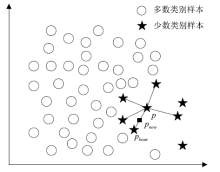
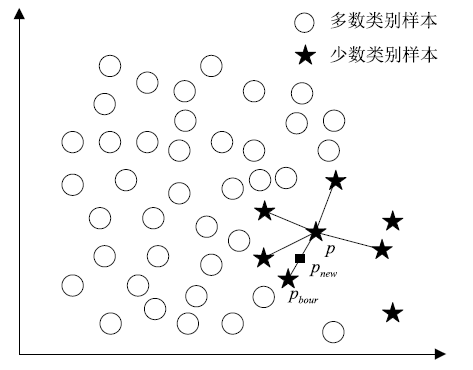
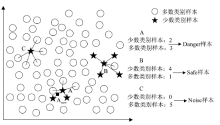
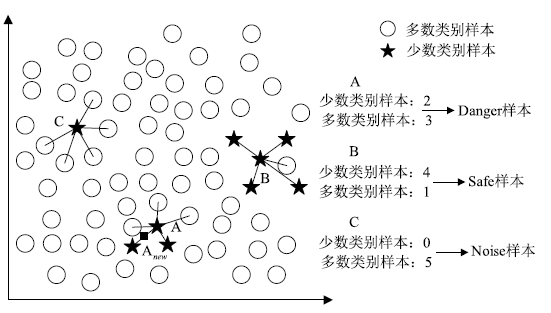
| [1] |
RUBIO J E, ALCARAZ C, ROMAN R, et al. Analysis of Intrusion Detection Systems in Industrial Ecosystems[C]// INSTICC. 14th International Conference on Security and Cryptography, July 26-28, 2017, Madrid, Spain. Madrid: INSTICC, 2017: 116-128.
|
| [2] |
FAN Xiaohe, FAN Kefeng, WANG Yong, et al. Overview of Cyber-security of Industrial Control System[C]// IEEE. 2015 International Conference on Cyber Security of Smart Cities, August 5-7, 2015, Shanghai, China. New Jersey: IEEE, 2015: 1-7.
|
| [3] |
YU Bangbing, WANG Huazhong, YAN Bingyong, Intrusion Detection of Industrial Control System Based on Grey Wolf Algorithm and Case-based Reasoning[J]. Journal of East China University of Science and Technology(Natural Science Edition), 2018,44(2):239-245.
|
|
於帮兵, 王华忠, 颜秉勇. 基于灰狼算法和案例推理的工控系统入侵检测[J]. 华东理工大学学报(自然科学版), 2018,44(2):239-245.
|
| [4] |
TRAUTMAN L J, ORMEROD P C. Industrial Cyber Vulnerabilities: Lessons from Stuxnet and the Internet of Things[J]. University of Miami Law Review, 2017,72(3):761.
|
| [5] |
DI P A, DRAGONI Y, CARCANO A. TRITON. The First ICS Cyber Attack on Safety Instrument Systems[C]// Black Hat. Black Hat USA 2018, August 4-6, 2018, Las Vegas, USA. Las Vegas: BLACK HAT, 2018: 1-26.
|
| [6] |
CHENG Dongmei, YAN Biao, WEN Hui, SUN Limin. The Design and Implement of Rule Matching-based Distributed Intrusion Detection Framework for Industry Control System[J]. Netinfo Security, 2017,17(7):45-51.
|
| [7] |
WU Yali, LI Guoting, FU Yulong, et al. A New Intrusion Detection Model Based on Adaptability and Robustness[J]. Control and Decision, 2019,34(11):2330-2336.
|
|
吴亚丽, 李国婷, 付玉龙, 等. 基于自适应鲁棒性的入侵检测模型[J]. 控制与决策, 2019,34(11):2330-2336.
|
| [8] |
KHALILI A, SAMI A. SysDetect: A Systematic Approach to Critical State Determination for Industrial Intrusion Detection Systems Using Apriori Algorithm[J]. Journal of Process Control, 2015,32(C):154-160.
|
| [9] |
MIRZA B, LIN Zhiping, LIU Nan. Ensemble of Subset Online Sequential Extreme Learning Machine for Class Imbalance and Concept Drift[J]. Neurocomputing, 2015,149(A):316-329.
|
| [10] |
HU Ji, YAN Chenggang, LIU Xin, et al. Truncated Gradient Confidence-Weighted Based Online Learning for Imbalance Streaming Data[C]// IEEE. 2019 IEEE International Conference on Multimedia and Expo(ICME), July 8-12, 2019, Shanghai, China. New Jersey: IEEE, 2019: 133-138.
|
| [11] |
CHAWLA N V, BOWYER K W, HALL L O, et al. SMOTE: Synthetic Minority Over-sampling Technique[J]. Journal of Artificial Intelligence Research, 2002,16(1):321-357.
|
| [12] |
HUANG Jianming, LI Xiaoming, QU Hezuo, et al. Method for Fault Type Identification of Transmission Line Considering Wavelet Singular Information and Unbalanced Dataset[J]. Proceedings of the CSEE, 2017,37(11):3099-3107, 3365.
|
|
黄建明, 李晓明, 瞿合祚, 等. 考虑小波奇异信息与不平衡数据集的输电线路故障识别方法[J]. 中国电机工程学报, 2017,37(11):3099-3107,3365.
|
| [13] |
LIU Chao, WU Shen, ZHENG Yichao, et al. Classification of Cancer Based on DeepForest and DNA Methylation[J]. Computer Engineering and Applications. 2020,56(13):189-193.
|
|
刘超, 吴申, 郑一超, 等. 基于深度森林和DNA甲基化的癌症分类研究[J]. 计算机工程与应用, 2020,56(13):189-193.
|
| [14] |
HAN Hui, WANG Wenyuan, MAO Binghuan. Borderline-SMOTE: A New Over-sampling Method in Imbalanced Data Sets Learning[C]// Springer. International Conference on Intelligent Computing, August 22-26, 2005, Hefei, China. Berlin: Springer, 2005: 878-887.
|
| [15] |
KHEMCHANDANI R, CHANDRA S. Twin Support Vector Machines for Pattern Classification[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2007,29(5):905-910.
doi: 10.1109/tpami.2007.1068
URL
pmid: 17469239
|
| [16] |
MATHUR A P, TIPPENHAUER N O. SWaT: A Water Treatment Testbed for Research and Training on ICS Security[C]// IEEE. 2016 International Workshop on Cyber-physical Systems for Smart Water Networks(CySWater), April 11, 2016, Vienna, Austria. New Jersey: IEEE, 2016: 31-36.
|