINOV K, ROSCULETE L, MITRA T, et al. Automated Partitioning of Android Applications for Trusted Execution Environments[C]// ACM. The 38th International Conference on Software Engineering (ICSE’16), May 14-22, 2016, Austin, TX, USA. New York: ACM, 2016: 923-934. |
| [13] | AZAB A M, NING P, SHAH J, et al. Hypervision Across Worlds: Real-time Kernel Protection from the Arm Trustzone Secure World[C]// ACM. The 2014 ACM SIGSAC Conference on Computer and Communications Security (CCS’14), November 3-7, 2014, Scottsdale, Arizona, USA. New York: ACM, 2014: 90-102. |
| [14] | GE Xinyang, VIJAYAKUMAR H, JAEGER T. Sprobes: Enforcing Kernel Code Integrity on the TrustZone Architecture[J]. Computer Science, 2014,25(6):1793-1795. |
| [15] | CHEN Haogang, MAO Yandong, WANG Xi, et al. Linux Kernel Vulnerabilities: State-of-the-art Defenses and Open Problems[C]// ACM. The Second Asia-Pacific Workshop on Systems (APSys’11), July 11-12, 2011, Shanghai, China. New York: ACM, 2014: 1-5. |
| [16] | GUO Hui, WANG Yongyi, PAN Zulie, et al. Research on Detecting Windows Vulnerabilities Based on Security Patch Comparison[C]// IEEE. Sixth International Conference on Instrumentation & Measurement, July 21-23, 2016, Harbin, China. Piscataway: IEEE, 2016: 366-369. |
| [17] | NEHAL A, AHLAWAT P. Securing IoT Applications with OP-TEE from Hardware Level OS[C]// IEEE. 3rd International Conference on Electronics, Communication and Aerospace Technology (ICECA), June 12-14, 2019, Coimbatore, India. Piscataway: IEEE, 2019: 1441-1444. |
| [1] | LU Jiali. Log Anomaly Detection Method Based on Improved Time Series Model [J]. Netinfo Security, 2020, 20(9): 1-5. |
| [2] | SHEN Jinwei, ZHAO Yi, LIANG Chunlin, ZHANG Ping. RFID Group Tag Ownership Transfer Protocol Based on Cyclic Grouping Function [J]. Netinfo Security, 2020, 20(9): 102-106. |
| [3] | ZHOU Zhining, WANG Binjun, ZHAI Yiming, TONG Xin. Spam Filtering Model Based on ALBERT Dynamic Word Vector [J]. Netinfo Security, 2020, 20(9): 107-111. |
| [4] | HAN Lei, CHEN Wuping, ZENG Zhiqiang, ZENG Yingming. Research on Hierarchical Network Structure and Application of Blockchain [J]. Netinfo Security, 2020, 20(9): 112-116. |
| [5] | LI Qiao, LONG Chun, WEI Jinxia, ZHAO Jing. A Hybrid Model of Intrusion Detection Based on LMDR and CNN [J]. Netinfo Security, 2020, 20(9): 117-121. |
| [6] | TONG Xin, WANG Luona, WANG Runzheng, WANG Jingya. A Generation Method of Word-level Adversarial Samples for Chinese Text Classification [J]. Netinfo Security, 2020, 20(9): 12-16. |
| [7] | HUANG Na, HE Jingsha, WU Yabiao, LI Jianguo. Method of Insider Threat Detection Based on LSTM Regression Model [J]. Netinfo Security, 2020, 20(9): 17-21. |
| [8] | ZHANG Runzi, LIU Wenmao, YOU Yang, XIE Feng. Research on AISecOps Automation Levels and Technology Trends [J]. Netinfo Security, 2020, 20(9): 22-26. |
| [9] | WU Zenan, TIAN Liqin, CHEN Nan. Research on Quantitative Analysis of System Security Based on Stochastic Petri Net [J]. Netinfo Security, 2020, 20(9): 27-31. |
| [10] | XU Yu, ZHOU You, LIN Lu, ZHANG Cong. Applied Research of Unsupervised Machine Learning in Game Anti-fraud [J]. Netinfo Security, 2020, 20(9): 32-36. |
| [11] | XU Huikai, LIU Yue, MA Zhenbang, DUAN Haixin. A Large-scale Measurement Study of MQTT Security [J]. Netinfo Security, 2020, 20(9): 37-41. |
| [12] | LIU Daheng, LI Hongling. Research on QR Code Phishing Detection [J]. Netinfo Security, 2020, 20(9): 42-46. |
| [13] | WANG Jinmiao, XIE Yongheng, WANG Guowei, LI Yiting. A Method of Privacy Preserving and Access Control in Blockchain Based on Attribute-based Encryption [J]. Netinfo Security, 2020, 20(9): 47-51. |
| [14] | ZENG Yingming, WANG Bin, GUO Min. Research on Collaborative Defense Technology of Network Security Based on Swarm Intelligence [J]. Netinfo Security, 2020, 20(9): 52-56. |
| [15] | LI Shibin, LI Jing, TANG Gang, LI Yi. Method of Network Security States Prediction and Risk Assessment for Industrial Control System Based on HMM [J]. Netinfo Security, 2020, 20(9): 57-61. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||